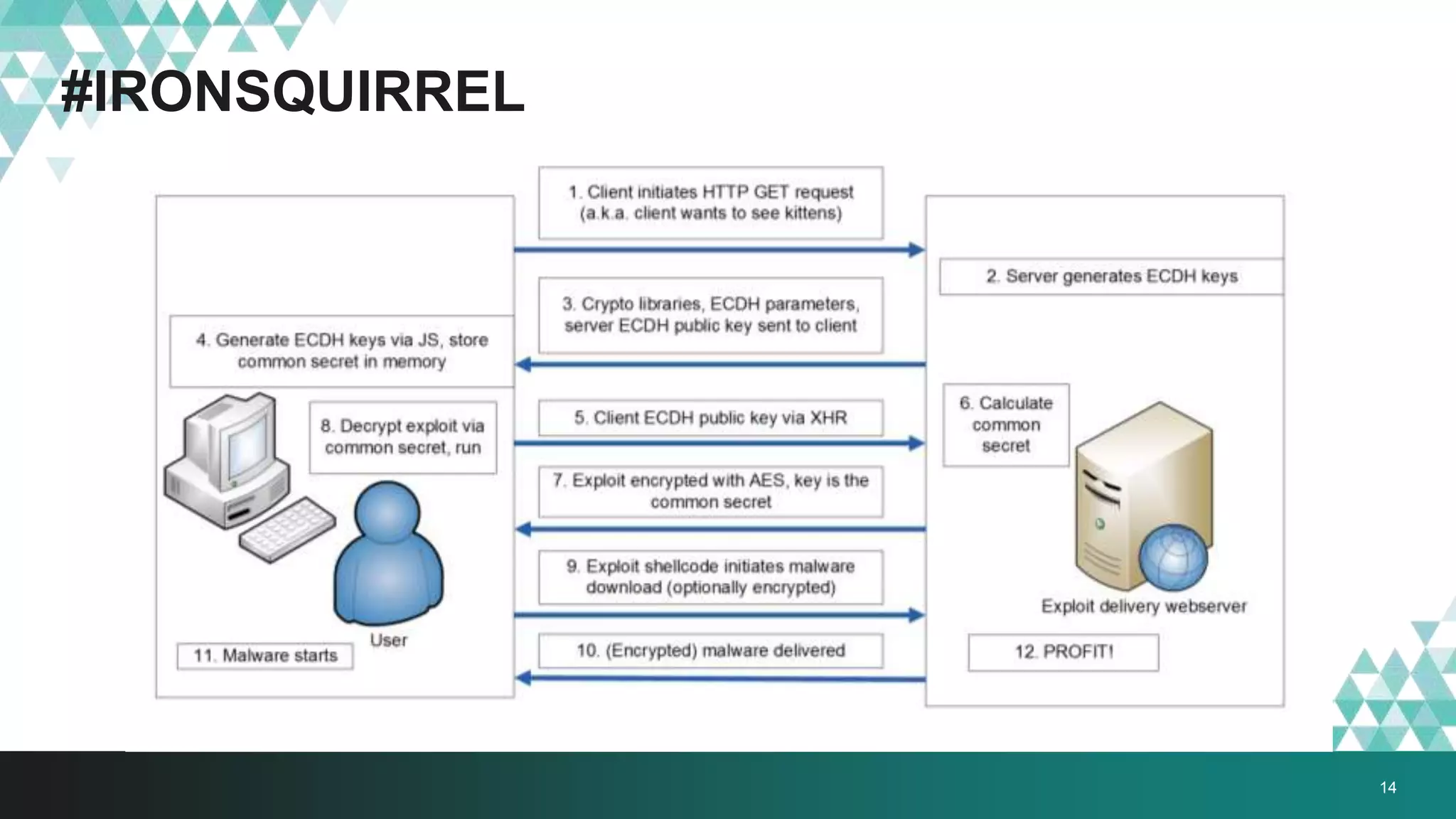
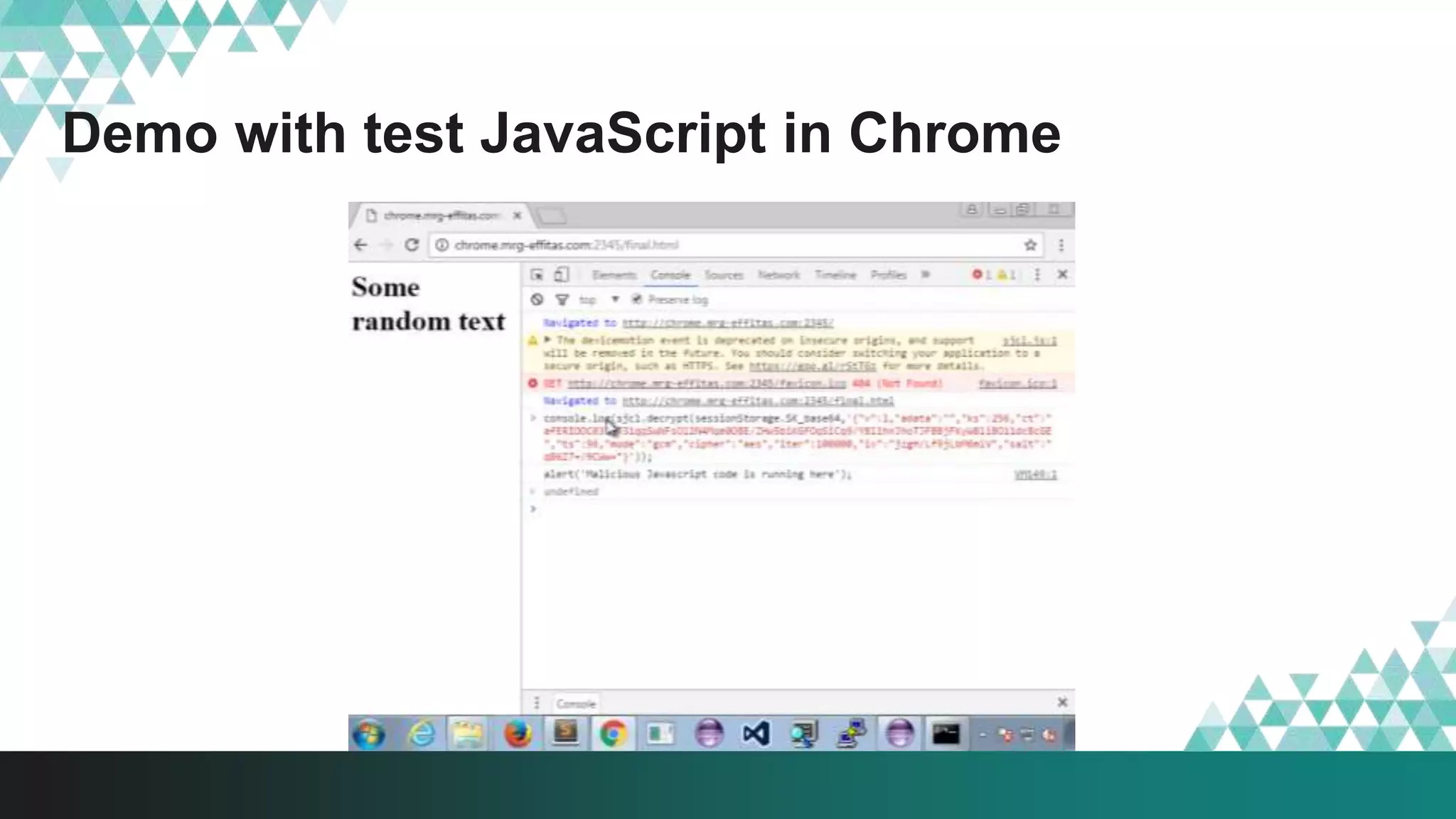
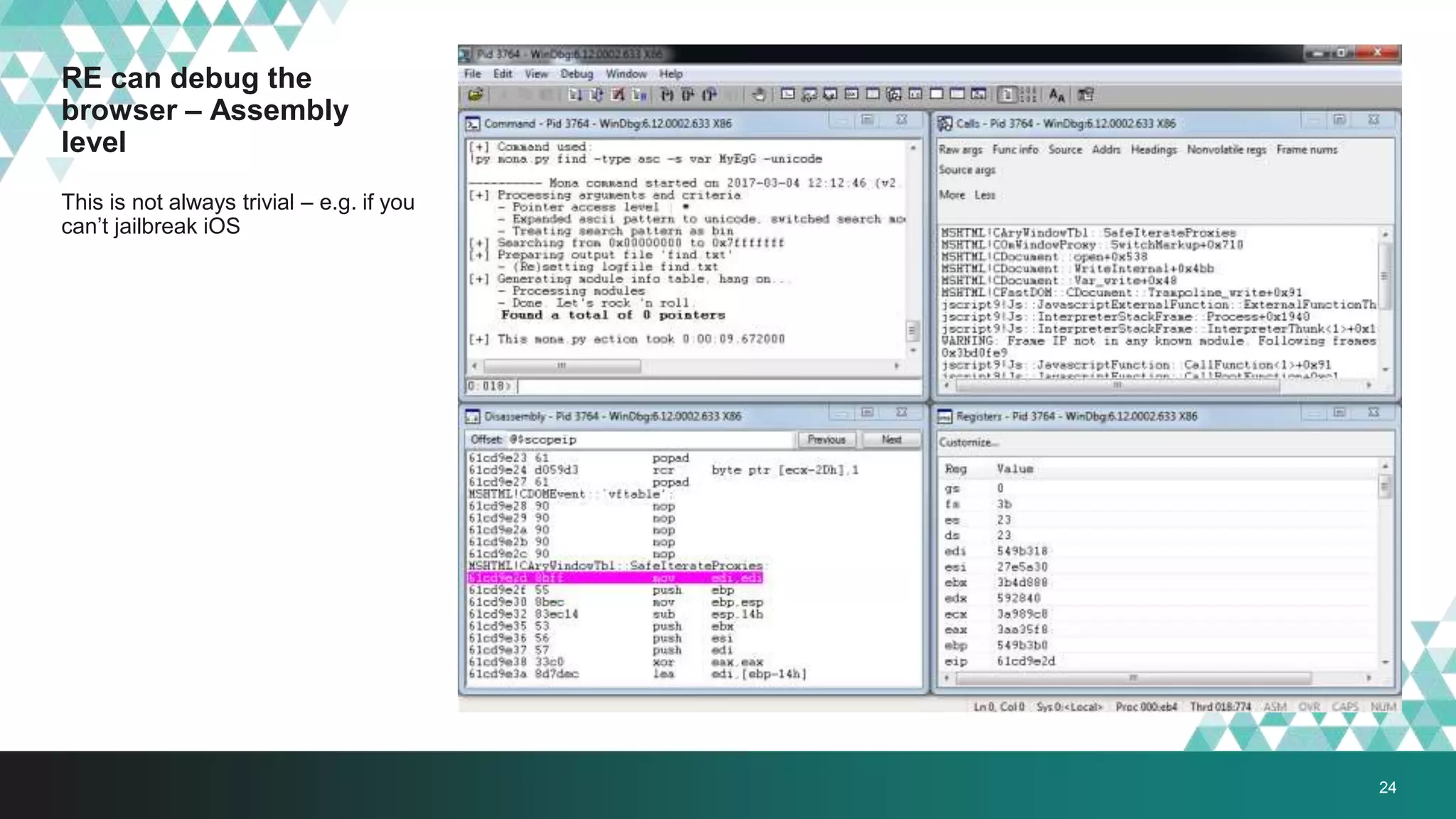
