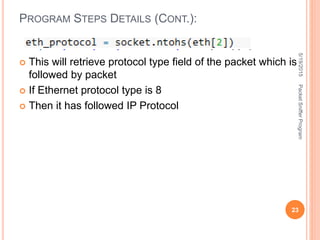
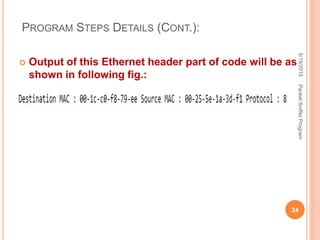
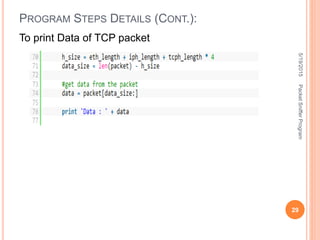
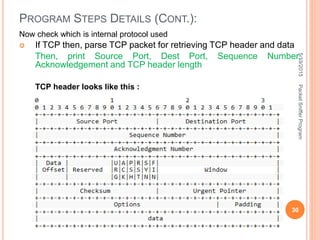
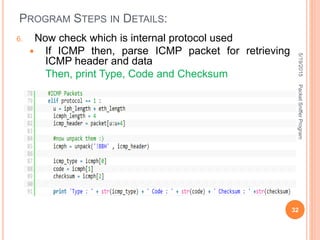
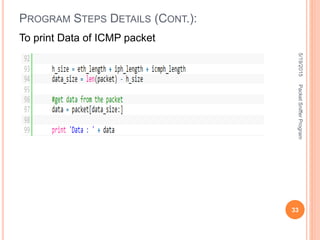
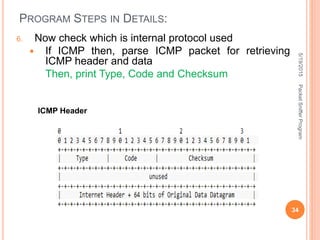
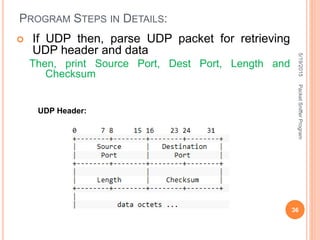
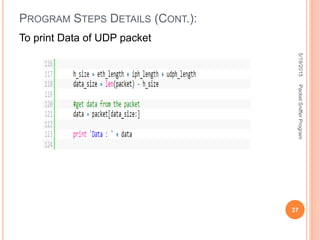
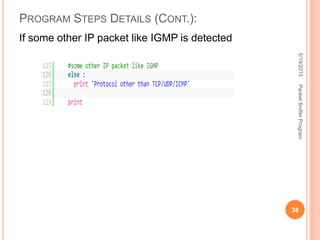
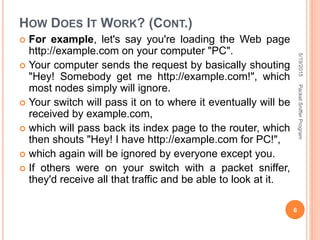
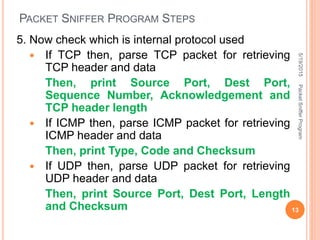
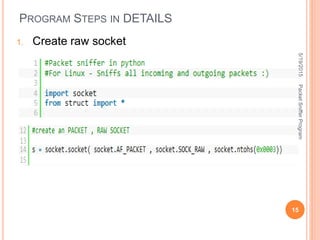
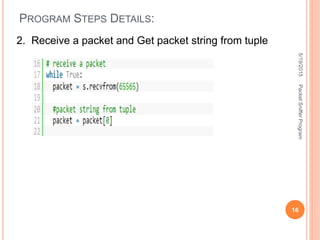
The document describes a packet sniffer program and how it works. It explains that packet sniffing involves capturing network traffic and analyzing it to gather useful information. It then discusses how packet sniffers work by listening to broadcast data on a local network. Finally, it provides details on the types of information that can be gathered from sniffed packets, such as usernames, passwords, emails, and websites visited.











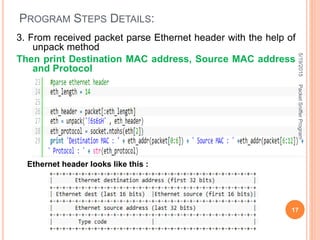
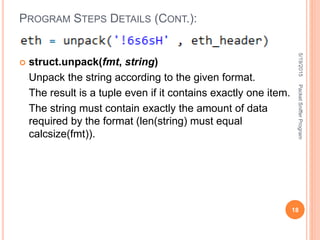
![ Here is the meaning of, ‘6s6sH’
s is char[] of size 6
And H is unsigned short, integer of size 2
Hence total is,
6 char + 6 char + 2 integer = total 8
This format string will take out required fields of header
packet
PROGRAM STEPS DETAILS (CONT.):
5/19/2015
22
PacketSnifferProgram](https://image.slidesharecdn.com/sniffpresentation-150519050440-lva1-app6892/85/Packet-Sniffer-22-320.jpg)