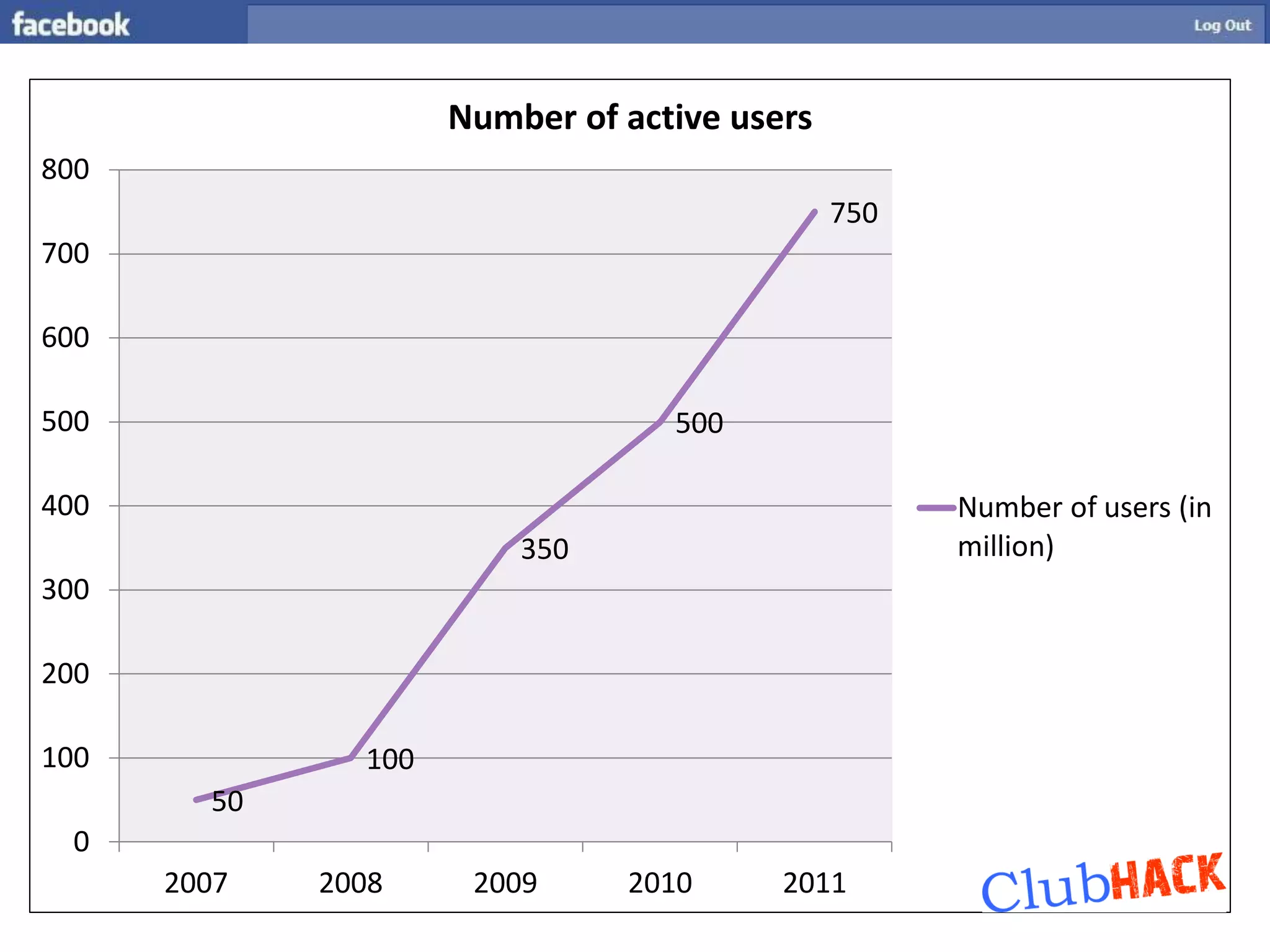