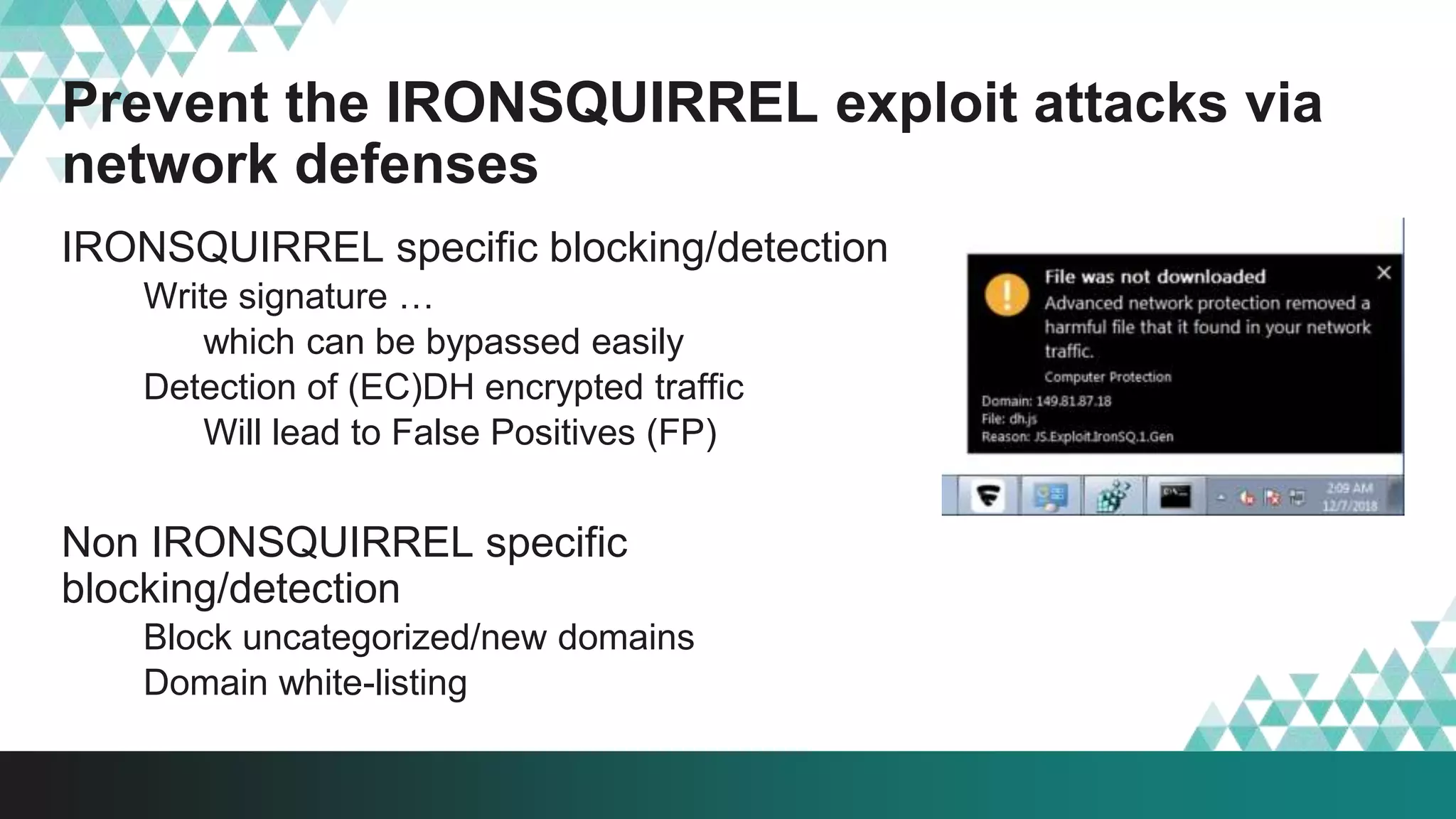
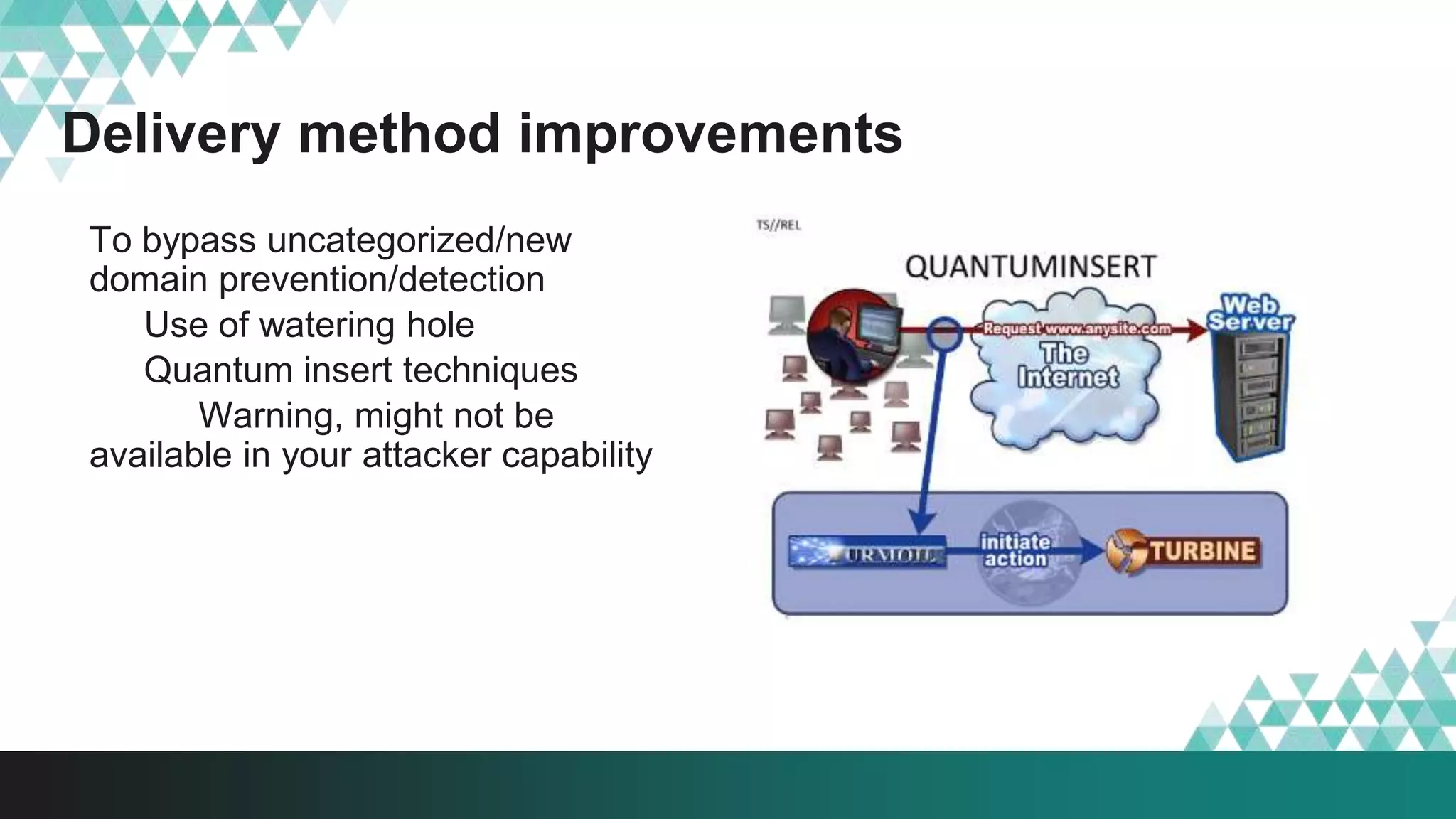
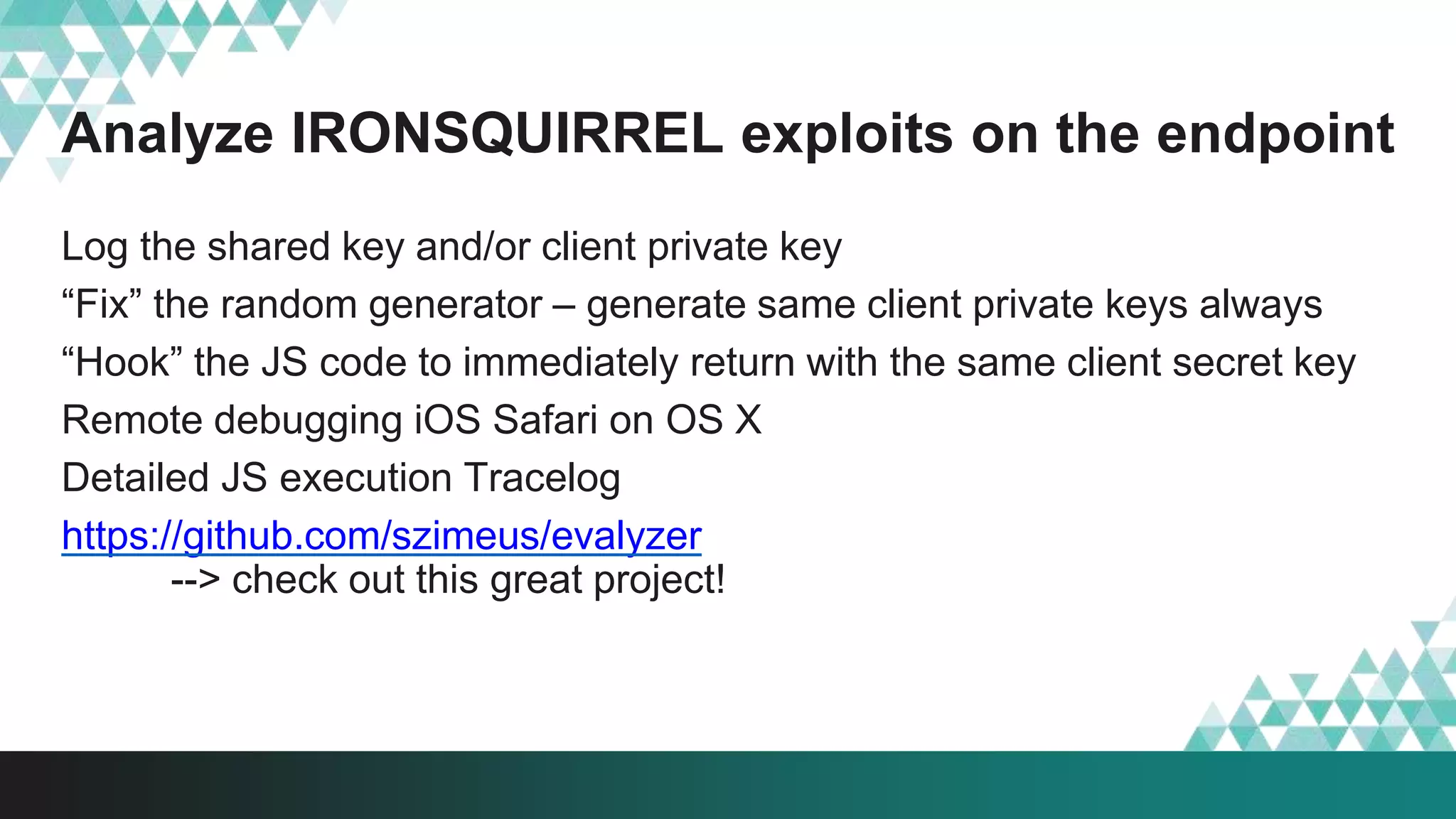
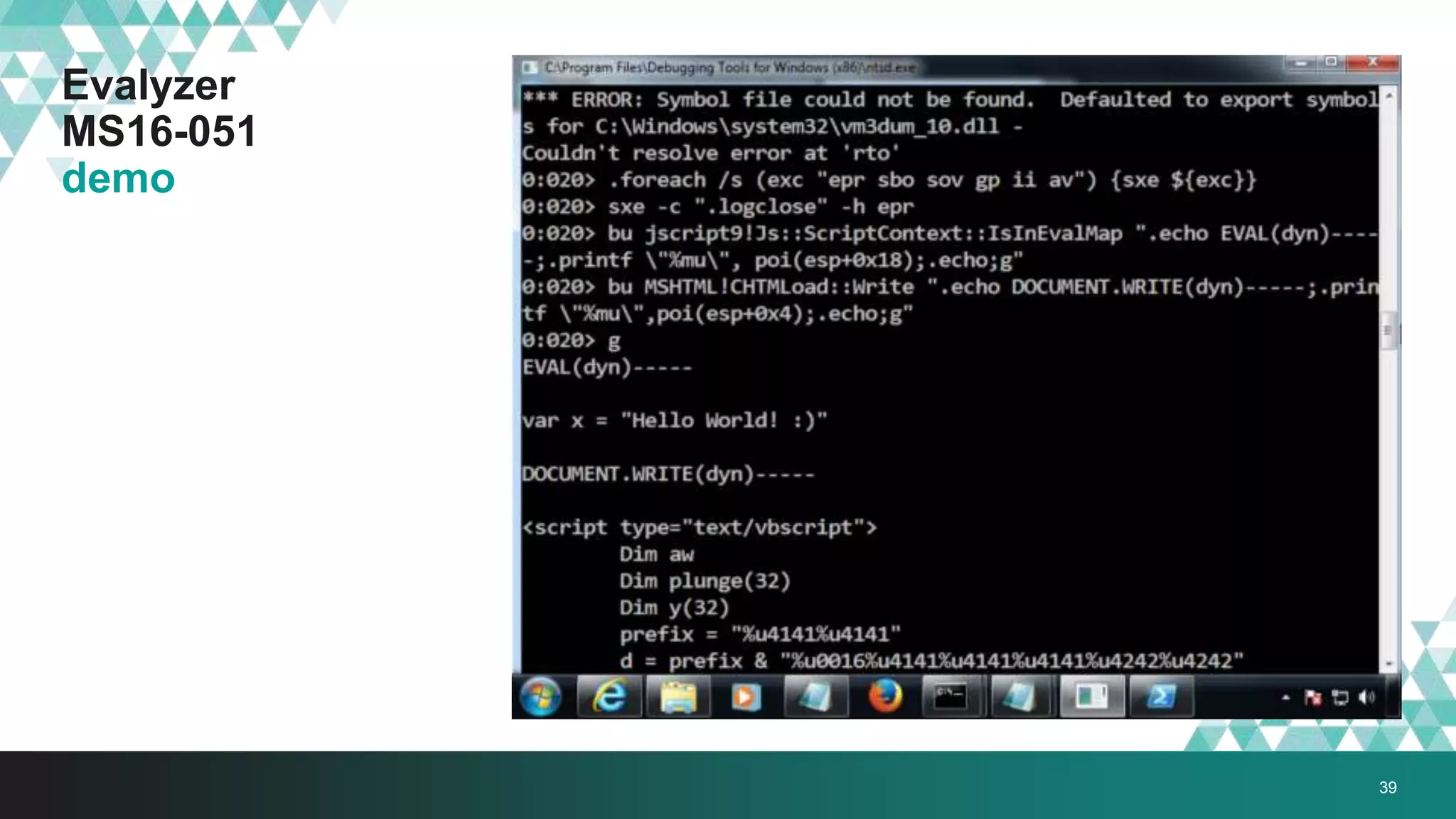
