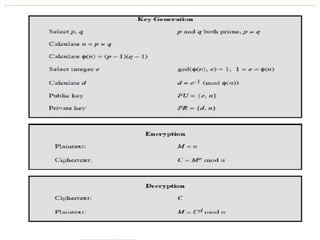
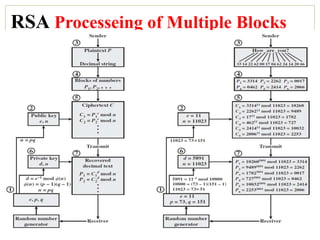
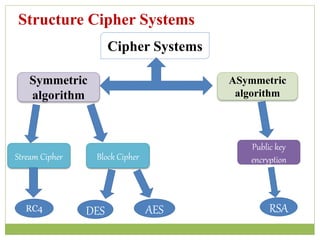
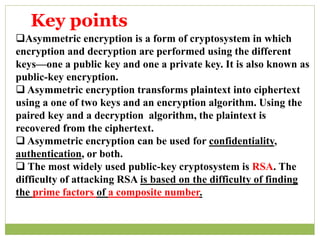
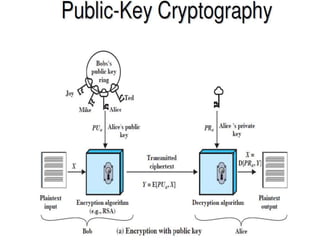
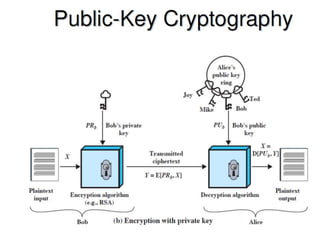
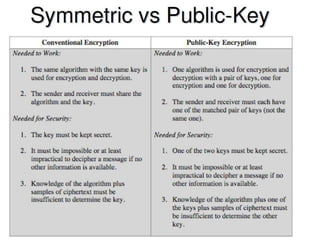
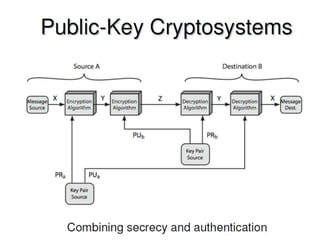
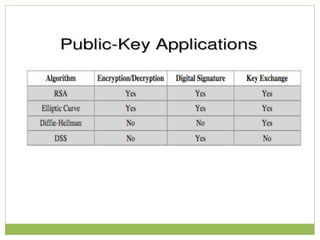
The document outlines the principles of public-key cryptography, focusing on the RSA algorithm as the most widely used public-key cryptosystem. It explains how asymmetric encryption uses a pair of keys, a public key for encryption and a private key for decryption, and describes key generation, digital signatures, and key exchange processes. The RSA algorithm's security relies on the difficulty of factoring large composite numbers, and it includes multiple approaches for potential attacks.







![1. It is computationally easy for a party B to generate a pair
(public key PUb, private key PRb).
2. It is computationally easy for a sender A, knowing the public
key and the message to be encrypted,M, to generate the
corresponding ciphertext:
C = E(PUb,M)
3. It is computationally easy for the receiver B to decrypt the
resulting ciphertext using the private key to recover the
original message:
M = D(PRb, C) = D[PRb, E(PUb,M)]
Requirements for Public-Key
Cryptography](https://image.slidesharecdn.com/informationanddatasecuritypublic-keycryptographyandrsa-170928113313/85/Information-and-data-security-public-key-cryptography-and-rsa-16-320.jpg)
![4. It is computationally infeasible for an adversary, knowing the
public key, PUb, to determine the private key,PRb.
5. It is computationally infeasible for an adversary, knowing the
public key, PUb, and a ciphertext, C, to recover the original
message,M. We can add a sixth requirement that, although useful,
is not necessary for all public-key applications:
6. The two keys can be applied in either order:
M = D[PUb, E(PRb,M)] = D[PRb, E(PUb,M)]
Requirements for Public-Key
Cryptography](https://image.slidesharecdn.com/informationanddatasecuritypublic-keycryptographyandrsa-170928113313/85/Information-and-data-security-public-key-cryptography-and-rsa-17-320.jpg)
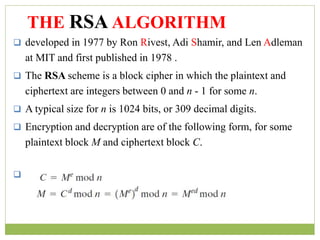
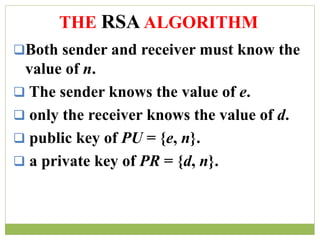
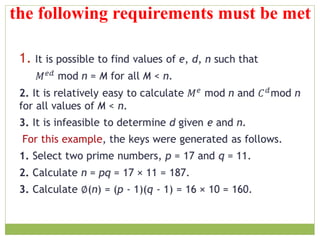
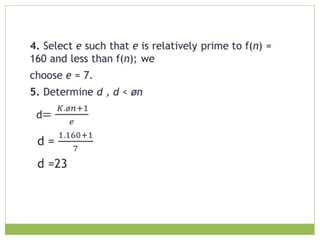
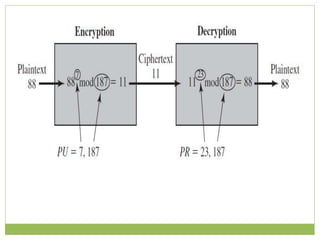
![ The resulting keys are public key PU = {7, 187} and private
key PR = {23, 187}, the example shows the use of these keys
for plaintext M = 88 .
For encryption
88^7 mod 187 = [(88^4 mod 187) × (88^2 mod 187)
× (88^1 mod 187)] mod 187
88^1 mod 187 = 88
88^2 mod 187 = 7744 mod 187 = 77
88^4 mod 187 = 59,969,536 mod 187 = 132
88^7 mod 187 = (88 × 77 × 132) mod 187 = 894,432 mod 187
= 11](https://image.slidesharecdn.com/informationanddatasecuritypublic-keycryptographyandrsa-170928113313/85/Information-and-data-security-public-key-cryptography-and-rsa-22-320.jpg)