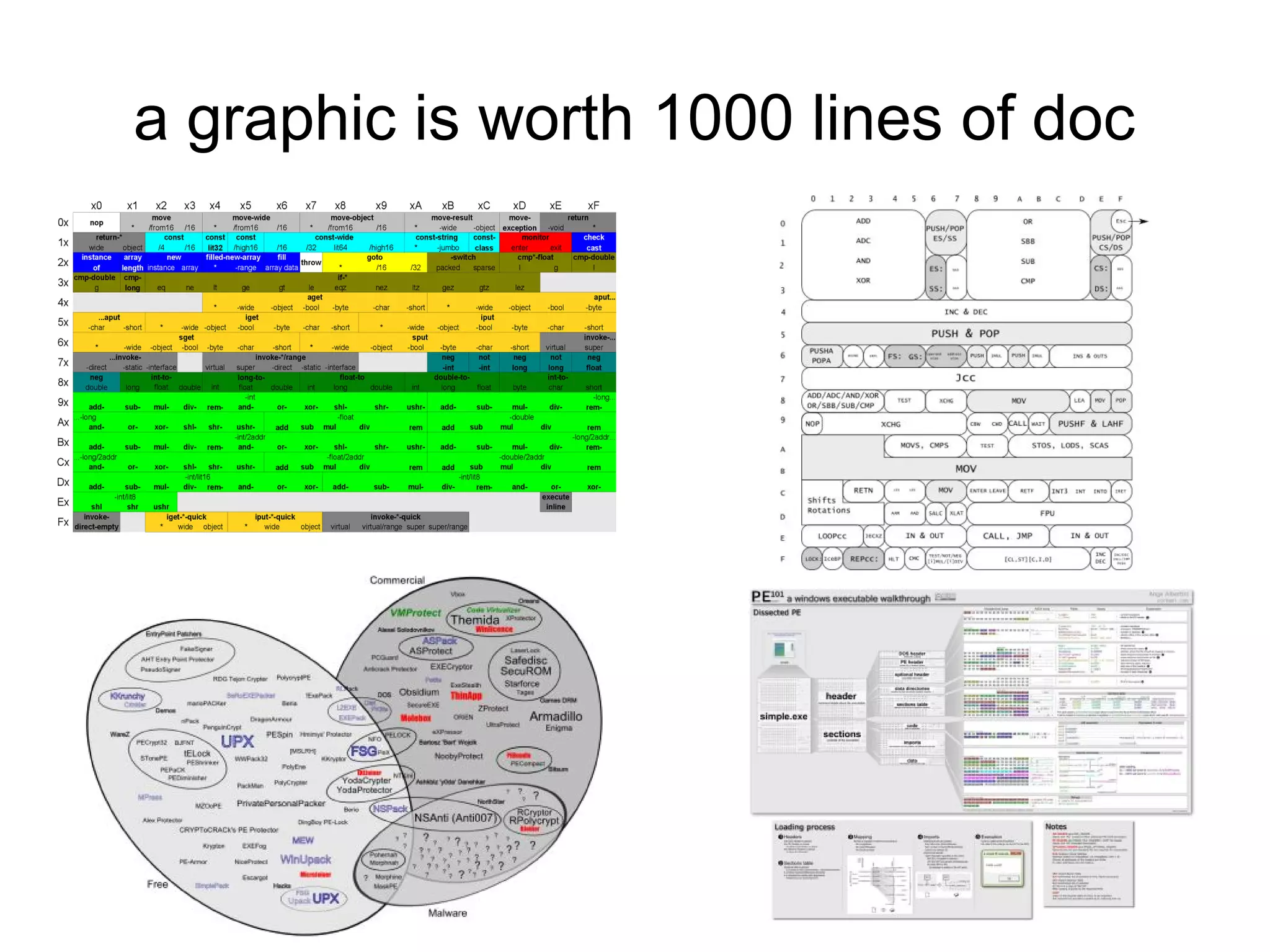
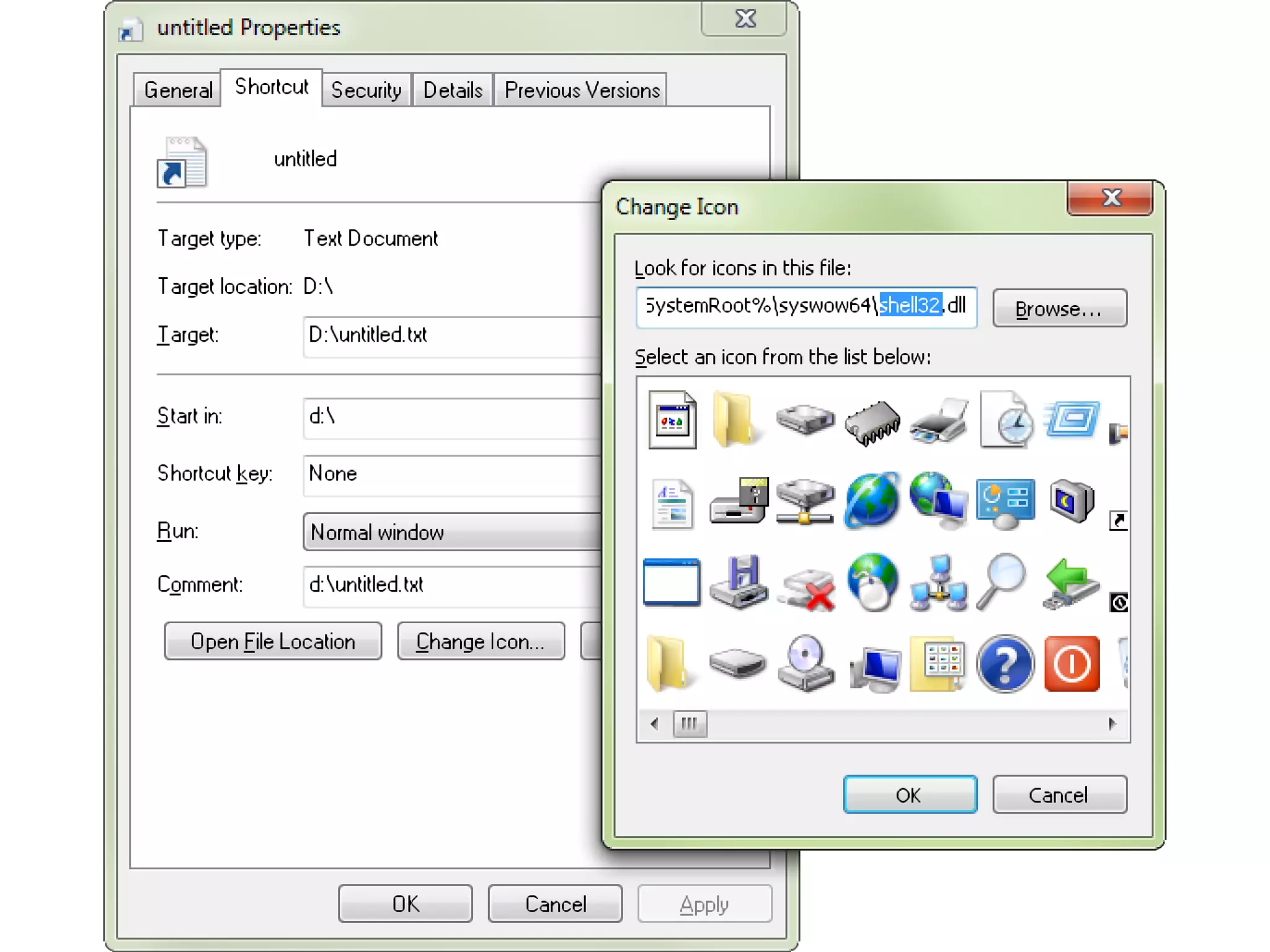
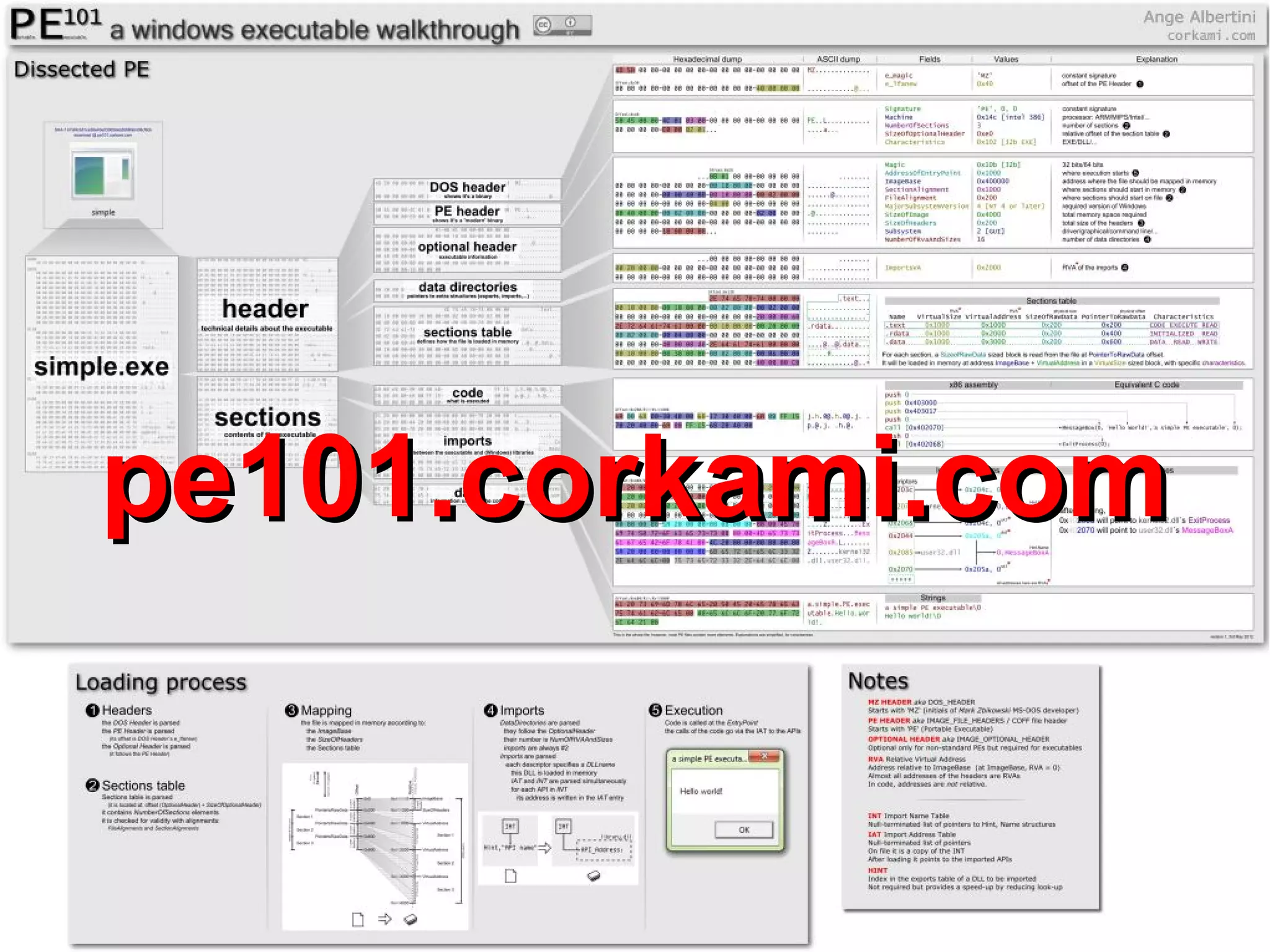
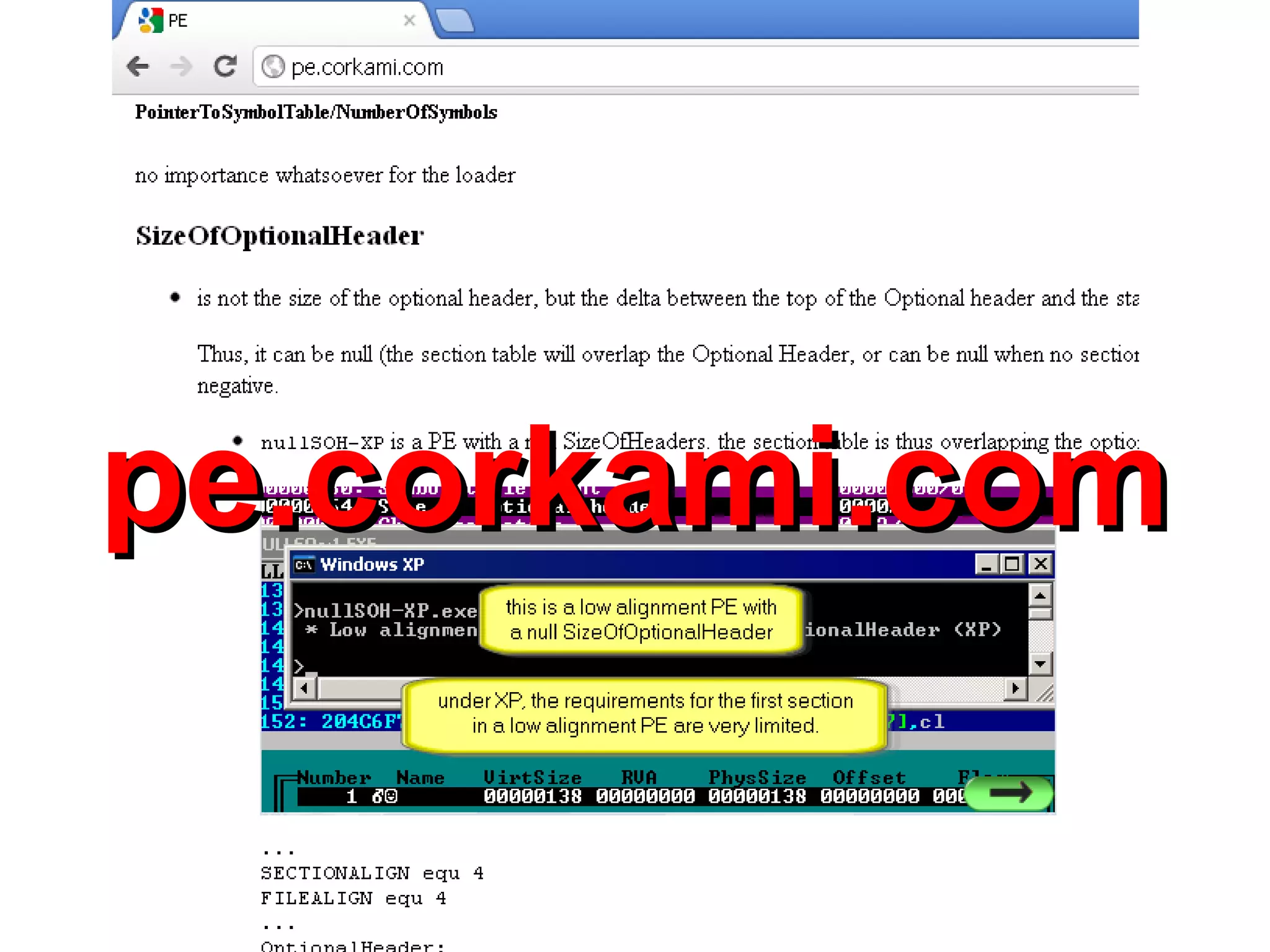
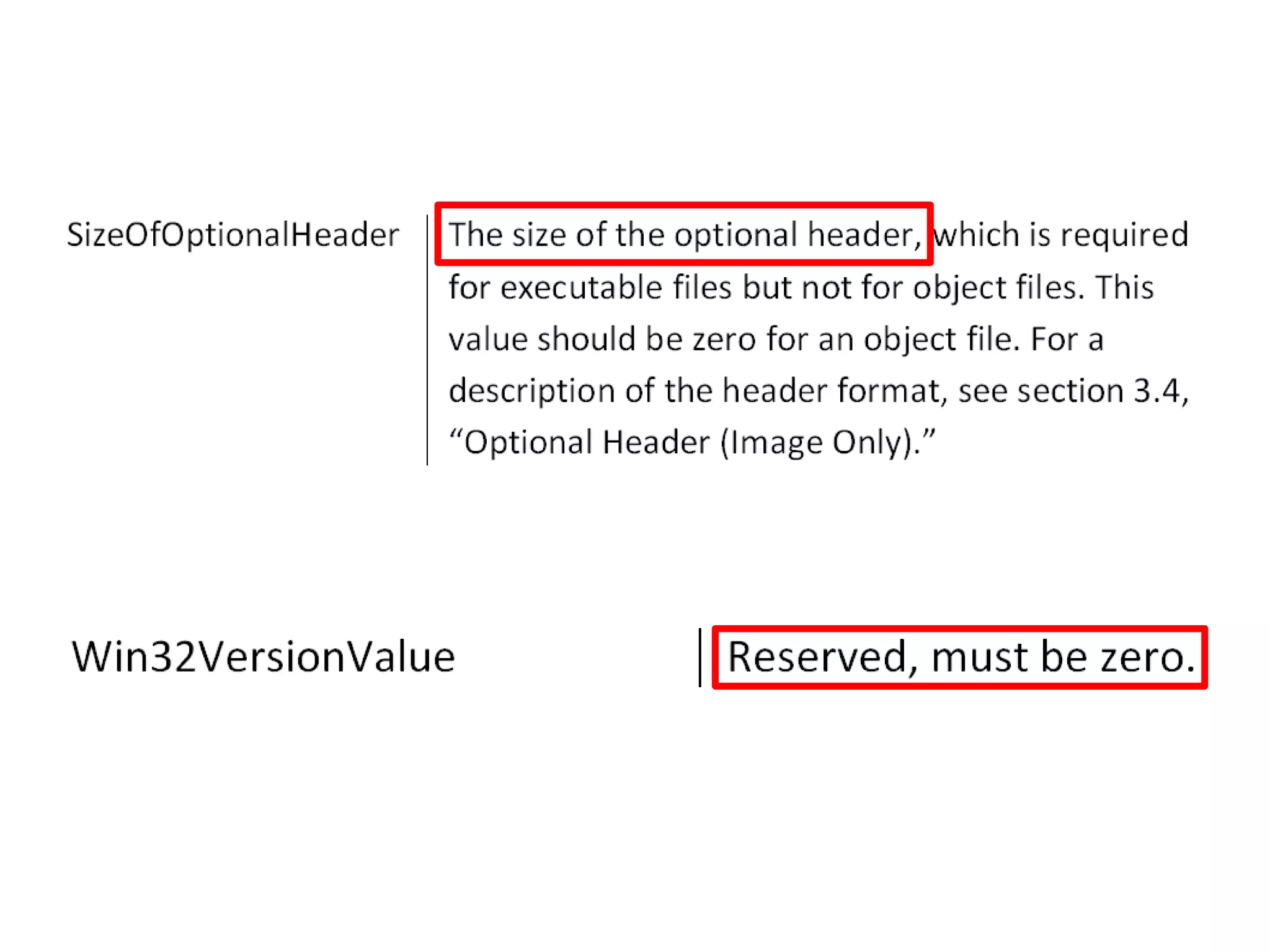