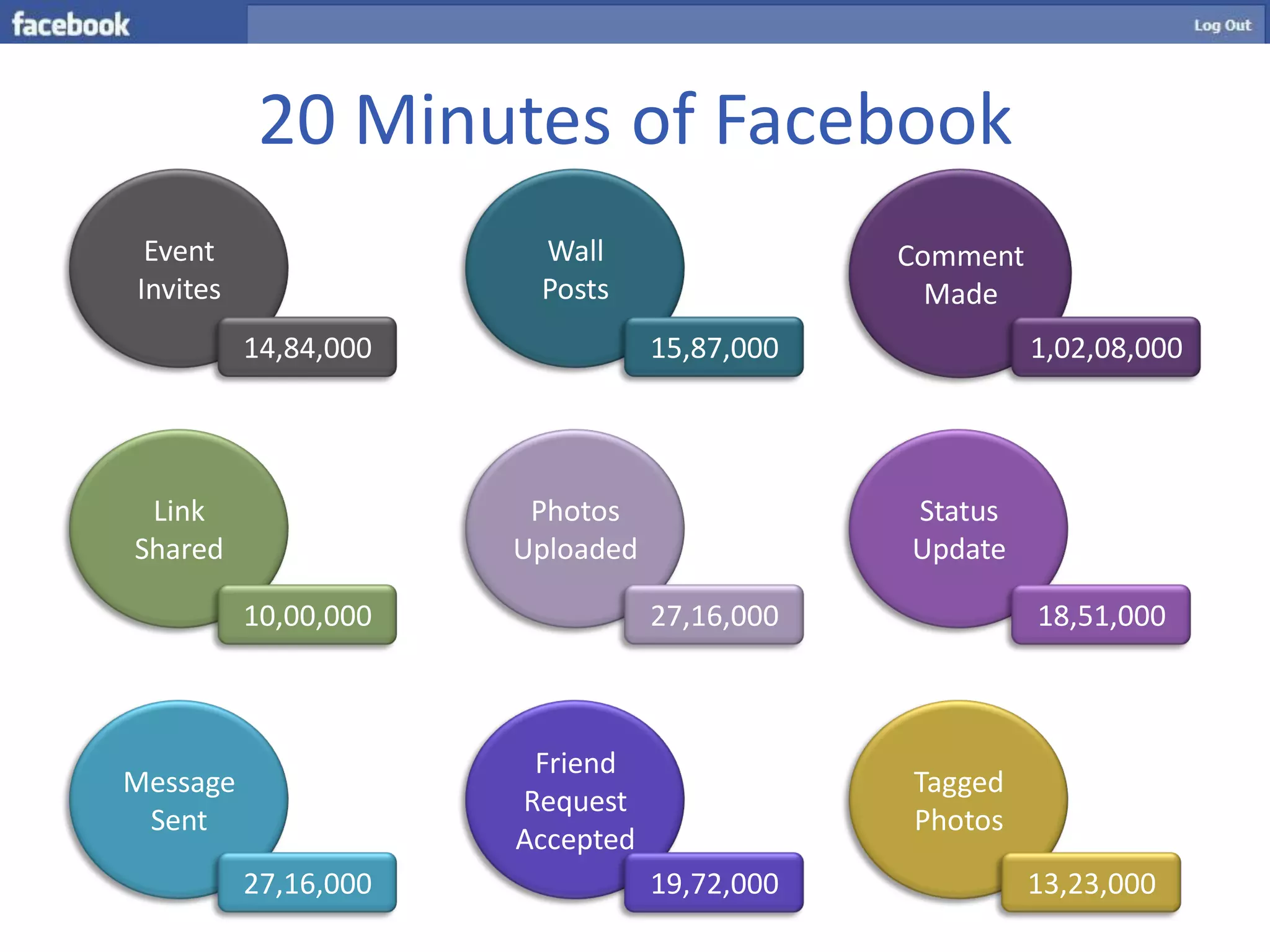
