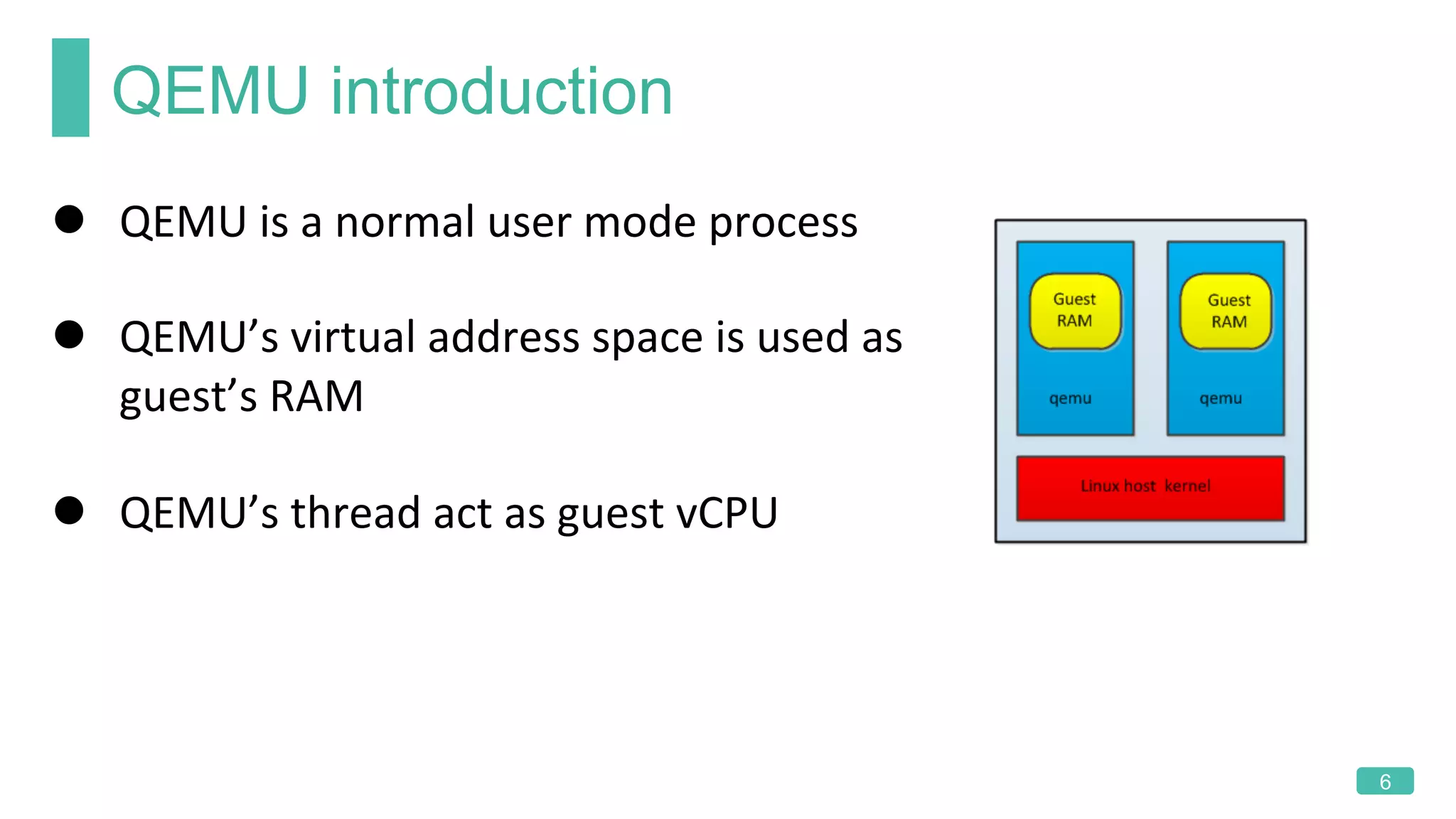
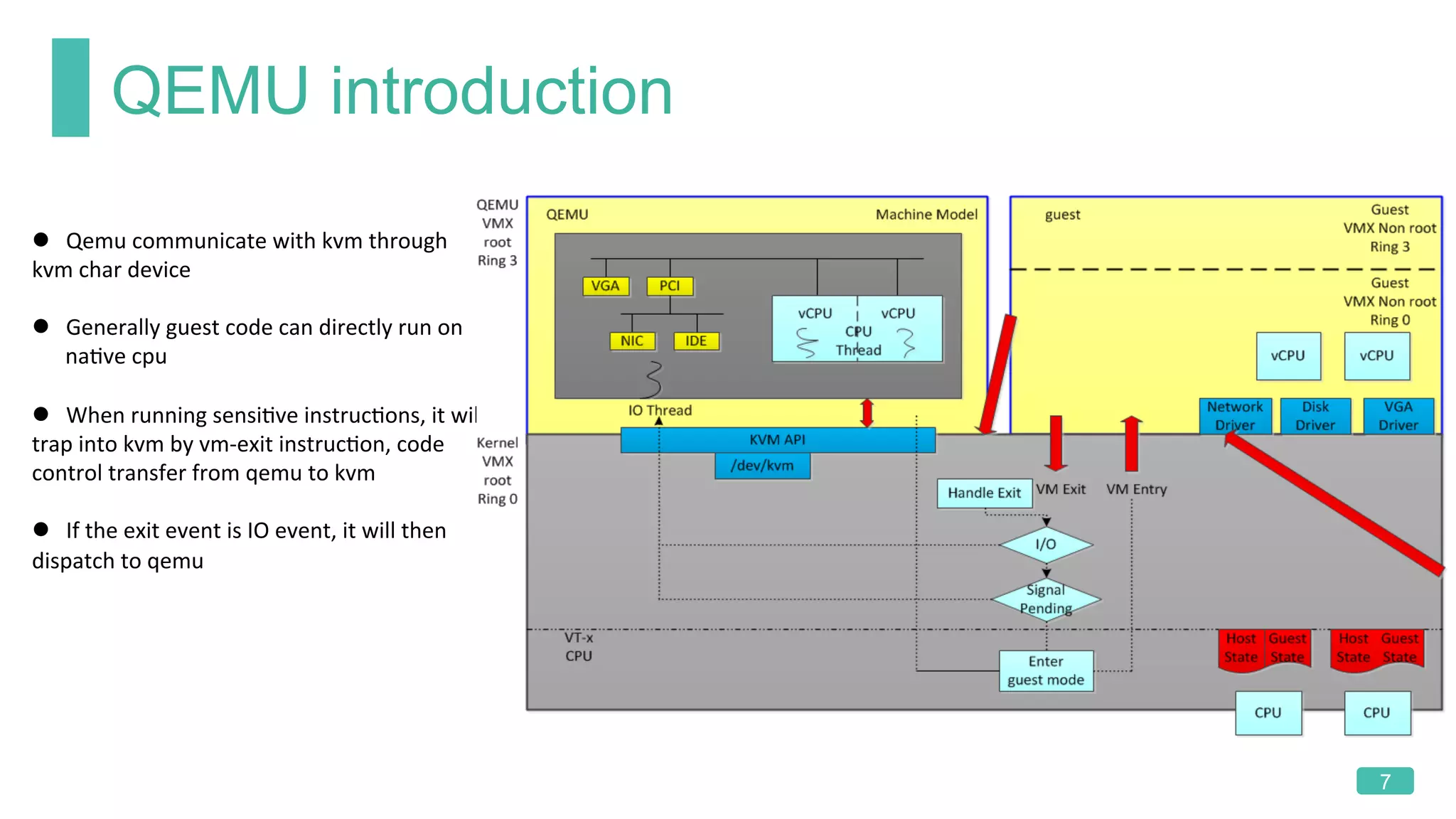
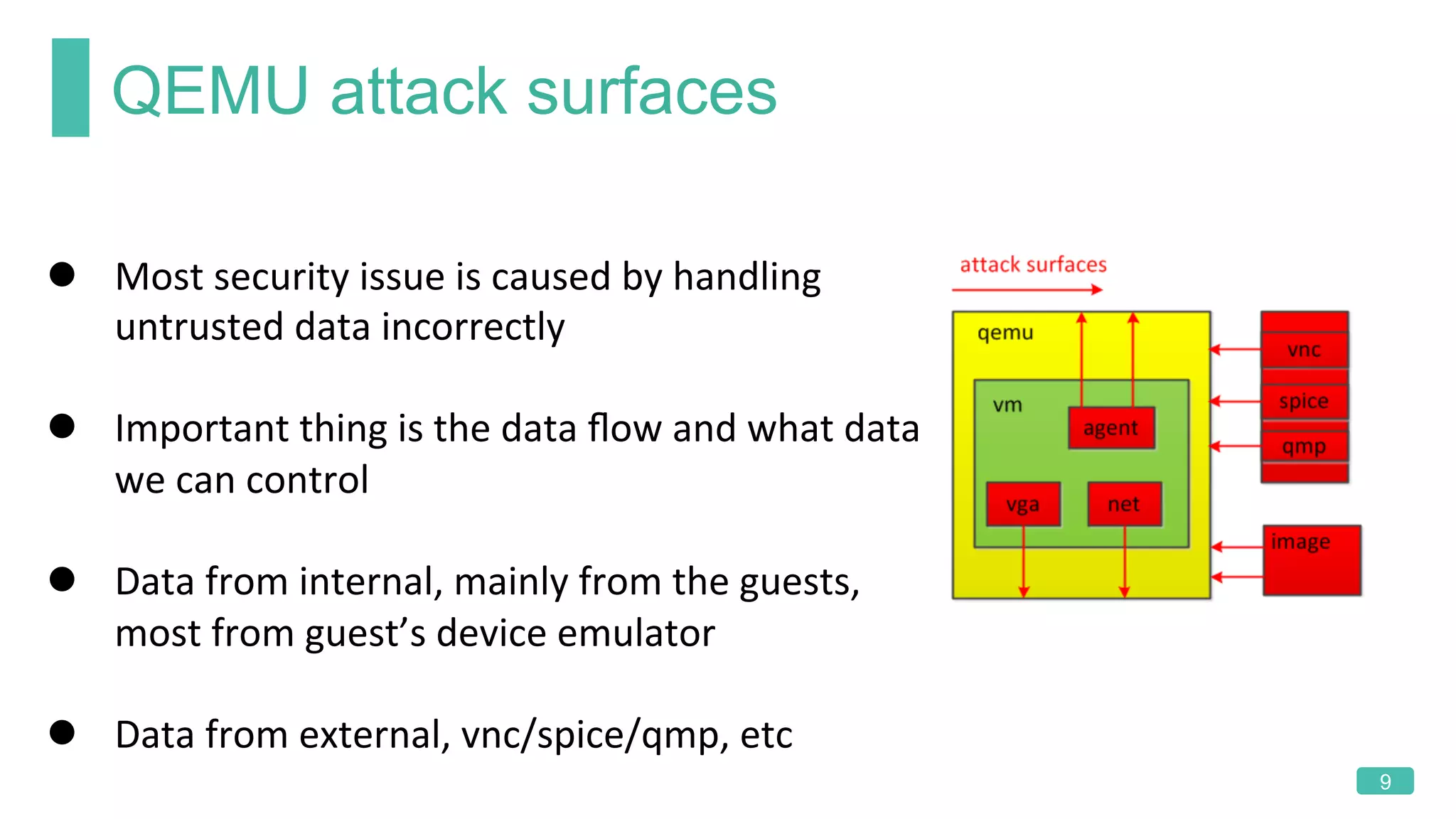
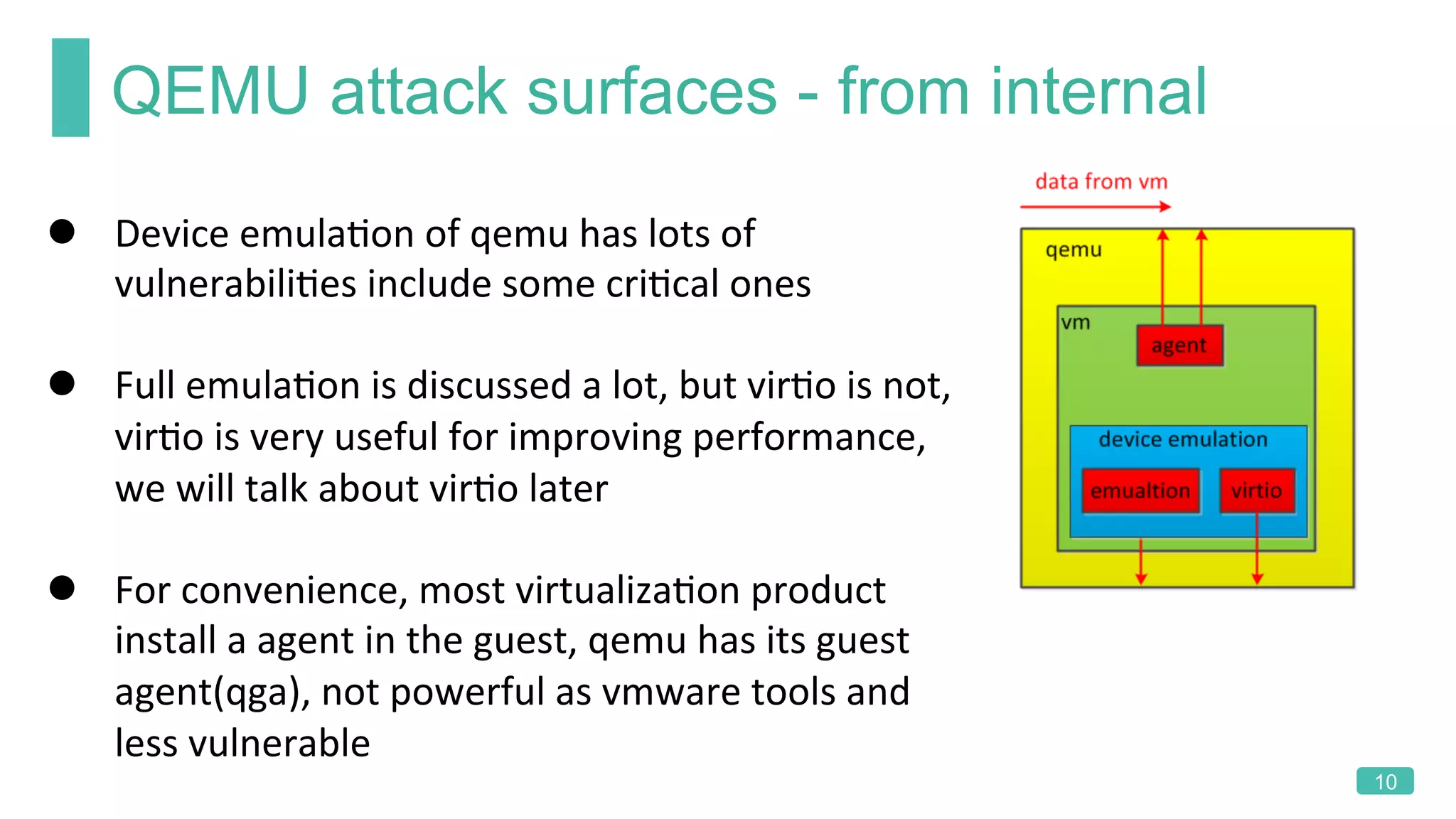
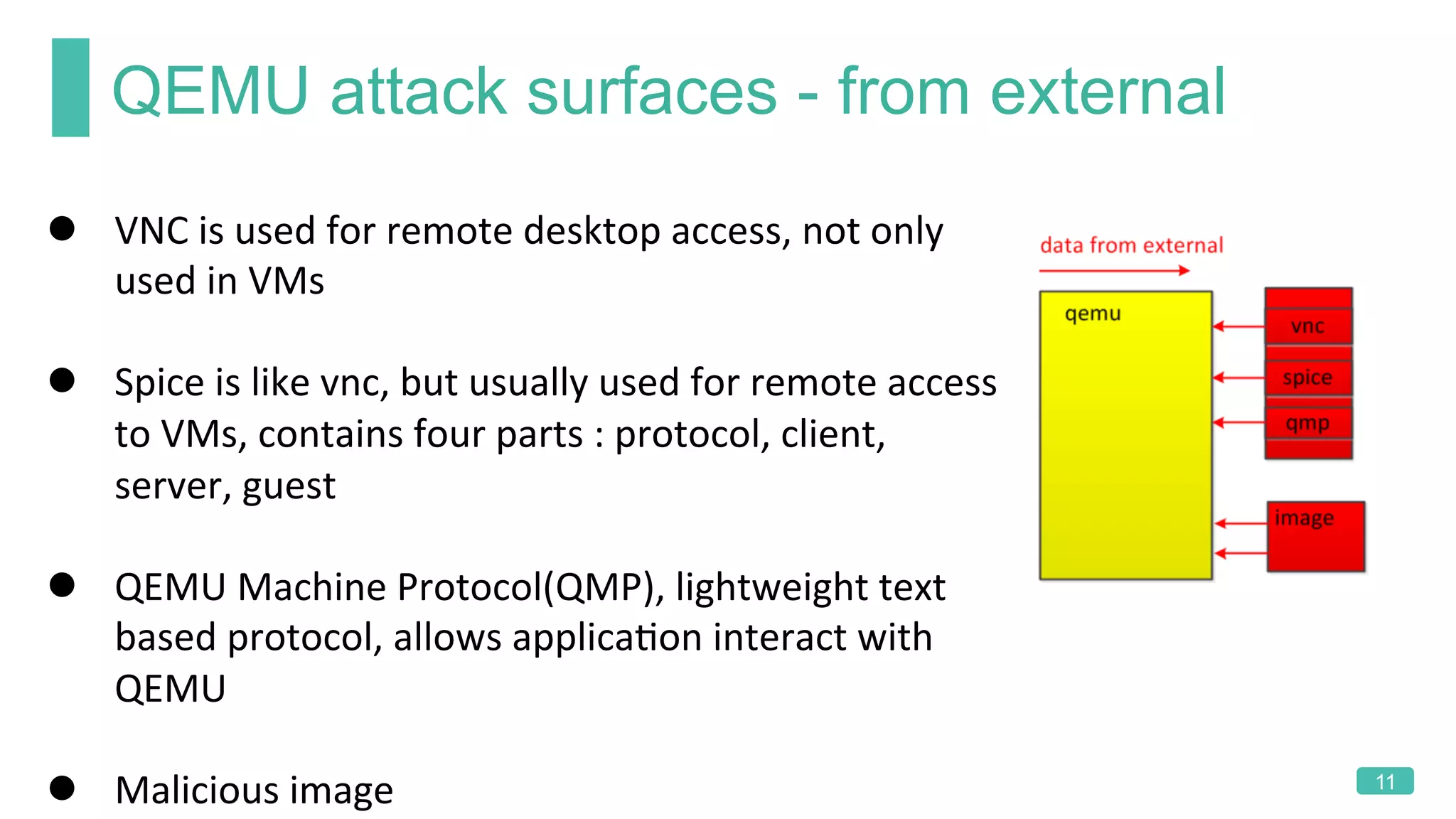
