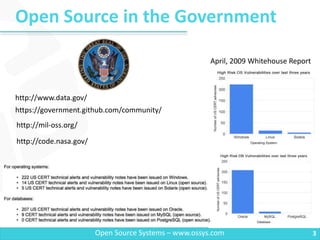
The document addresses the intersection of cyber security and open-source software, emphasizing the importance of knowledge to counter fear and misconceptions about open-source tools. It outlines common security threats, debunks myths surrounding open source, and advocates for the effective use of open-source resources and processes in software development. The speaker, Chad Cravens, shares insights from his experience and encourages embracing agile methodologies to enhance software security.