This document discusses computer security basics and malicious software. It covers the following key points:
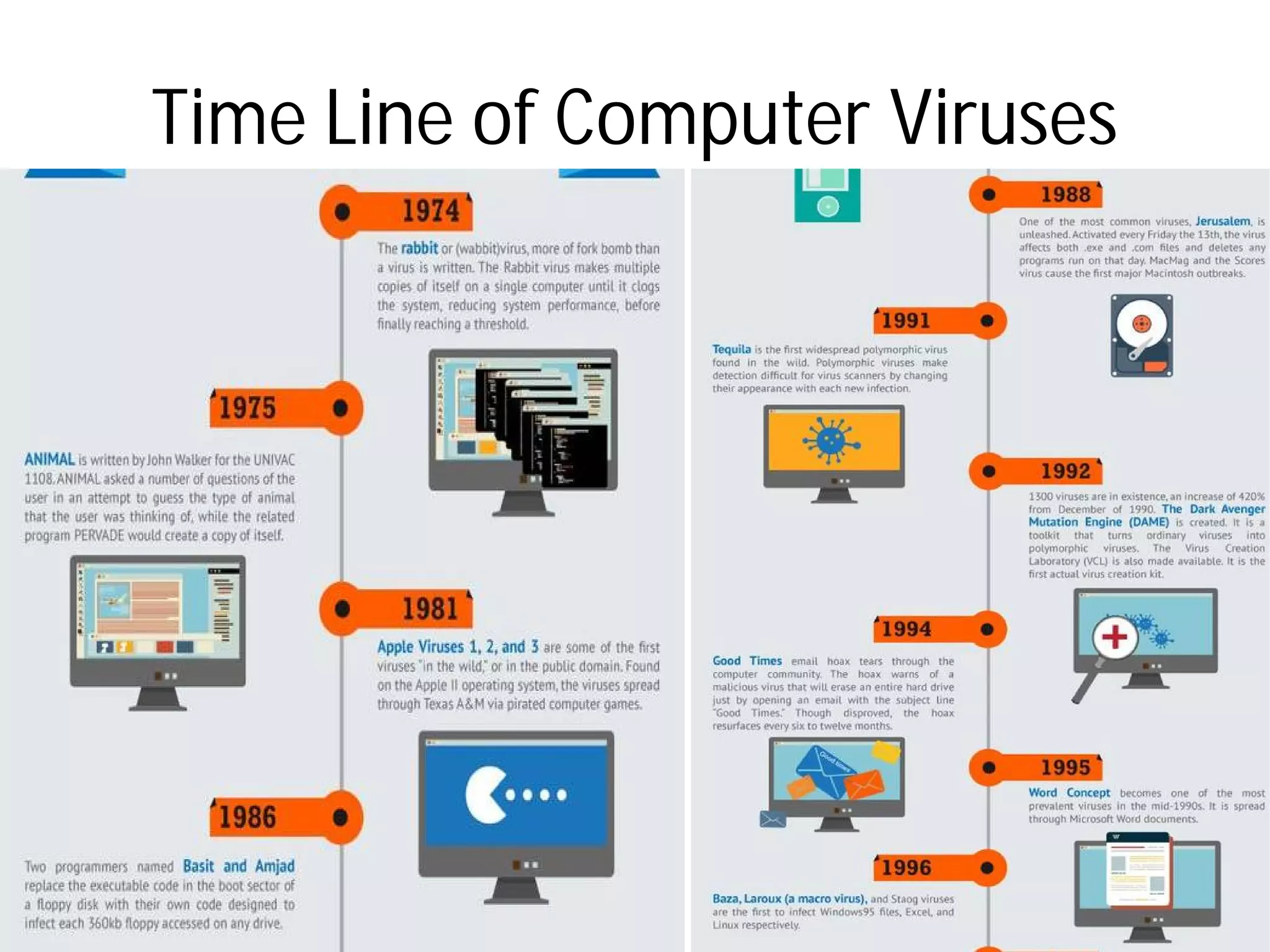
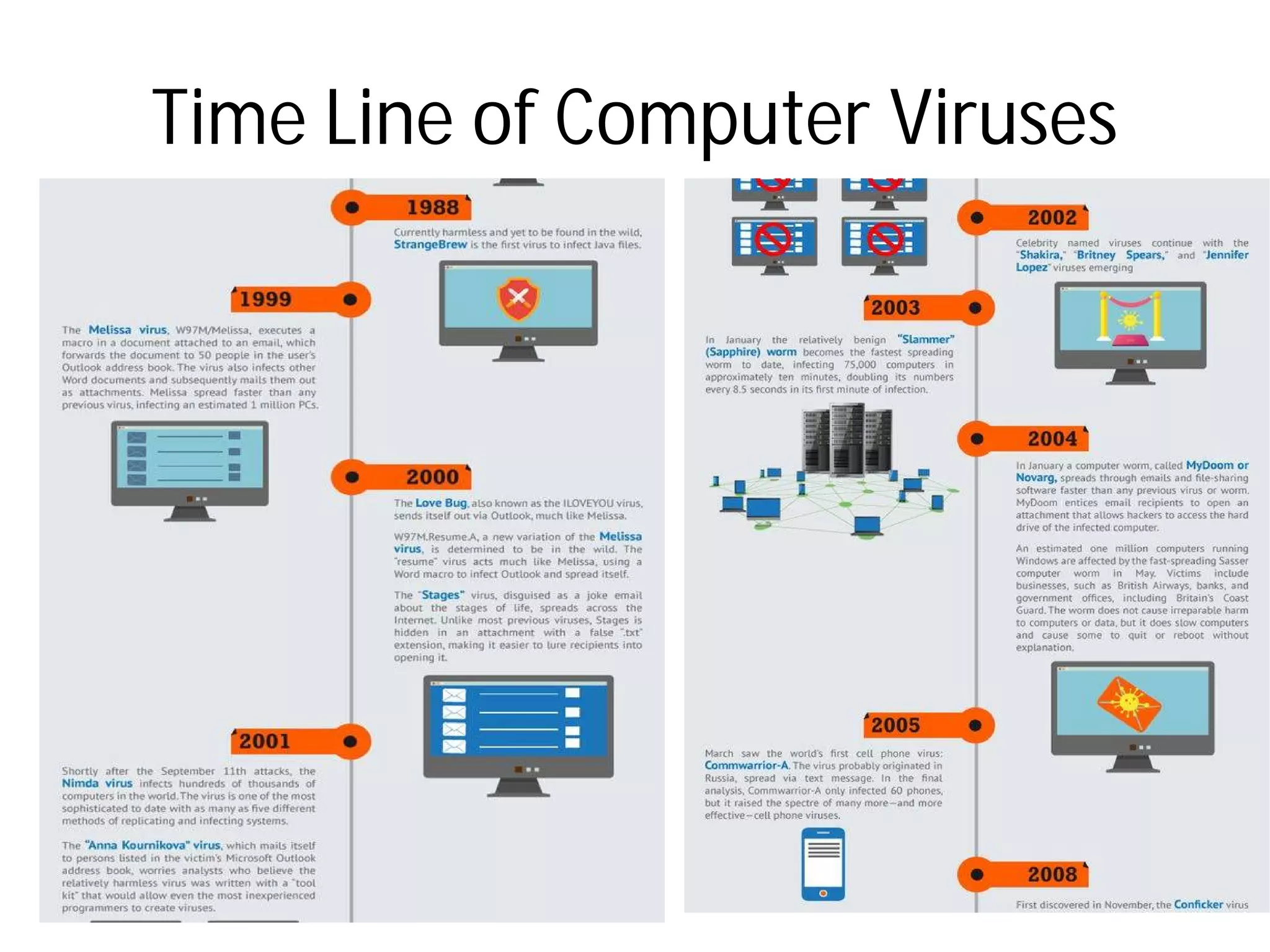
