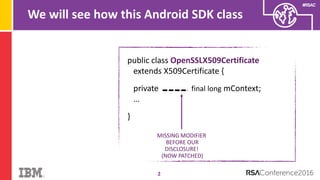
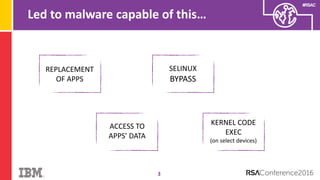
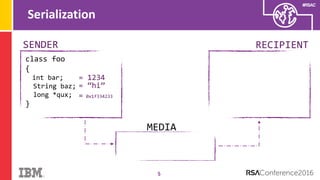
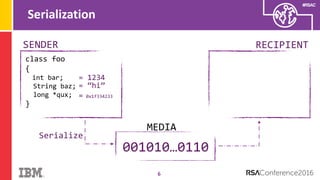
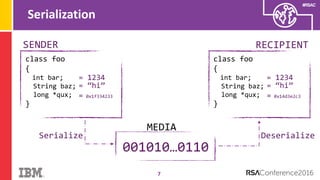
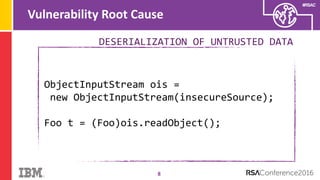
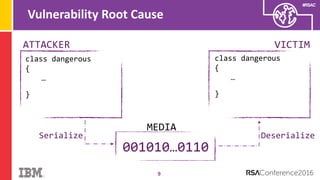
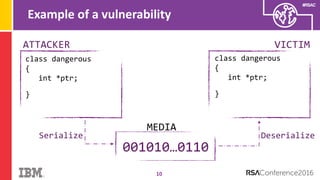
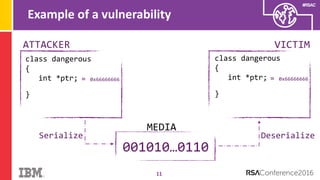
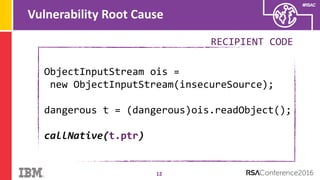
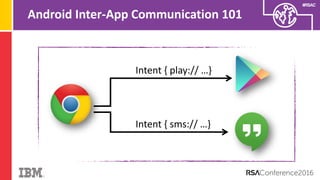
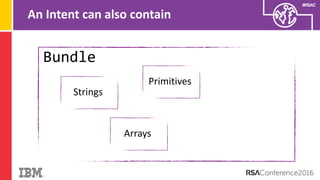
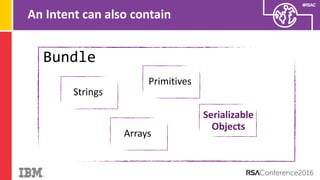
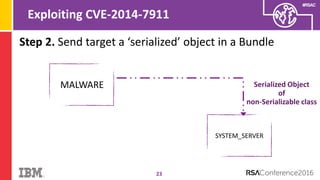
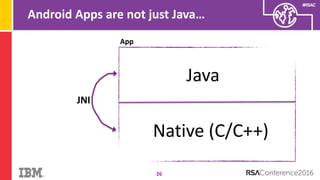
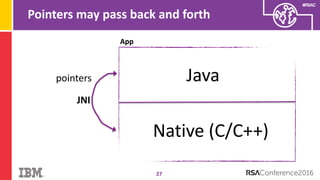
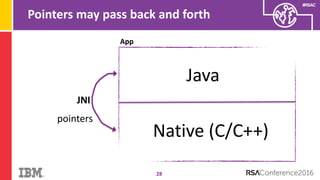
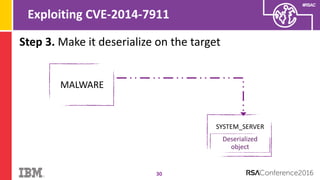
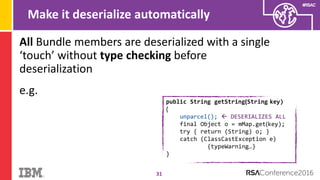
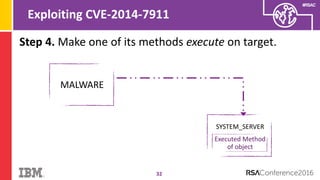
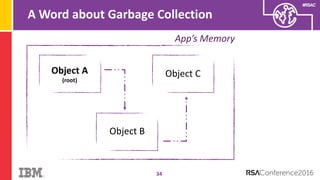
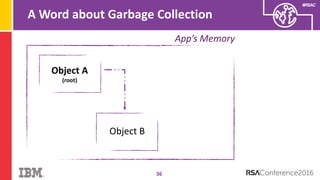
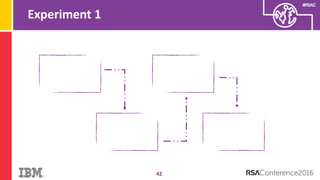
