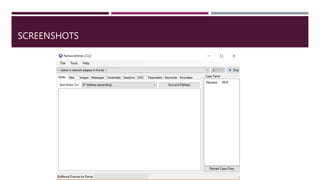
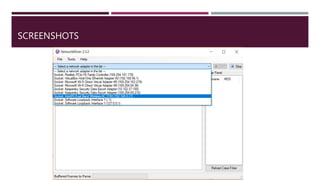
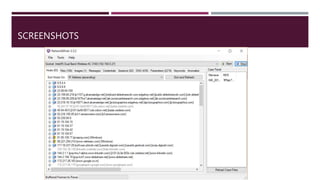
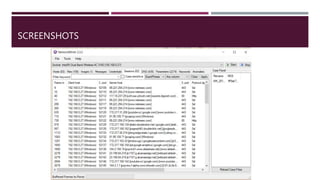
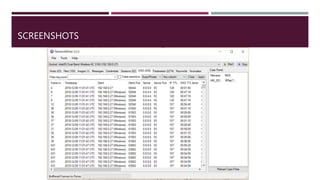
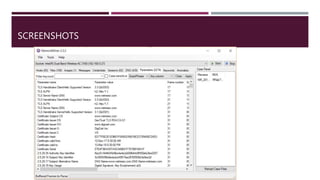
The document discusses network forensics, including the collection and analysis of network data to identify security incidents. It introduces Network Miner, an open-source tool for capturing and analyzing network traffic, highlighting its features like file extraction and keyword searches. The document also provides a case scenario to illustrate its application in troubleshooting network issues.