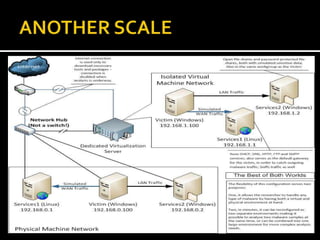
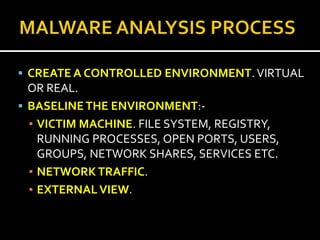
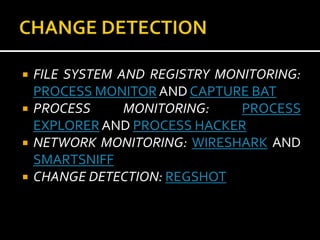
The document provides a comprehensive overview of malware analysis, including theoretical frameworks and practical case studies. It discusses methodologies such as static and behavioral analysis, the importance of virtualization, and the use of specific tools and environments for effective malware research. The material emphasizes the complexities of modern malware and the necessity for automation and careful analysis to keep pace with evolving threats.

























![ THE OPTIONS OFFERED IN NDIFF INCLUDE:
ndiff [-b|-baseline <file-or-:tag>] [-o|-observed <file-or-:tag>]
[-op|-output-ports <ocufx>] [-of|-output-hosts <nmc>]
[-fmt|-format <terse | minimal | verbose | machine | html | htmle>]
NDIFF OUTPUT MAY BE REDIRECTED TO A WEB PAGE:
ndiff –b base-line.txt –o tested.txt –fmt machine | ndiff2html >
differences.html
THE OUTPUT FILE, “DIFFERENCES.HTML”, MAY BE DISPLAYED
IN A WEB BROWSER. THIS WILL SEPARATE HOSTS INTO THREE
MAIN CATEGORIES:
o NEW HOSTS,
o MISSING HOSTS, AND
o CHANGED HOSTS.](https://image.slidesharecdn.com/malwareanalysis-anoverview-100703073937-phpapp01/85/Malware-Analysis-by-PP-Singh-31-320.jpg)