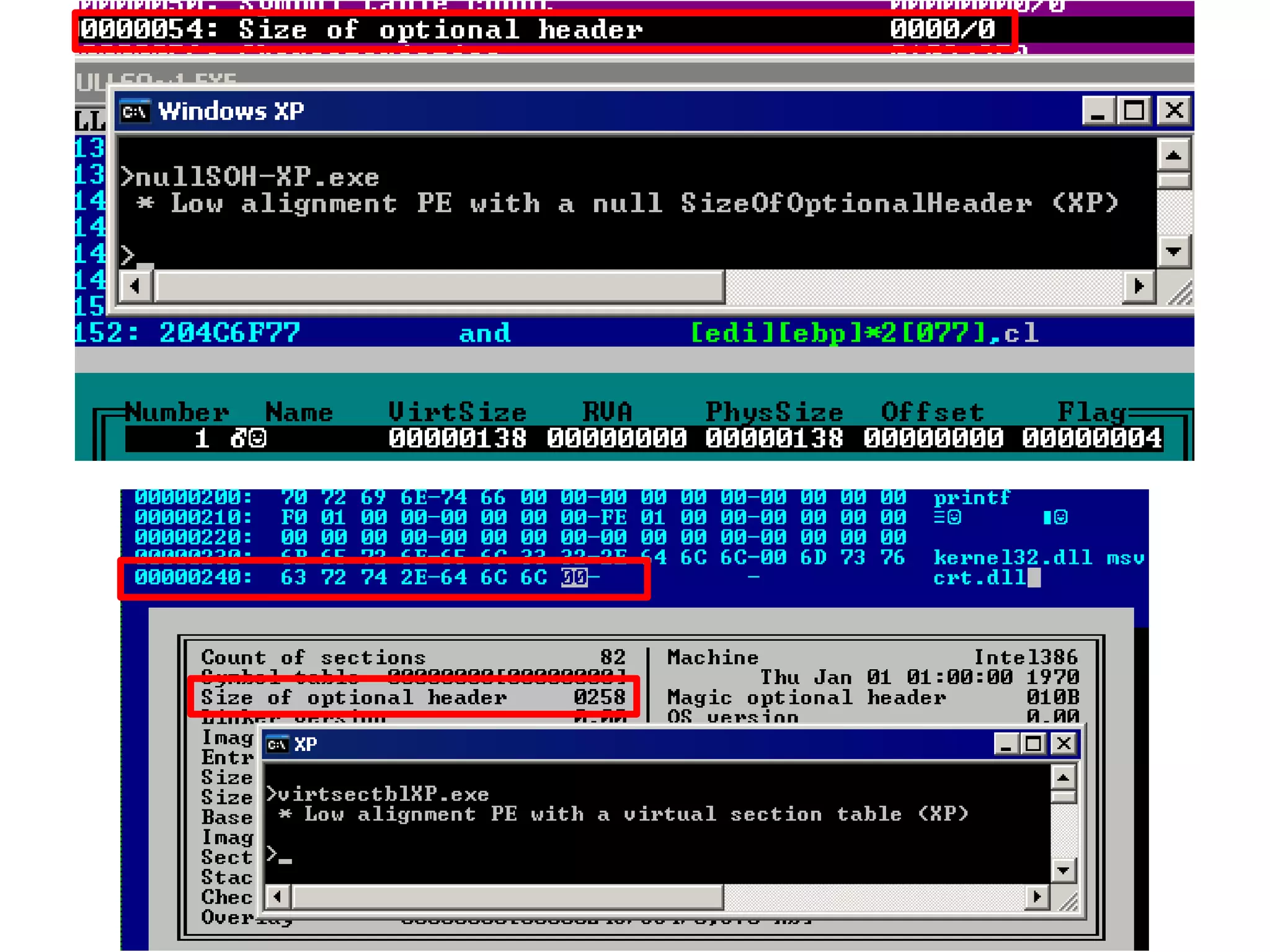
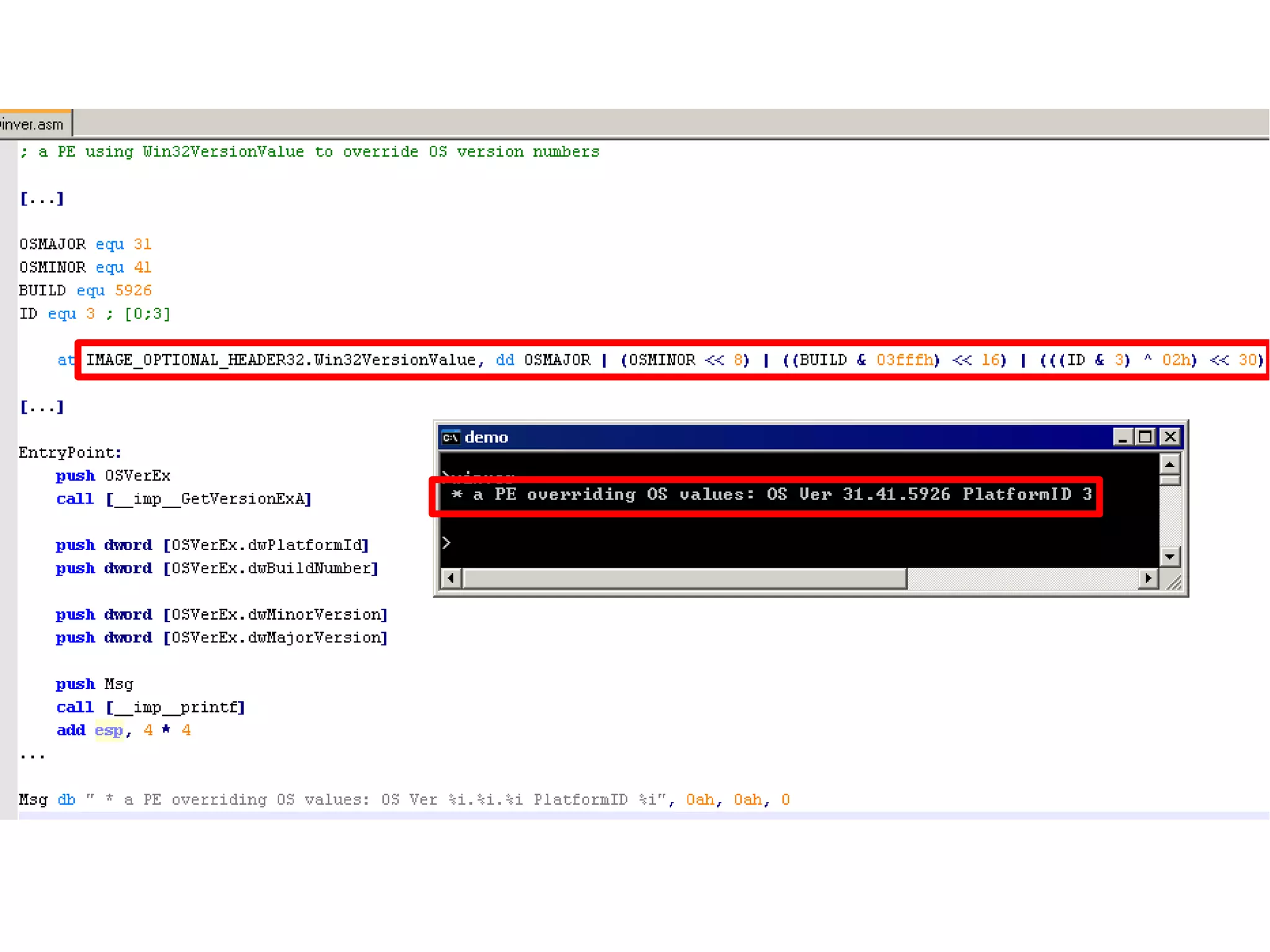
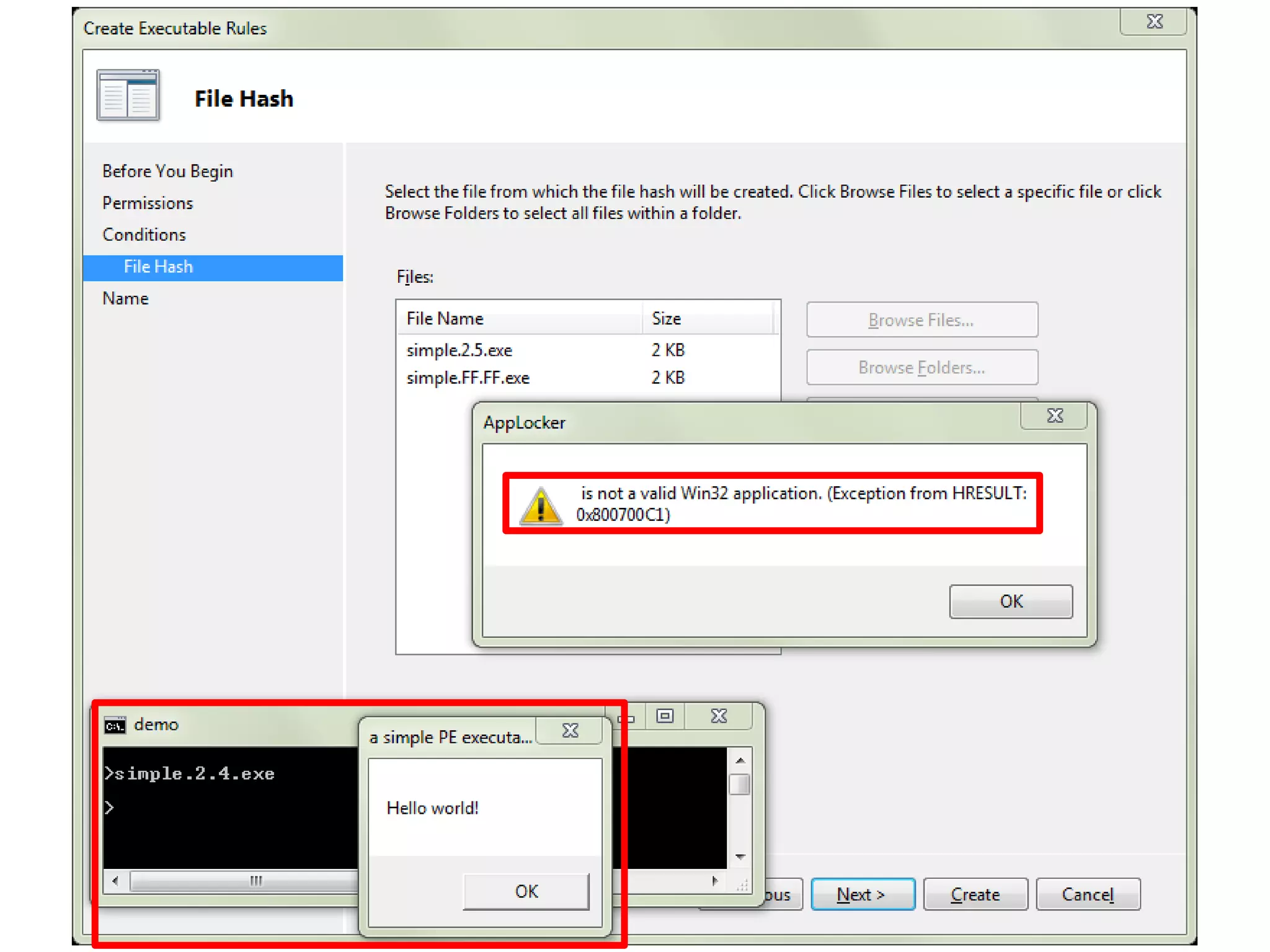
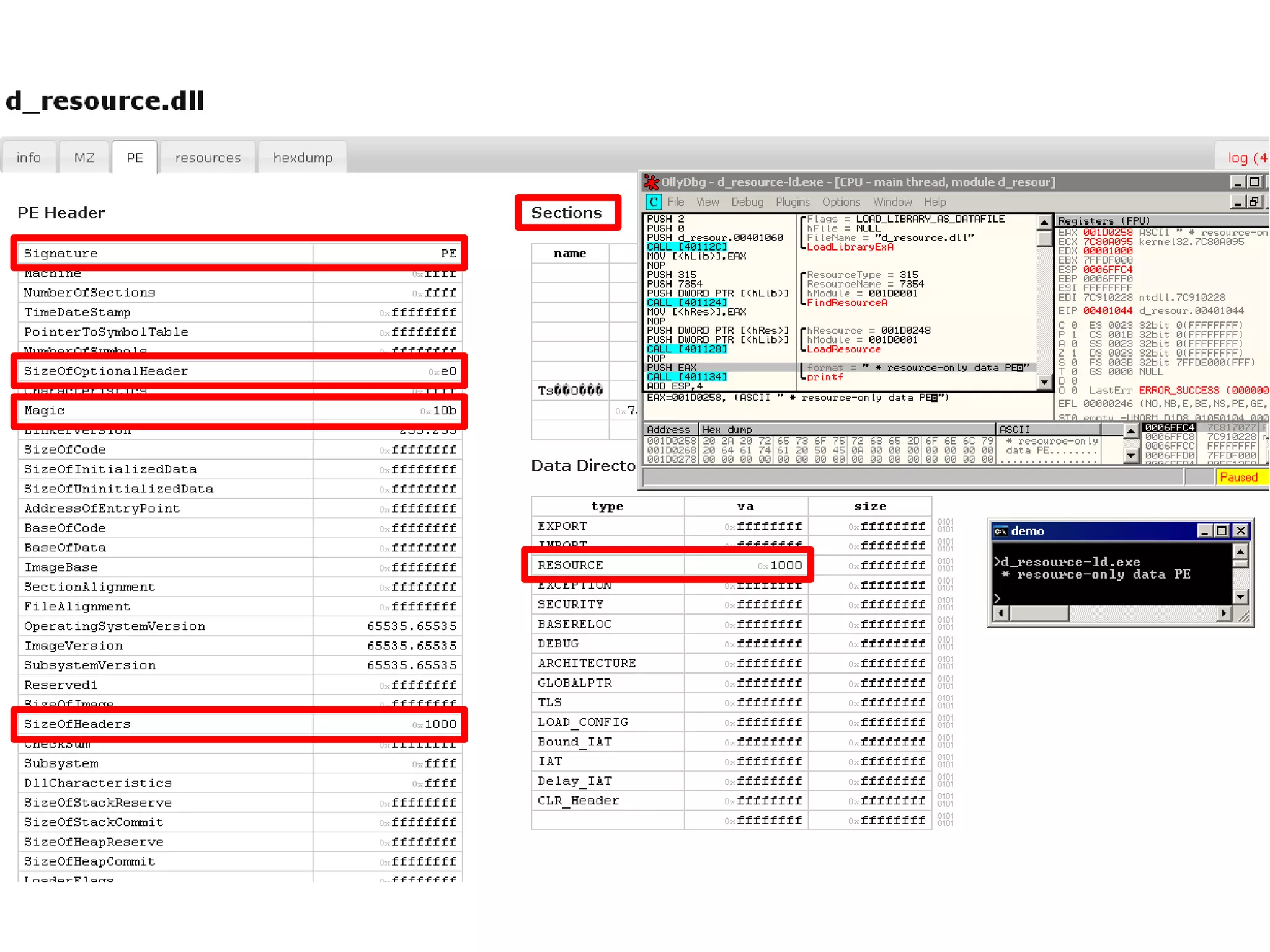
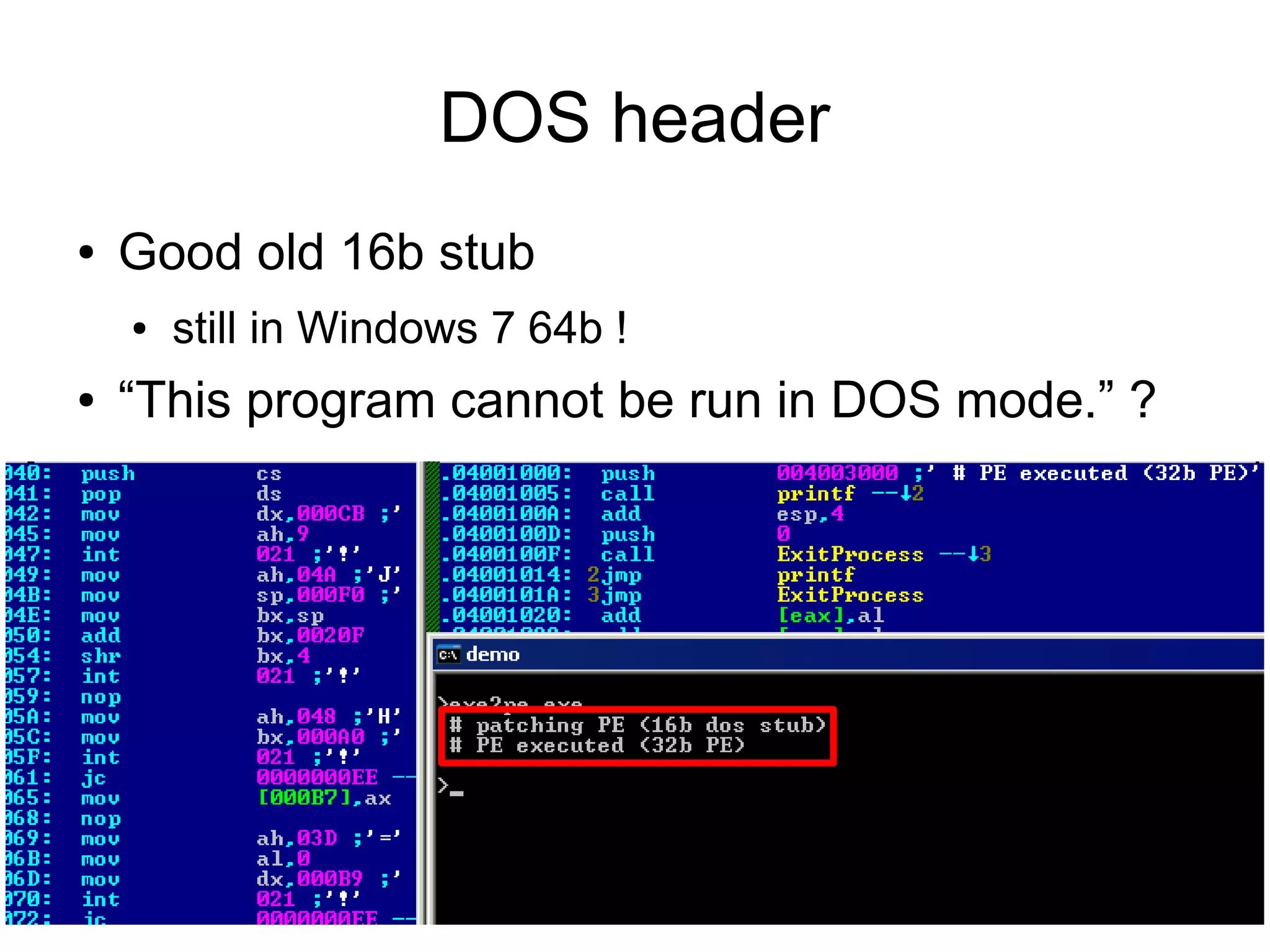
