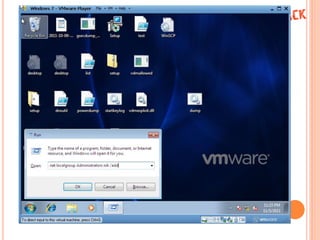
The document discusses using a Teensy microcontroller device to compromise secure environments. It begins by providing background on the presenter and an overview of topics to be covered. It then discusses limitations in typical pentests and how exploiting vulnerabilities is important. The document proposes using a Teensy device to bypass security controls and perform tasks like enabling RDP, downloading files, and keylogging. It demonstrates some payloads, notes current limitations, and ideas for future improvements like using additional storage. The conclusion is that Teensy can be used as a complete pentesting device if leveraged properly.