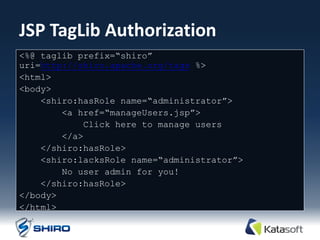
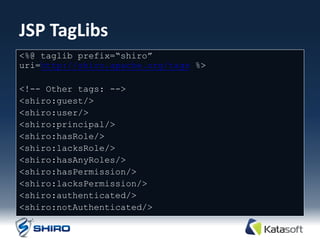
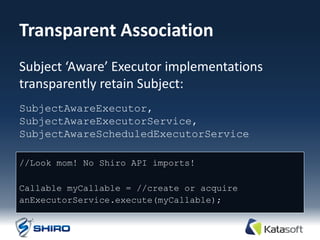
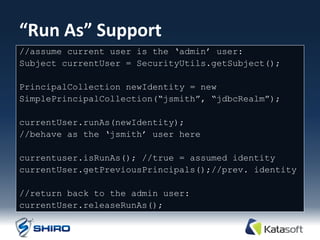
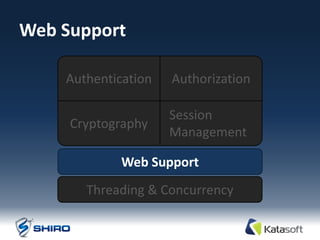
The document provides an overview of Apache Shiro, an application security library designed to simplify and enhance security features like authentication, authorization, session management, and cryptography. It details Shiro's architecture, core components, and practical use cases, outlining steps for implementing security within applications. The document also includes examples of how to authenticate users, manage sessions, and handle permissions using Shiro's APIs.
































![Shiro’s CipherService Interface
public interface CipherService {
ByteSource encrypt( byte[] raw, byte[]
key);
void encrypt(InputStream in,
OutputStream out, byte[] key);
ByteSource decrypt( byte[] cipherText,
byte[] key);
void decrypt(InputStream in,
OutputStream out, byte[] key);
}](https://image.slidesharecdn.com/apacheshiropresentation-20101013-101021174352-phpapp01/85/Super-simple-application-security-with-Apache-Shiro-40-320.jpg)

![Shiro’s Hash Interface
public interface Hash {
byte[] getBytes();
String toHex();
String toBase64();
}](https://image.slidesharecdn.com/apacheshiropresentation-20101013-101021174352-phpapp01/85/Super-simple-application-security-with-Apache-Shiro-42-320.jpg)


![web.xml
<filter>
<filter-name>ShiroFilter</filter-name>
<filter-class>org.apache.shiro.web.servlet.IniShiroFilter</filter-
class>
<init-param><param-name>config</param-name><param-value>
[main]
realm = com.my.custom.realm.Implementation
securityManager.realm = $realm
[urls]
/account/** = authc
/remoting/** = authc, roles[b2bClient], ...
</param-value></init-param>
</filter>
<filter-mapping>
<filter-name>ShiroFilter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>](https://image.slidesharecdn.com/apacheshiropresentation-20101013-101021174352-phpapp01/85/Super-simple-application-security-with-Apache-Shiro-46-320.jpg)