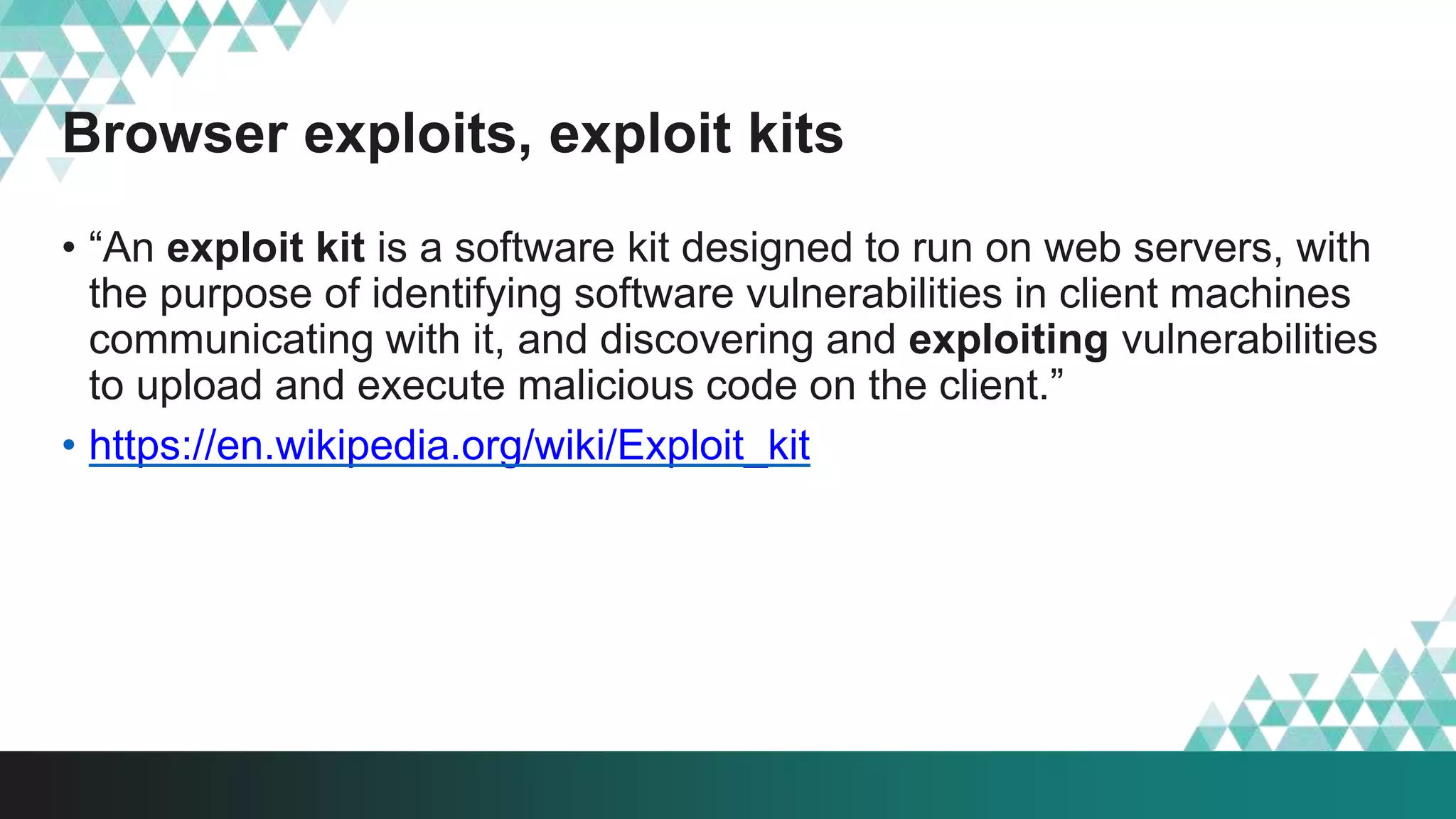
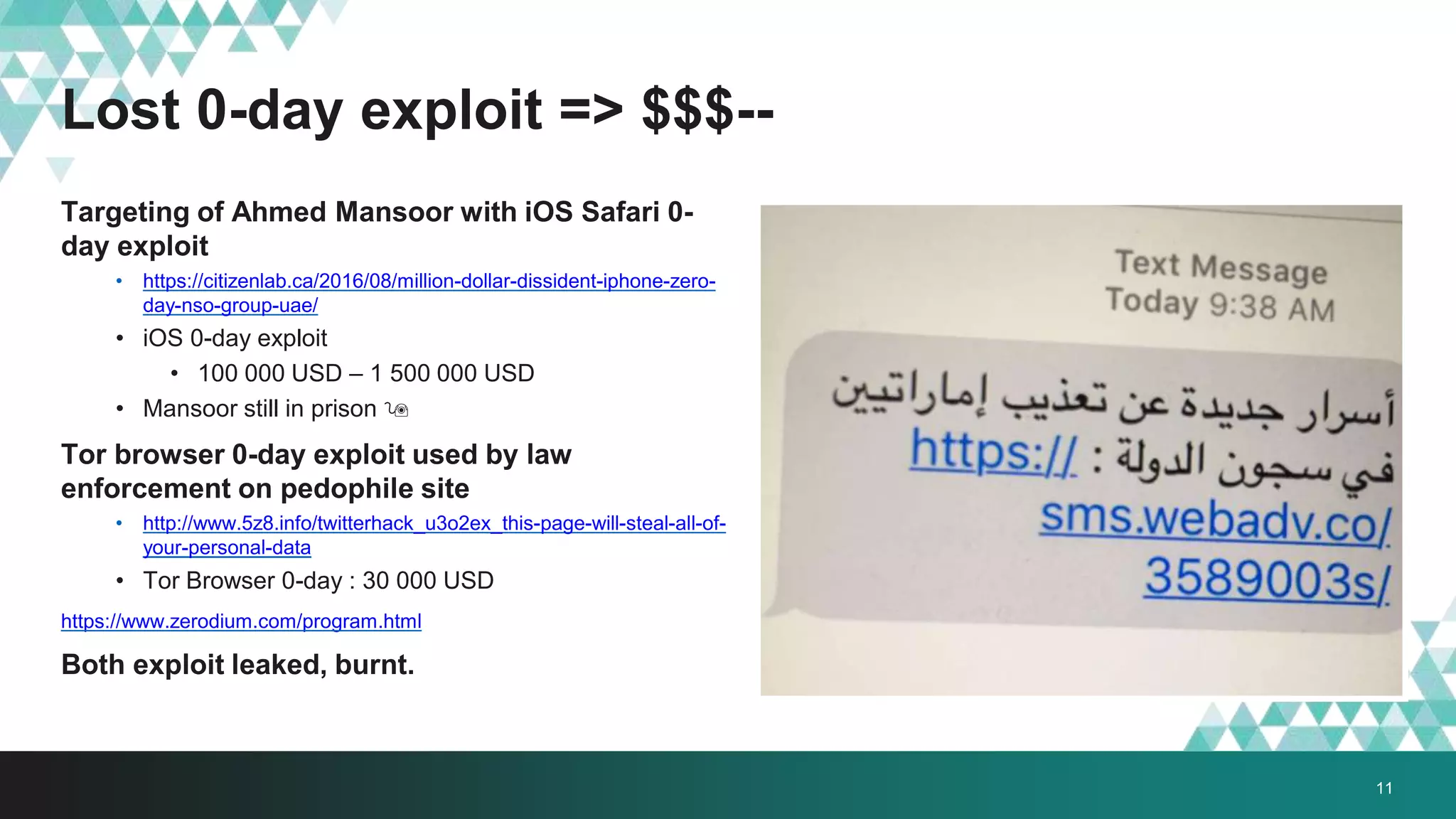
1. The document describes a method called #IRONSQUIRREL for delivering browser exploits in an encrypted format using elliptic curve Diffie-Hellman key exchange to prevent detection and analysis.
