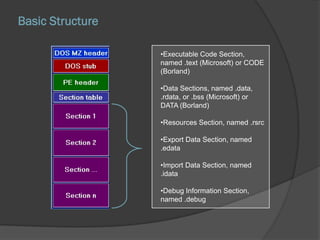
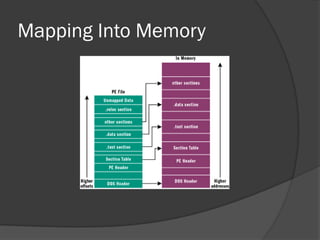
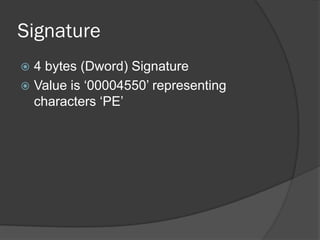
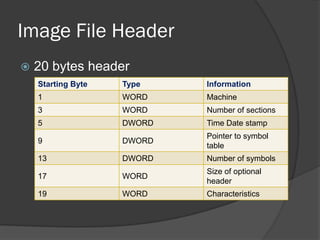
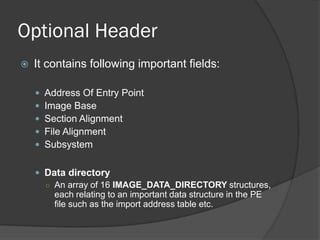
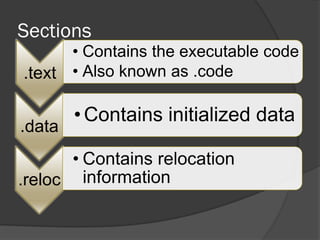
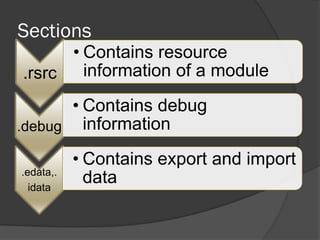
The document discusses the Portable Executable (PE) file format used in Windows operating systems. It describes the basic structure of a PE file which includes sections for executable code, data, resources, exports, imports, and debugging. It also explains the DOS header and stub, the PE file header containing signatures and metadata, and the image and optional headers containing addresses and alignments. Sections are described as containing code, data, resources, and other essential information.