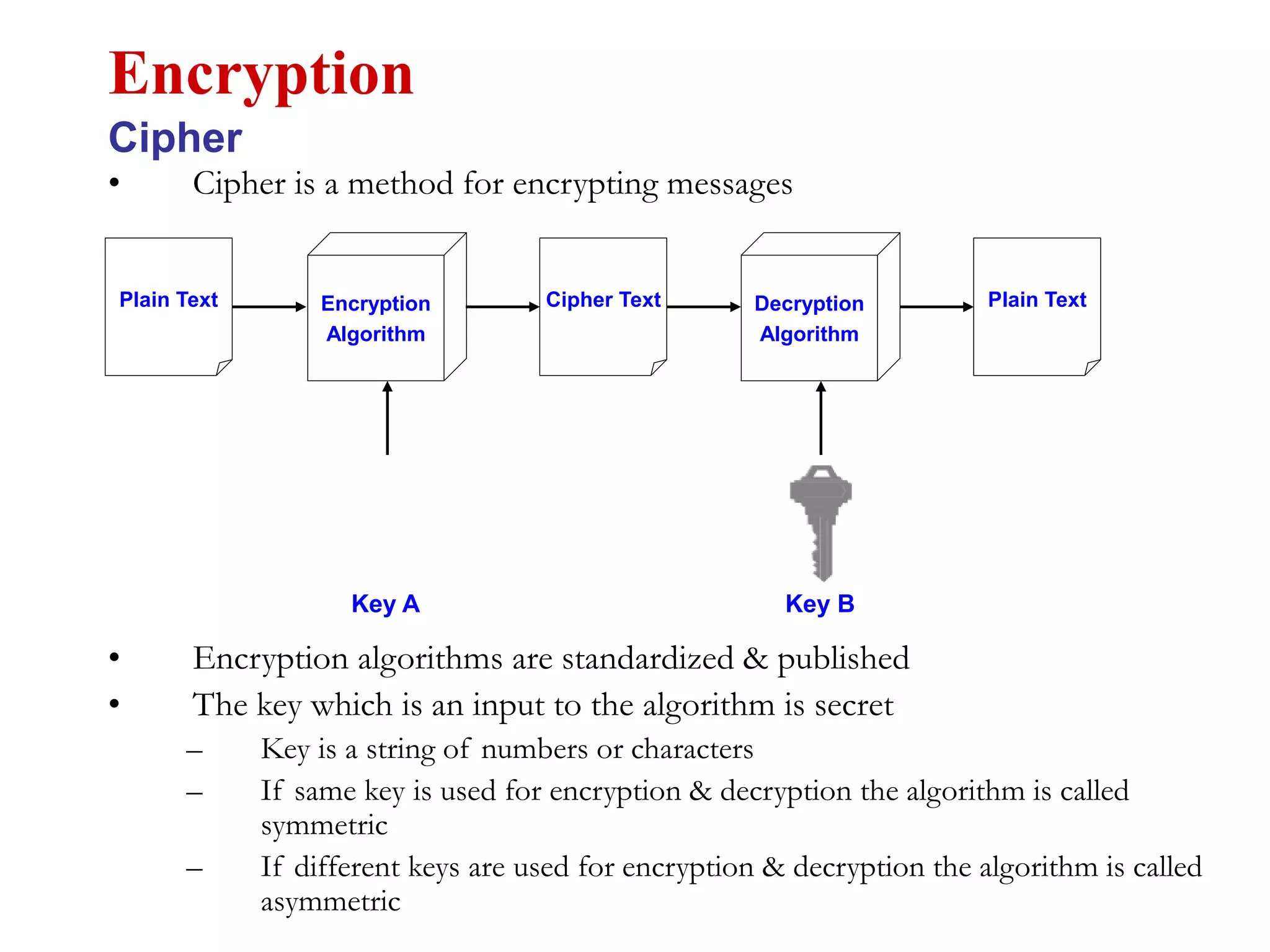
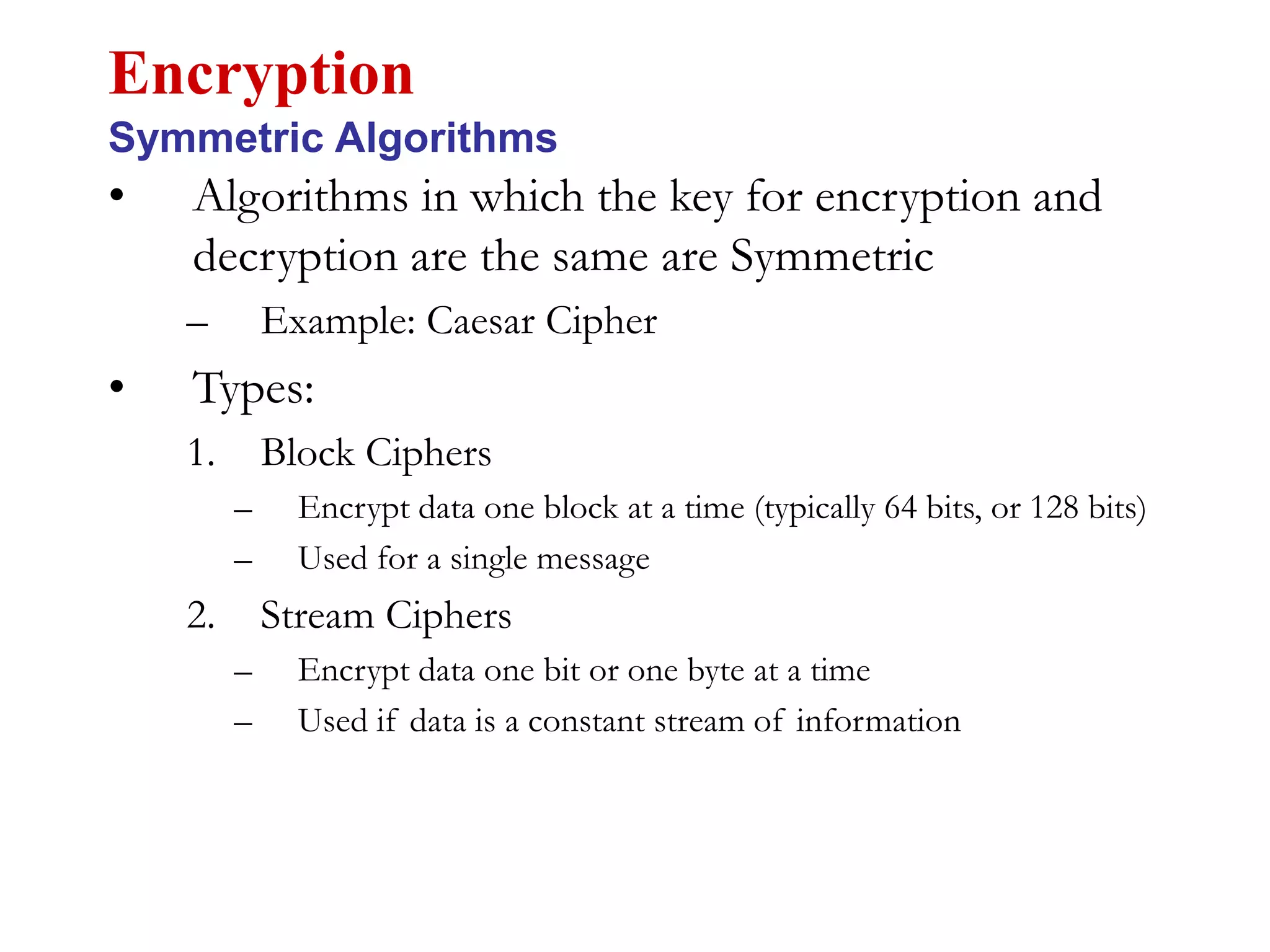
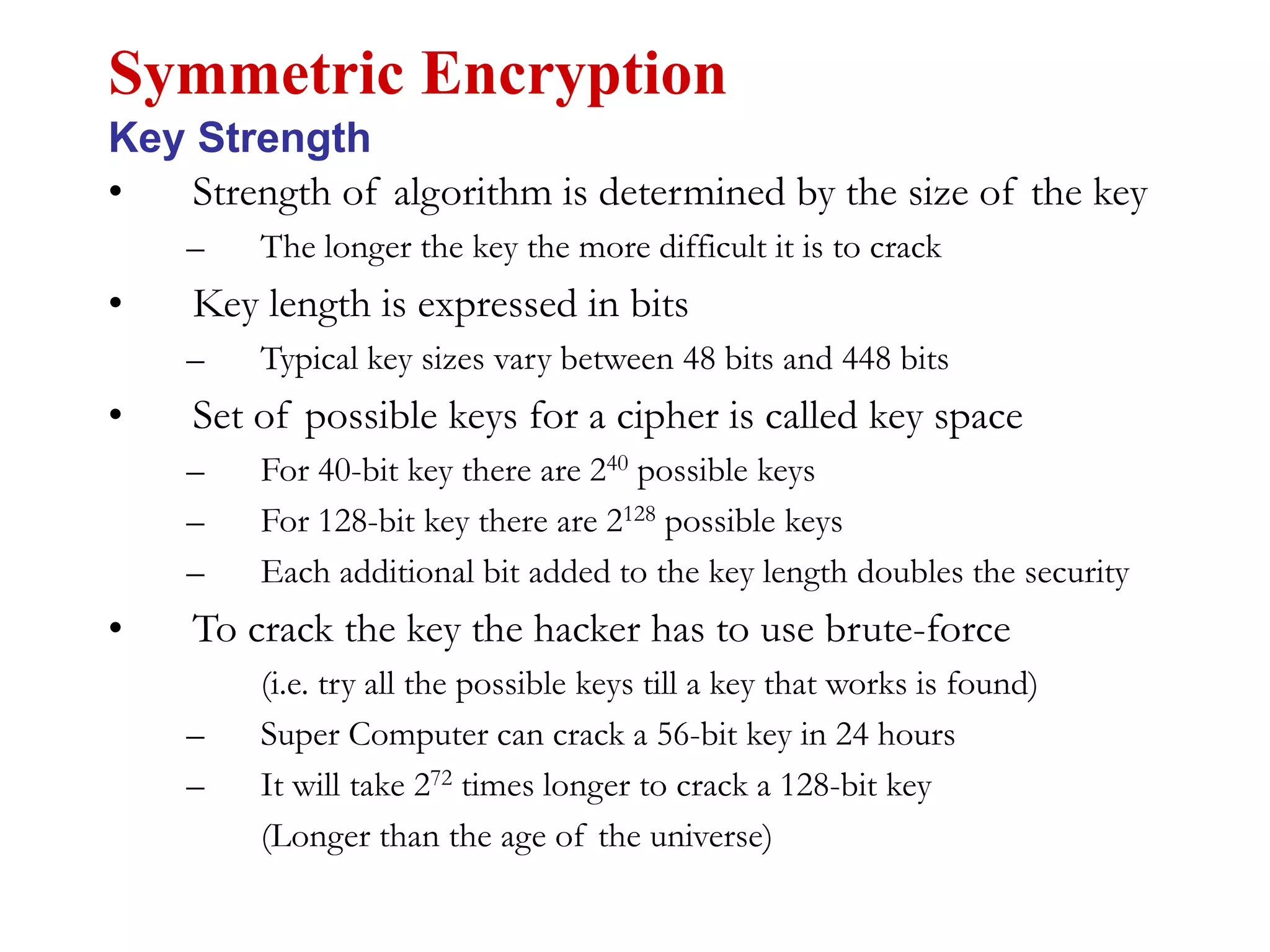