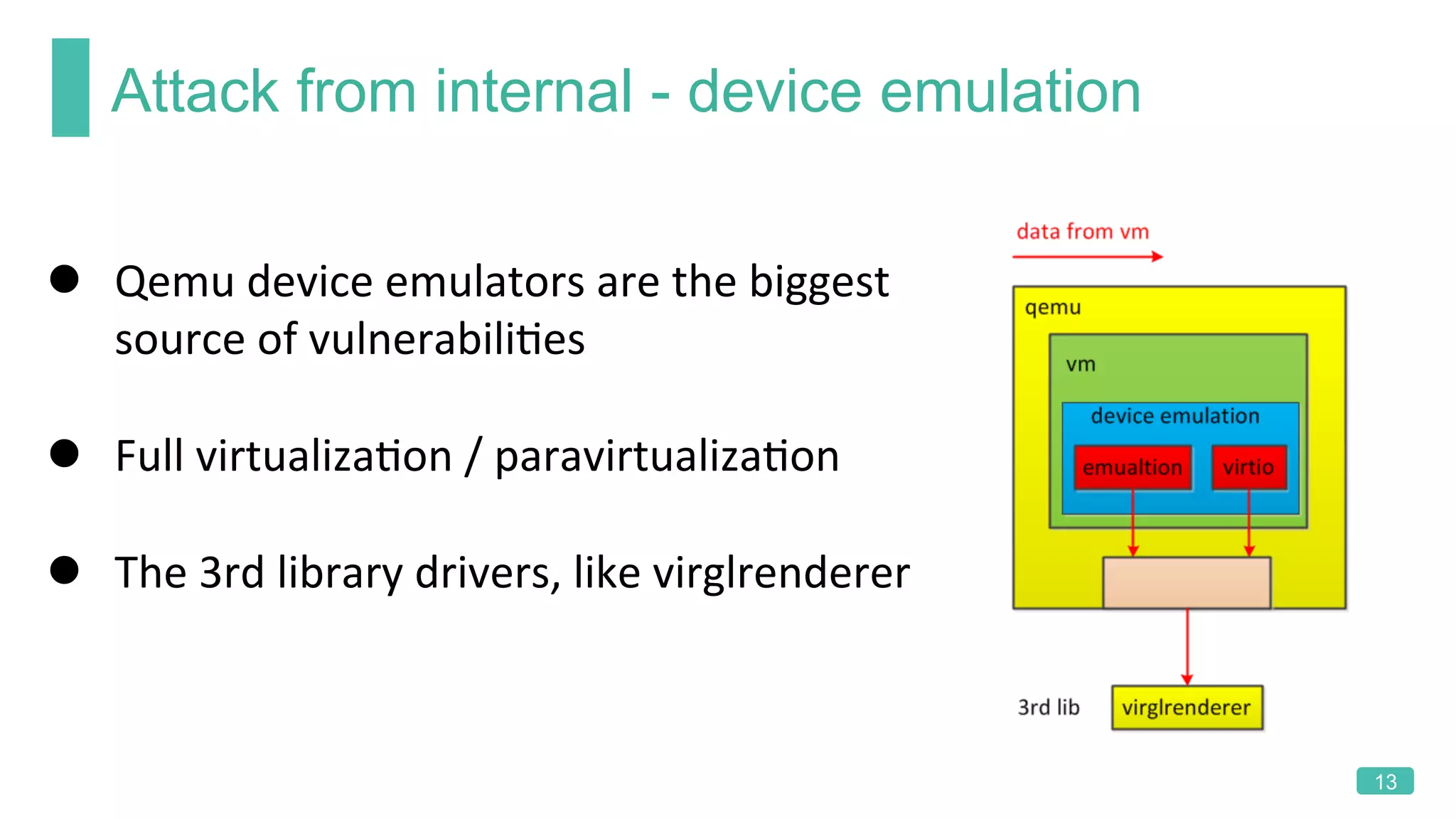
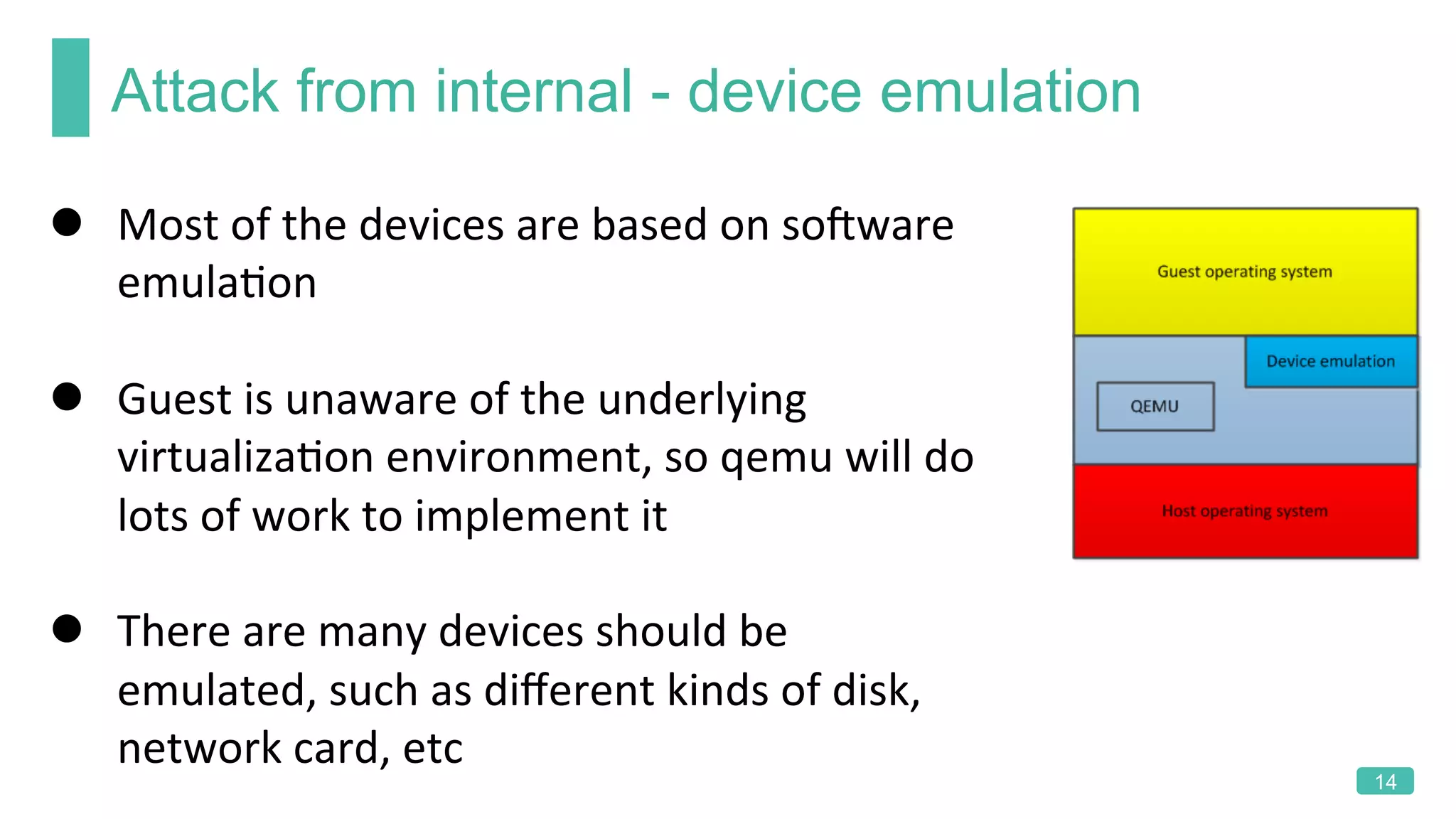
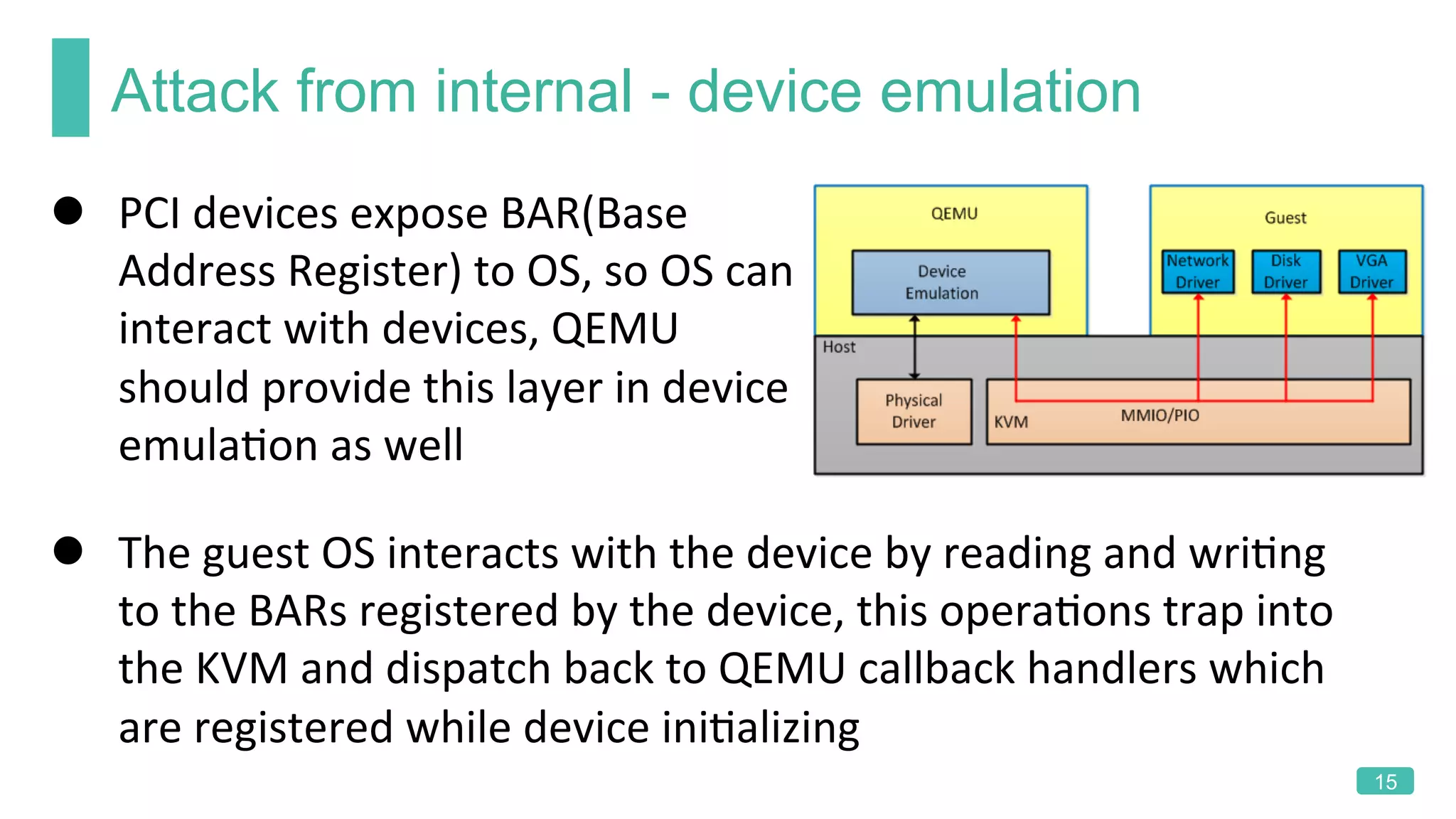
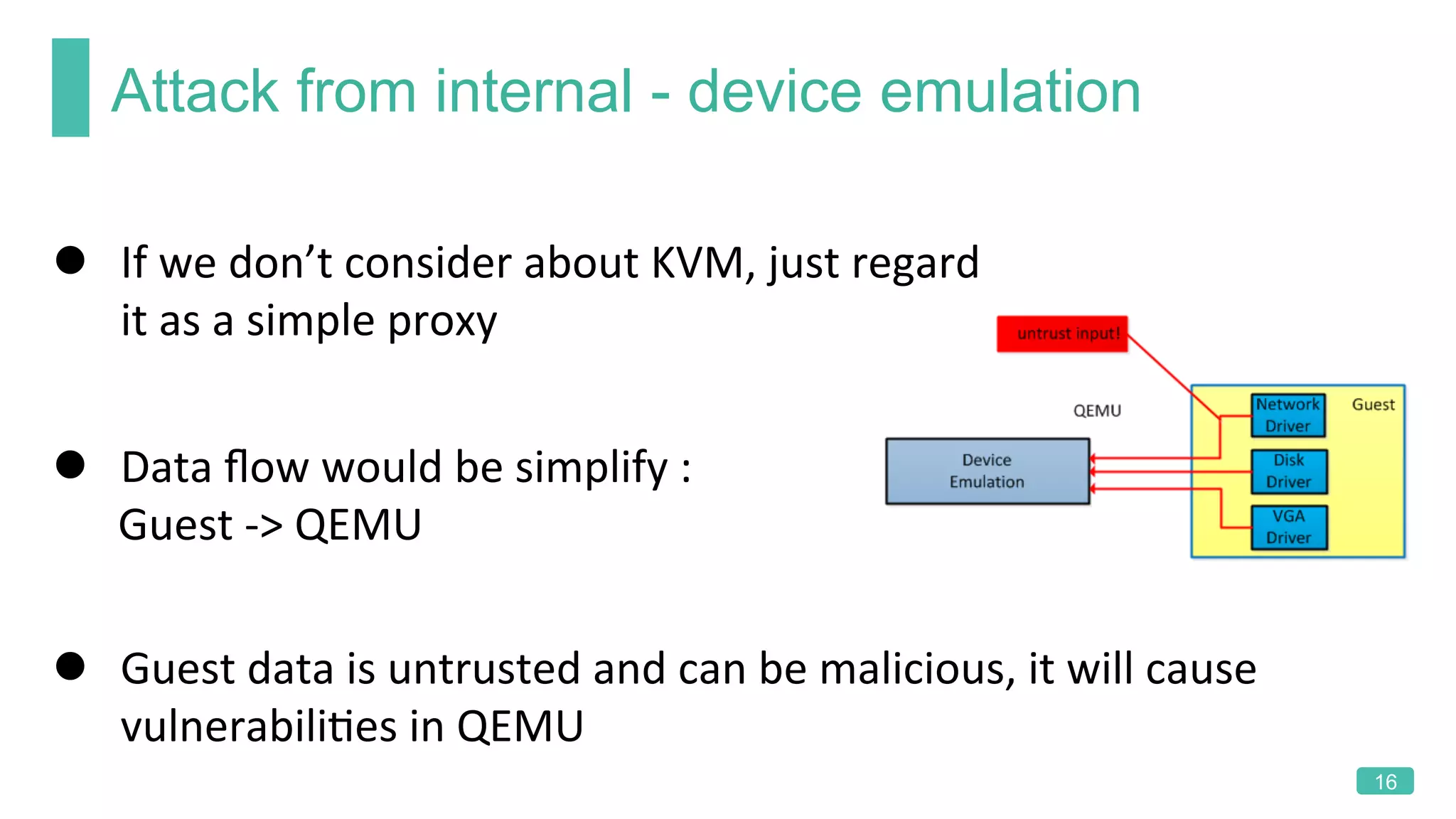