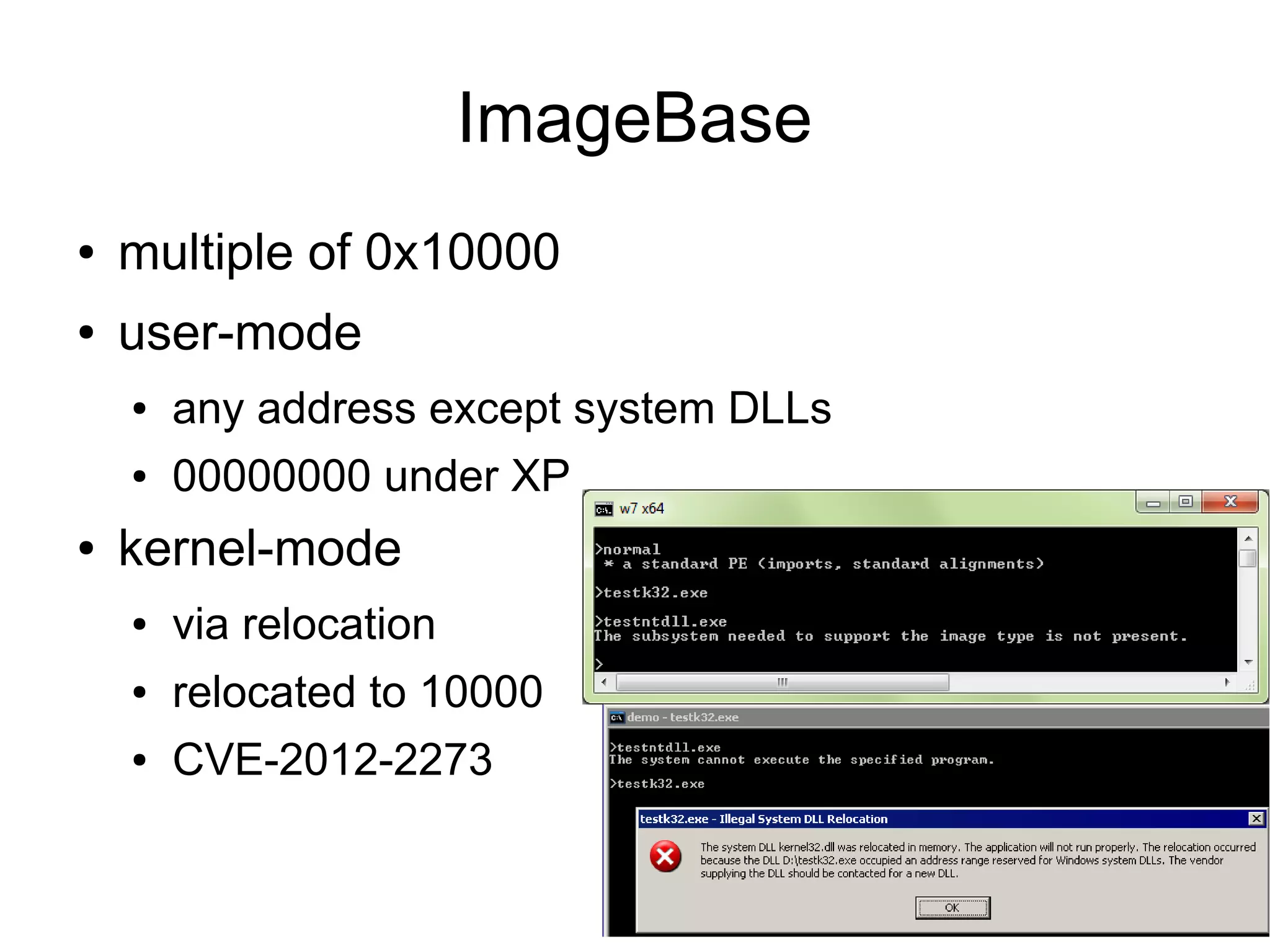
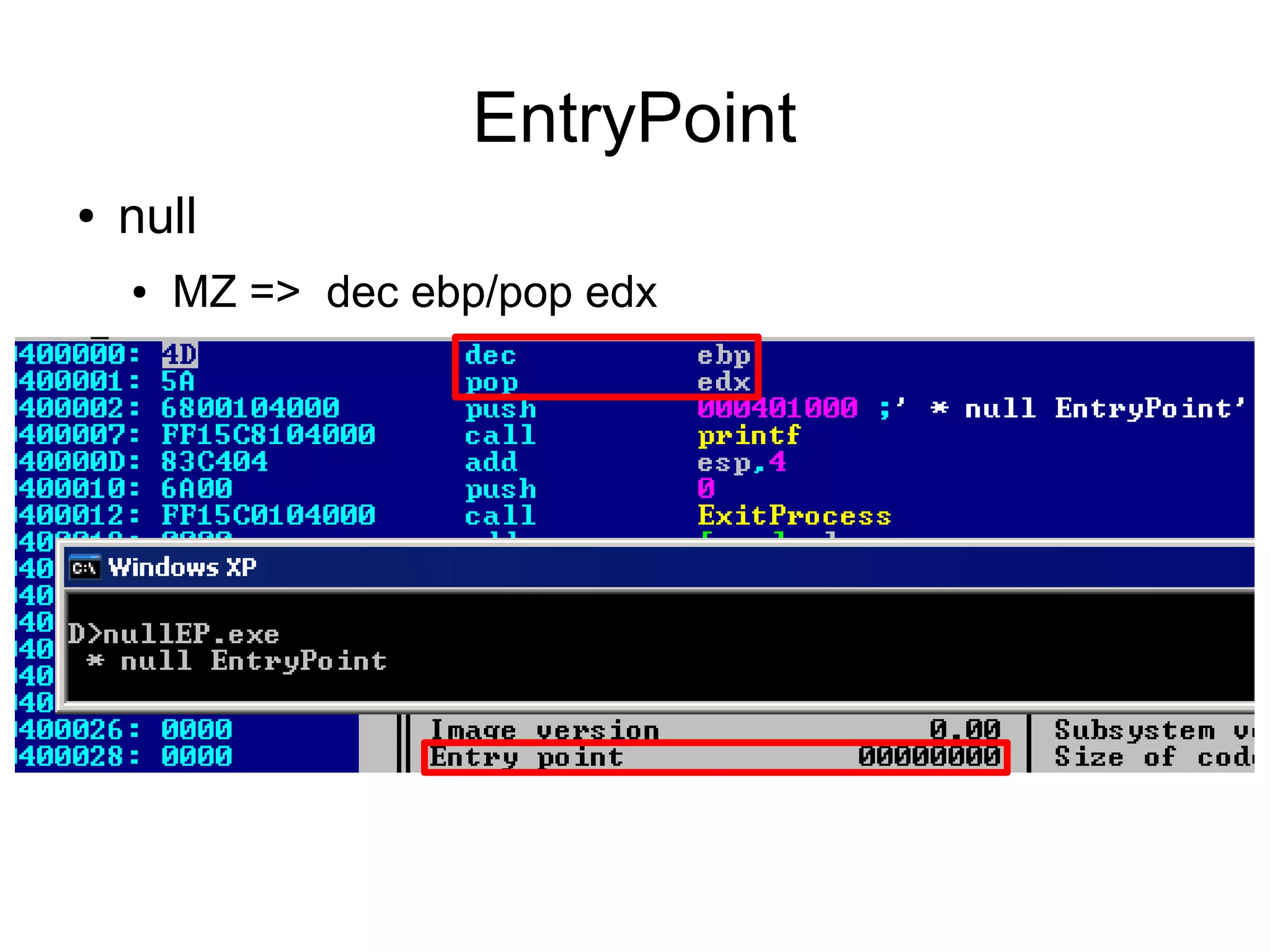
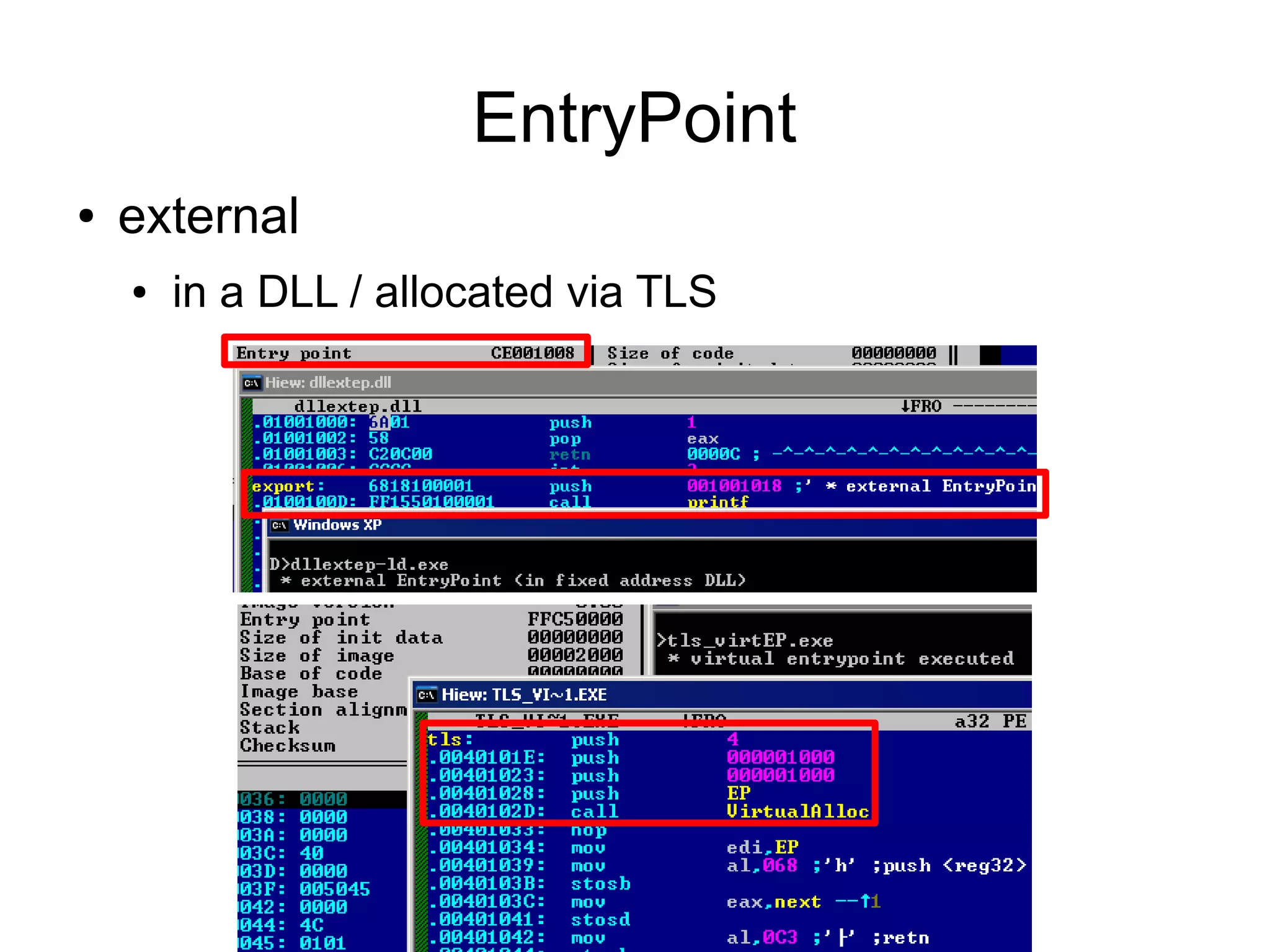
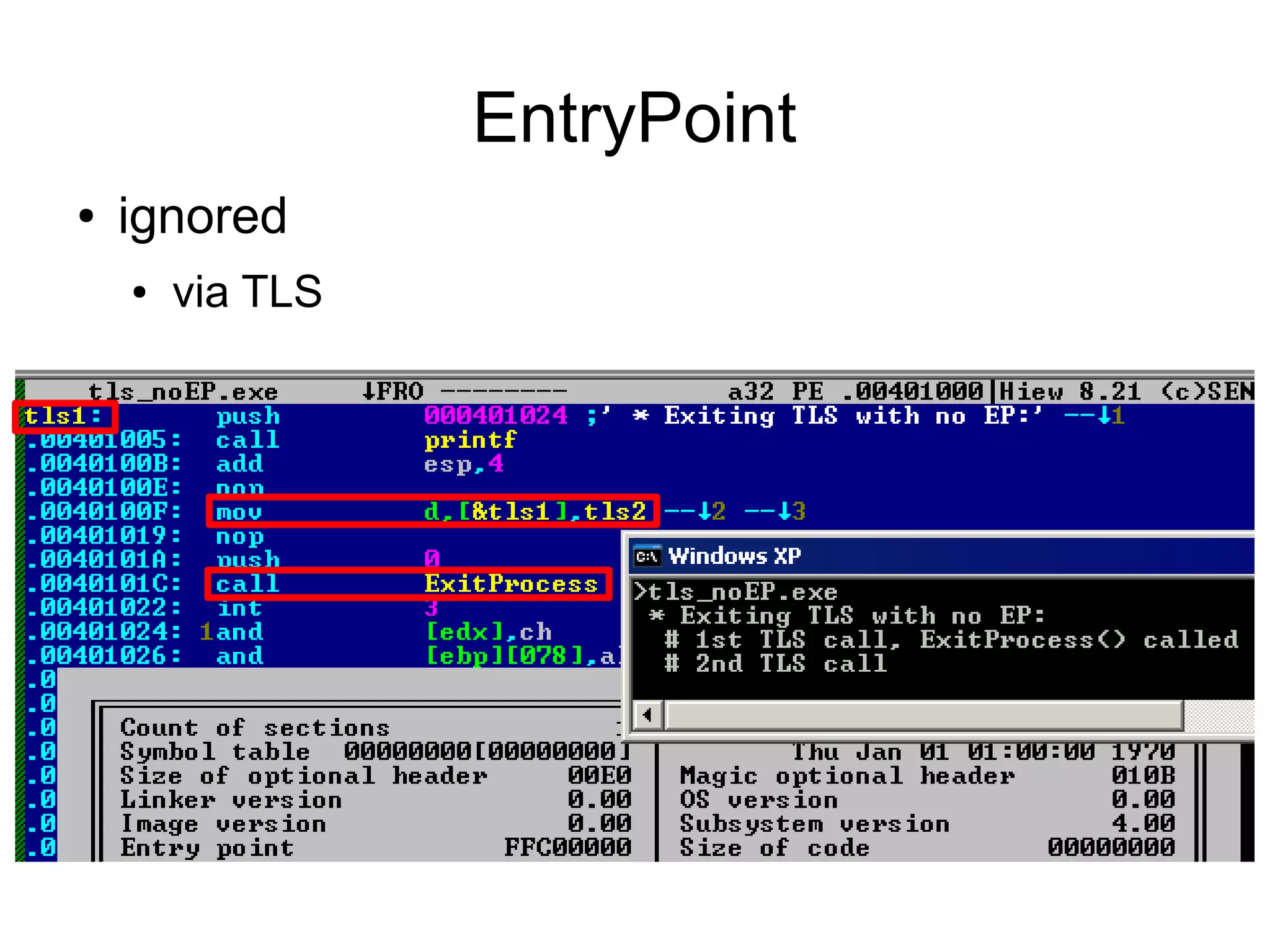
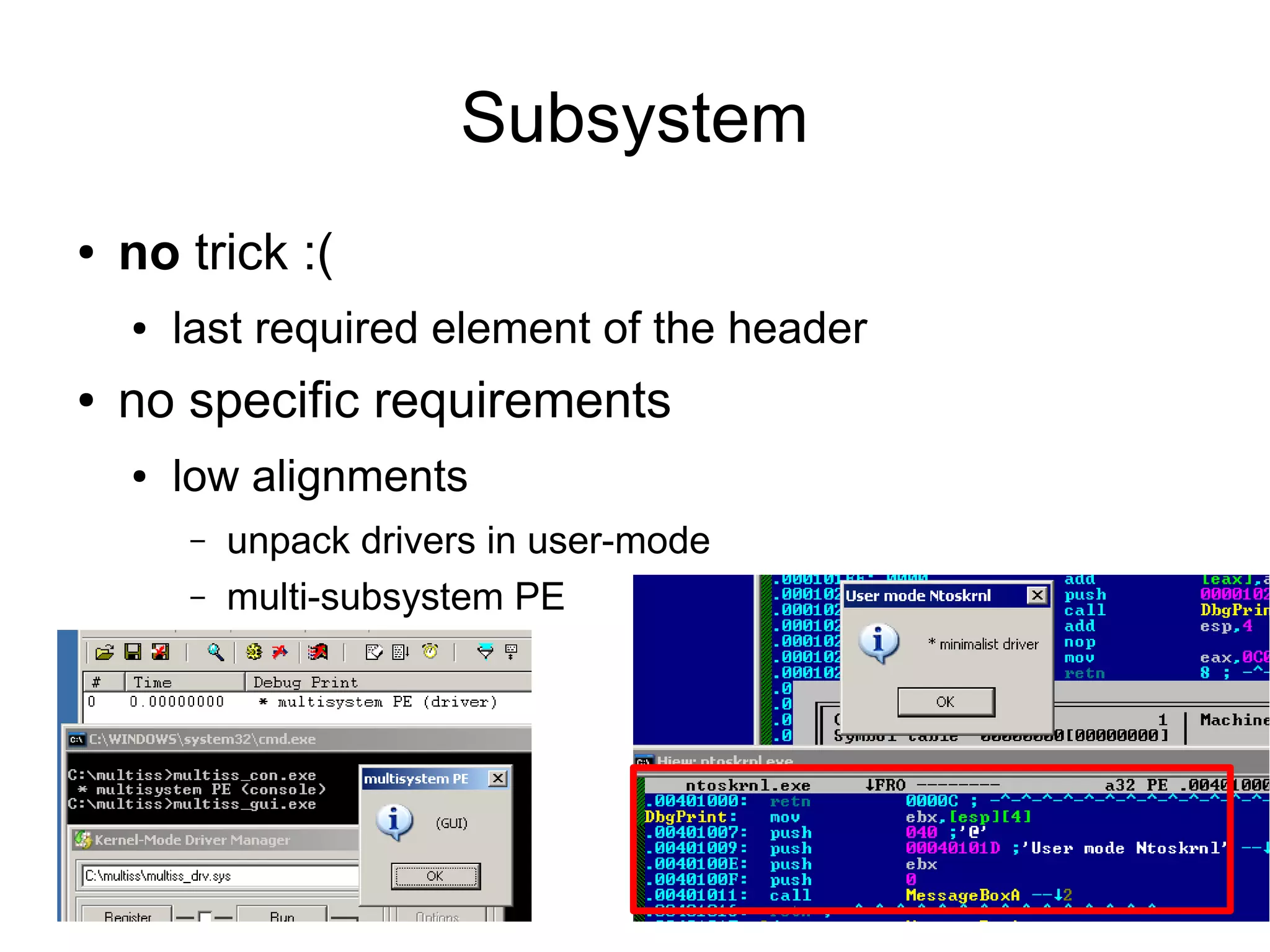