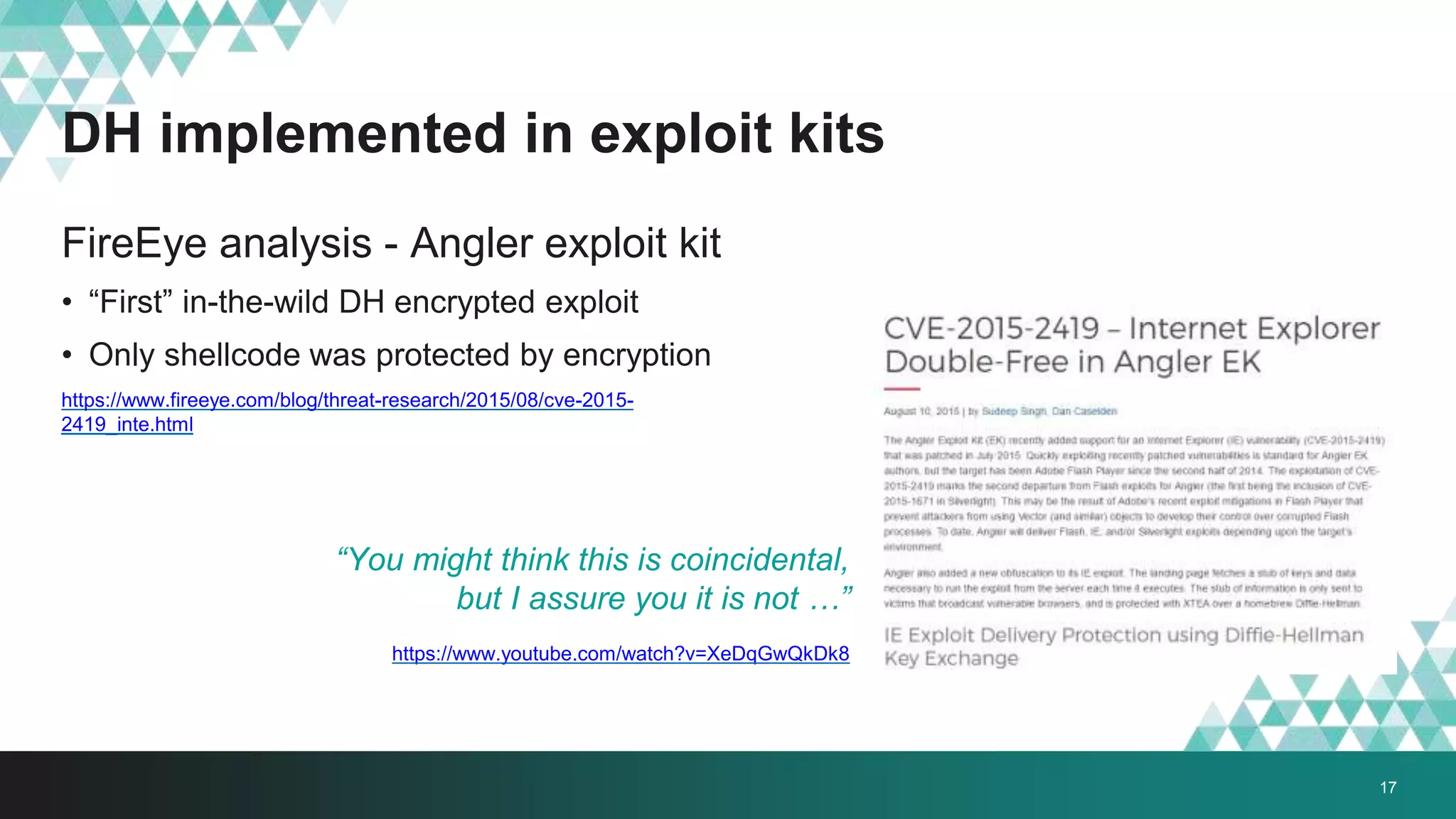
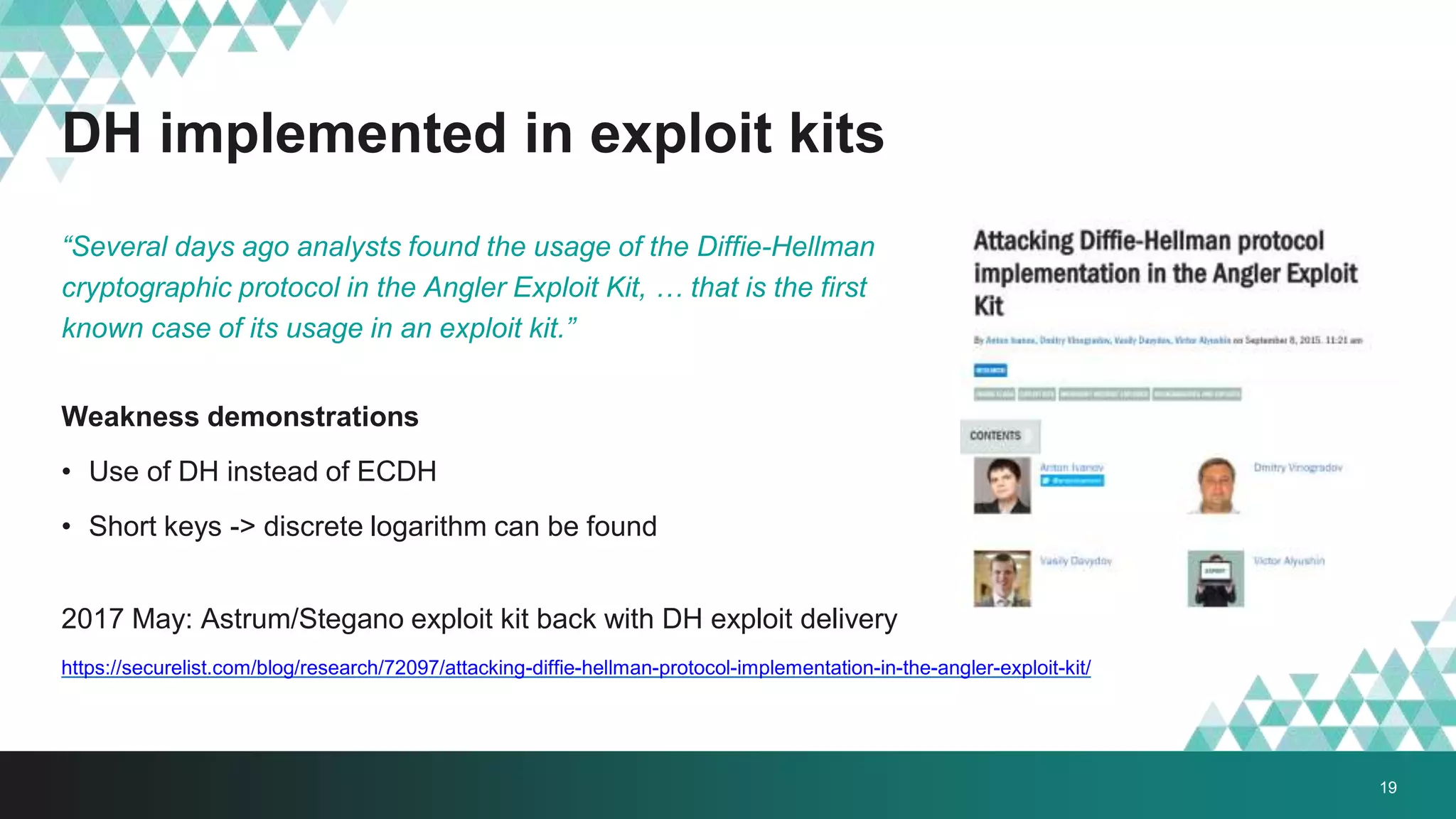
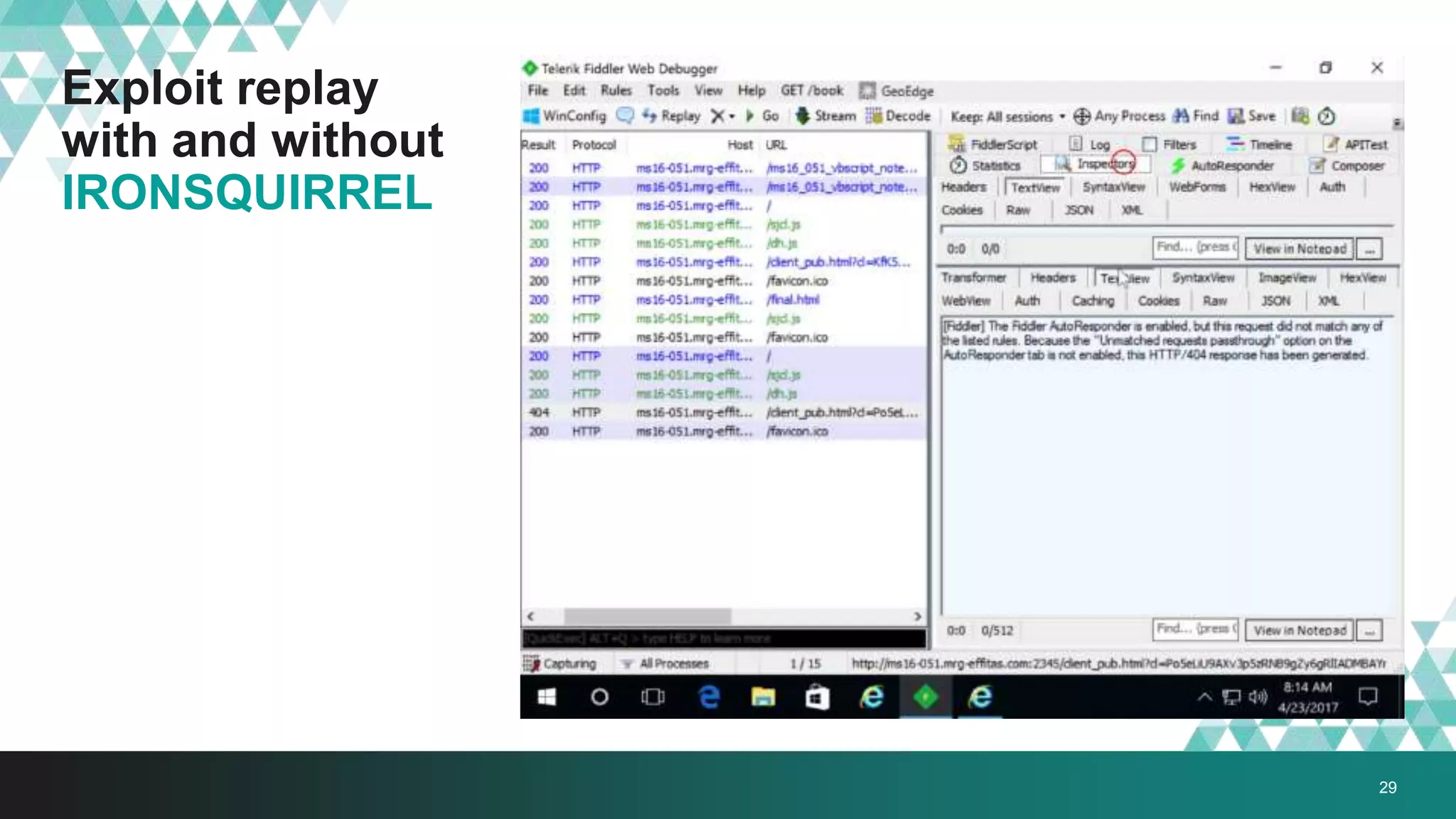
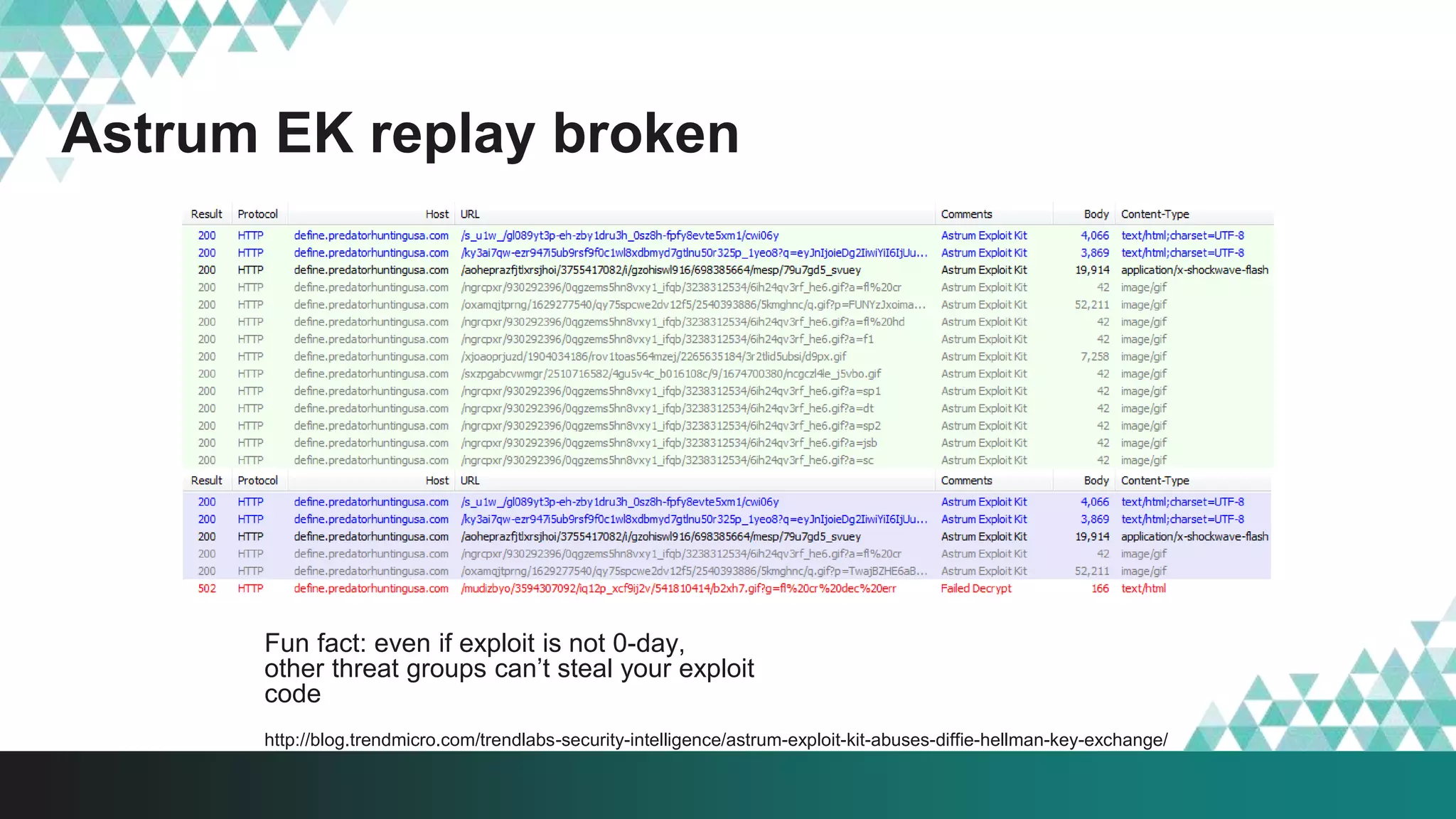
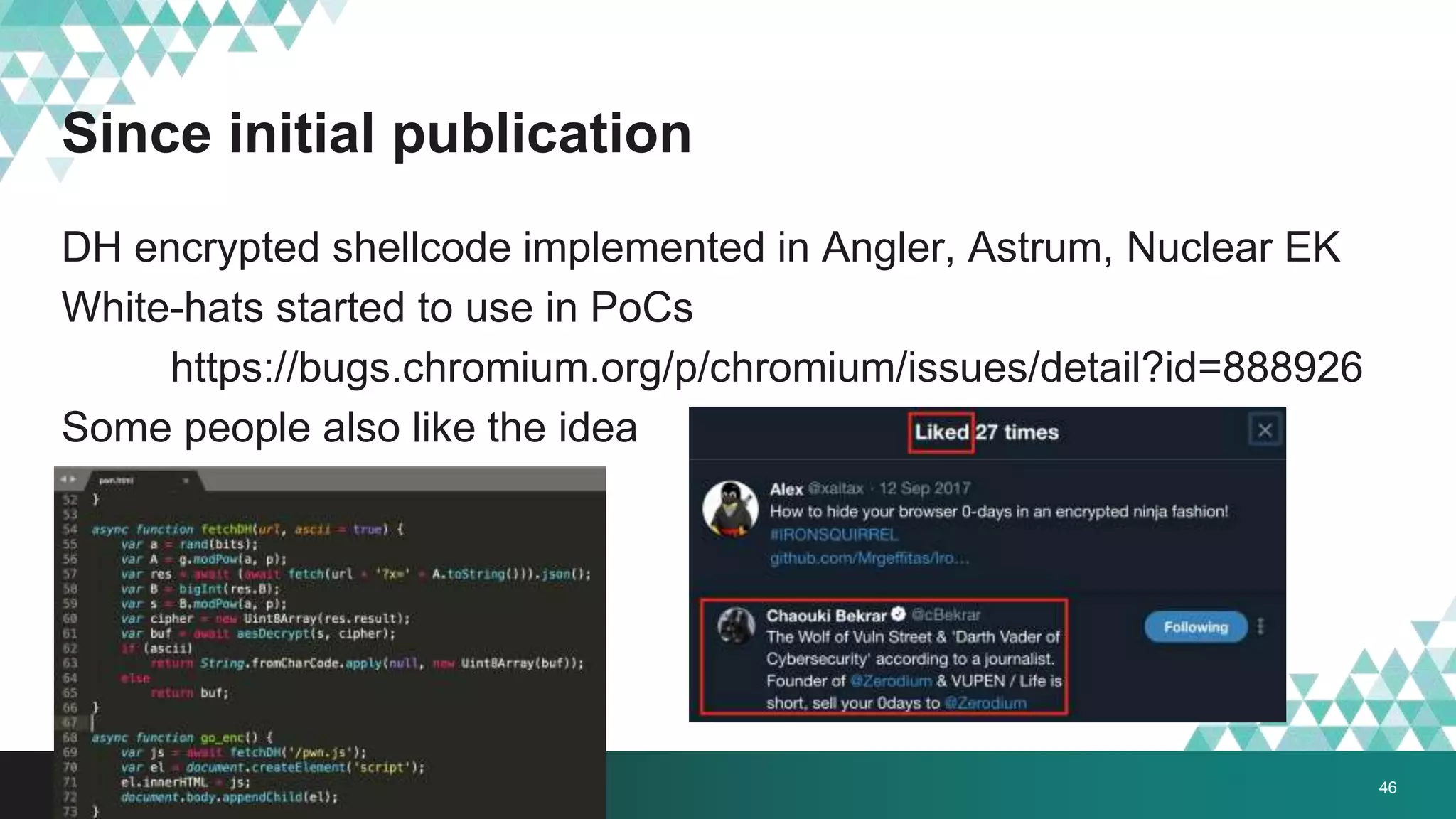
2. It was implemented in exploit kits like Angler to prevent reverse engineering of zero-day exploits and leakage of exploit code. The encrypted delivery prevents network-based detection and replay of the exploit.
