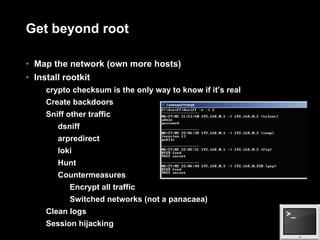
The document provides an outline for hacking different systems including performing internet footprinting, hacking Windows systems, hacking Unix/Linux systems, and hacking networks. It discusses techniques for scanning systems, enumerating services and users, penetrating targets by exploiting services or escalating privileges, gaining interactive access, and maintaining influence. It provides examples of tools that can be used for reconnaissance, attacks, and privilege escalation on the different system types. The document also covers vulnerabilities in systems like SNMP, HTTP, TFTP, and routing protocols that can be exploited, and techniques for dealing with firewalls like port scanning and redirection.








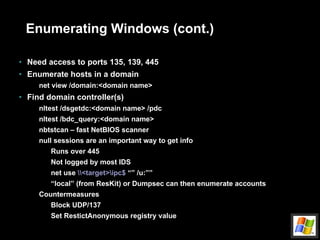
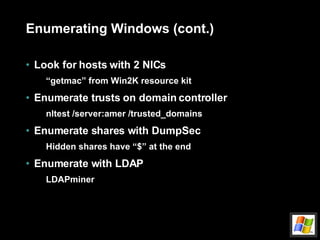
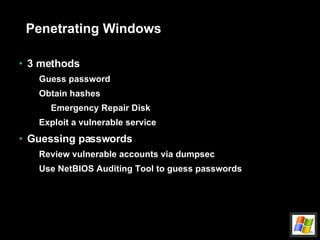

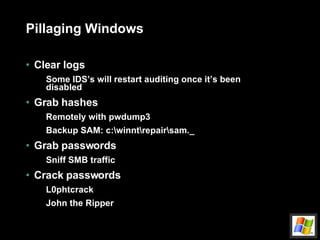







![Attack remotely (cont.) Buffer overflow example echo “vrfy `perl –e ‘print “a” x 1000’`” |nc www.targetsystem.com 25 Replace this with something like this… char shellcode[] = “\xeb\xlf\x5e\x89\x76\x08…” Input validation attacks PHF CGI – newline character SSI passes user input to O/S Back channels X-Windows Send display back to attacker’s IP Reverse telnet](https://image.slidesharecdn.com/intro-to-hacking-1216903710371131-8/85/Intro-To-Hacking-25-320.jpg)