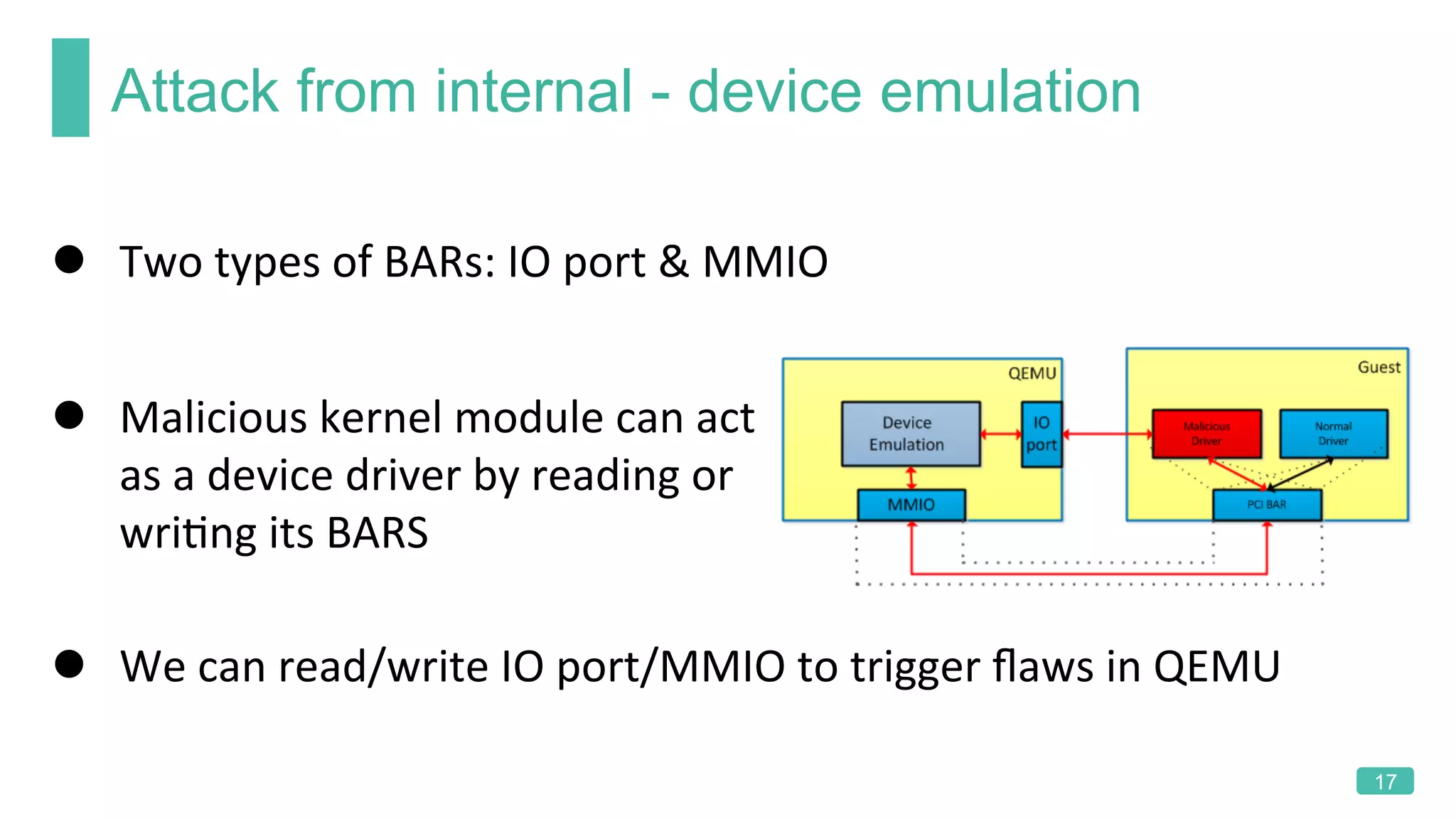
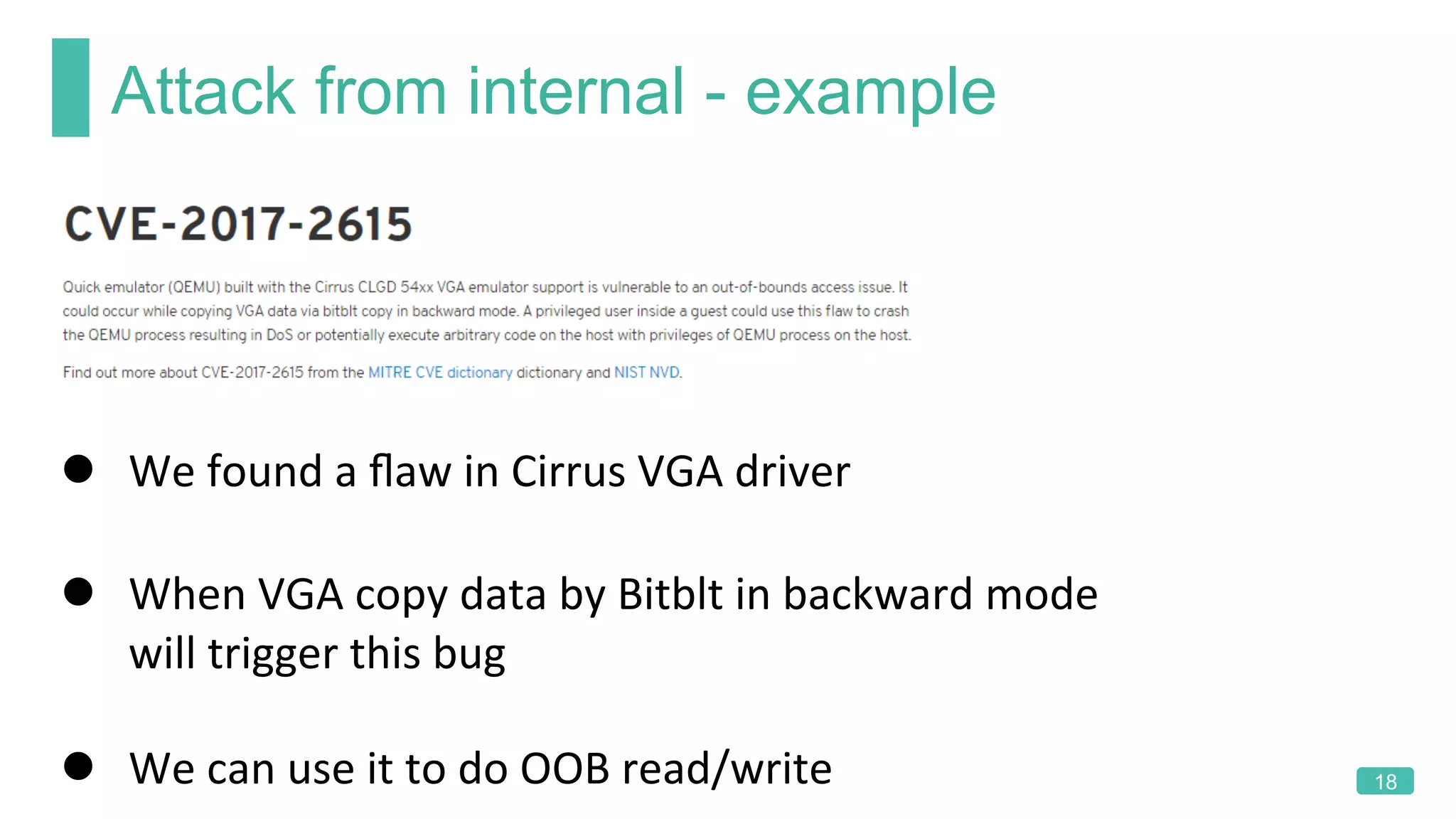
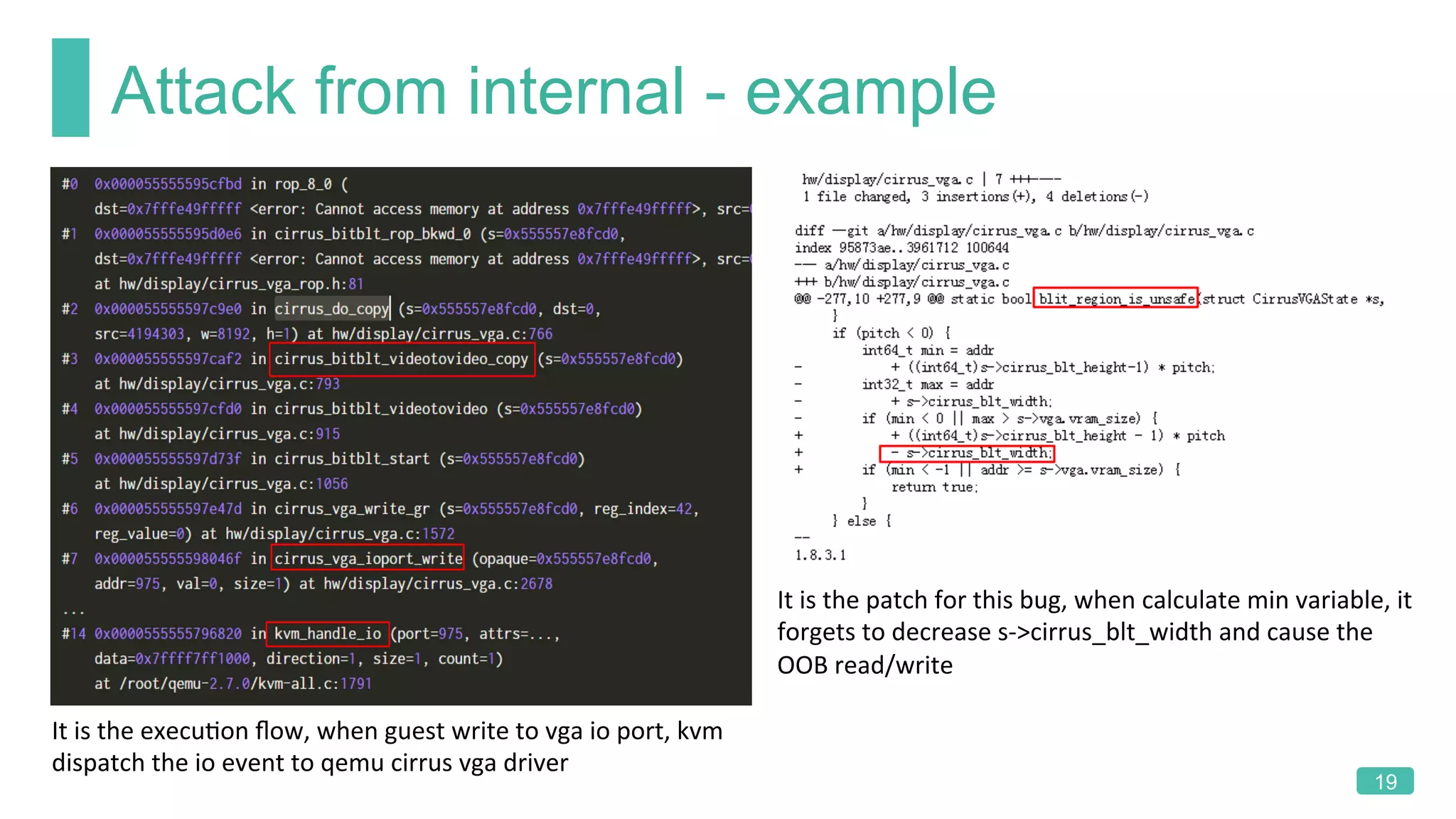
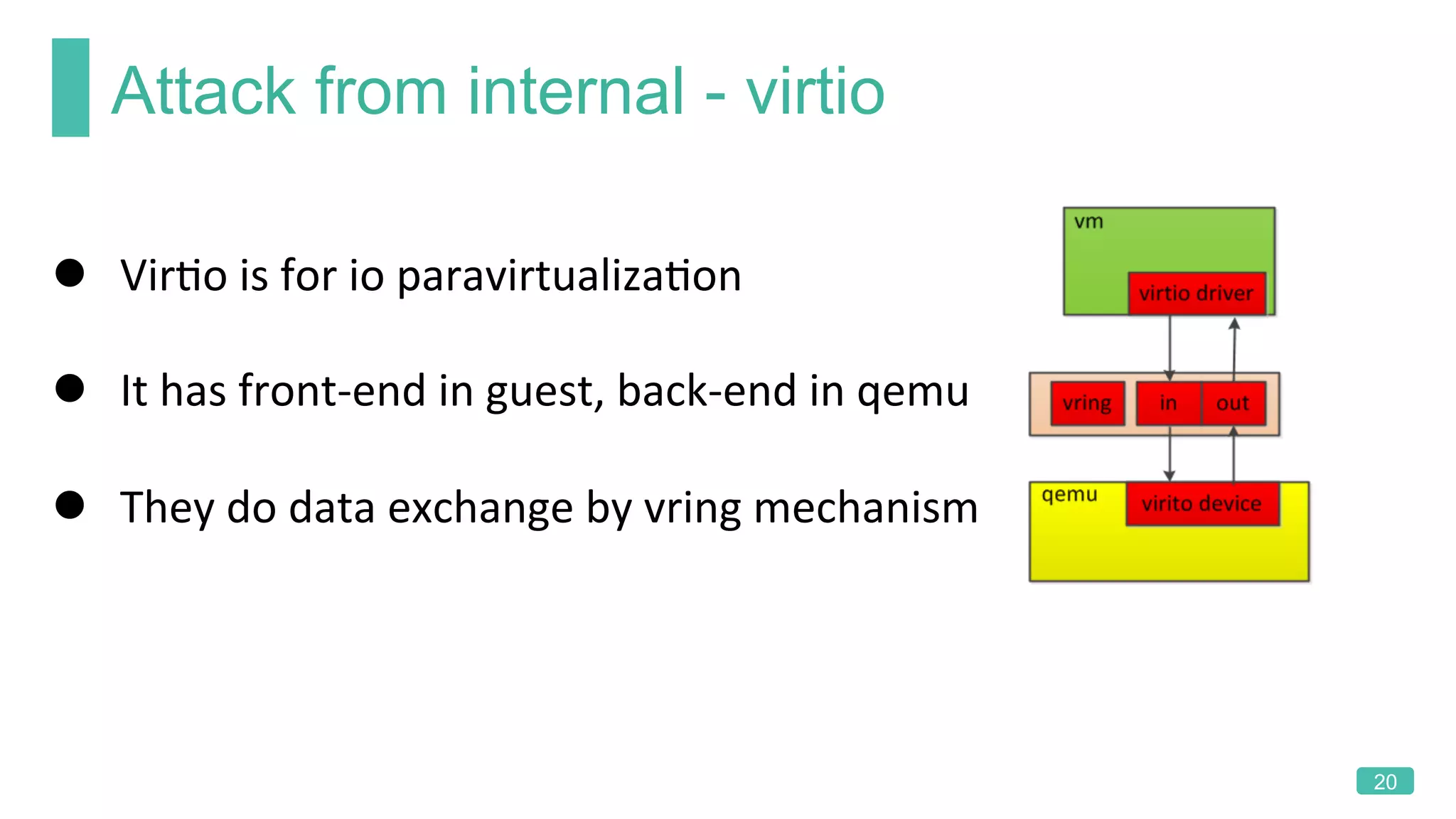
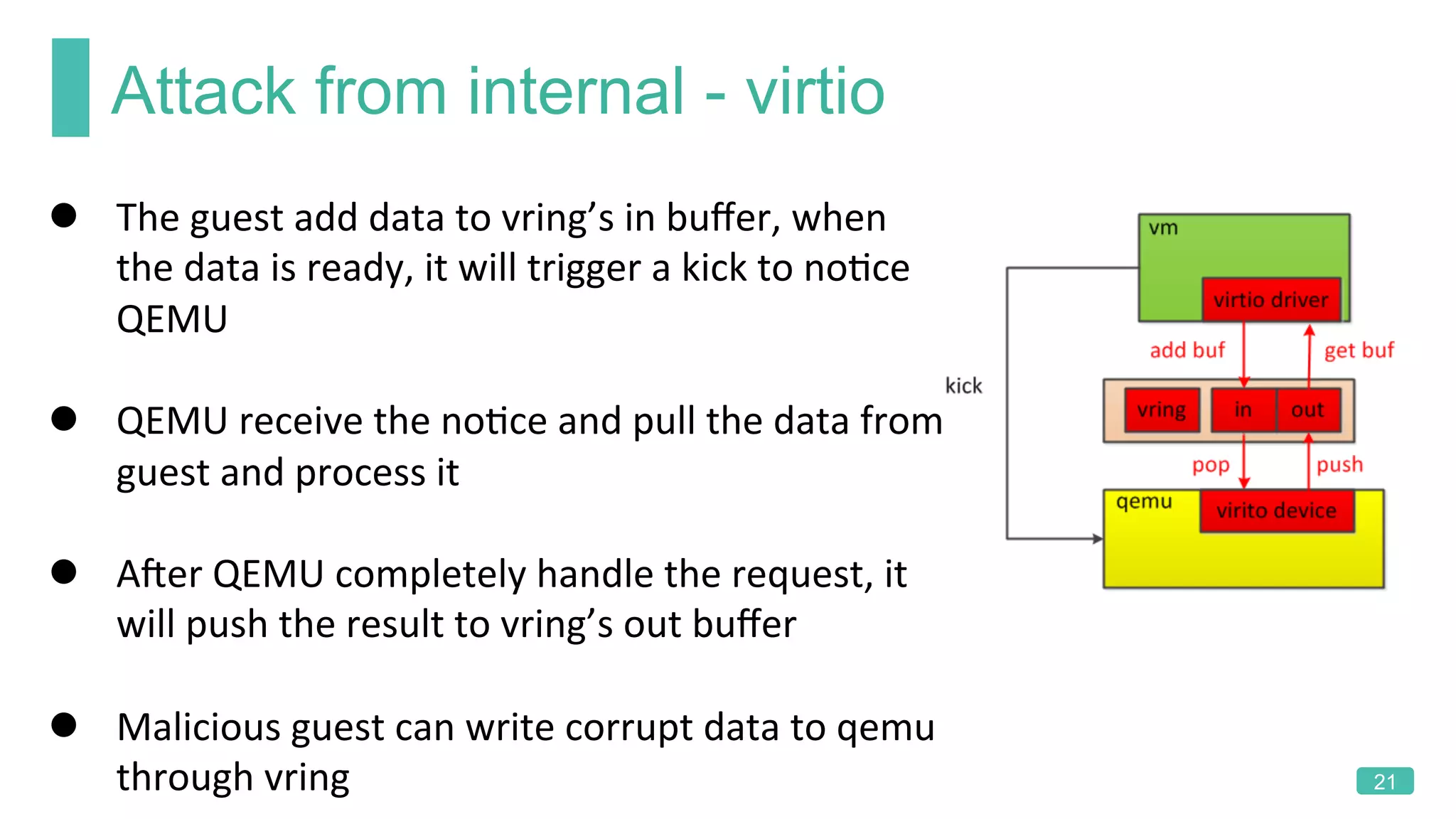