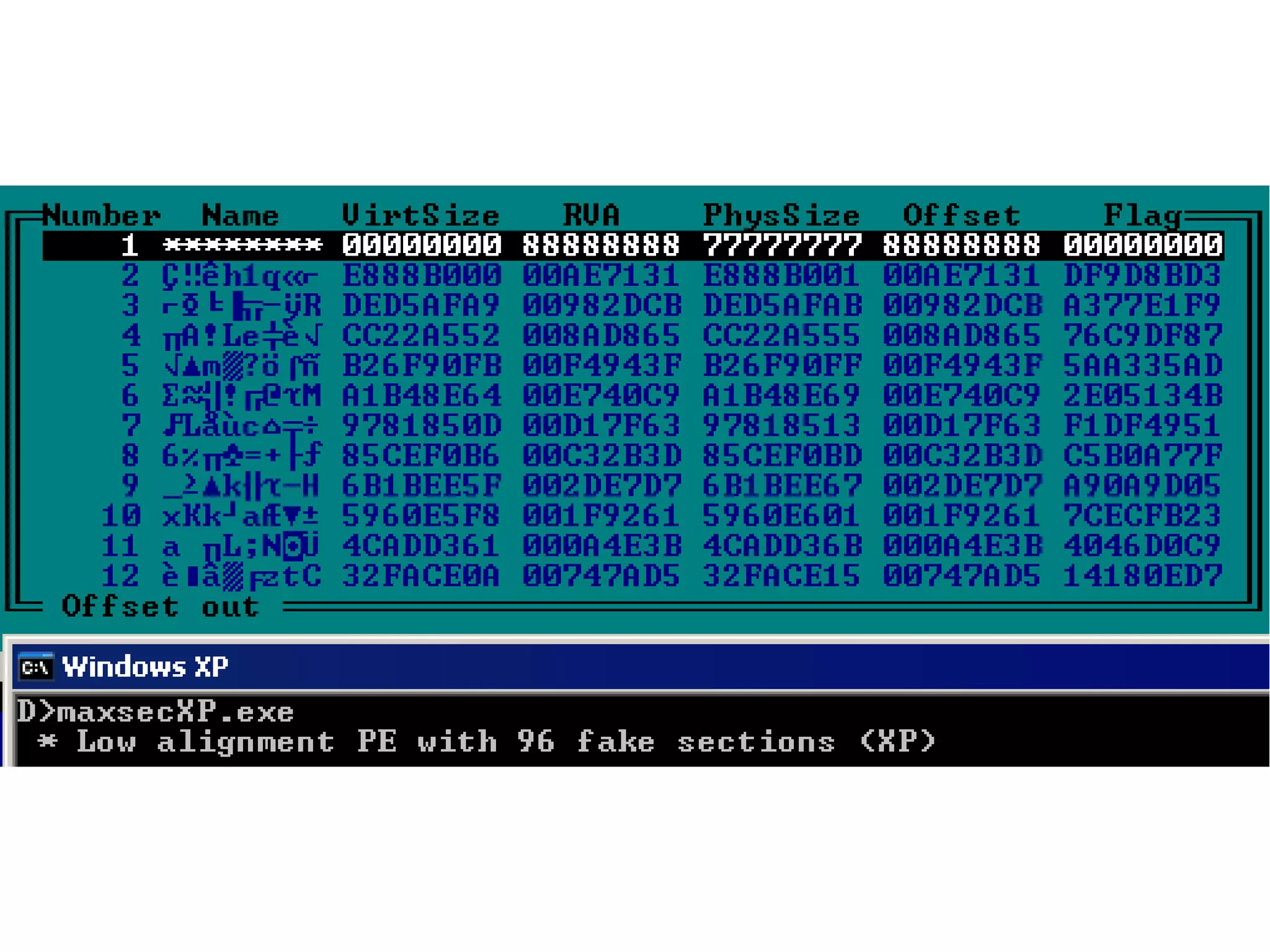
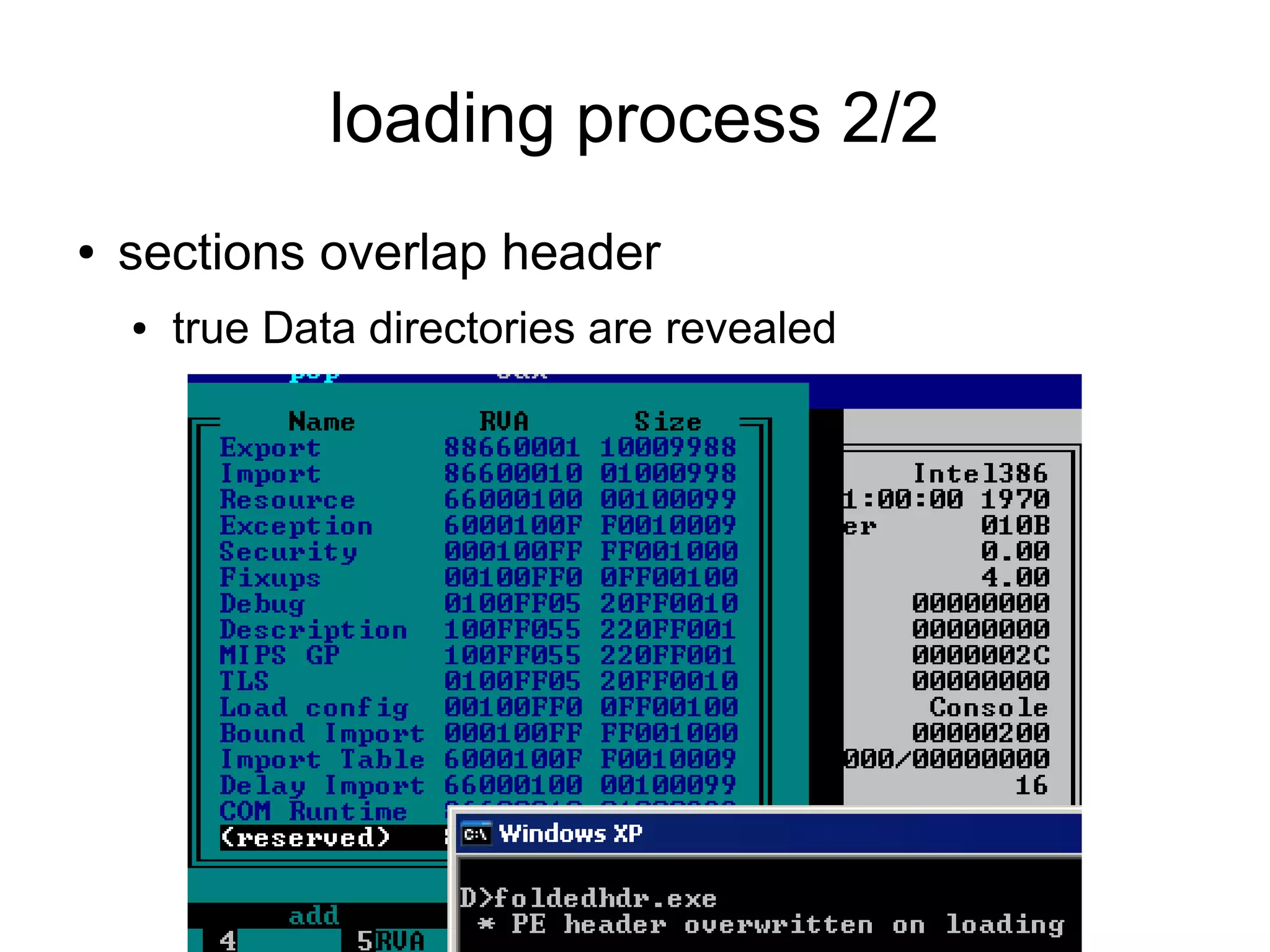
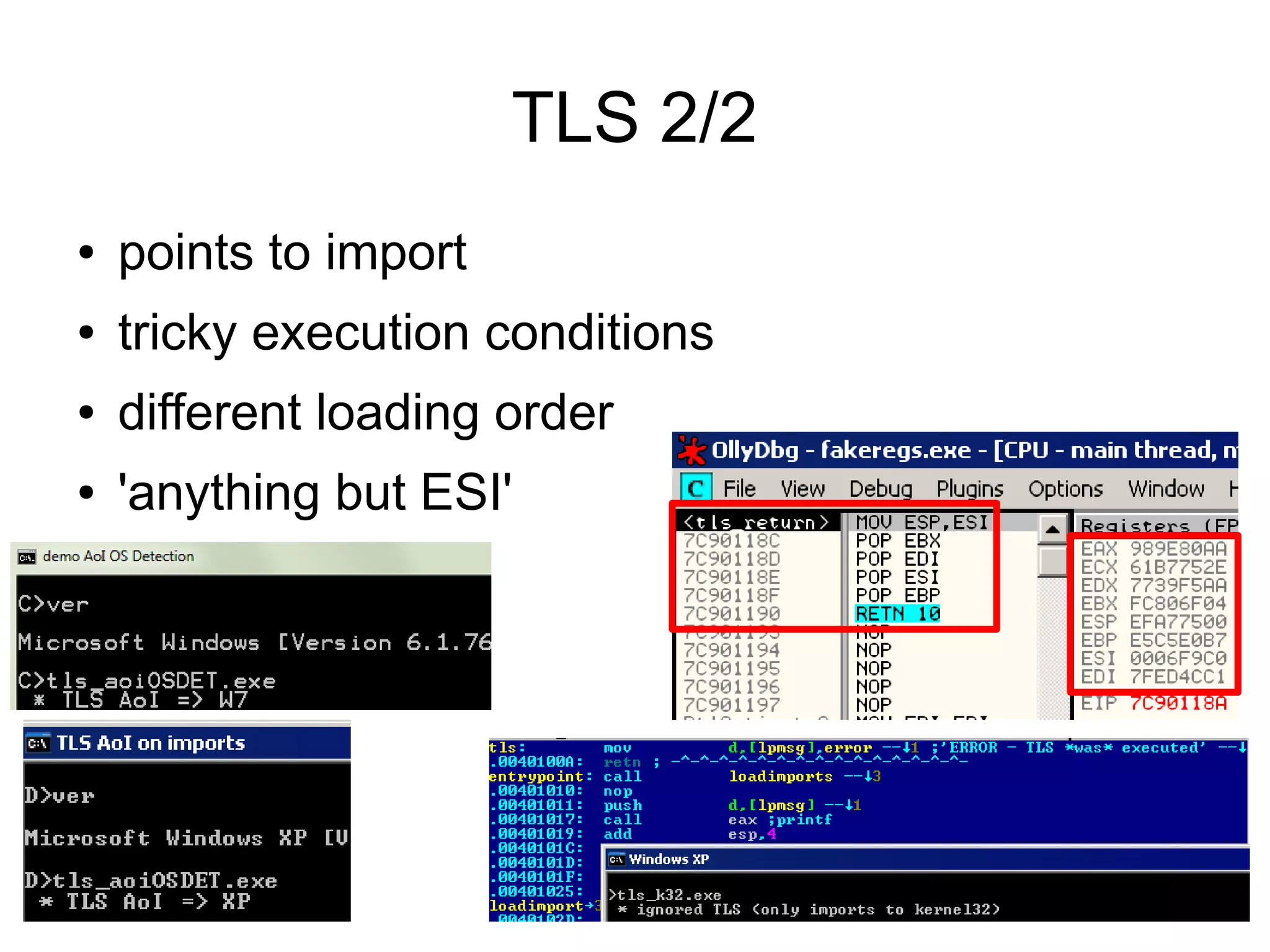
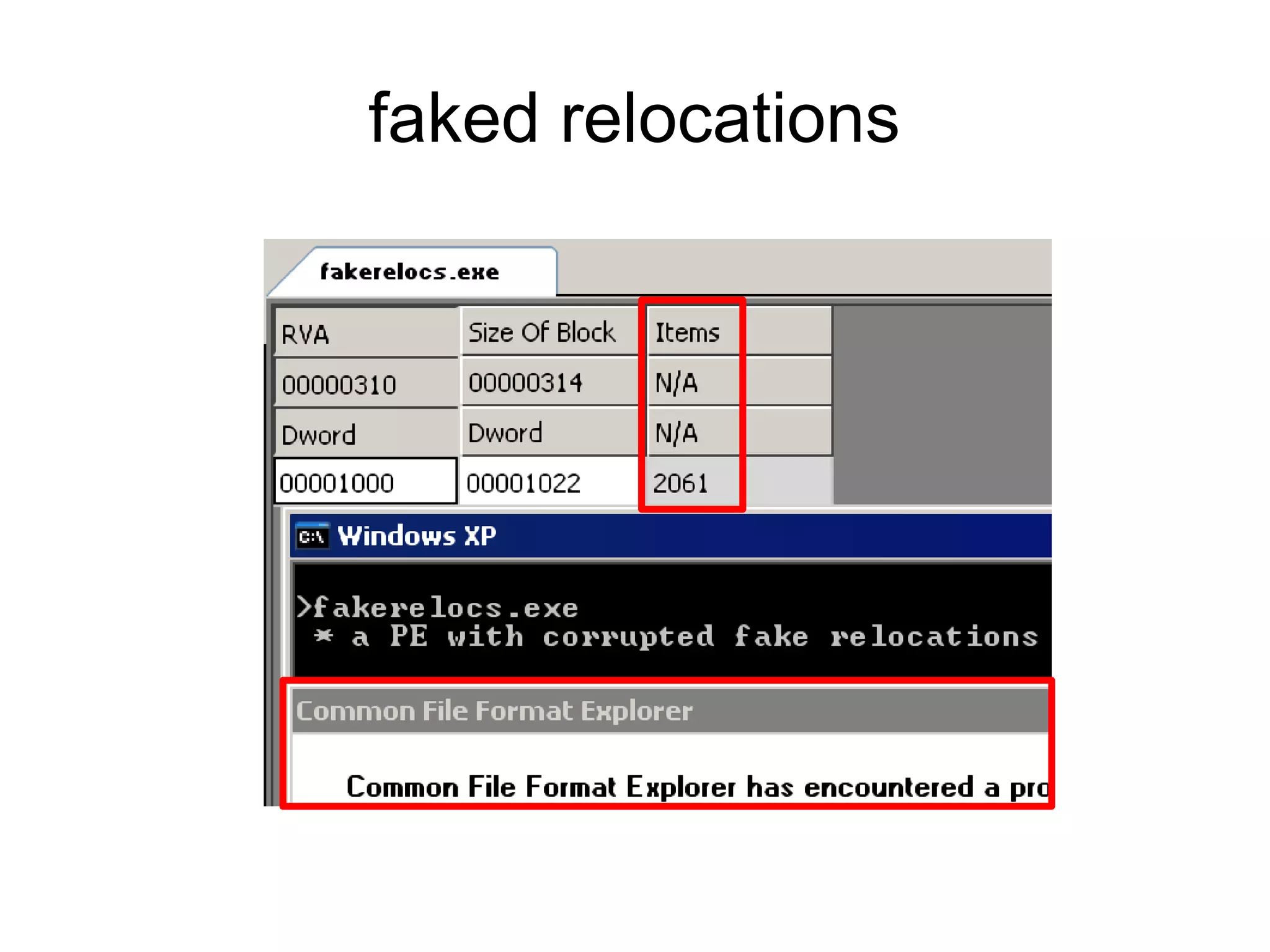
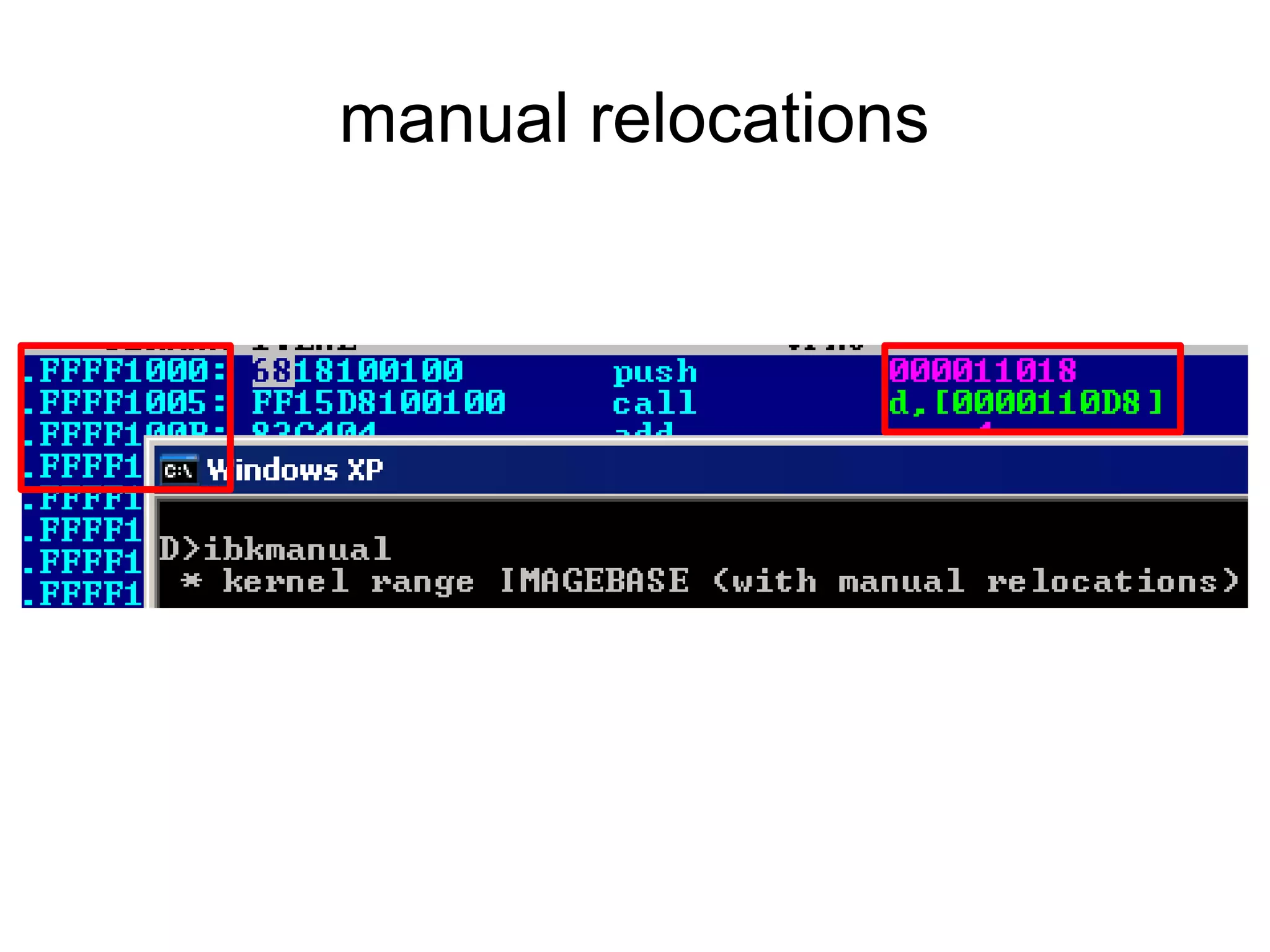
