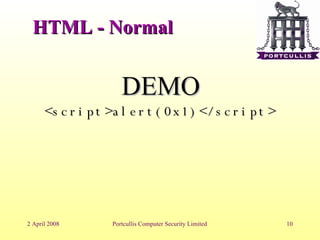
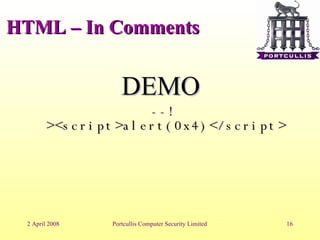
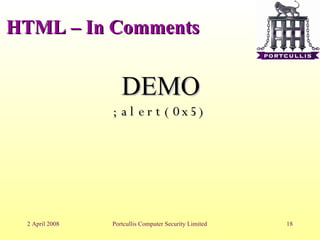
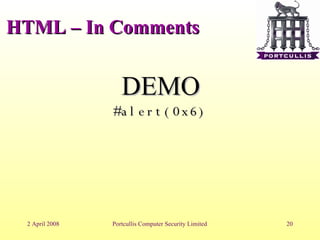
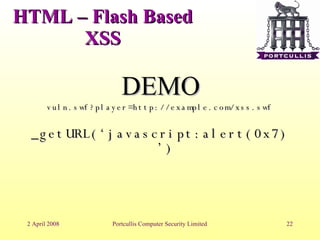
The document discusses different types of cross-site scripting (XSS) vulnerabilities and how to detect and exploit them. It outlines the main places where output can be injected, including directly into HTML, JavaScript blocks, attributes, comments, and Flash. It then provides examples and demonstrations of exploiting XSS in each of these contexts, such as by injecting JavaScript alerts. The document concludes by noting challenges in exploiting XSS and the importance of testing payloads with and without encoding.