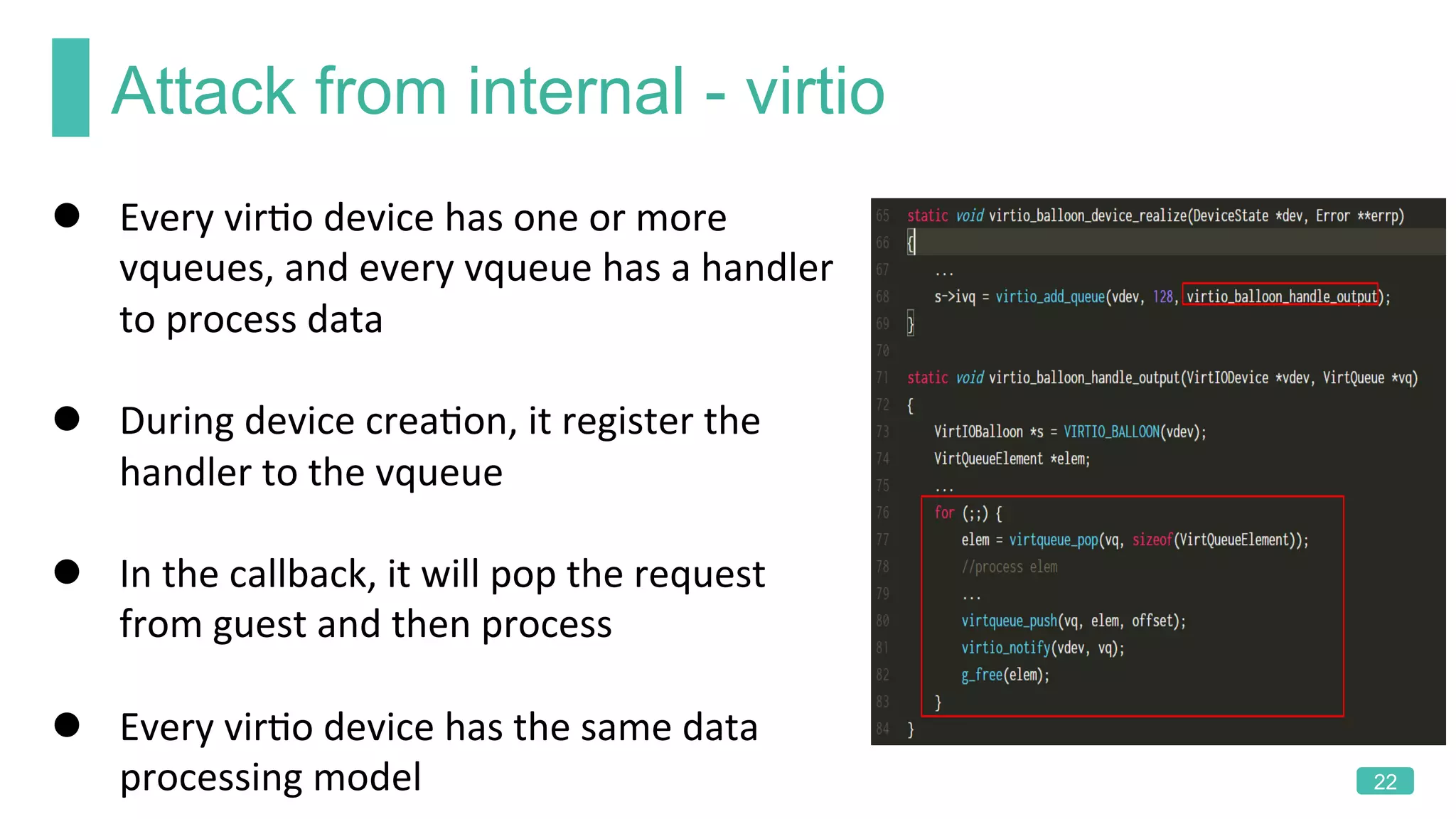
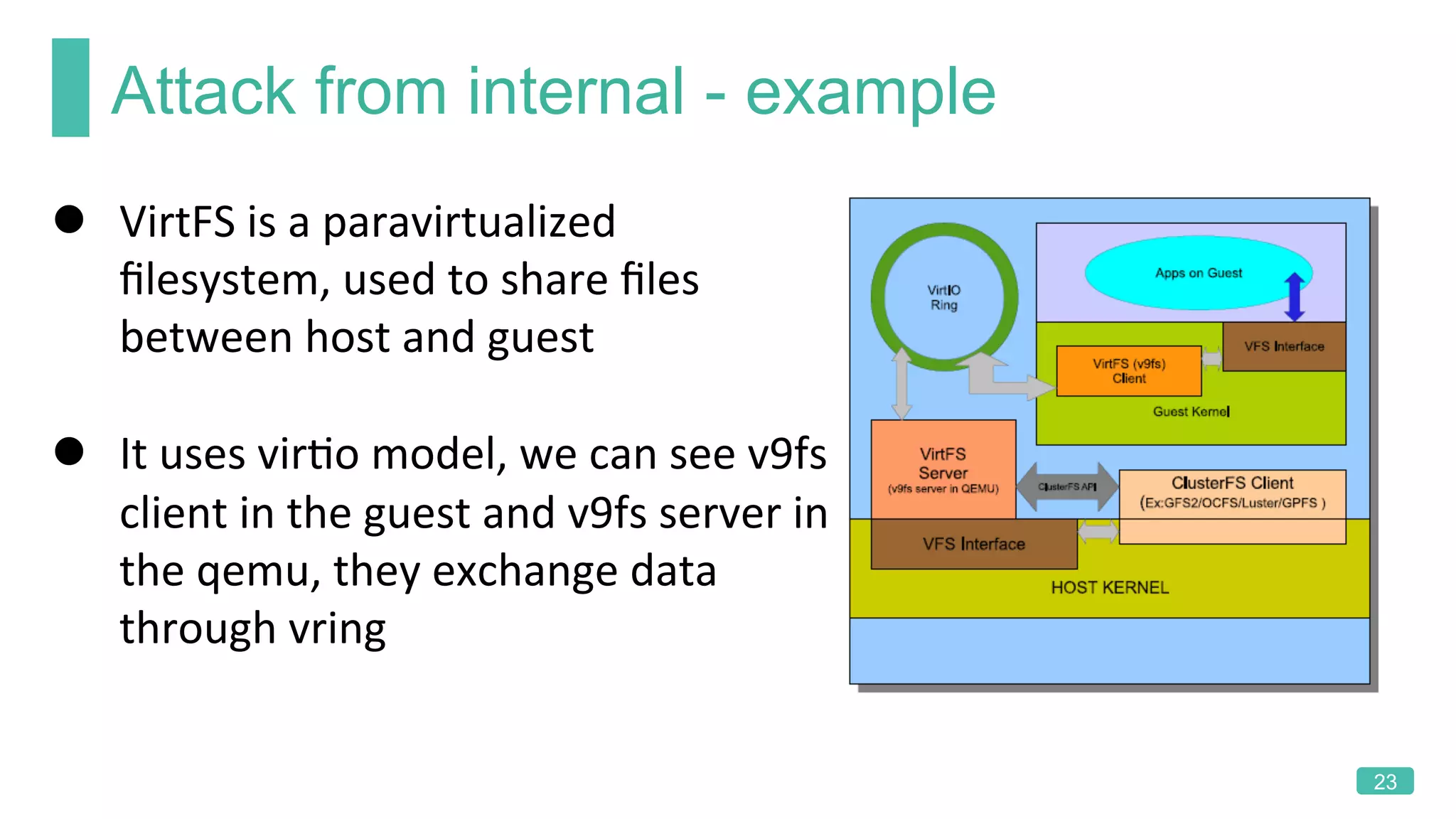
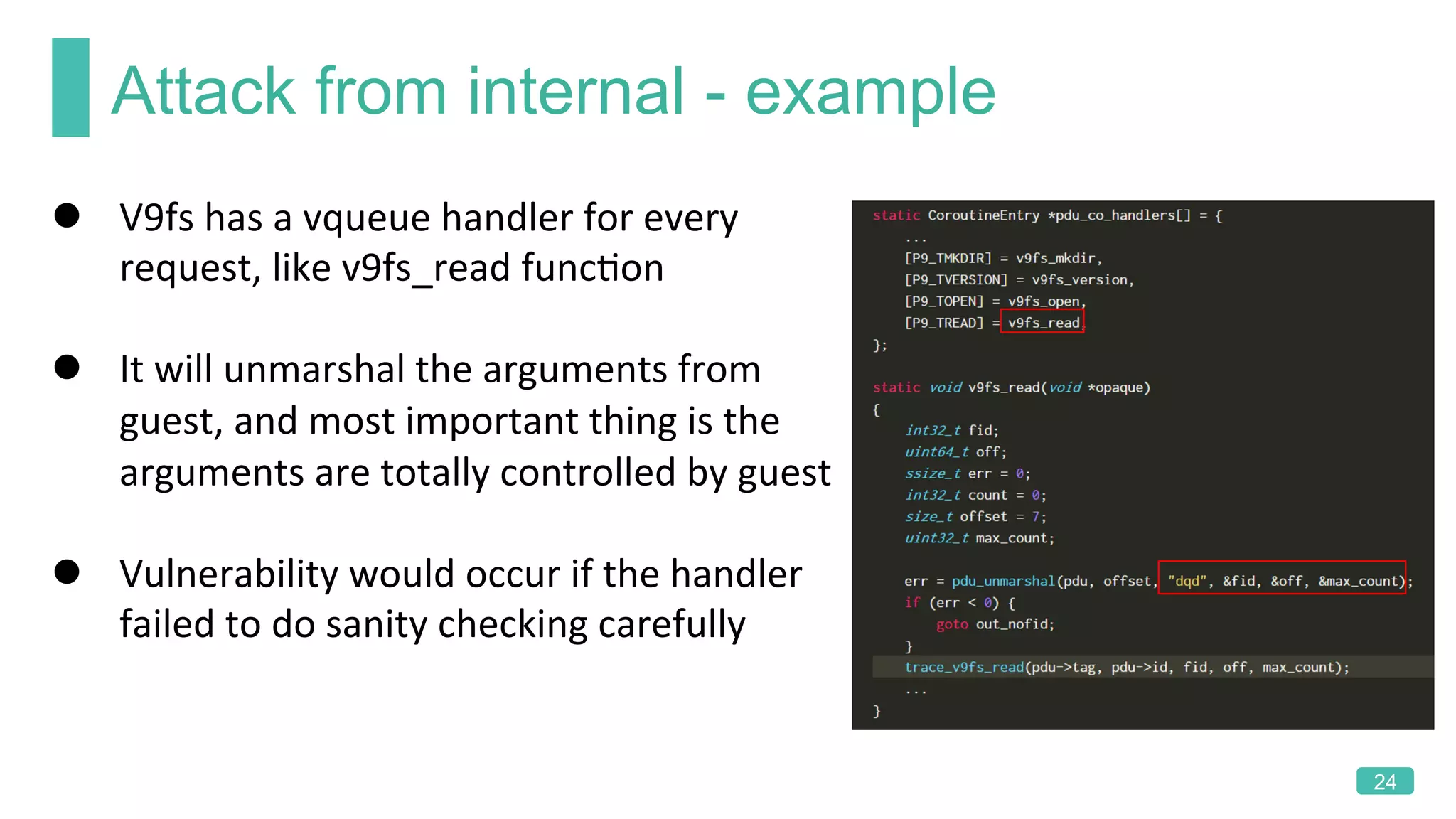
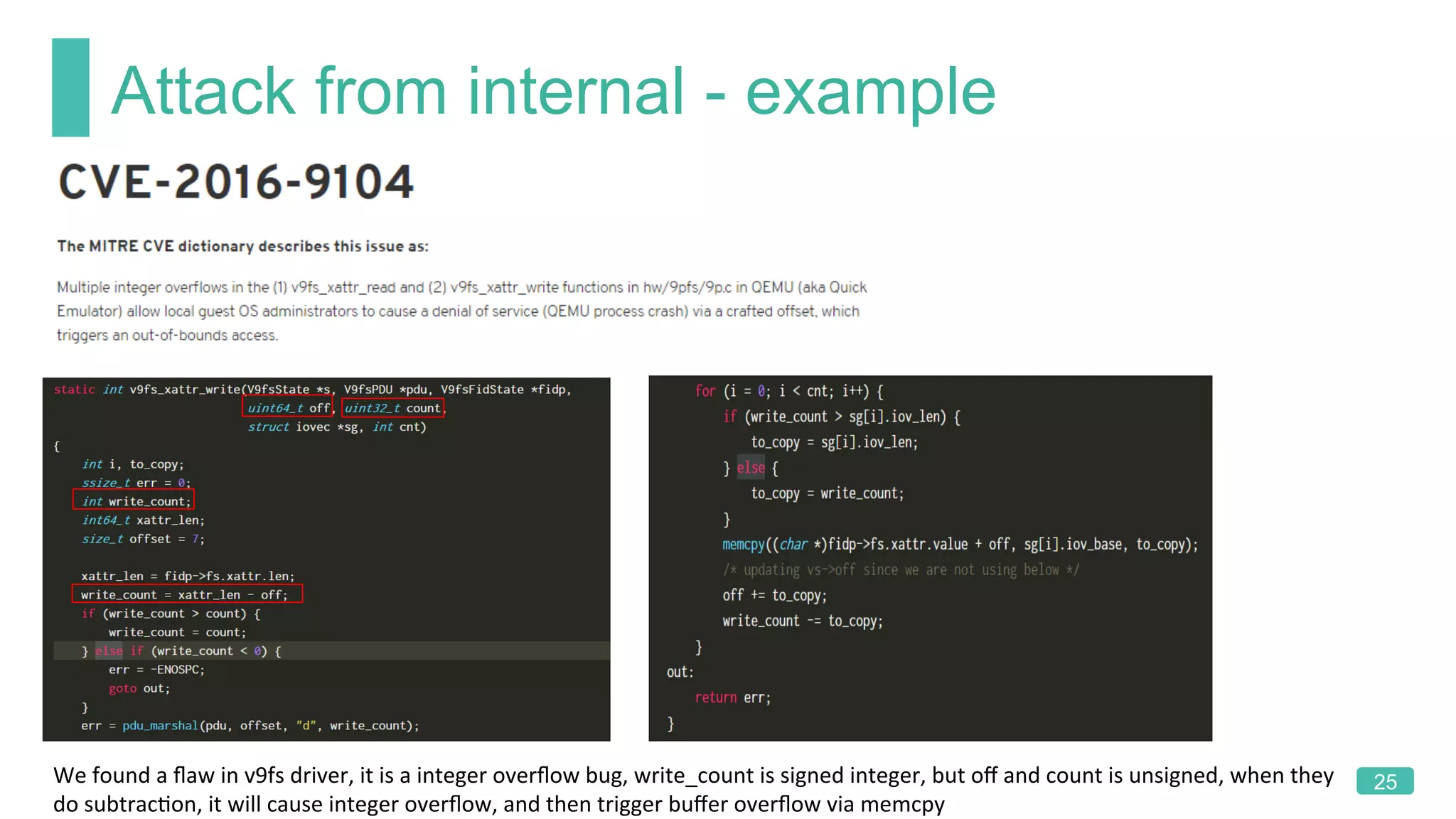