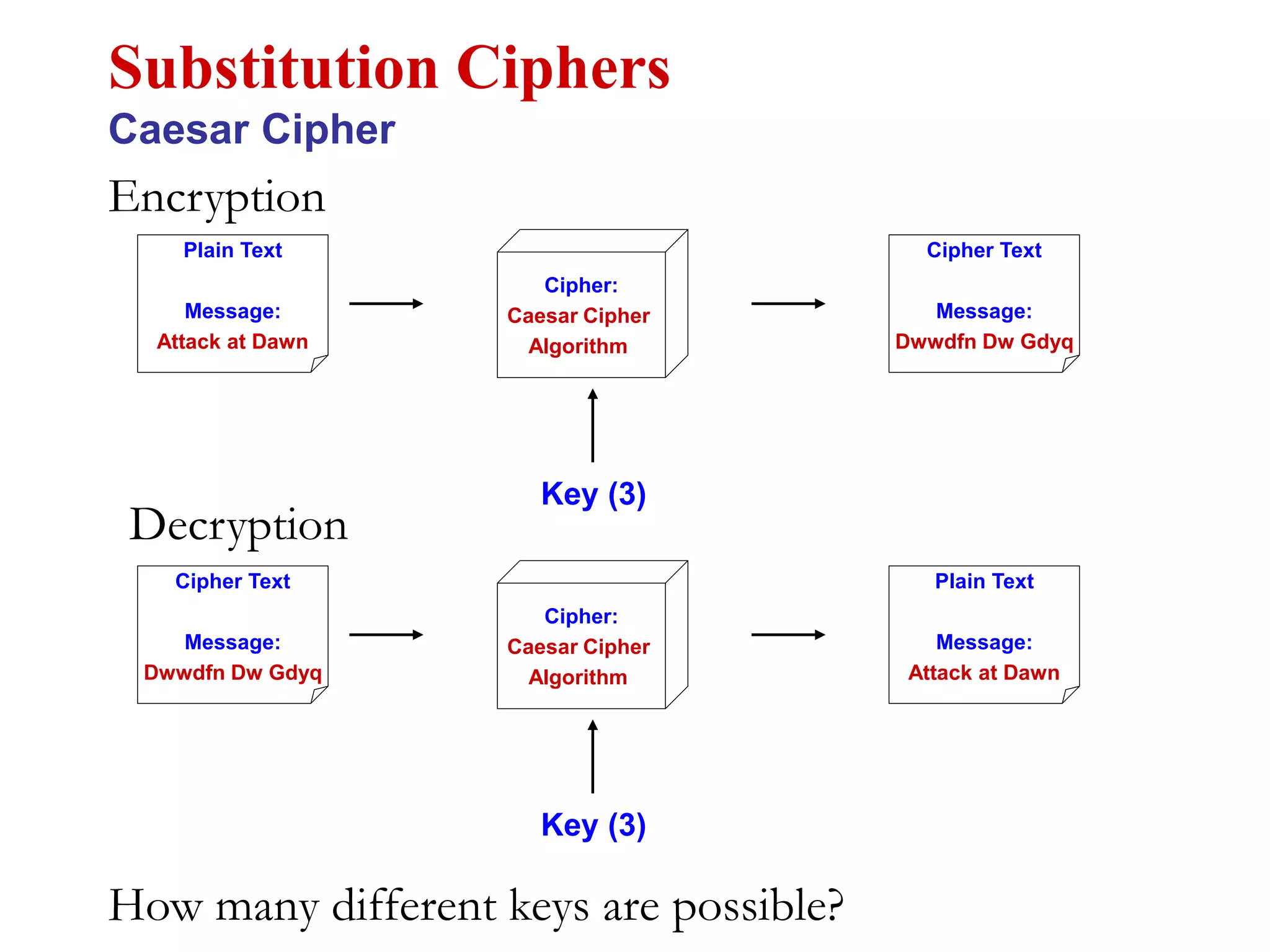
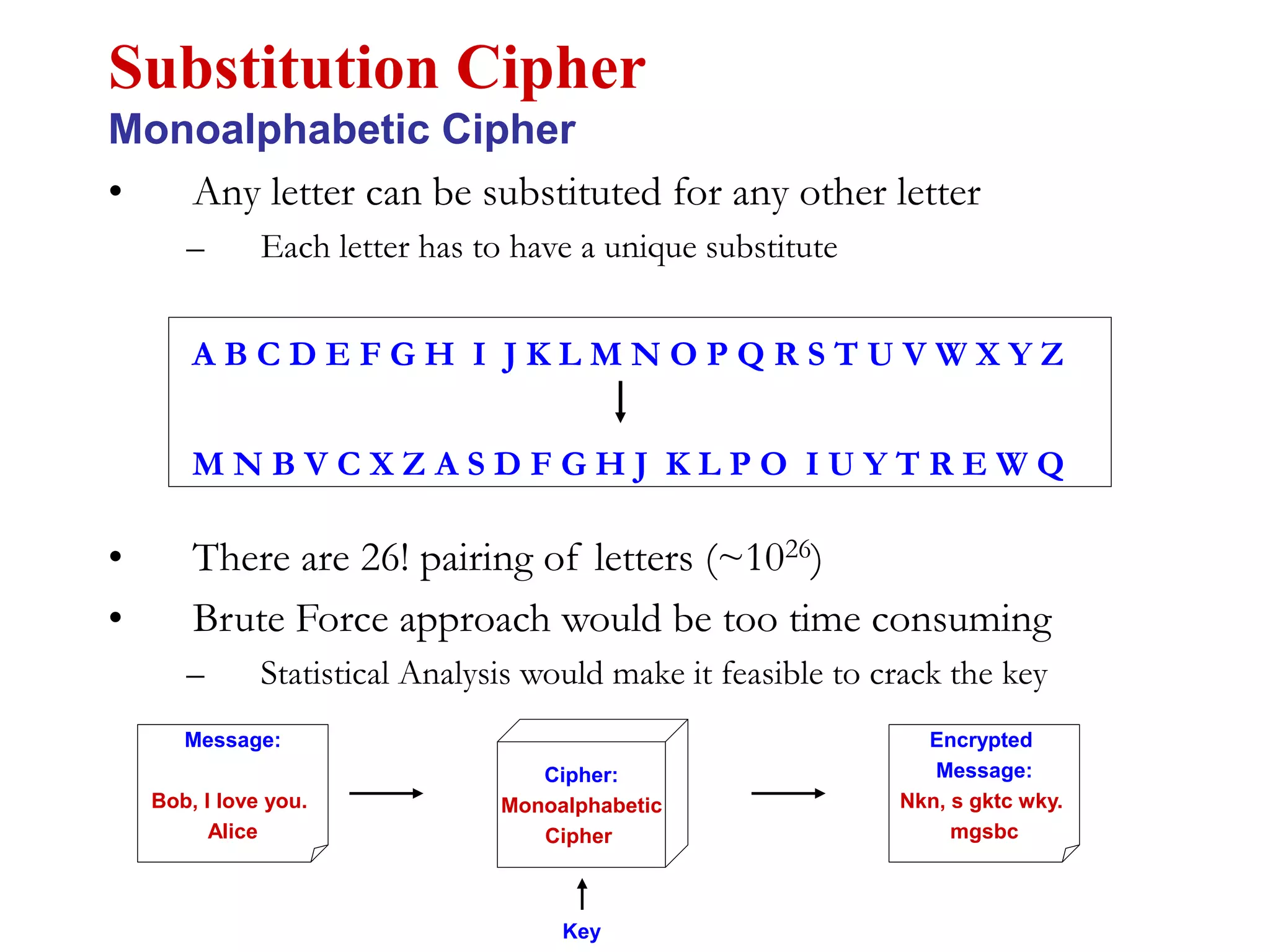
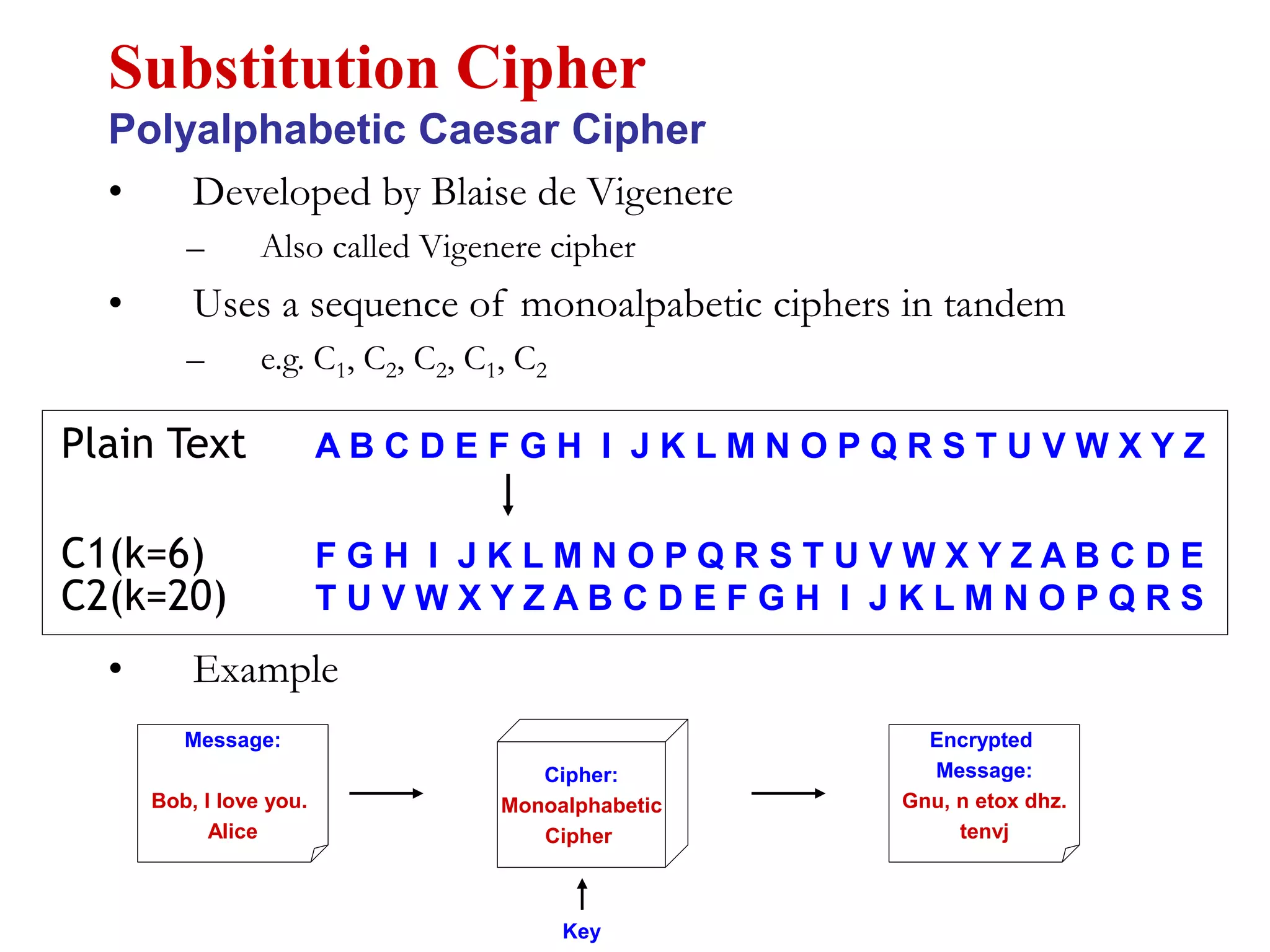
