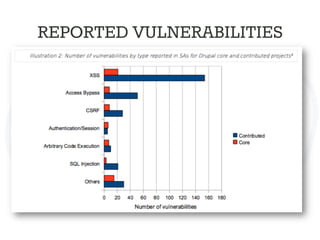
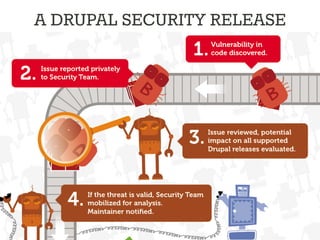
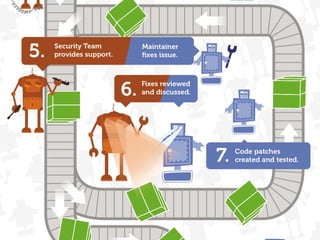
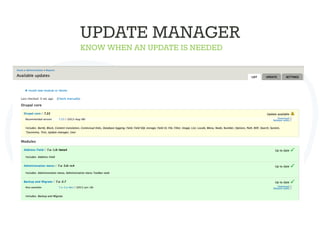
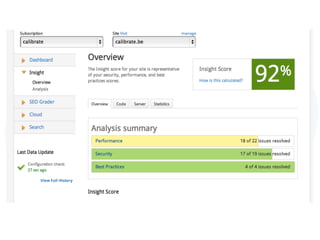
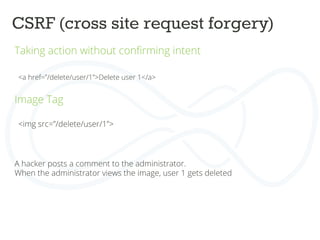
The document discusses secure Drupal development practices, emphasizing that security is an ongoing process and highlighting the importance of keeping Drupal installations and contributed modules up to date to mitigate vulnerabilities. It addresses common security issues such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF), and offers strategies for preventing them through best practices in coding and configuration. Additionally, it points to various tools and resources for monitoring and enhancing security in Drupal applications.













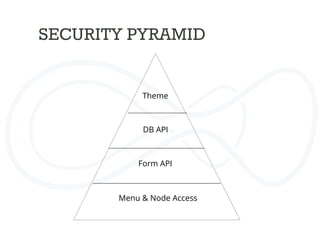





![XSS (cross site scripting)
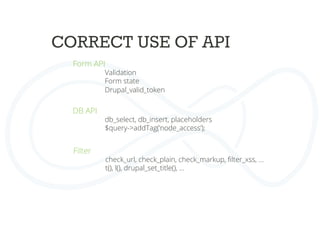
Validate forms
User input should never contain javascript
Form api
Never use $_POST variables
$form_state['values']
Form caching](https://image.slidesharecdn.com/drupalcampleuven-securedrupaldevelopment-140611081540-phpapp02/85/Drupal-campleuven-Secure-Drupal-Development-30-320.jpg)
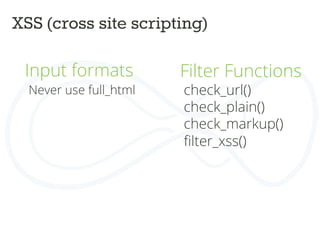
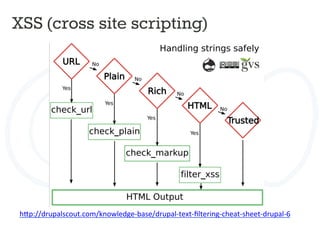
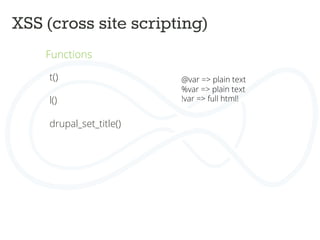



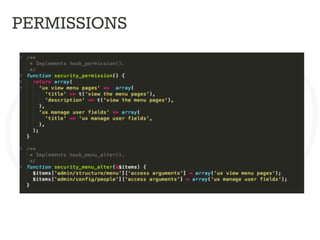
![ACCESS BYPASS
Rabbit_hole module
Rabbit Hole is a module that adds the ability to control what should happen
when an entity is being viewed at its own page.
Page manager can do the same.
Field access
$form['#access'] = custom_access_callback();
Menu access
$item['access callback'] = 'custom_access_callback',](https://image.slidesharecdn.com/drupalcampleuven-securedrupaldevelopment-140611081540-phpapp02/85/Drupal-campleuven-Secure-Drupal-Development-39-320.jpg)