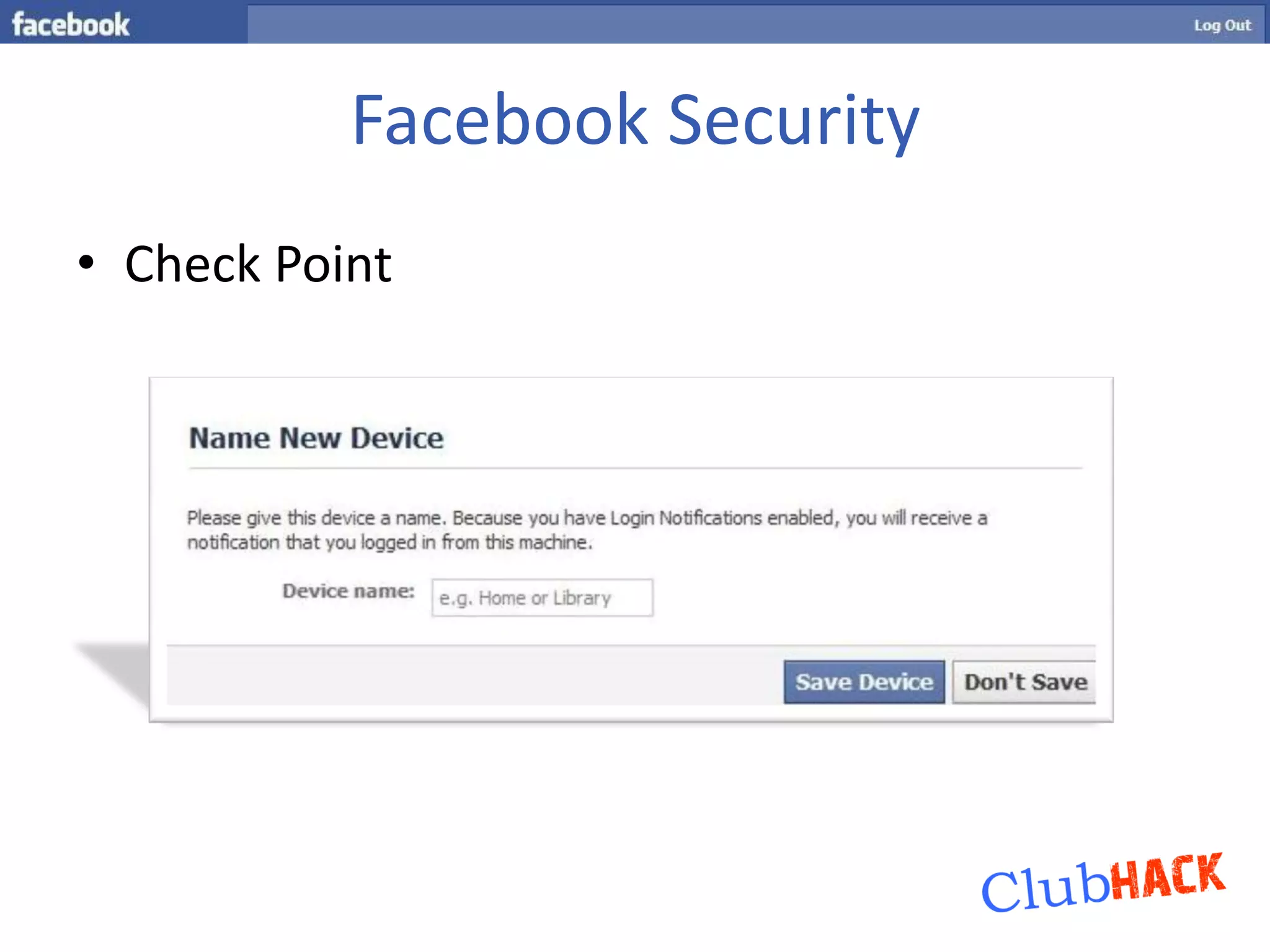
