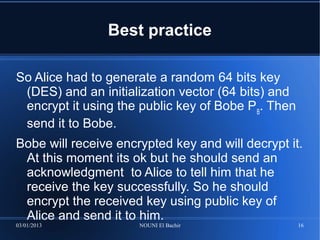
This document provides an overview of the DES and RSA encryption algorithms. DES is a symmetric algorithm that is fast for large data sizes but requires securely exchanging keys, while RSA is an asymmetric algorithm that is slower for large data sizes but uses public/private key pairs to encrypt and decrypt. The document then demonstrates implementing DES and RSA encryption using the OpenSSL tool, including generating keys, encrypting and decrypting files, and best practices for key exchange between two parties.



![TP : Test Each Algorithm (DES)
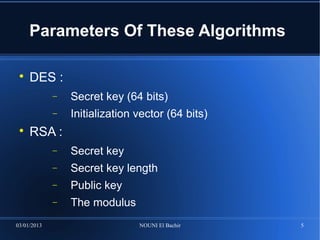
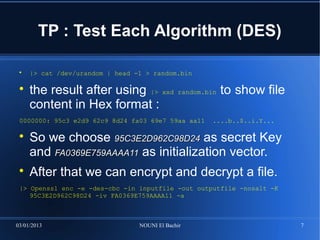
-des-cbc : DES algorithm using CBC mode
-e : for encryption
-in [inputfile] : to specify input file
-out [outputfile] : to specify output file
-K XX..XX : to specify secret key 64 bits
-iv XX..XX : to specify initialization vector 64 bits
-a : encoding output file in base64 format
-nosalt : no salt will be used
03/01/2013 NOUNI El Bachir 8](https://image.slidesharecdn.com/desandrsaoverview-130104052301-phpapp01/85/Crypto-DES-And-RSA-Algorithms-Overview-8-320.jpg)

![TP : Test Each Algorithm (RSA)
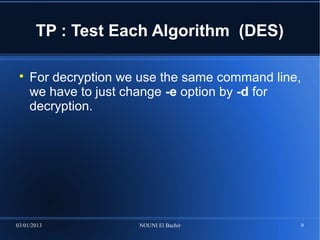
openssl genrsa [-out filename] [-passout arg] [-des] [-des3] [-idea]
[-f4] [-3] [-rand file(s)] [-engine id] [numbits]
openssl rsa [-inform PEM|NET|DER] [-outform PEM|NET|DER] [-in
filename] [-passin arg] [-out filename] [-passout arg] [-sgckey] [-
des] [-des3] [-idea] [-text] [-noout] [-modulus] [-check] [-pubin]
[-pubout] [-engine id]
For encryption we will use rsautl command of
following synopsis :
openssl rsautl [-in file] [-out file] [-inkey file] [-pubin] [-
certin] [-sign] [-verify] [-encrypt] [-decrypt] [-pkcs] [d-ssl] [-
raw] [-hexdump] [-asn1parse]
Lets now try this algorithm :
03/01/2013 NOUNI El Bachir 11](https://image.slidesharecdn.com/desandrsaoverview-130104052301-phpapp01/85/Crypto-DES-And-RSA-Algorithms-Overview-11-320.jpg)