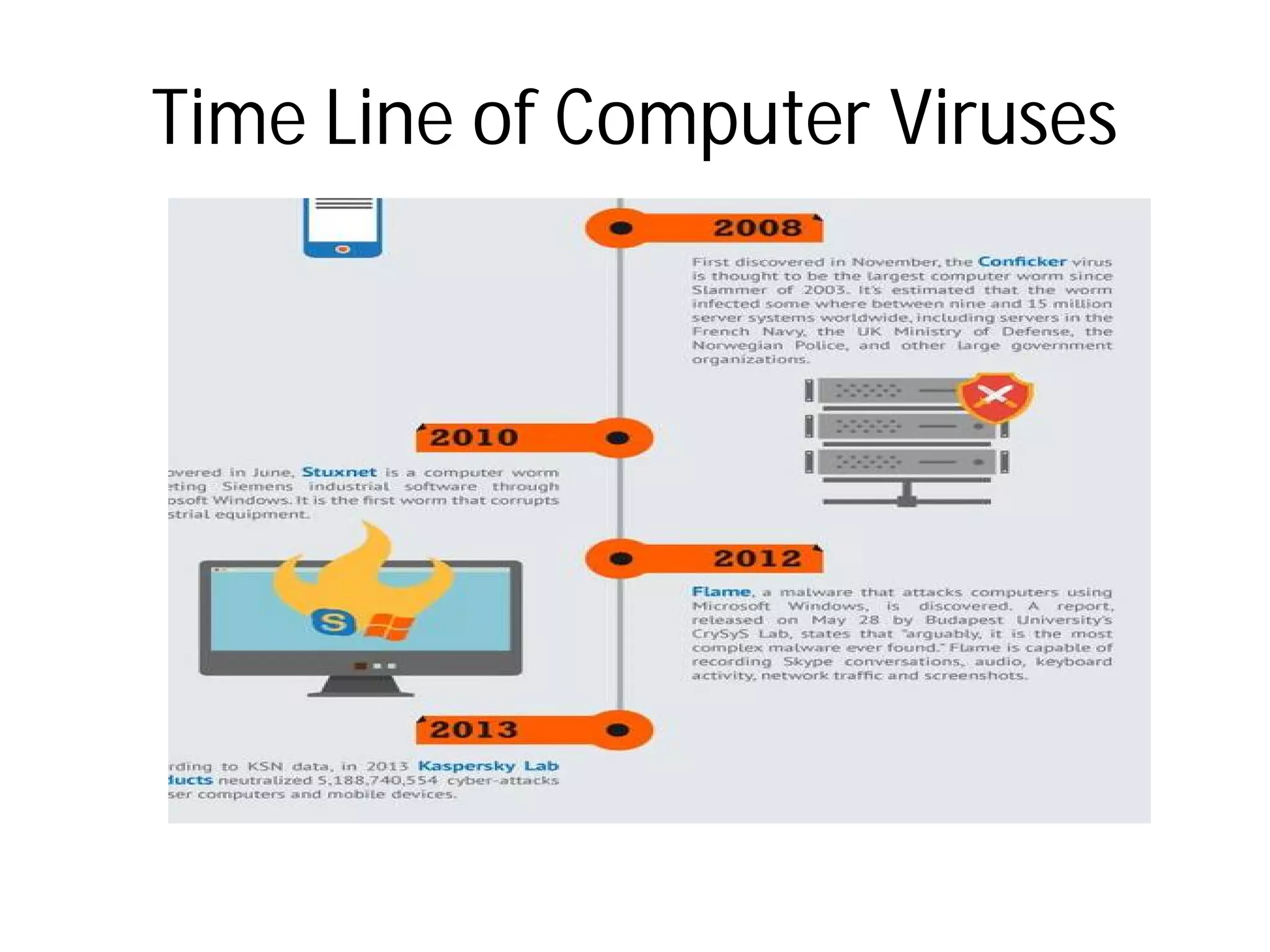
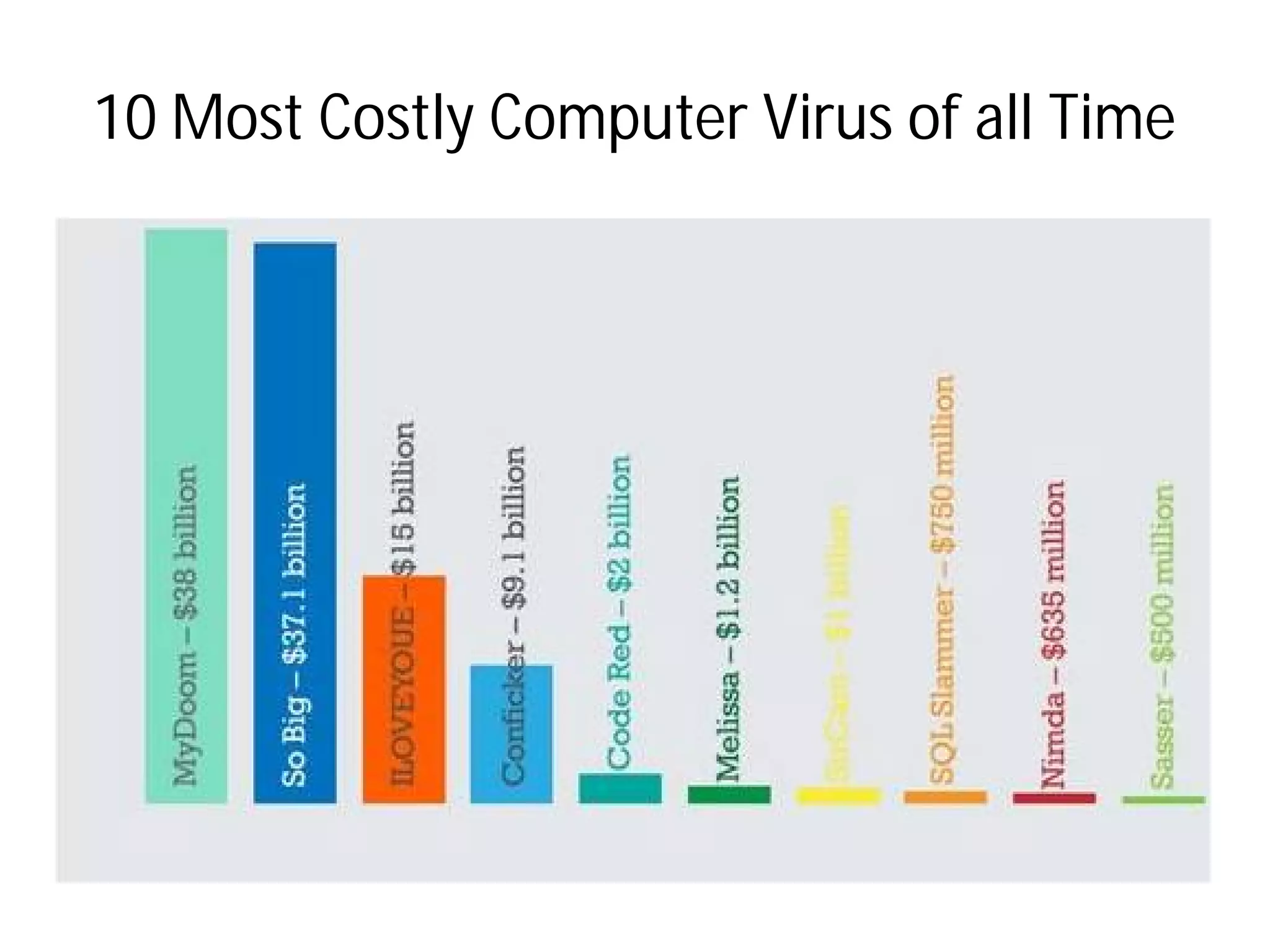