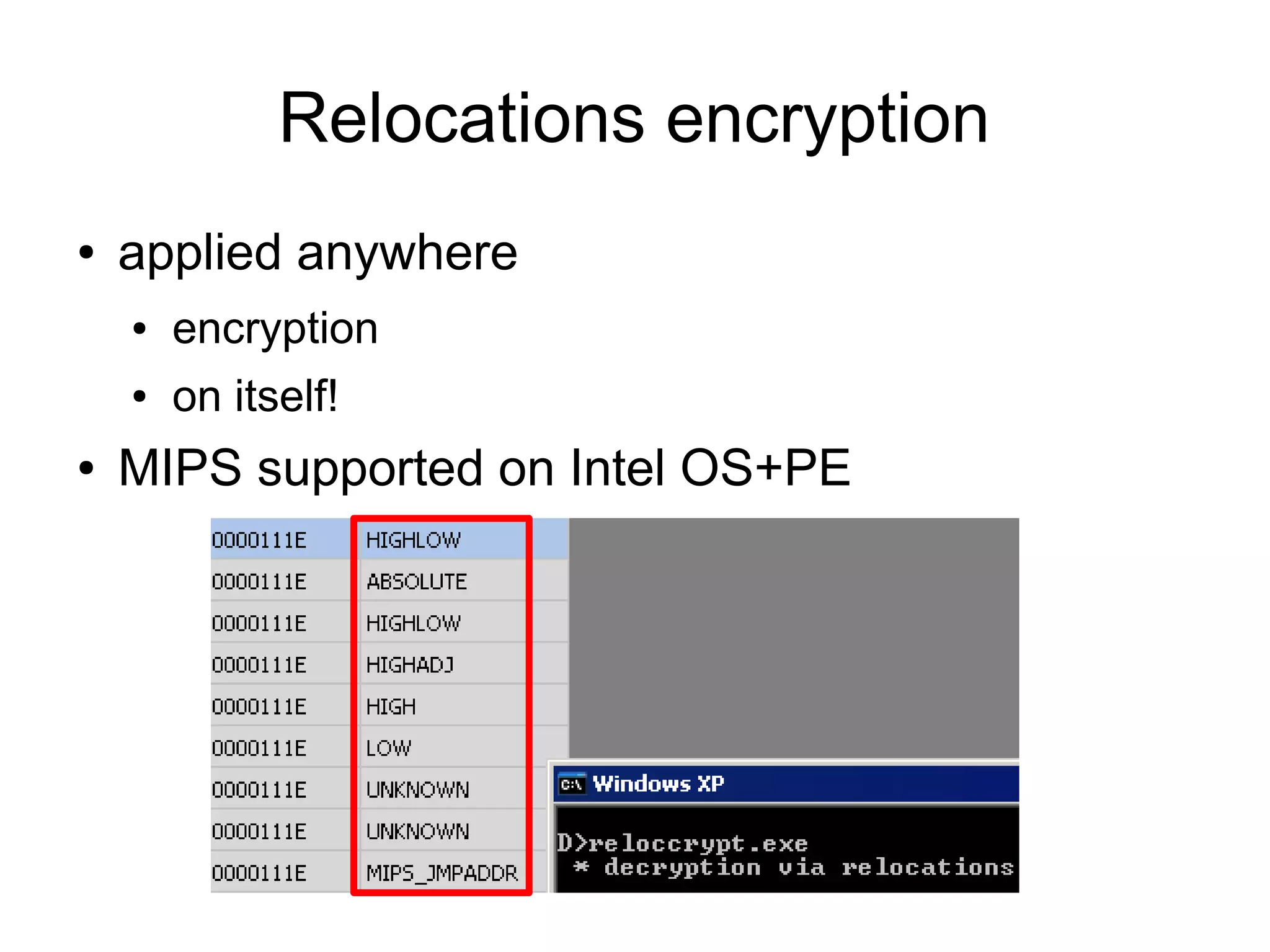
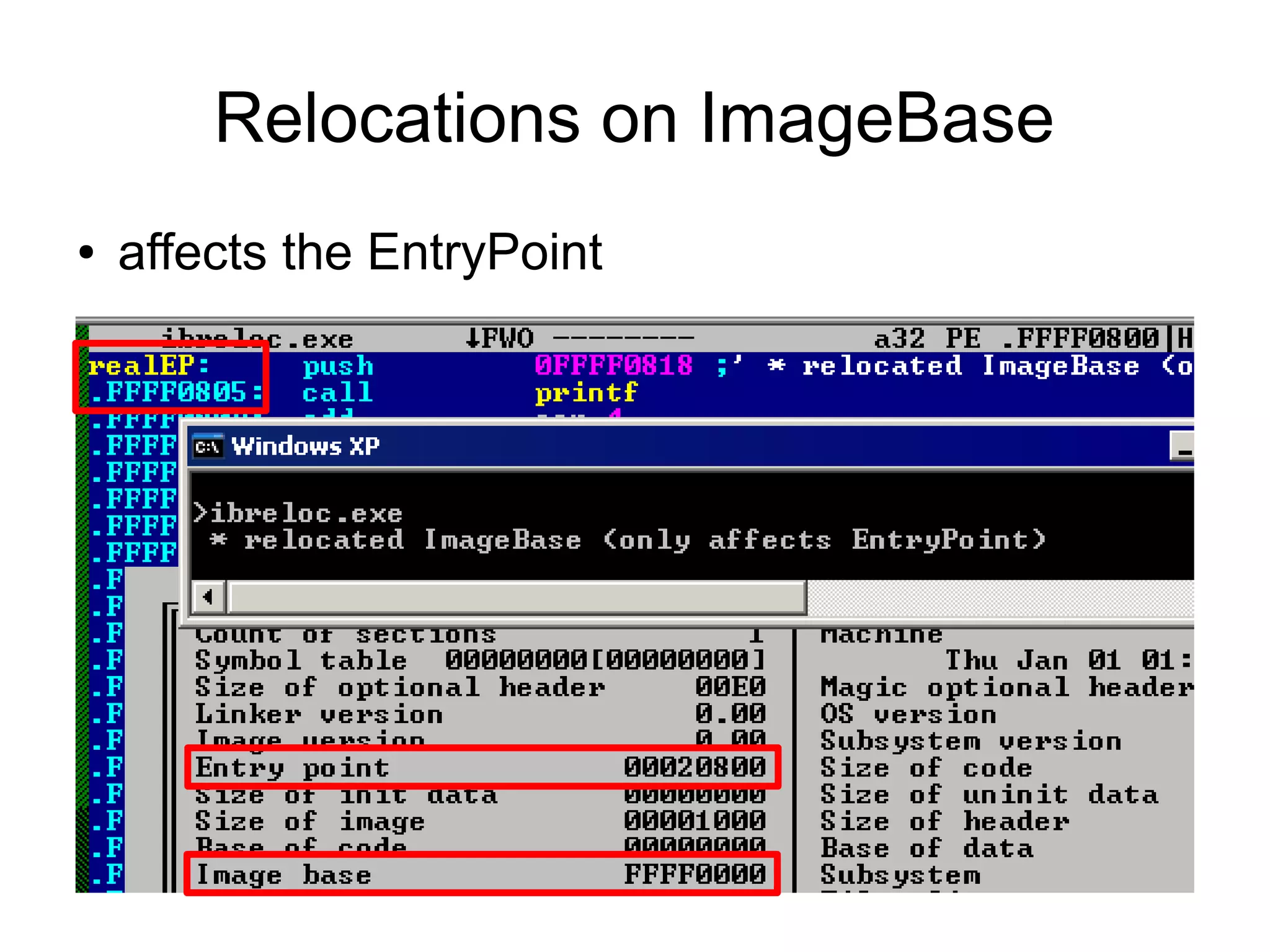
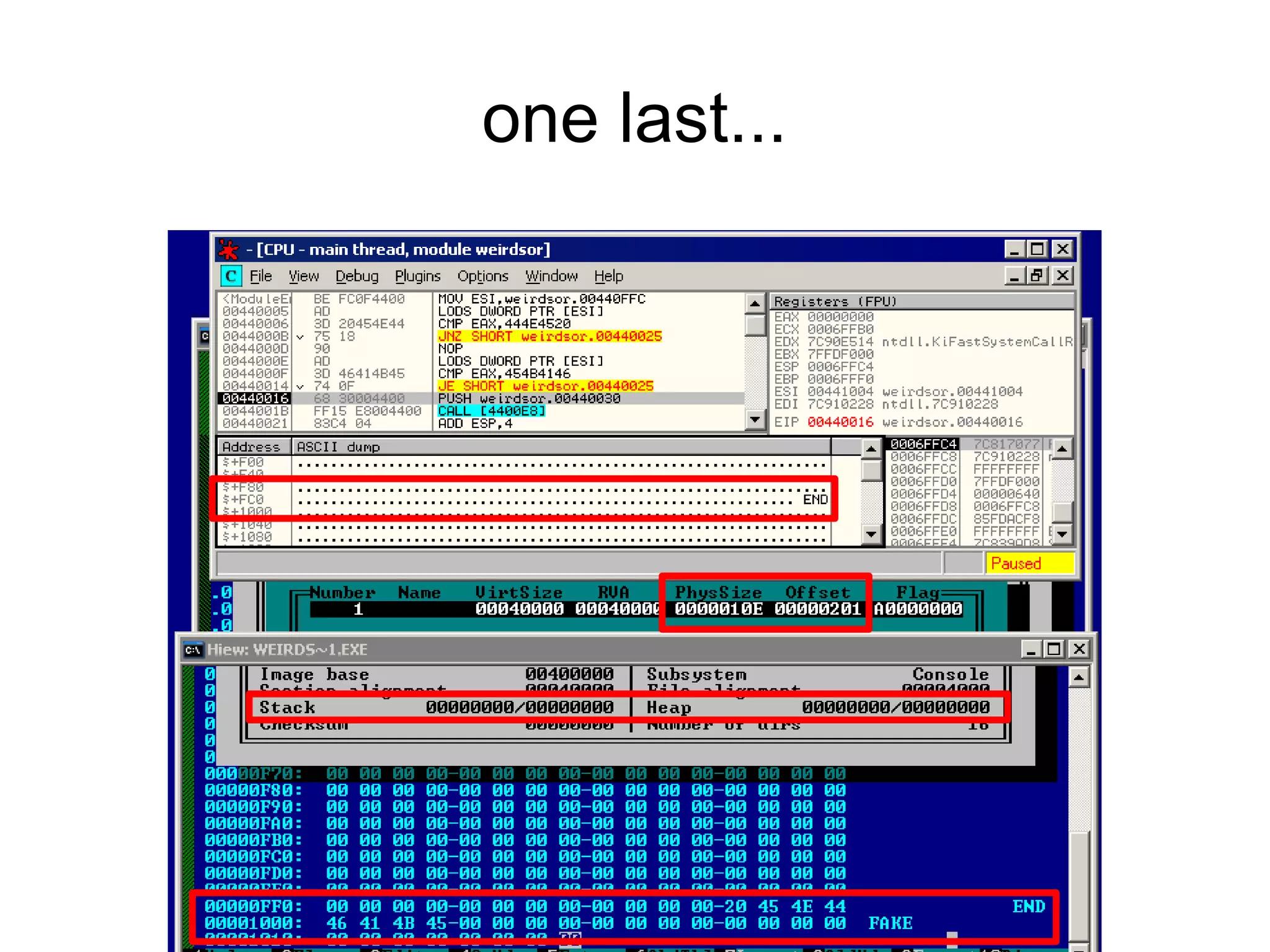
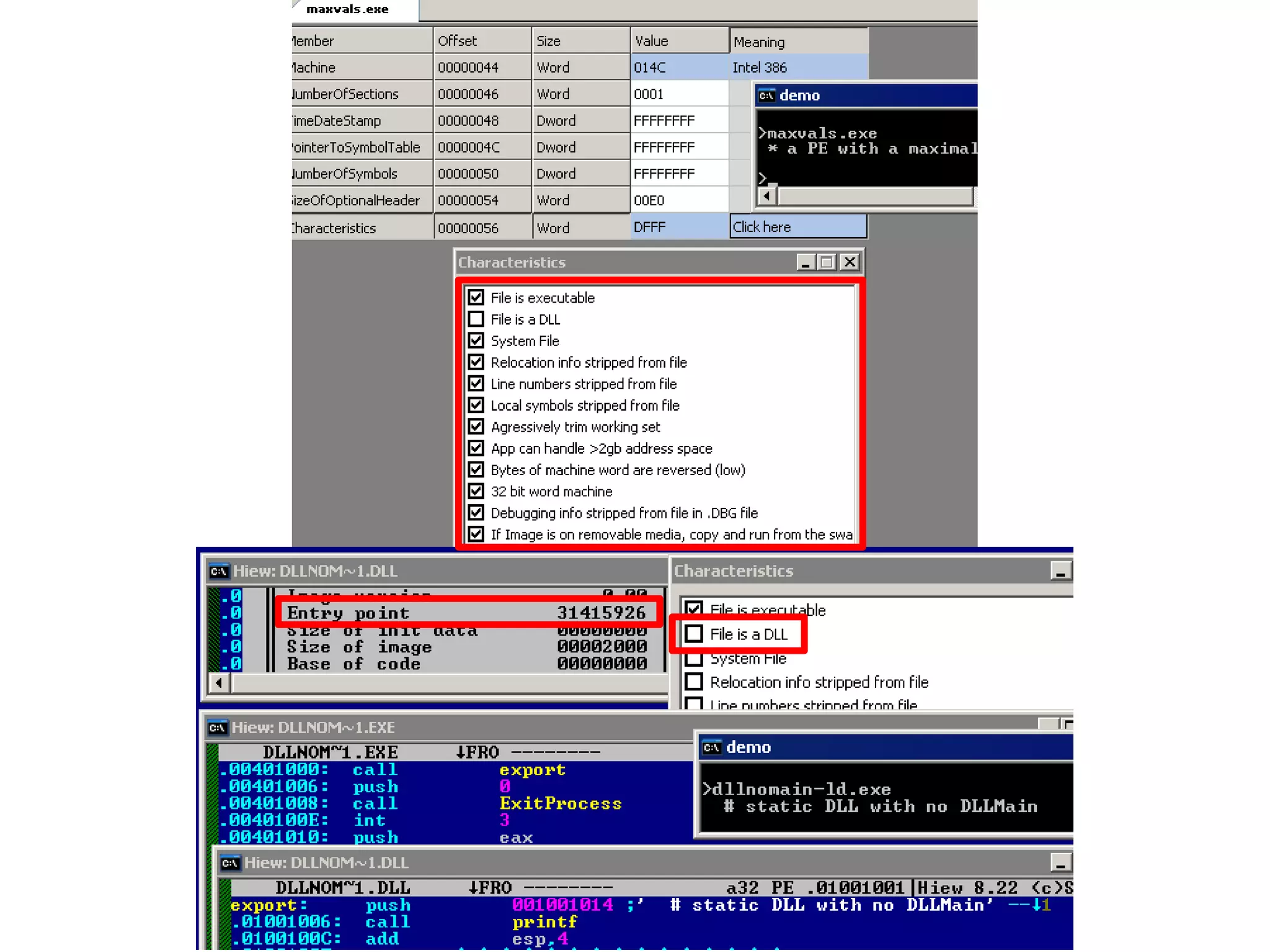
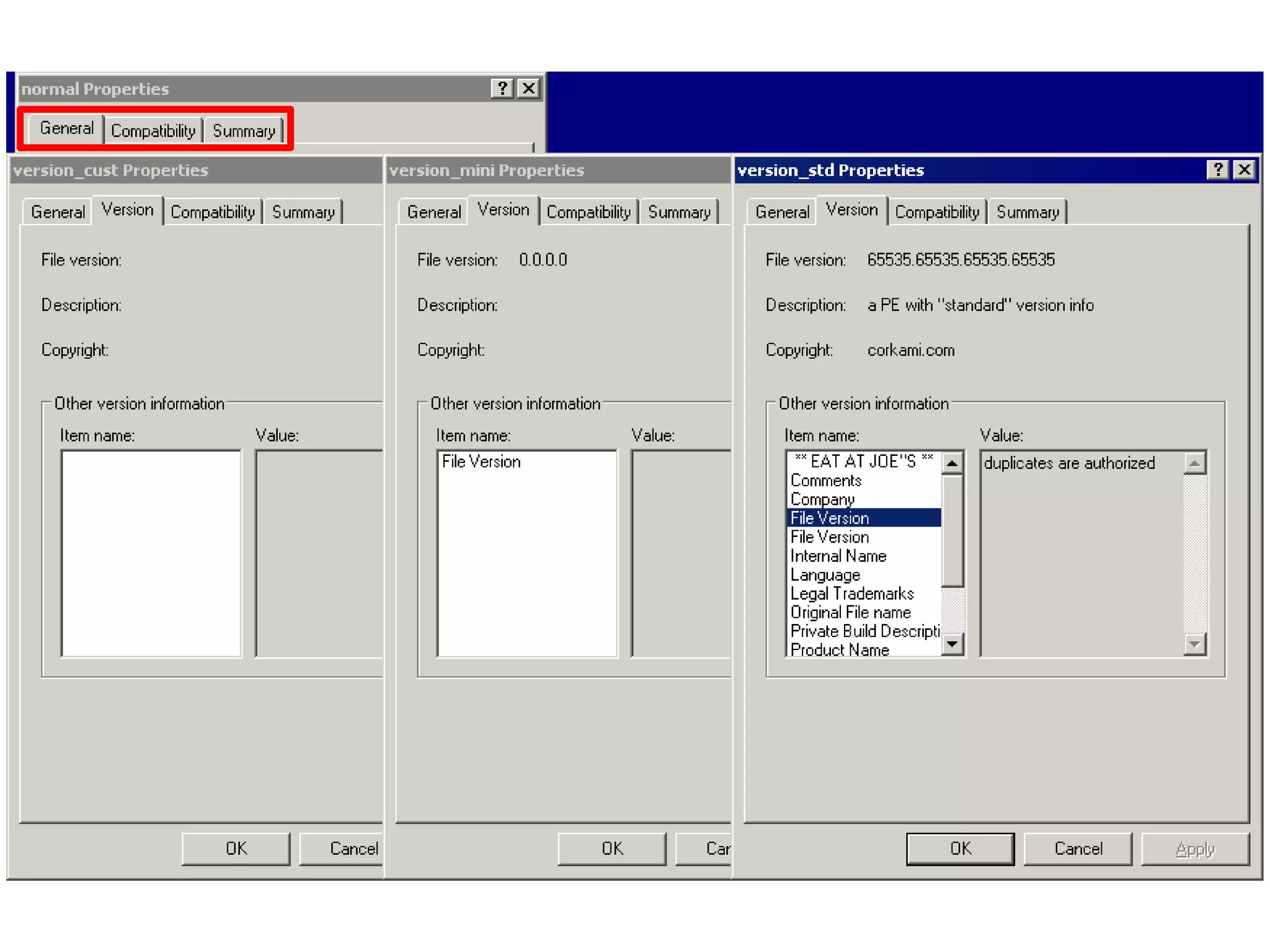
