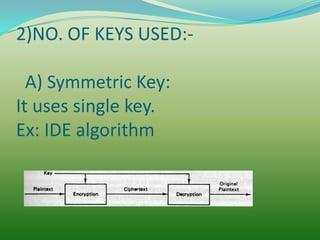
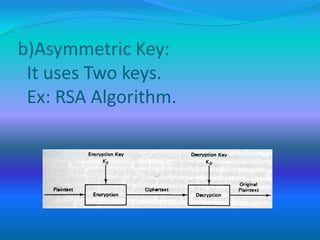
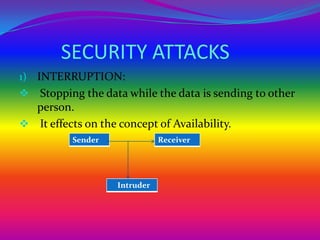
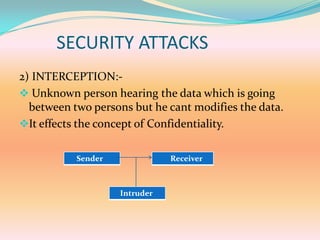
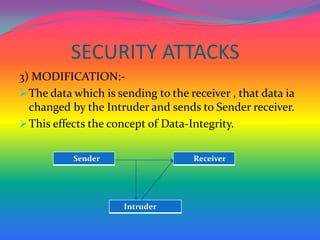
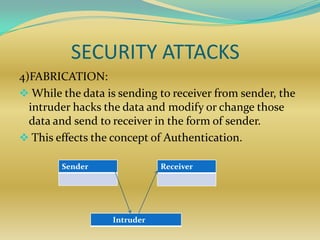
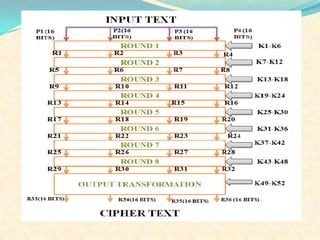
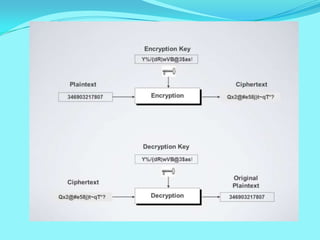
The document discusses network security concepts and algorithms. It introduces network security and defines it as protection of networks from unauthorized access, modification, or disclosure. It then describes common network security concepts like authentication, confidentiality, and data integrity. It also discusses common security attacks like interception, modification, and fabrication. The document also summarizes the RSA and IDEA encryption algorithms, including how keys are generated and how encryption and decryption work.