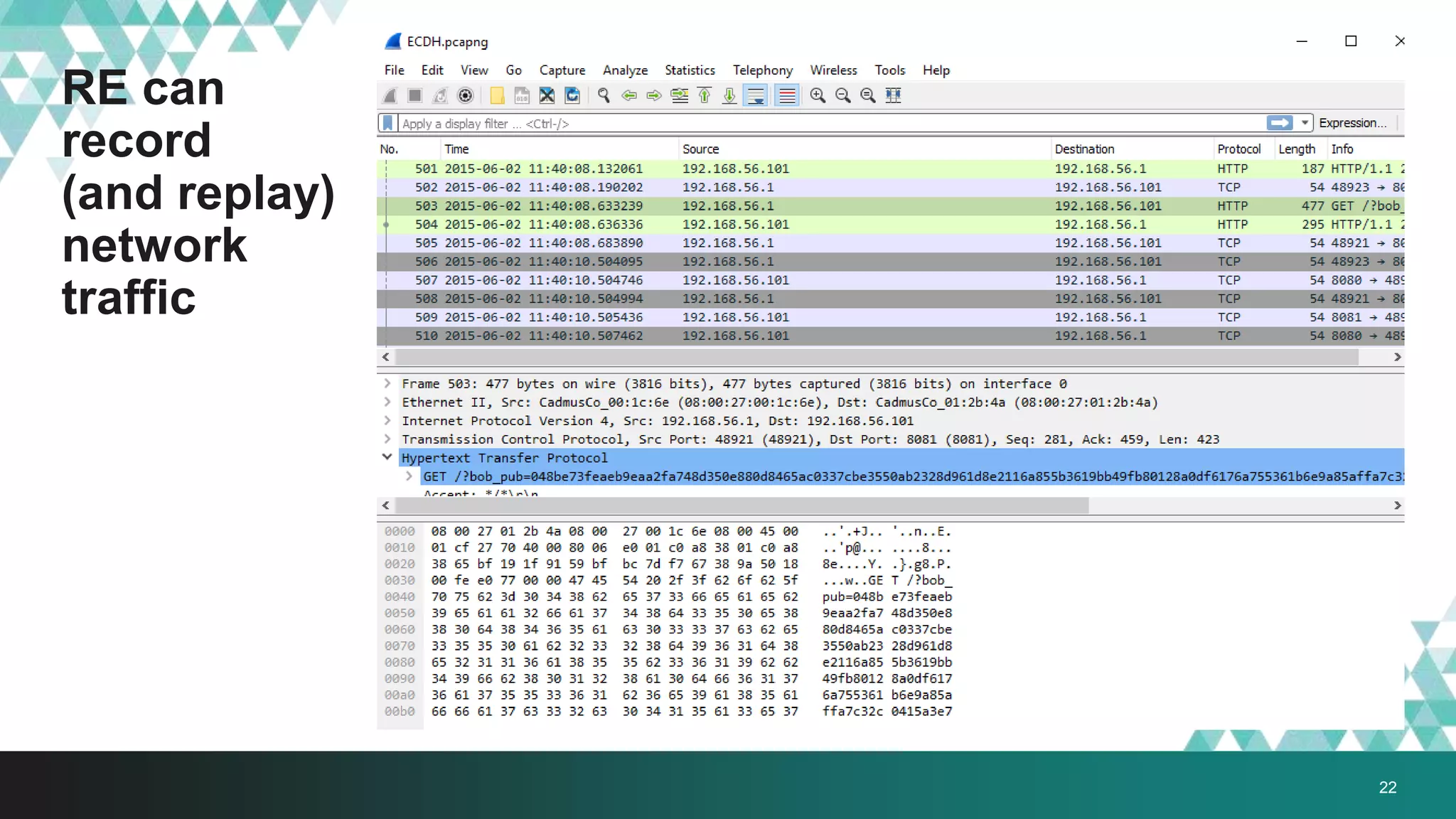
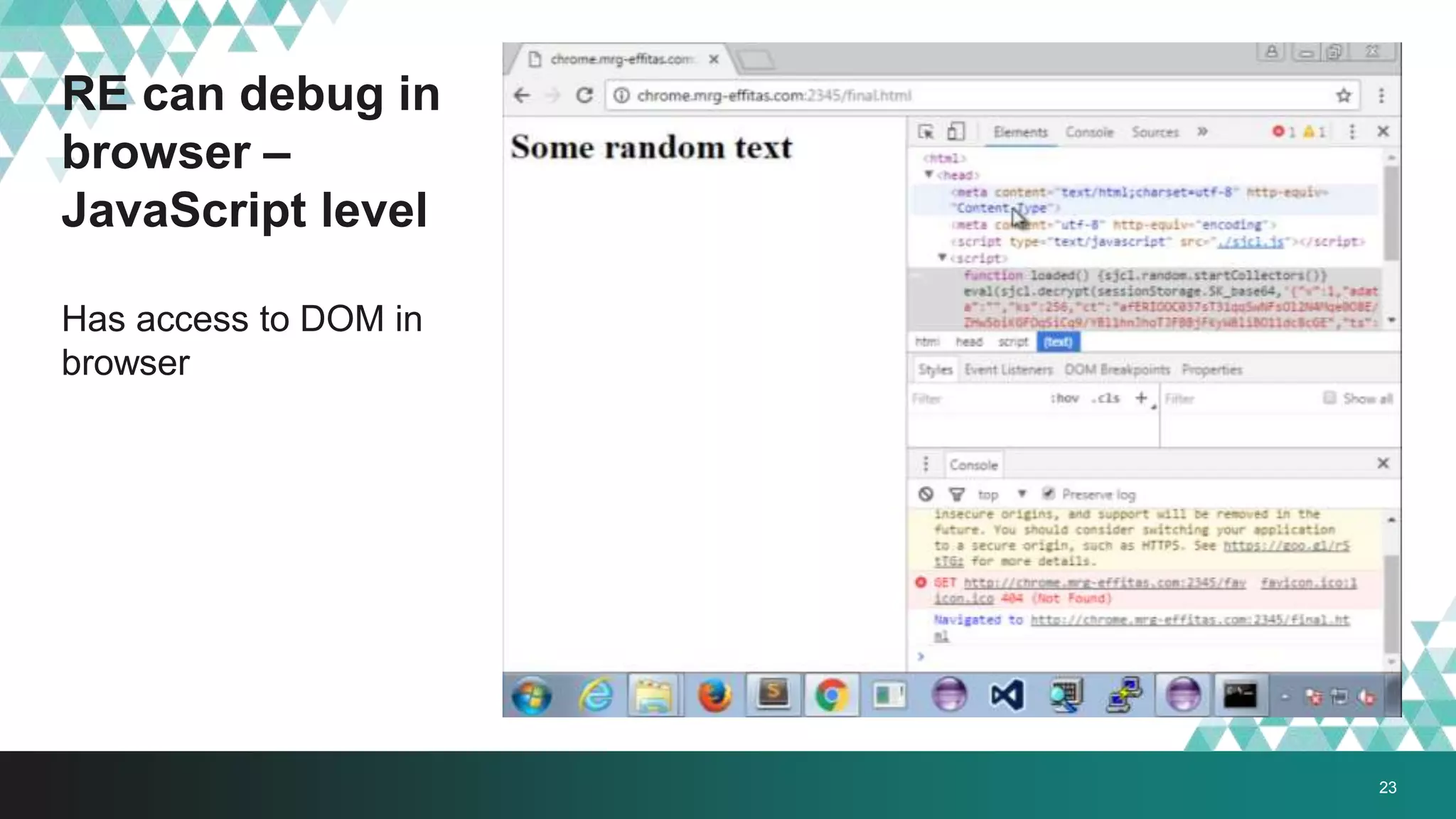
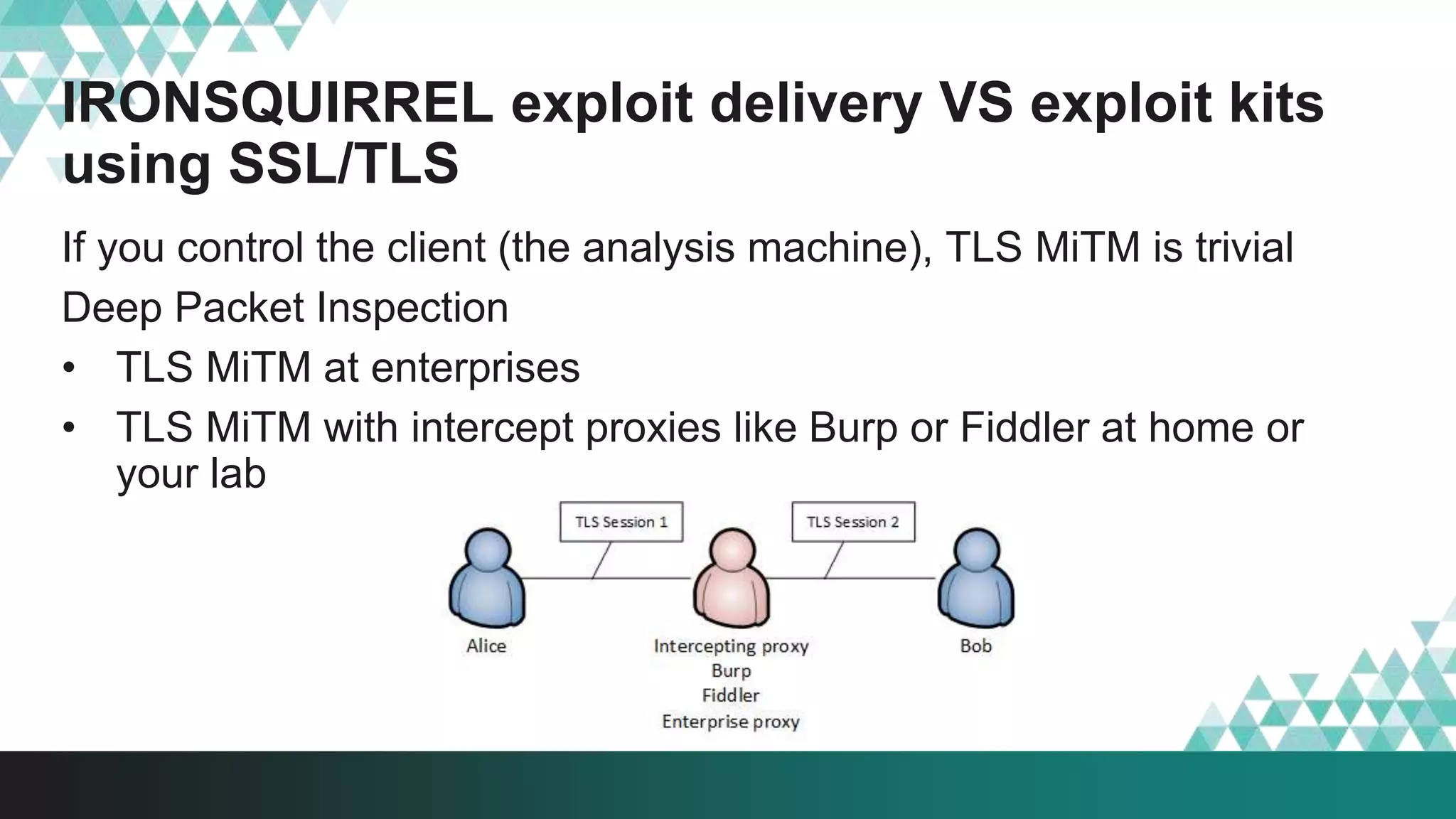
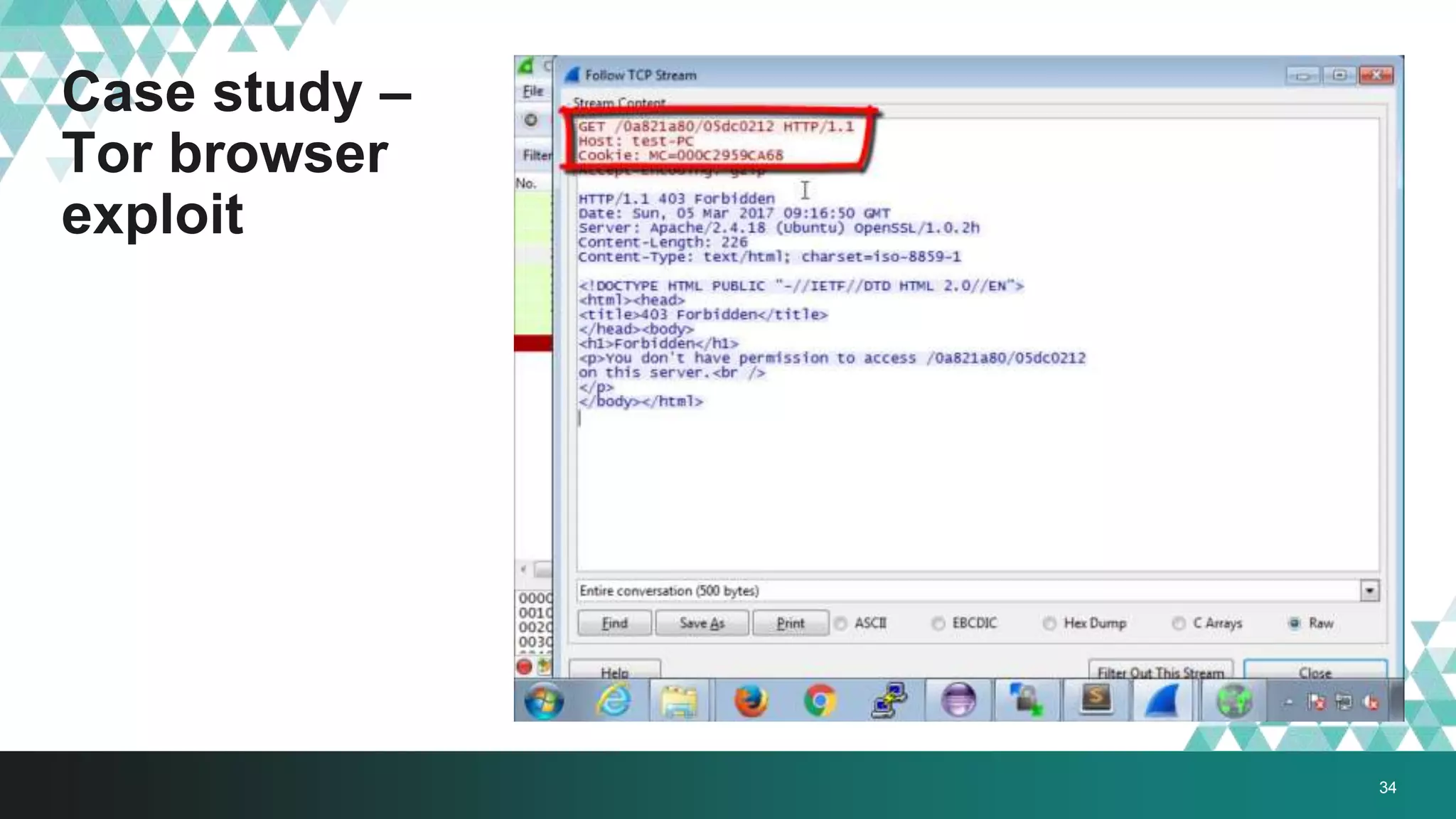
3. The document provides details on how #IRONSQUIRREL works and improves on previous encrypted delivery methods. It also discusses challenges and techniques for analysts to detect and analyze such encrypted exploits, as well as recommendations for attackers to strengthen #IRONSQUIRREL against analysis.



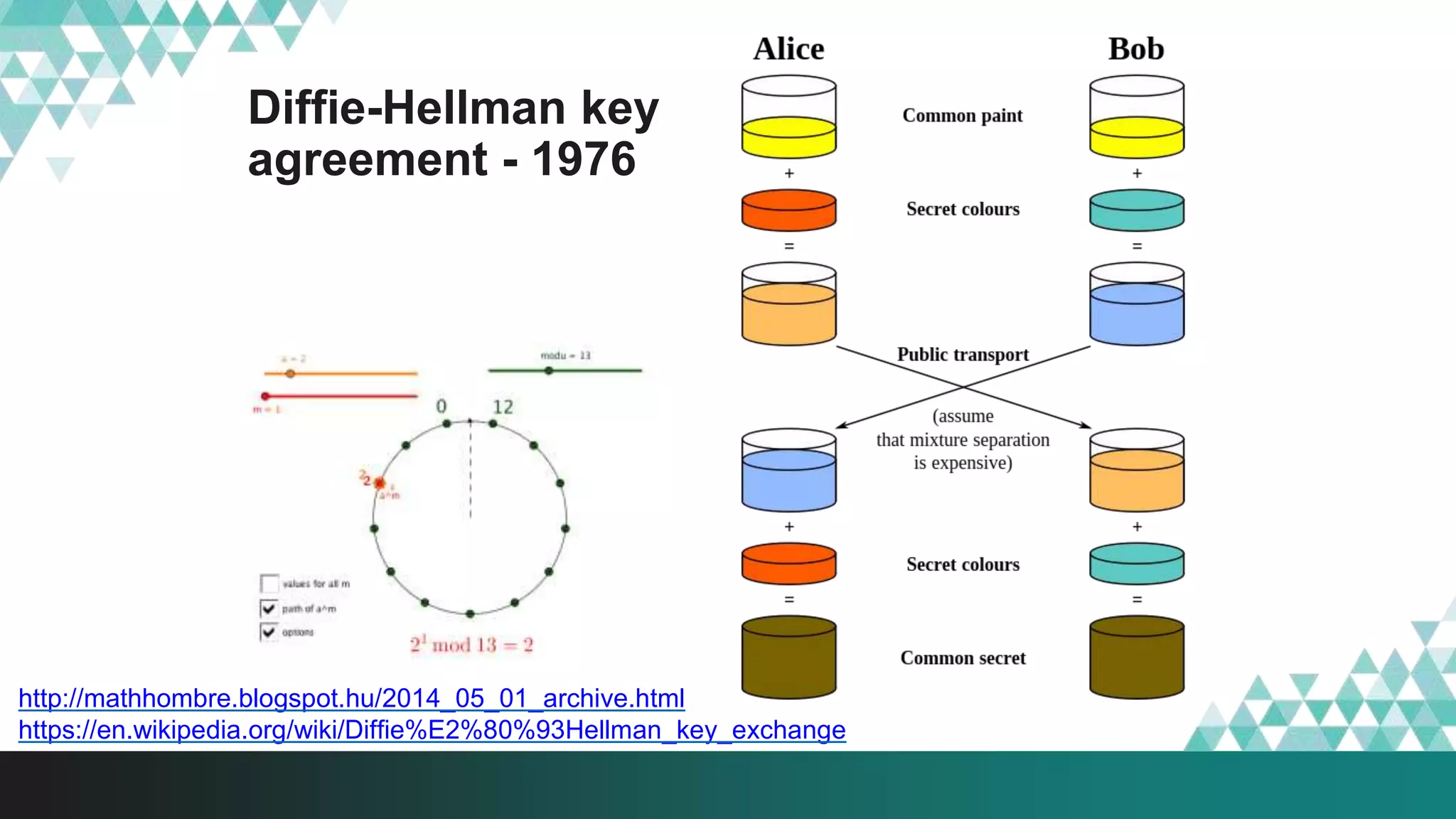
![Elliptic Curve based Diffie-Hellman
(ECDH) key agreement
ECDH key agreement 5-10 times faster on
same CPU [citation needed]
DH key agreement is too slow for JS
It is like you know the start and end position of
the billiard ball on the table, but god knows
the way it took to get there.
http://arstechnica.com/security/2013/10/a-relatively-easy-to-understand-primer-on-elliptic-curve-cryptography/1/
13](https://image.slidesharecdn.com/mrgdisobey-2019-ecdh-190115091928/75/How-to-hide-your-browser-0-day-Disobey-13-2048.jpg)