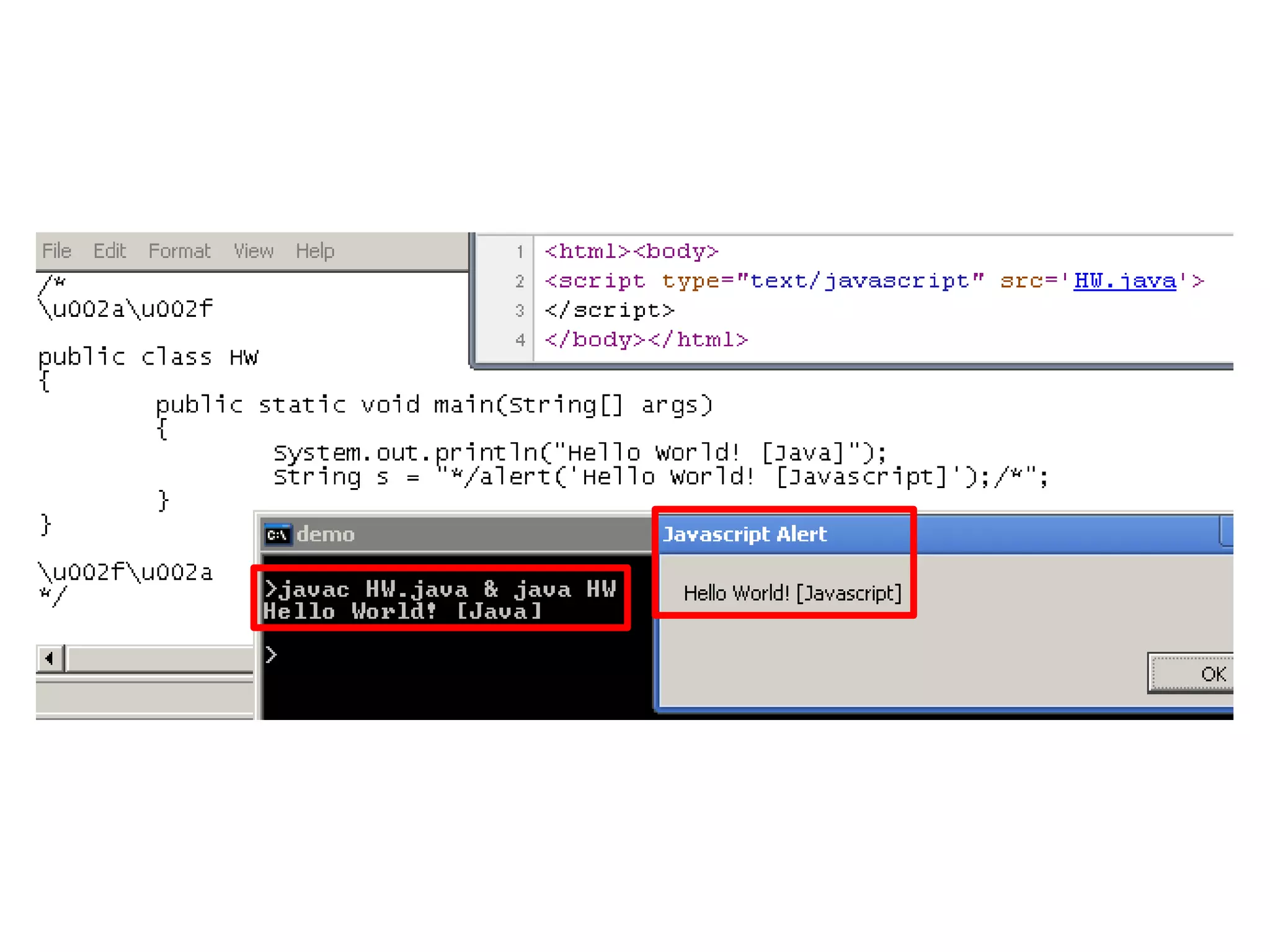
This document discusses oddities that can be found in Portable Executable (PE) file formats. It describes how static elements like the DOS header, image base, entry point, and sections can be manipulated in non-standard ways. It also explains how dynamic loading behaviors are affected by these oddities, such as through the thread local storage, relocations, and different parsing of headers and data directories between on-disk and in-memory formats. The document promotes further understanding of PE files through the use of proof of concepts provided on related websites.