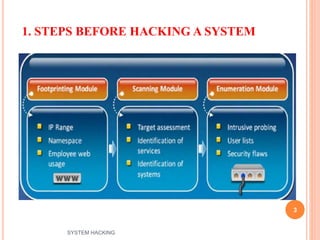
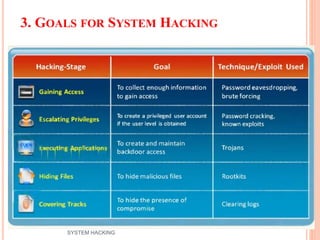
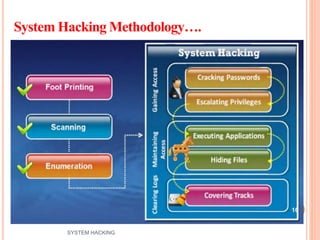
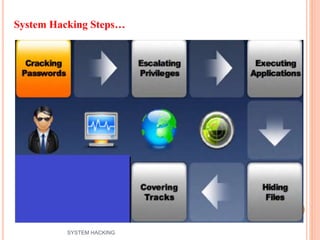
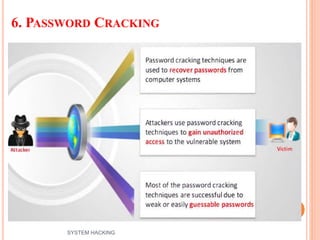
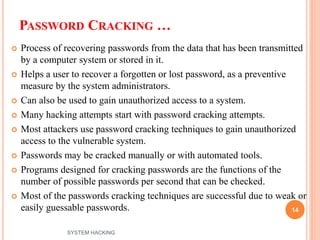
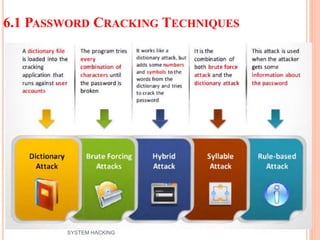
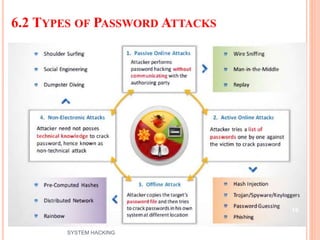
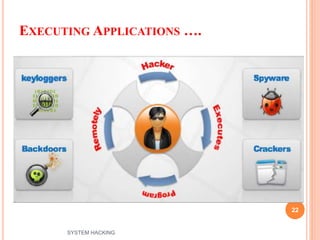
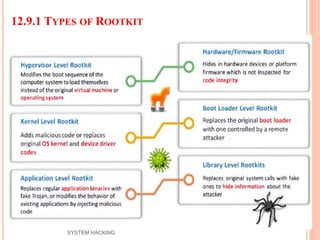
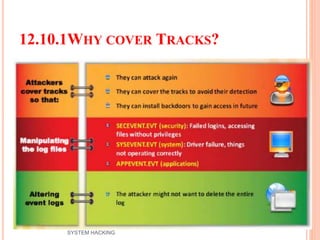
The document outlines the systematic approach to system hacking, detailing stages such as footprinting, scanning, and enumeration to gather information about a target network. It elaborates on various hacking techniques including password cracking, privilege escalation, and hiding files, emphasizing the importance of methodology and the goals behind attacks. Additionally, the document describes the tools and tactics used by attackers to execute malicious actions and cover their tracks.