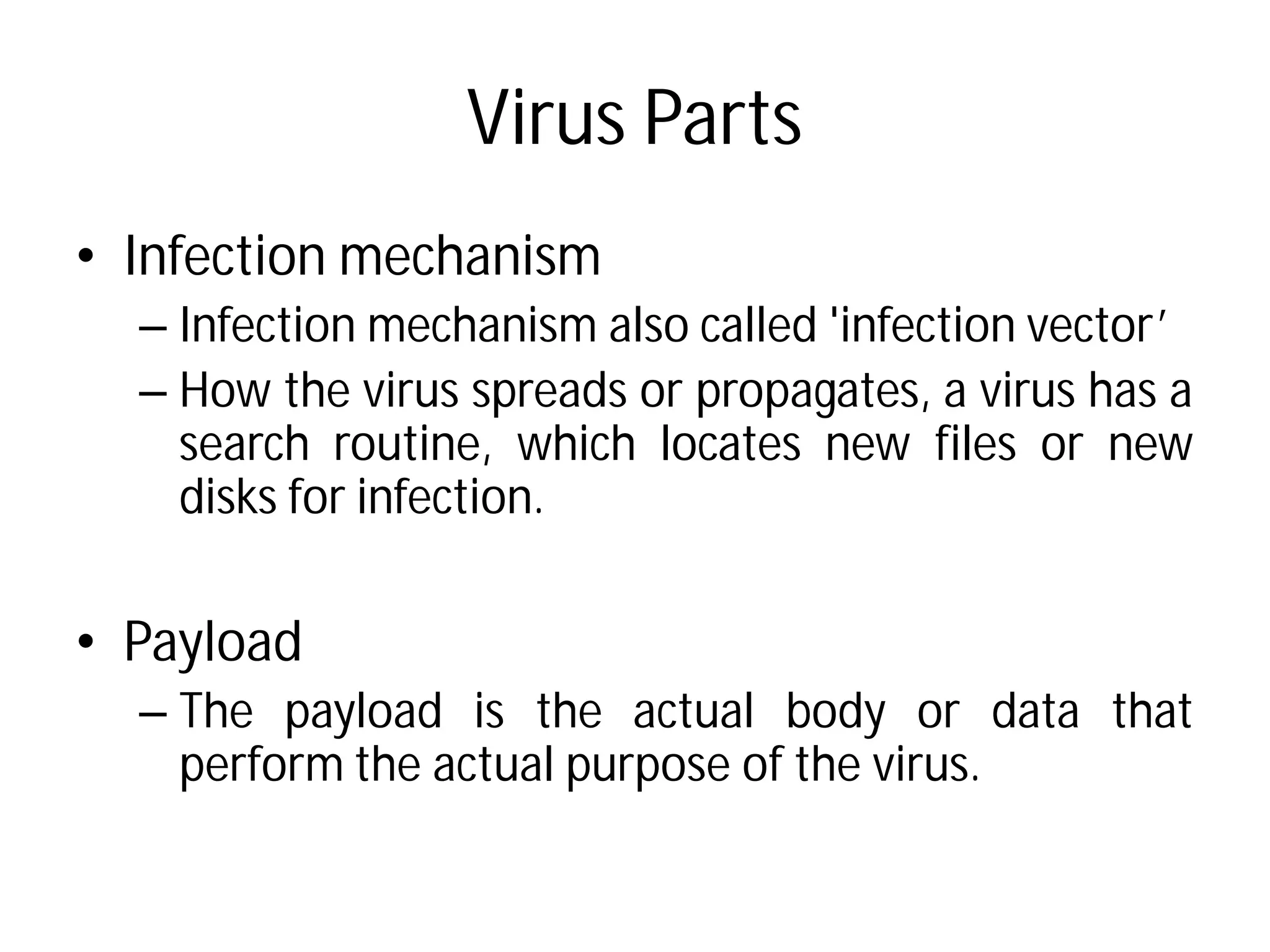
- Types of malware include viruses, adware, spyware, and browser hijacking software. Viruses can self-replicate and spread to other programs/disks.
