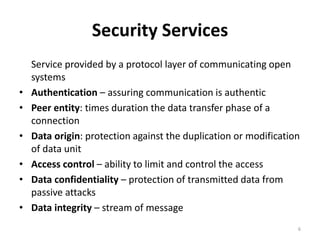
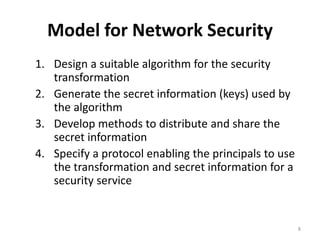
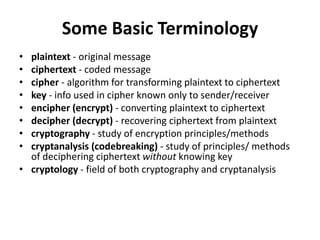
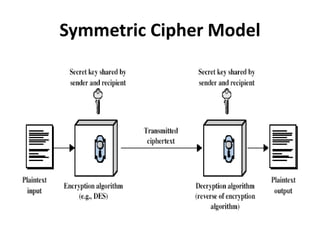
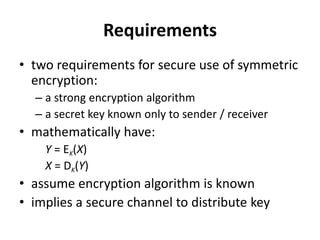
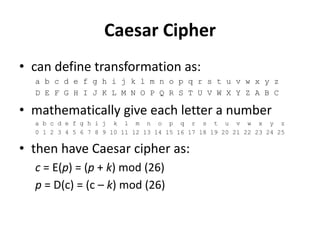
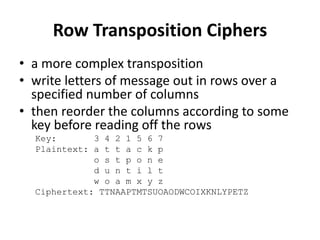
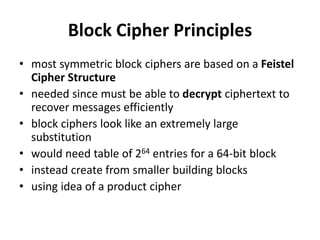
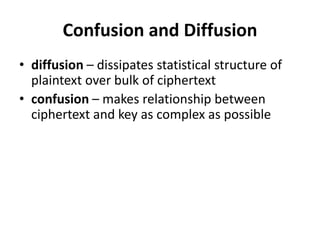
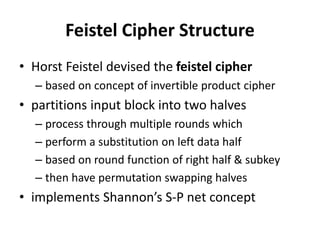
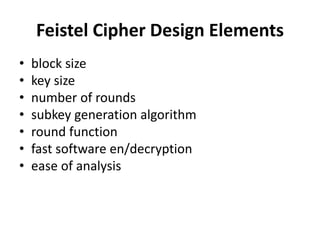
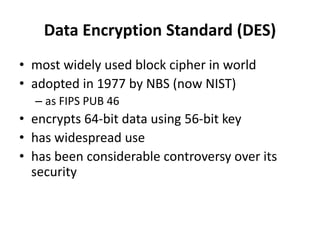
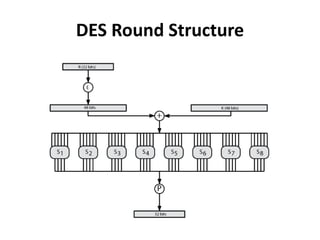
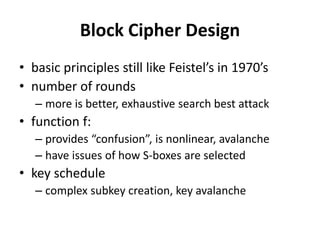
This document provides an overview of cryptography and network security concepts. It discusses computer security, network security, and internet security. It then covers security attacks like passive attacks which obtain transmitted information and active attacks which modify data. Security services like authentication, access control, and data confidentiality are explained. Security mechanisms like encipherment, digital signatures, and traffic padding are also introduced. Symmetric ciphers like the Caesar cipher, monoalphabetic cipher, Playfair cipher, polyalphabetic ciphers, and the one-time pad are described. Block ciphers principles involving confusion and diffusion are covered. The Data Encryption Standard (DES) cipher is explained in detail regarding its history, structure using Feistel networks, key size,