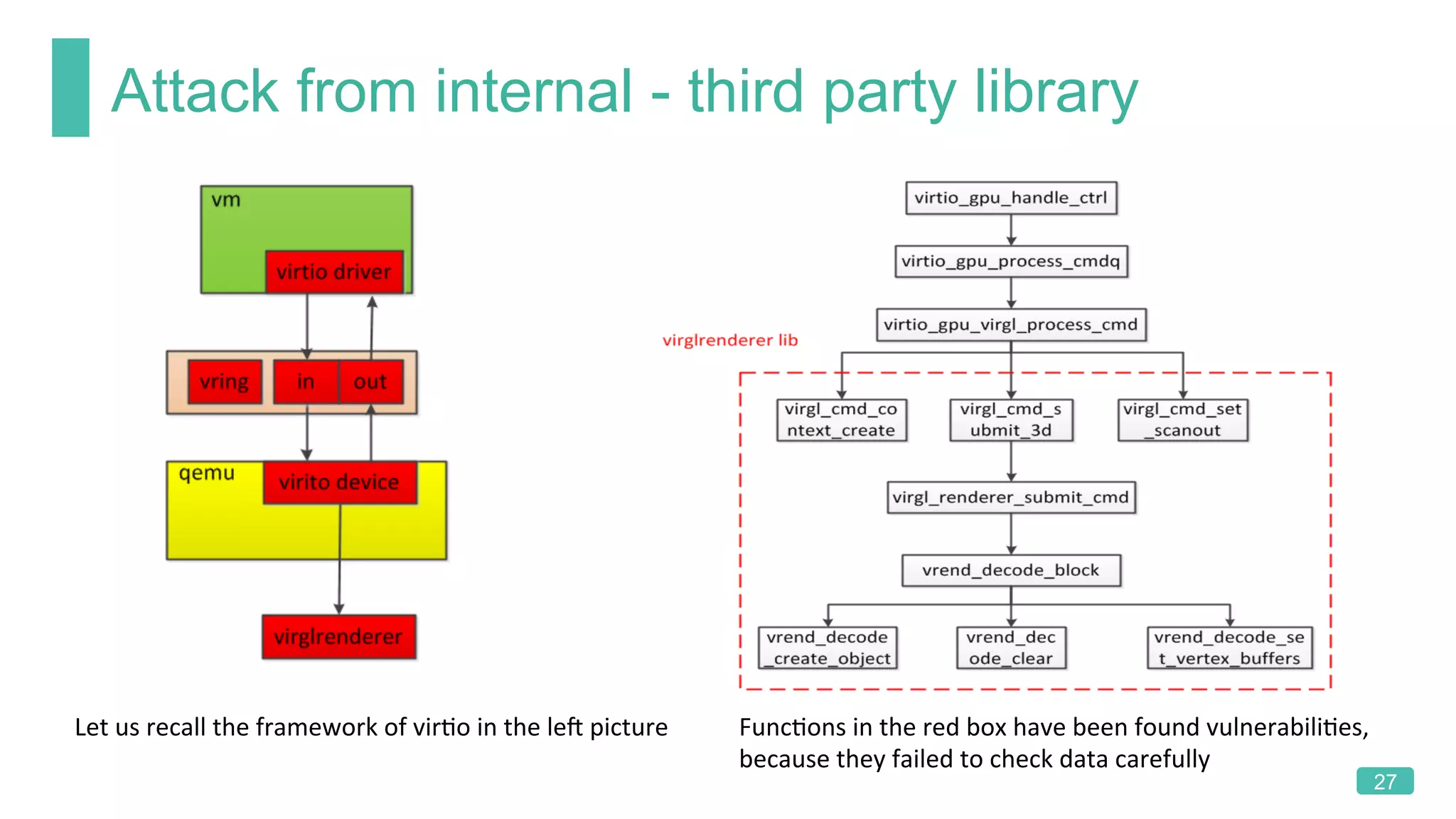
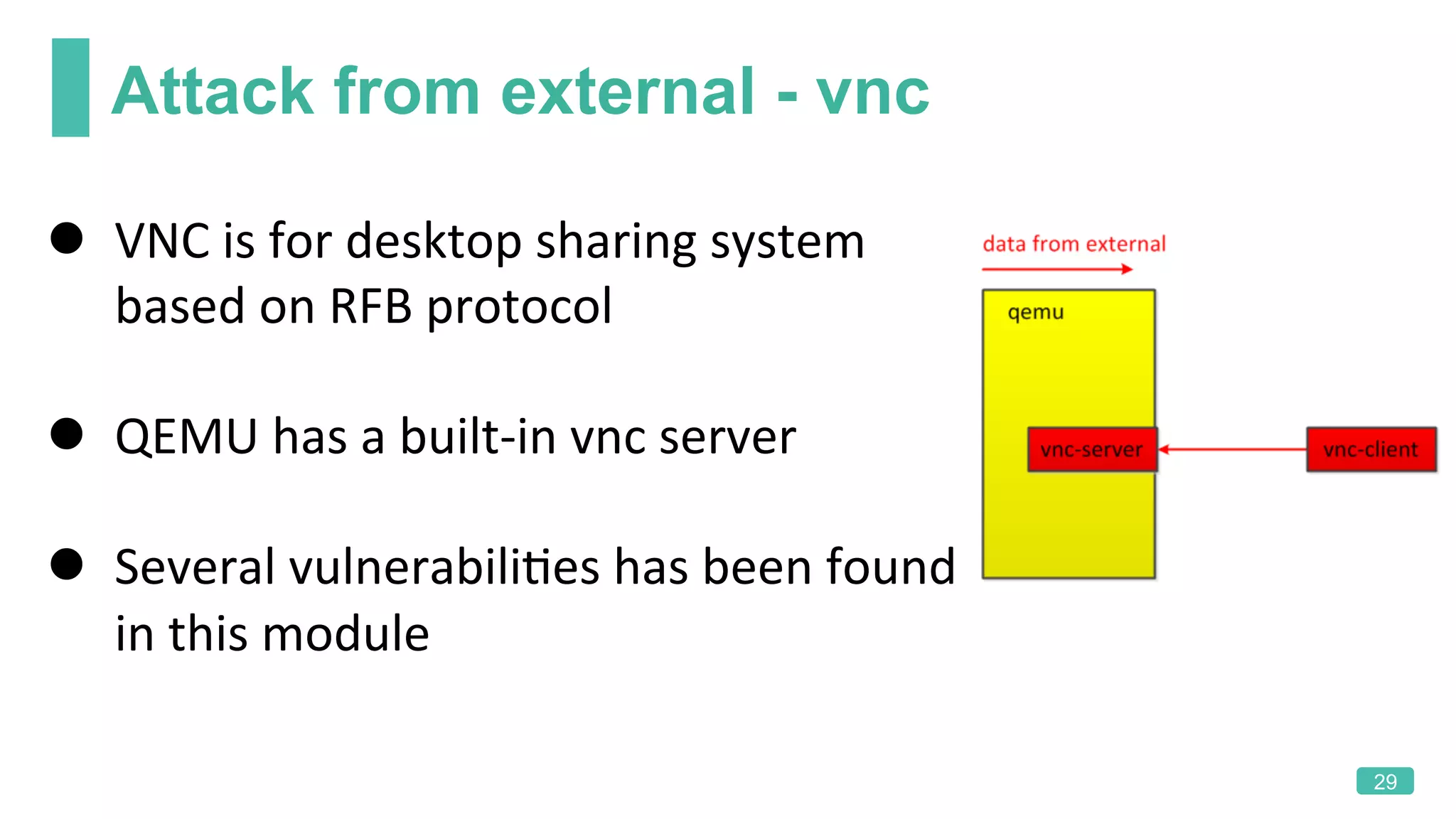
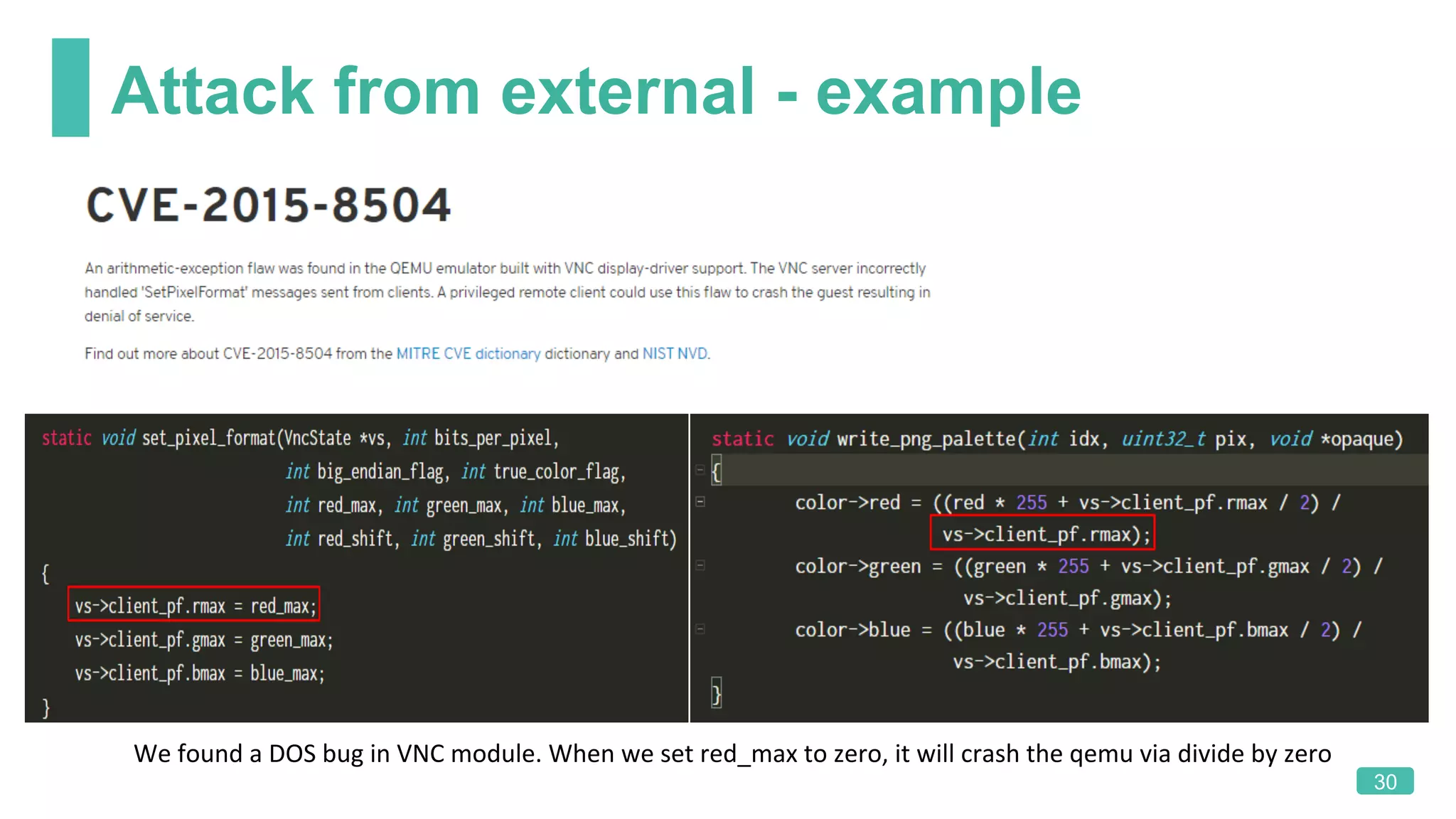
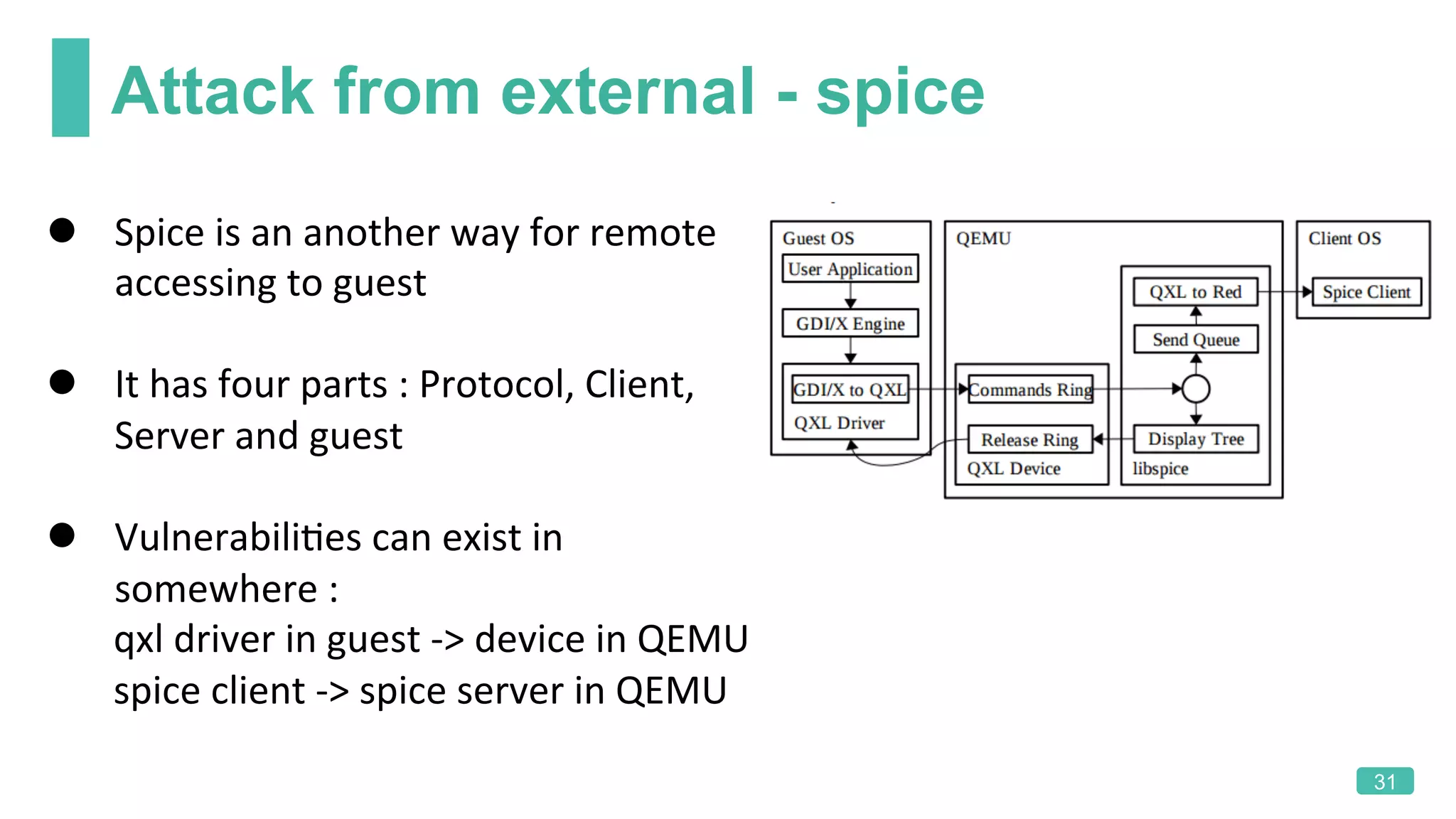
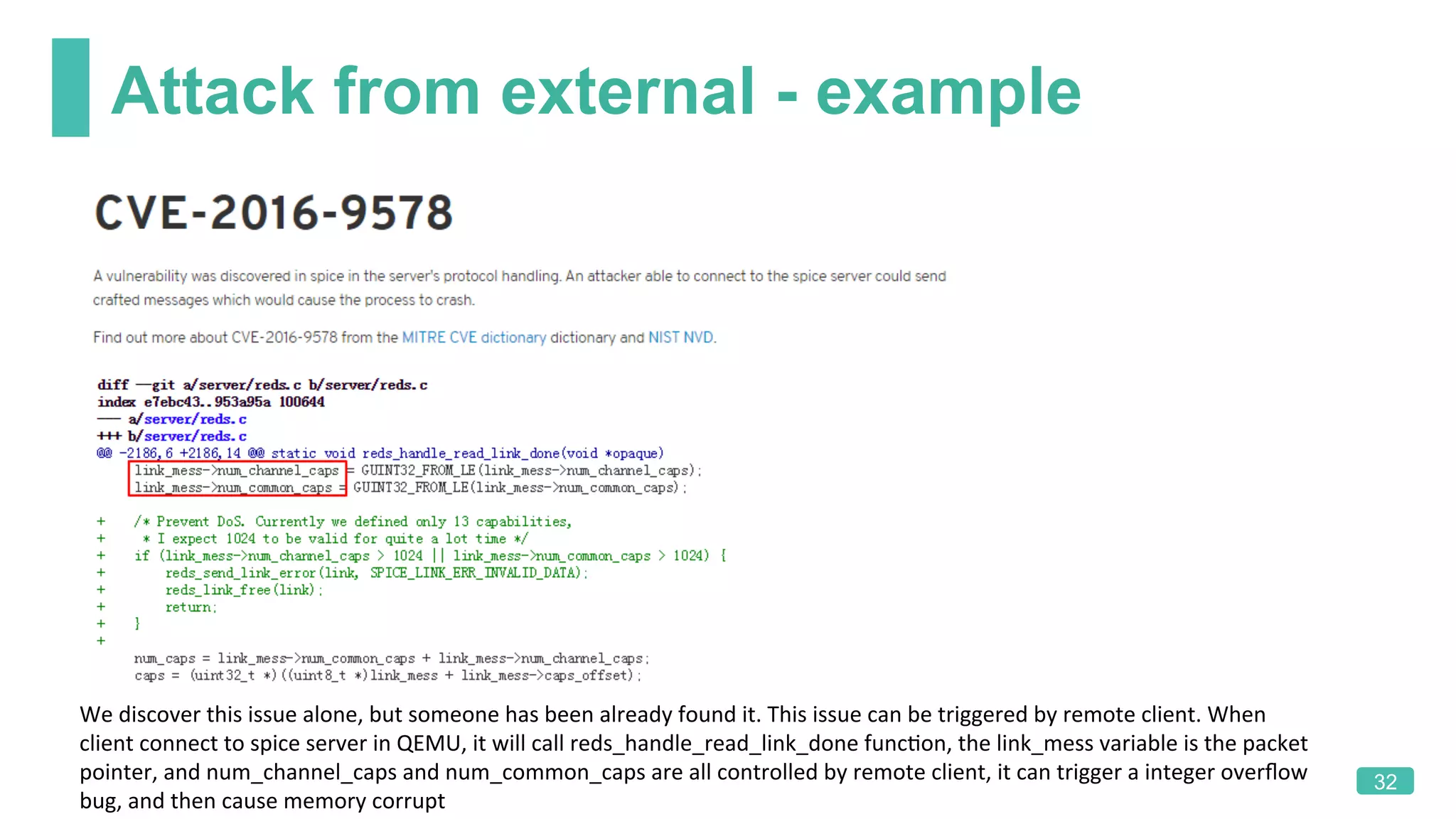
