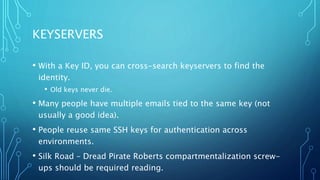
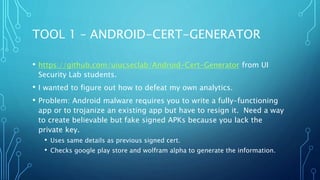
The document discusses operational security (opsec) and the pitfalls of using cryptography, emphasizing that not only is it vital to keep secrets, but also to not appear as if one has secrets worth hiding. It highlights various opsec problems with encryption, including the retention of metadata, the risks associated with SSL/TLS certificates, and how poor tech decisions can lead to exposure. Ultimately, it argues that effective opsec requires careful consideration of the adversaries involved and the notion of appearing 'normal' to avoid drawing unnecessary attention.










![AND THERE’S MORE
$ gpg -vvvv text.gpg
gpg: using character set `utf-8’
gpg: armor: BEGIN PGP MESSAGE
gpg: armor header: Version: GnuPG v2
:pubkey enc packet: version 3, algo 1, keyid F4402E054FD02AA1
data: [2046 bits]
gpg: public key is 4FD02AA1
:encrypted data packet: length: 400 mdc_method: 2
gpg: encrypted with RSA key, ID 4FD02AA1
gpg: decryption failed: secret key not available](https://image.slidesharecdn.com/defcon-crypto-160808003032/85/Defcon-Crypto-Village-OPSEC-Concerns-in-Using-Crypto-14-320.jpg)
![IF YOU HAVE THE KEY, YOU GET MORE
:secret key packet: version 4, algo 1, created 1442844965,
expires 0 skey[0]: [4096 bits] skey[1]: [17 bits] iter+salt
S2K, algo: 3, SHA1 protection, hash: 2, salt: 1edfd8aa175bb427
protect count: 65536 (96) protect IV: 8a d6 c0 76 0e
c4 86 5c encrypted stuff follows keyid:
0F3B1D99BBB8C31E:user ID packet: "John Bambenek
<john.bambenek@fidelissecurity.com>”
Anonymity with PGP is hard. See Tom Ritter’s Deanonymizing
Alt.Anonymous.Messages talk: https://ritter.vg/p/AAM-
defcon13.pdf](https://image.slidesharecdn.com/defcon-crypto-160808003032/85/Defcon-Crypto-Village-OPSEC-Concerns-in-Using-Crypto-15-320.jpg)