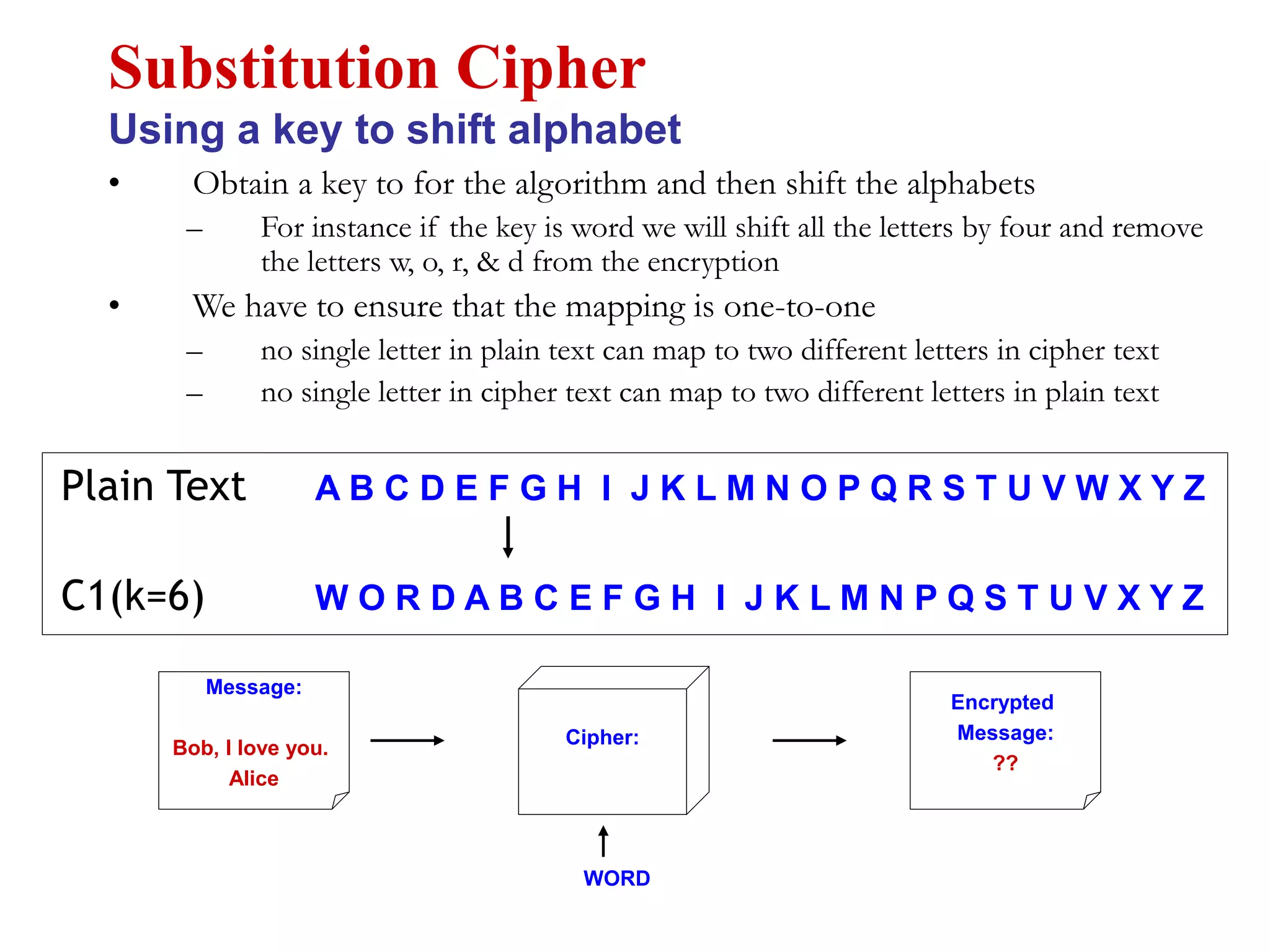
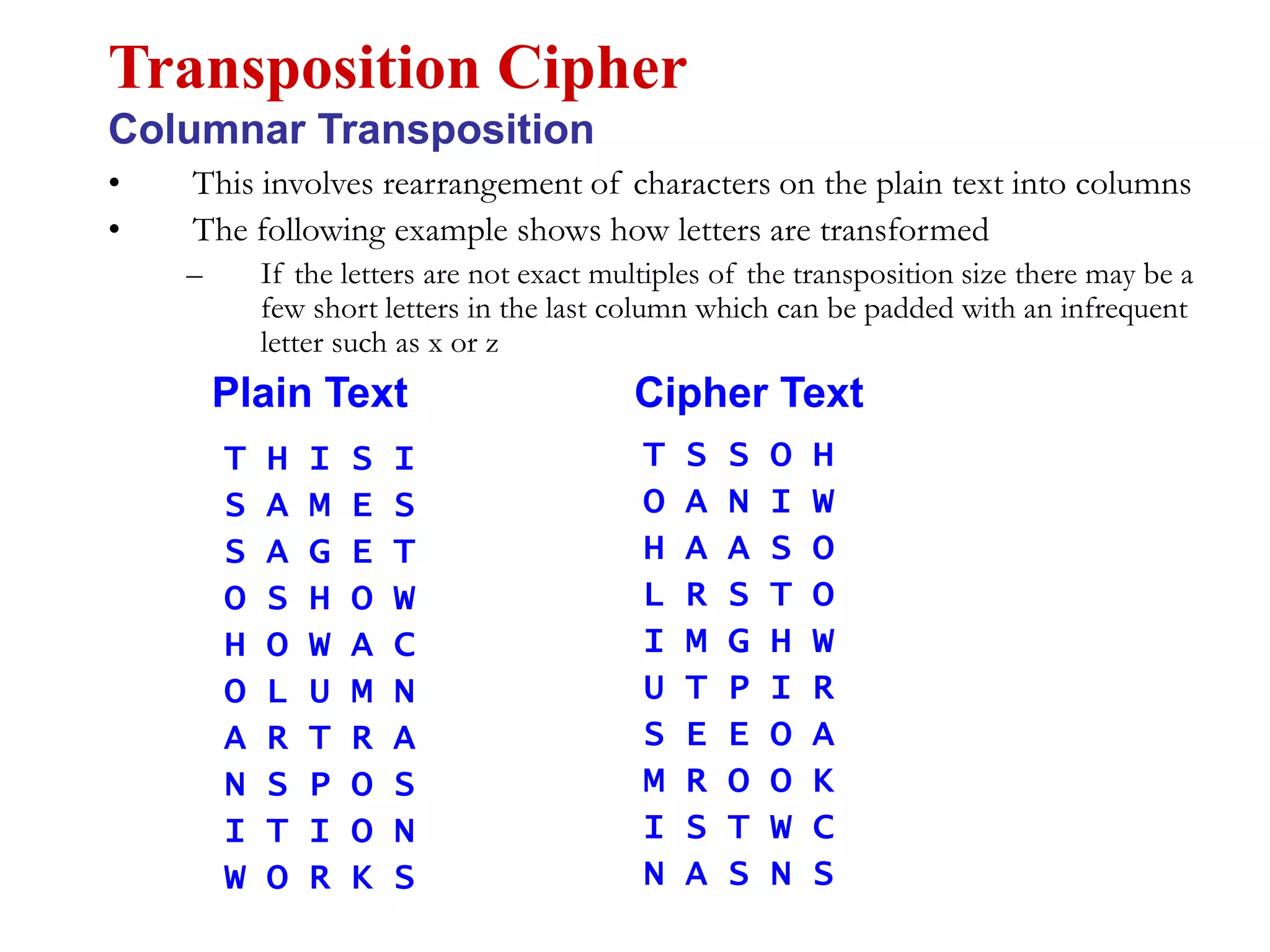
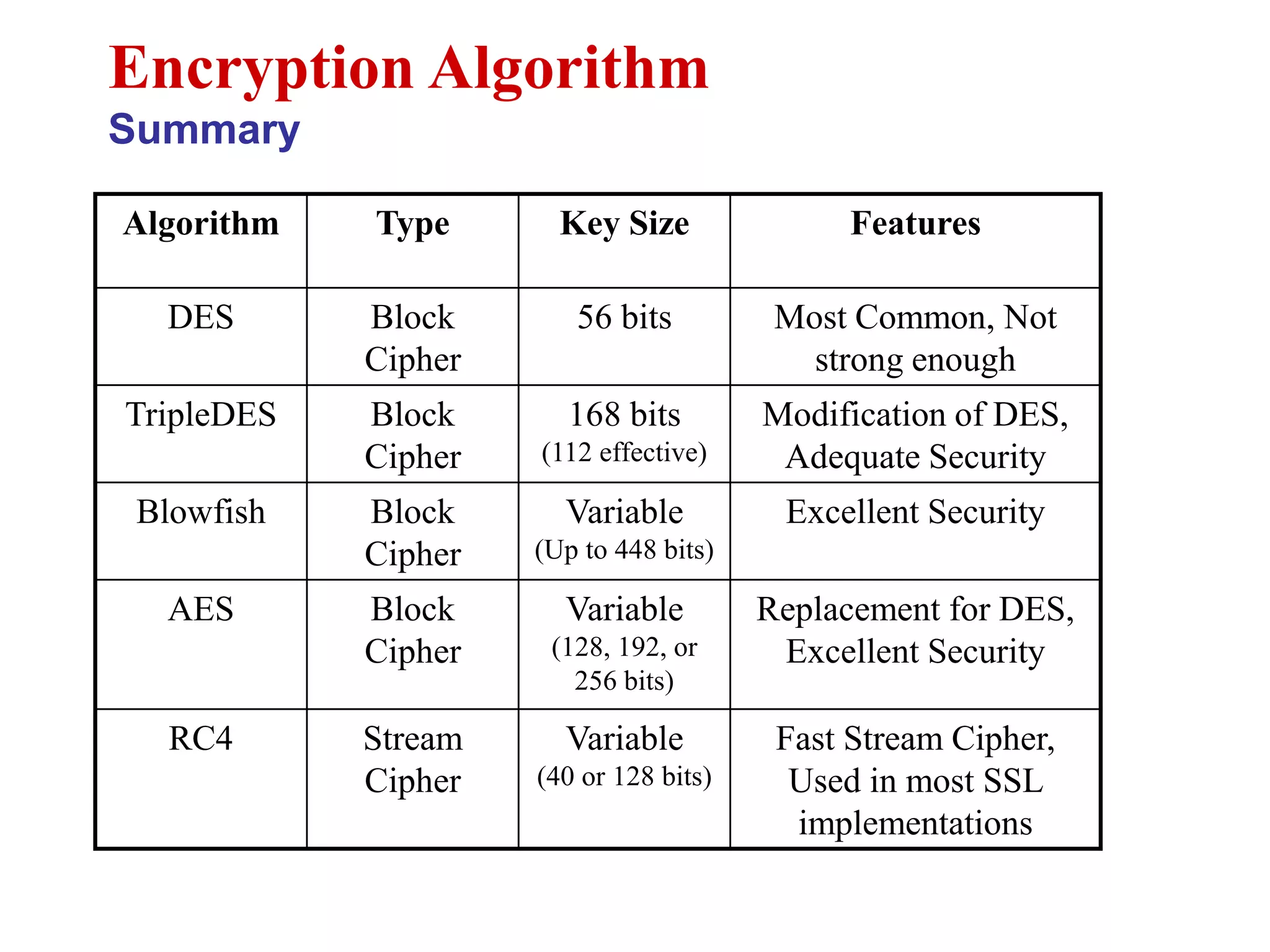