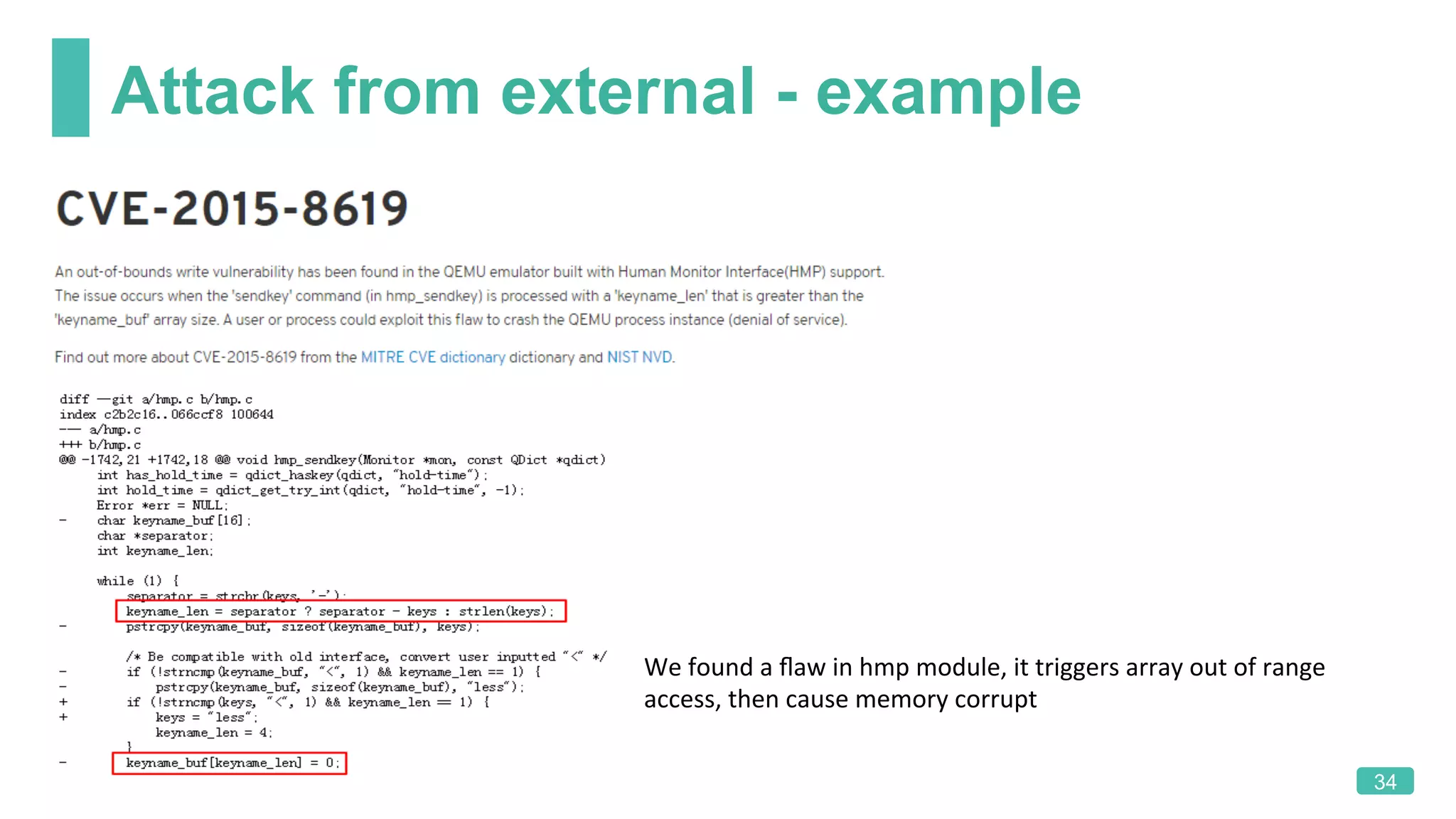
The document summarizes a presentation on analyzing the security of QEMU. It introduces QEMU and describes its main attack surfaces, including device emulation, virtio, third-party libraries, VNC, Spice, and QMP. Examples of vulnerabilities found in Cirrus VGA, virtio filesystem, virglrenderer library, VNC, and QMP are provided. The document concludes with thoughts on efficient security analysis, noting that combining in-depth knowledge with fuzzing is most effective for finding bugs in complex software like QEMU.