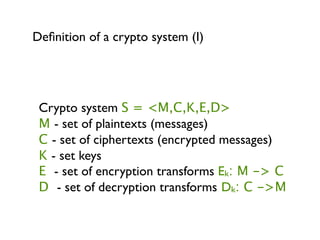
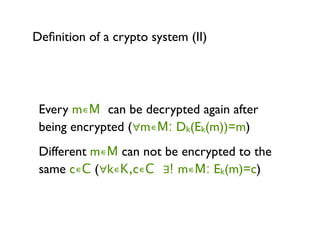
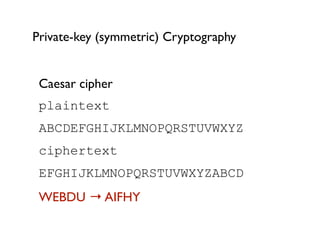
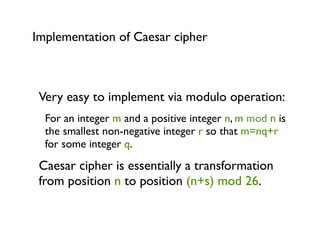
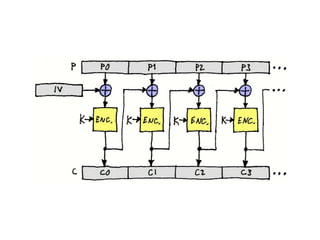
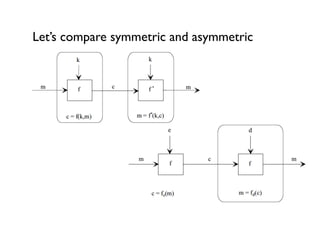
Cryptography for Developers provides an overview of cryptography concepts for developers. It defines cryptography as the encryption of plaintext into ciphertext and back again. It discusses symmetric and asymmetric cryptography, including examples like the Caesar cipher. It covers hashing of passwords for storage and discusses popular algorithms like MD5 and SHA-2. The document also summarizes public key cryptography techniques like RSA and references materials for further learning.