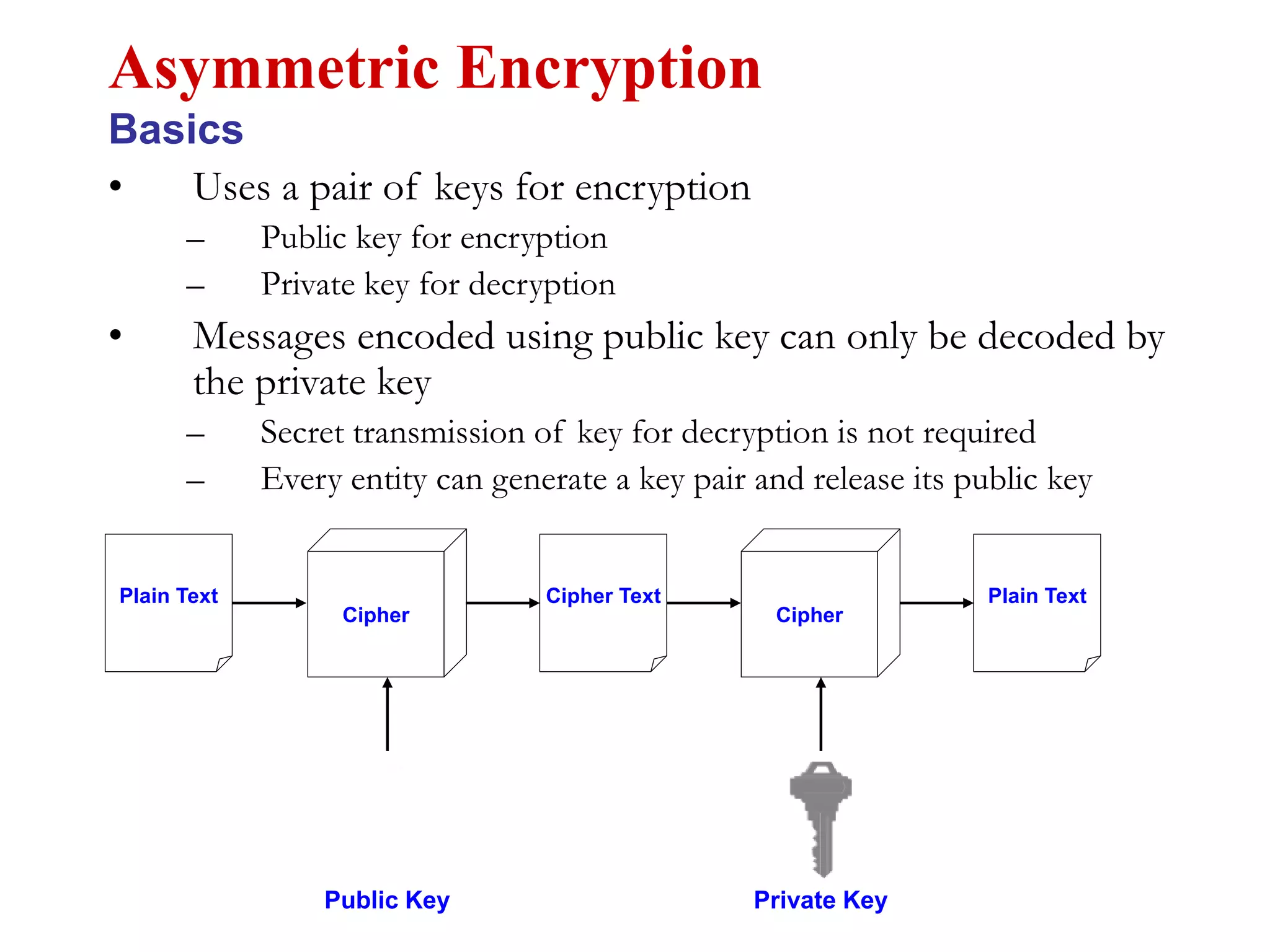
This document discusses computer security and cryptography. It covers the basic needs and requirements of secure communication such as secrecy, authentication, and message integrity. It then describes the basics of cryptography including encryption algorithms, keys, symmetric and asymmetric encryption. Specific encryption algorithms covered include DES, Triple DES, Blowfish and AES. Cryptanalysis techniques for breaking encryption codes are also summarized. The document provides an overview of computer security and cryptography concepts.