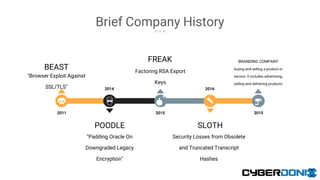
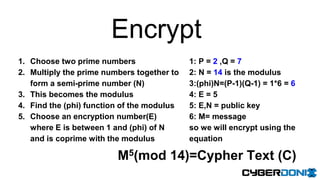
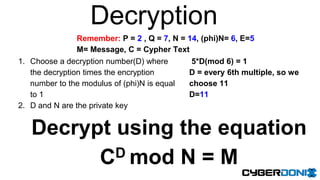
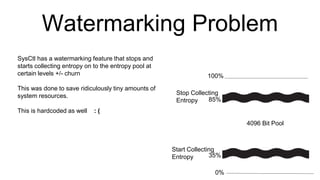
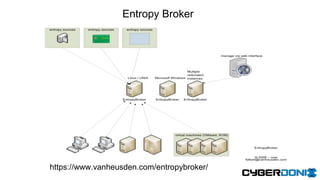
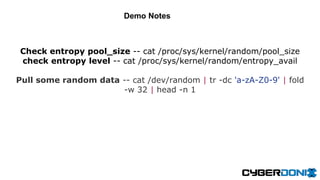
This document discusses an entropy downgrade attack and provides solutions to strengthen a system's entropy and random number generation. It explains that computers have limited entropy for generating strong cryptographic keys. An attacker can force a system to generate keys using less entropy, making the keys easier to crack. The document recommends increasing the entropy pool size, optimizing entropy collection, using hardware entropy sources, and caching previously generated strong primes to strengthen a system against this attack. It provides code examples and tools to help implement these solutions.