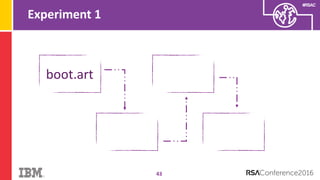
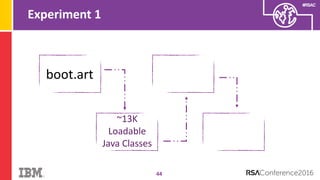
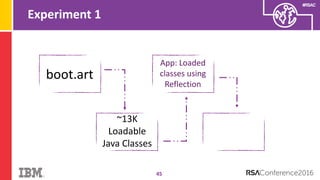
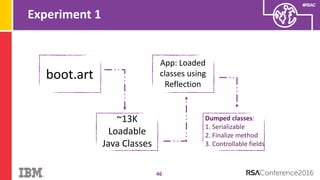
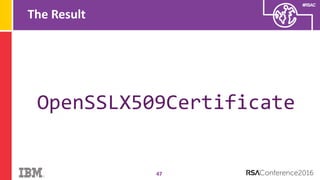
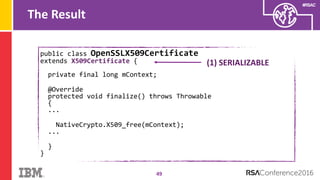
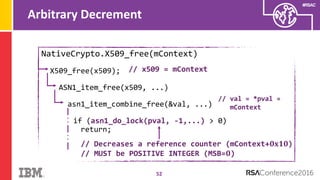
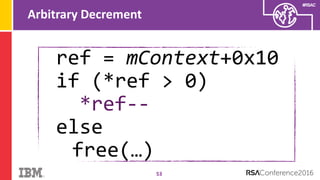
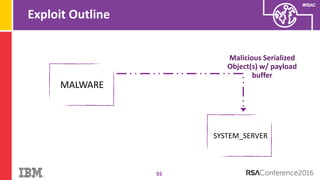
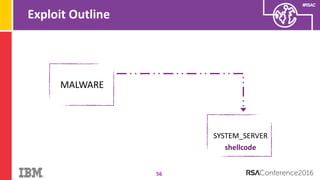
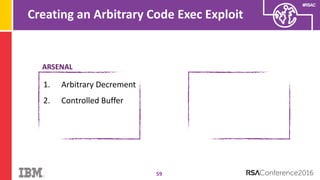
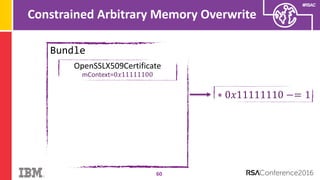
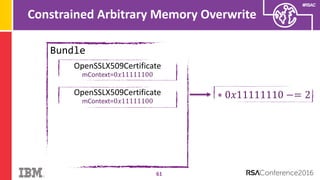
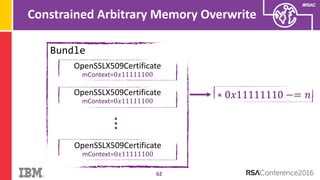
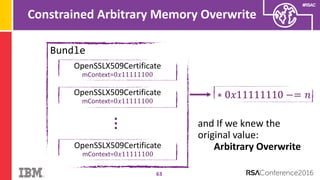
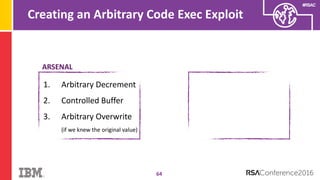
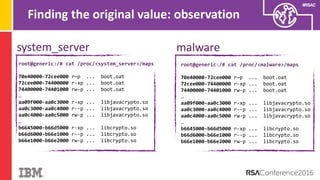
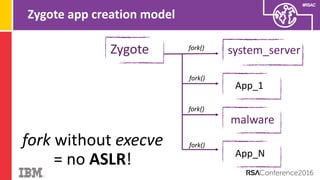
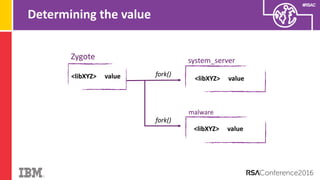
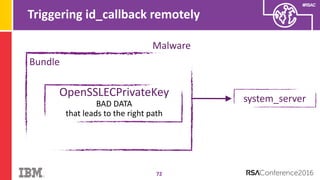
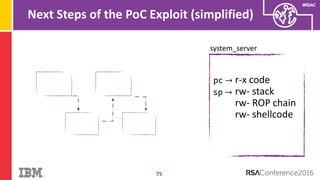
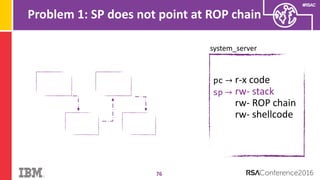
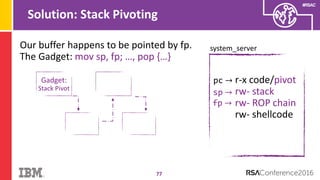
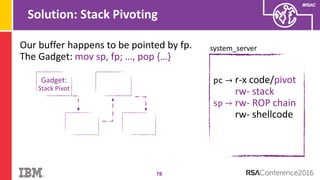