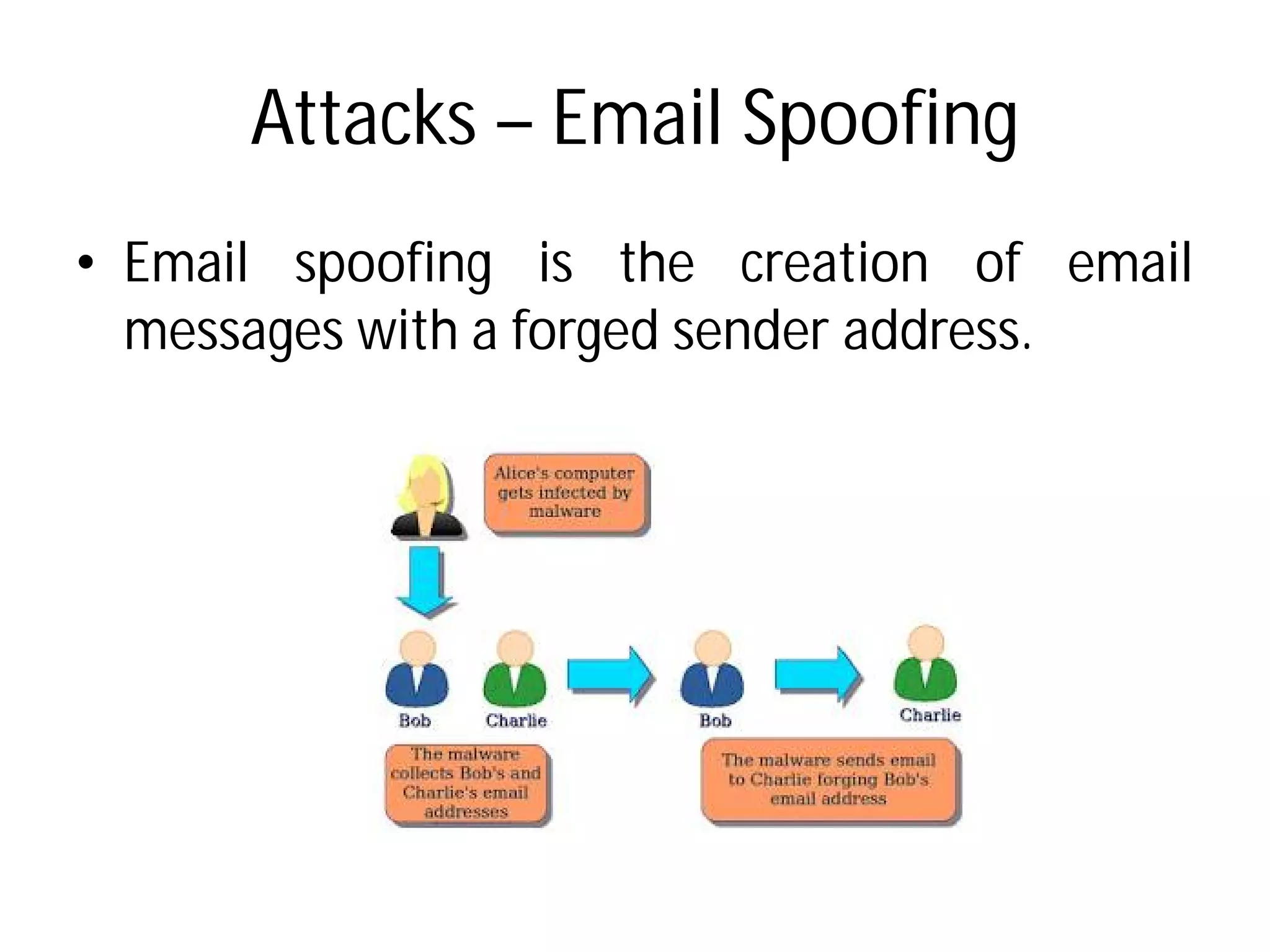
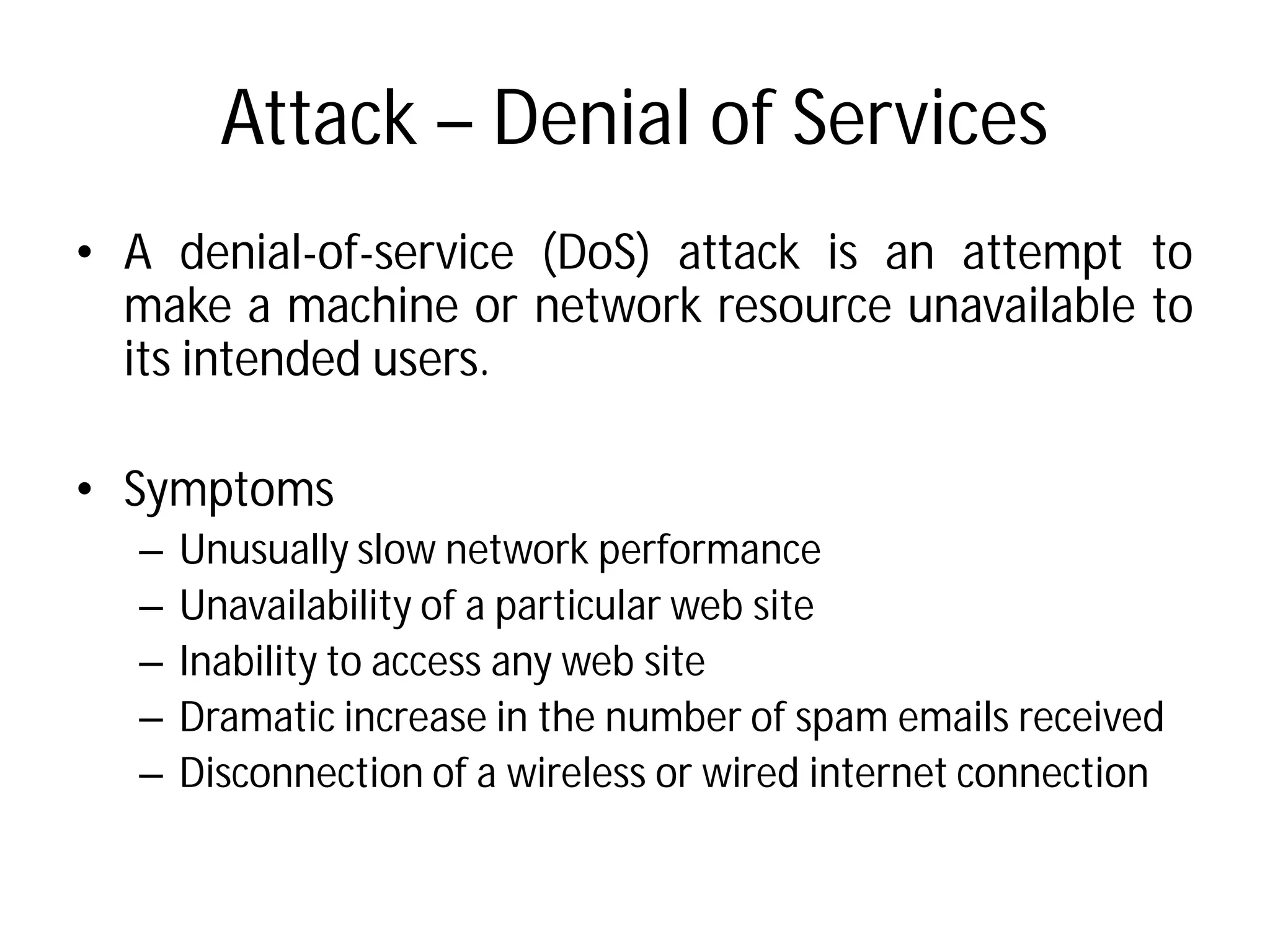
- Common security threats are malicious software, denial of service attacks, email spoofing, cyber stalking, spamming, and money laundering. Firewalls and passwords are important security measures.
- Good security practices involve locking computers when away, using boot passwords, and being cautious of unauthorized access to prevent data compromise. Understanding the risks of malware and different attack types is essential for computer security.