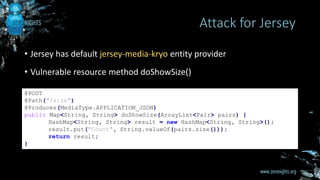
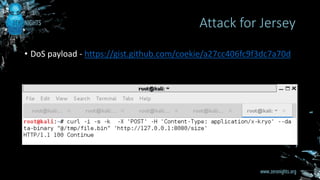
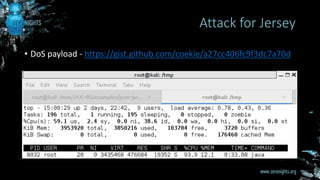
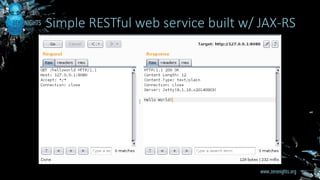
The document discusses entity provider selection confusion attacks in JAX-RS applications, highlighting vulnerabilities when resource methods do not specify preferred content types with the @consumes annotation. It details the impact of these attacks, including risks of remote code execution, denial of service, and cross-site request forgery, specifically addressing security flaws in RESTEasy and Jersey frameworks. Key recommendations include restricting content types and being cautious with multipart content types.

![• Security researcher, bug hunter
• Application security engineer at Odin [ Ingram Micro Cloud ]
• @0ang3el
• http://0ang3el.blogspot.com
• http://www.slideshare.net/0ang3el
About me](https://image.slidesharecdn.com/zn6jax-rs-161119135734/85/Entity-provider-selection-confusion-attacks-in-JAX-RS-applications-2-320.jpg)
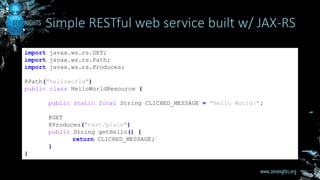
![• Java API for creating RESTful web services
• Part of J2EE since J2EE 6
• JAX-RS 2.0 [ https://jcp.org/aboutJava/communityprocess/final/jsr339/index.html ]
• RESTEasy [ Red Hat ] , Jersey [ Oracle ]
What is JAX-RS?](https://image.slidesharecdn.com/zn6jax-rs-161119135734/85/Entity-provider-selection-confusion-attacks-in-JAX-RS-applications-3-320.jpg)


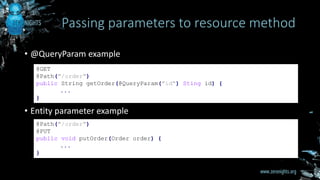

![• Entity providers – specials Java classes
• Annotated with @Provider
• Implement javax.ws.rs.ext.MessageBodyReader [ isReadable(), readFrom() ]
• Entity provider is selected based on
• Content type specified with @Consumes annotation
• Content-Type HTTP header in request
• Java Class of entity parameter
• There are interesting built-in entity providers
Entity providers](https://image.slidesharecdn.com/zn6jax-rs-161119135734/85/Entity-provider-selection-confusion-attacks-in-JAX-RS-applications-10-320.jpg)
![• Jersey performs WEB-INF/lib scanning for entity providers
• RESTEasy by default performs WEB-INF/lib scanning for entity
providers, parameter resteasy.scan.providers does not work
[ https://issues.jboss.org/browse/RESTEASY-1504 ]
Automated scanning for entity providers](https://image.slidesharecdn.com/zn6jax-rs-161119135734/85/Entity-provider-selection-confusion-attacks-in-JAX-RS-applications-11-320.jpg)

![• RESTEasy by default has SerializableProvider entity provider
• Vulnerable resource method doConcat()
Attack for RESTEasy [ CVE-2016-7050 ]
@POST
@Path("/concat")
@Produces(MediaType.APPLICATION_JSON)
public Map doConcat(Pair pair) {
HashMap result = new HashMap();
result.put("Result", pair.getP1() + pair.getP2());
return result;
}
public class Pair implements Serializable {
...
}](https://image.slidesharecdn.com/zn6jax-rs-161119135734/85/Entity-provider-selection-confusion-attacks-in-JAX-RS-applications-15-320.jpg)
![• isReadable() method of SerializableProvider
• SerializableProvider is used when Content-Type is application/x-java-
serialized-object and Java class of entity parameter is serializable
Attack for RESTEasy [ CVE-2016-7050 ]
public boolean isReadable(Class type, Type genericType, Annotation[] annotations,
MediaType mediaType) {
return (Serializable.class.isAssignableFrom(type)) &&
(APPLICATION_SERIALIZABLE_TYPE.getType().equals(mediaType.getType())) &&
(APPLICATION_SERIALIZABLE_TYPE.getSubtype().equals(mediaType.getSubtype()));
}](https://image.slidesharecdn.com/zn6jax-rs-161119135734/85/Entity-provider-selection-confusion-attacks-in-JAX-RS-applications-16-320.jpg)
![• readFrom() method of SerializableProvider
Attack for RESTEasy [ CVE-2016-7050 ]
public Serializable readFrom(Class type, Type genericType, Annotation[]
annotations, MediaType mediaType, MultivaluedMap httpHeaders, InputStream
entityStream) throws IOException, WebApplicationException {
BufferedInputStream bis = new BufferedInputStream(entityStream);
ObjectInputStream ois = new ObjectInputStream(bis);
try {
return (Serializable)Serializable.class.cast(ois.readObject());
} catch (ClassNotFoundException e) {
throw new WebApplicationException(e);
}
}](https://image.slidesharecdn.com/zn6jax-rs-161119135734/85/Entity-provider-selection-confusion-attacks-in-JAX-RS-applications-17-320.jpg)
![Attack for RESTEasy [ CVE-2016-7050 ]](https://image.slidesharecdn.com/zn6jax-rs-161119135734/85/Entity-provider-selection-confusion-attacks-in-JAX-RS-applications-18-320.jpg)
![Attack for RESTEasy [ CVE-2016-7050 ]](https://image.slidesharecdn.com/zn6jax-rs-161119135734/85/Entity-provider-selection-confusion-attacks-in-JAX-RS-applications-19-320.jpg)