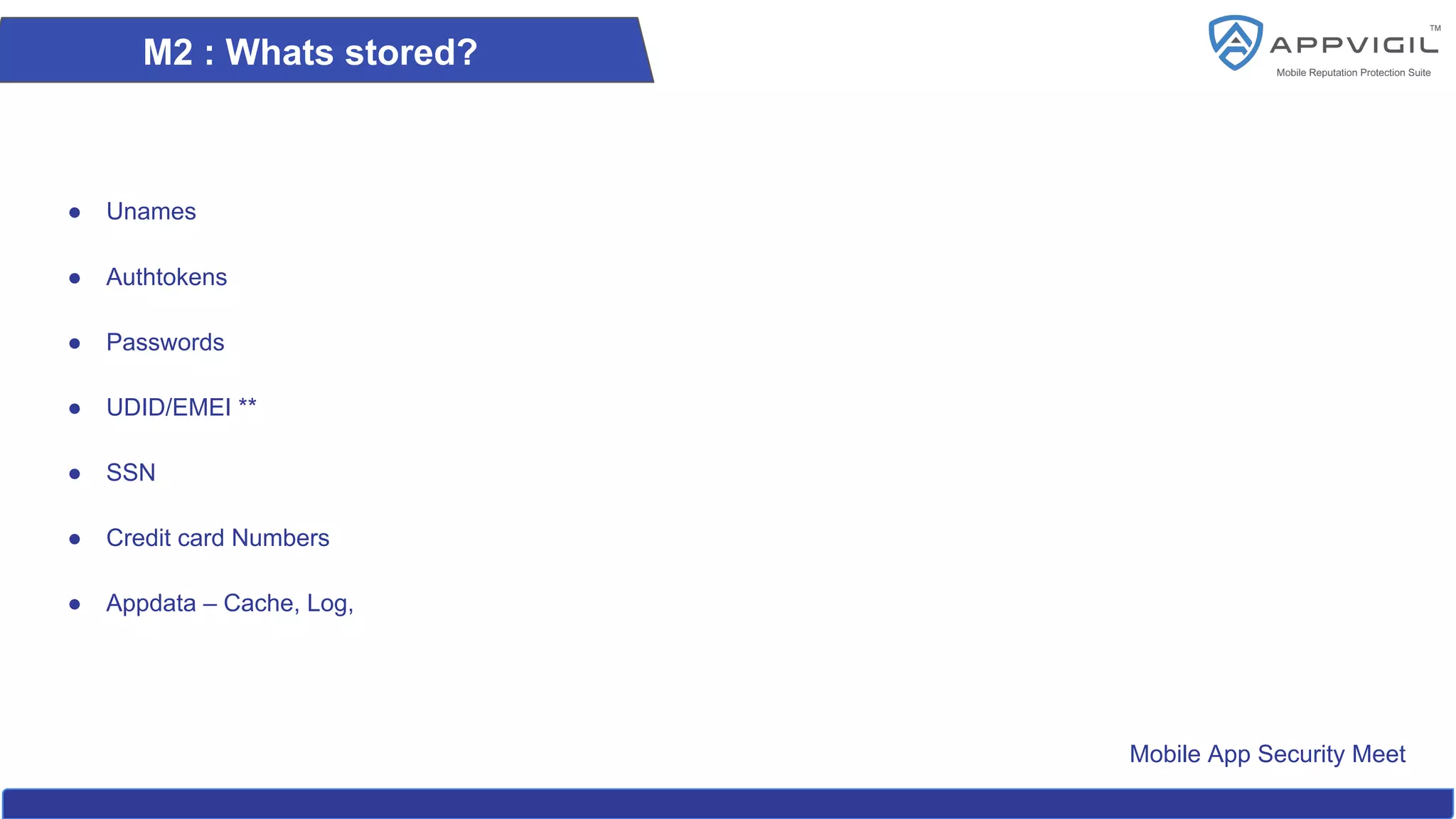
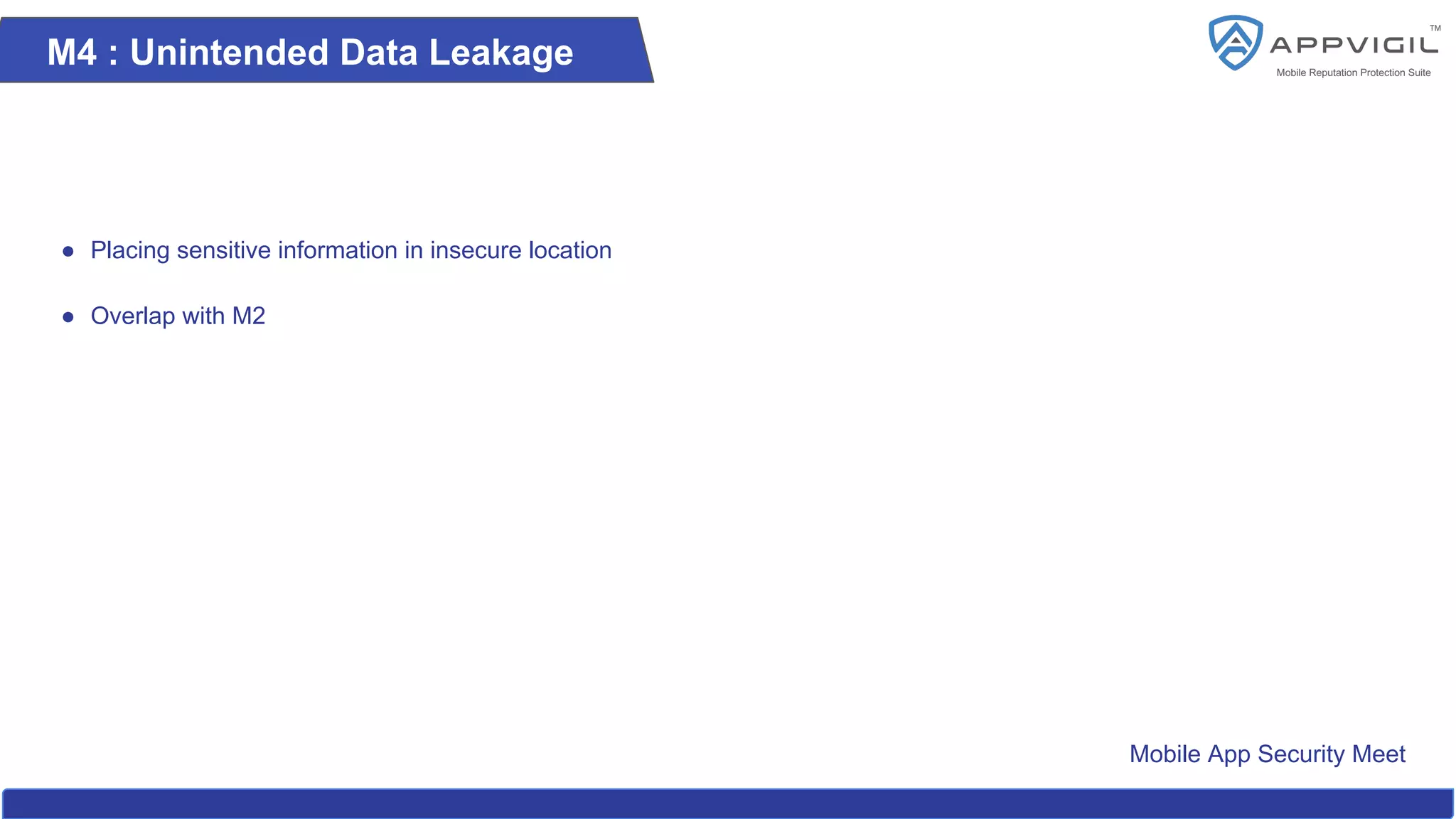
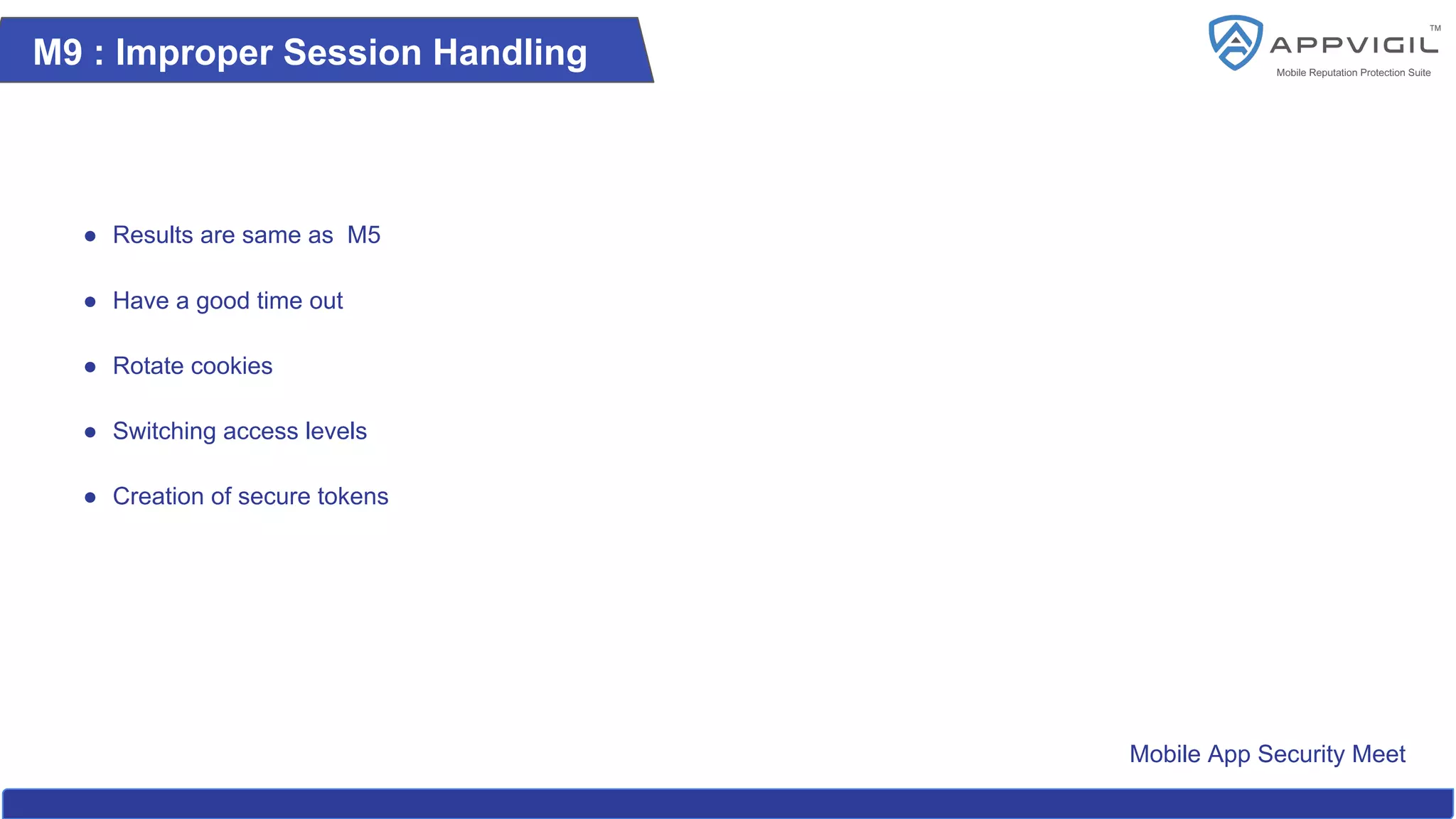
The document summarizes a recap of the OWASP Mobile App Security Meet, outlining key aspects of mobile app security, including its history, the essential top 10 security issues, and best practices. It emphasizes the importance of securing sensitive data, preventing data leakage, addressing client-side vulnerabilities, and enforcing robust server-side controls. Additionally, it highlights the need for developers to adhere to OWASP guidelines for ensuring mobile application security.