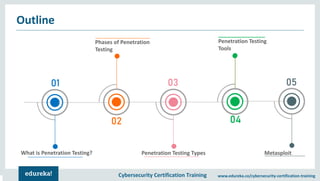
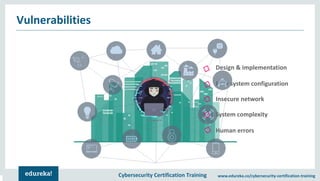
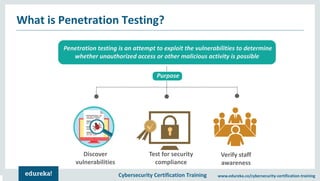
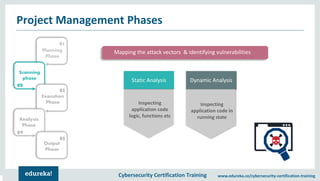
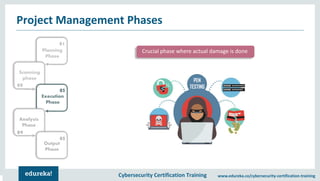
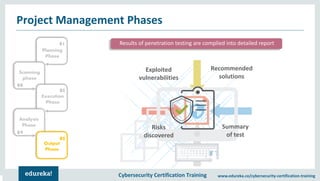
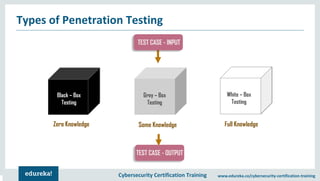
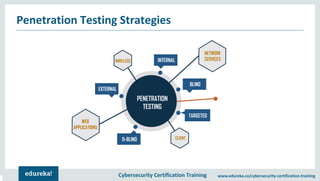
The document outlines cybersecurity certification training focused on penetration testing, which aims to exploit vulnerabilities to assess security. It details the phases of penetration testing, including planning, scanning, exploitation, and reporting, as well as various types and strategies of testing. Additionally, it emphasizes the importance of penetration testing tools for efficient and accurate results.