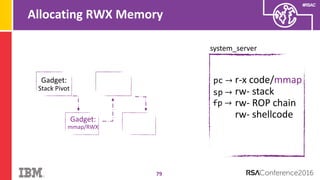
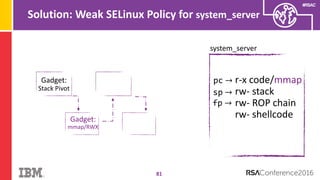
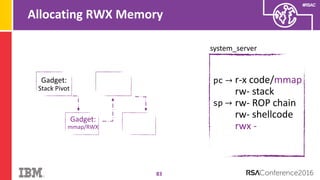
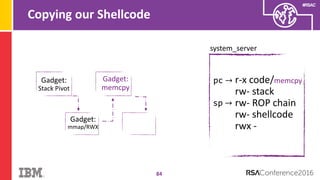
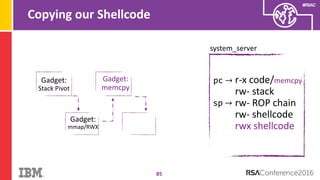
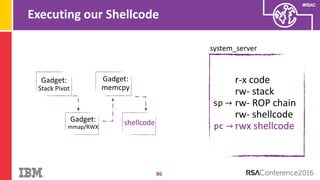
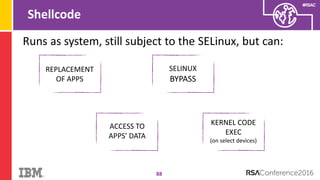
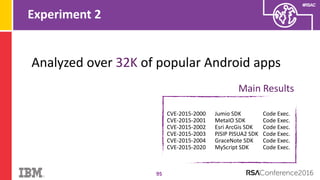
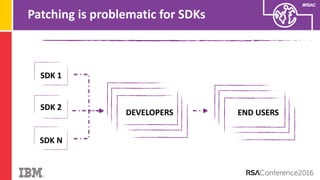
The document discusses vulnerabilities in Android related to serialization, specifically focusing on the CVE-2014-7911 and CVE-2015-3825 exploits that allowed malware to execute arbitrary code through deserialization of untrusted data in system_server. It outlines the history of serialization vulnerabilities and presents a detailed overview of how these exploits operate, including examples of code and techniques used by attackers. The document also notes Google’s patches for these vulnerabilities and the need for ongoing improvements in security measures against such exploits.