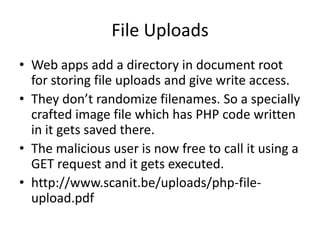
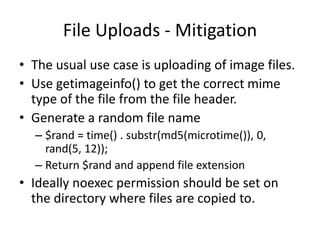
This document summarizes common web application vulnerabilities like cross-site scripting (XSS), SQL injection, and file uploads. It provides examples of each vulnerability and recommendations for mitigation strategies. For XSS, it recommends sanitizing input and escaping output. For SQL injection, it suggests using parameterized queries, stored procedures, and escaping strings. For file uploads, it advises validating file types, randomizing filenames, and restricting directory permissions. The document aims to help secure PHP web applications from these common risks.



![SQL Injection
• Allowing SQL to be injected in the database
query.
• Most common attack point is the search of any
dynamic website and registration forms. These
two will be definitely talking to the database.
• $sql = "SELECT * FROM table WHERE id = '" .
$_REQUEST['id'] . "'";
• id = ‘ OR 1 UNION ALL SELECT * FROM table;
• Excellent examples
http://google.com/search?q=site:slideshare.net
sql injection](https://image.slidesharecdn.com/phpsecurity-100402073728-phpapp02/85/null-Bangalore-meet-Php-Security-4-320.jpg)