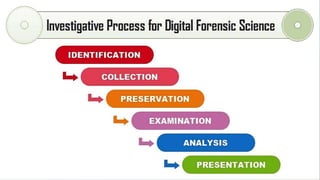
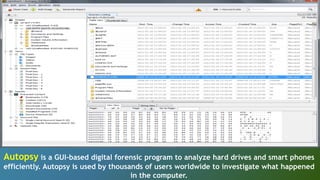
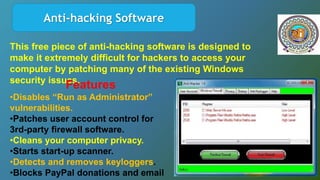
The document discusses various forensic investigation tools used to combat cybersecurity threats, highlighting tools like Network Miner, Wireshark, and Autopsy for digital forensic analysis. It explains the features and functionalities of these tools, such as network traffic analysis, data reconstruction, and hard drive examination. Additionally, it covers various types of cyber threats like ransomware and phishing, emphasizing the need for effective cybersecurity measures and awareness.