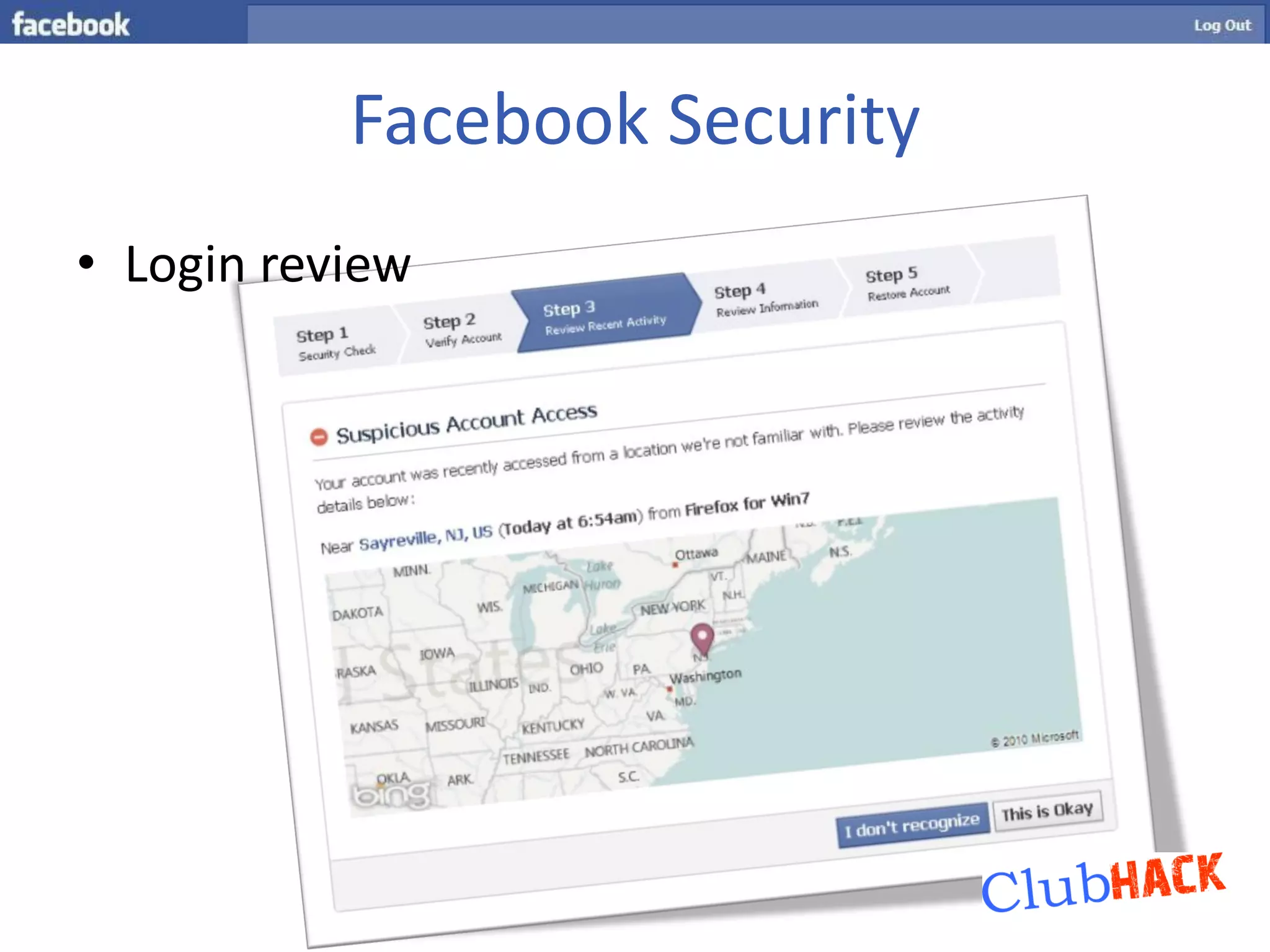
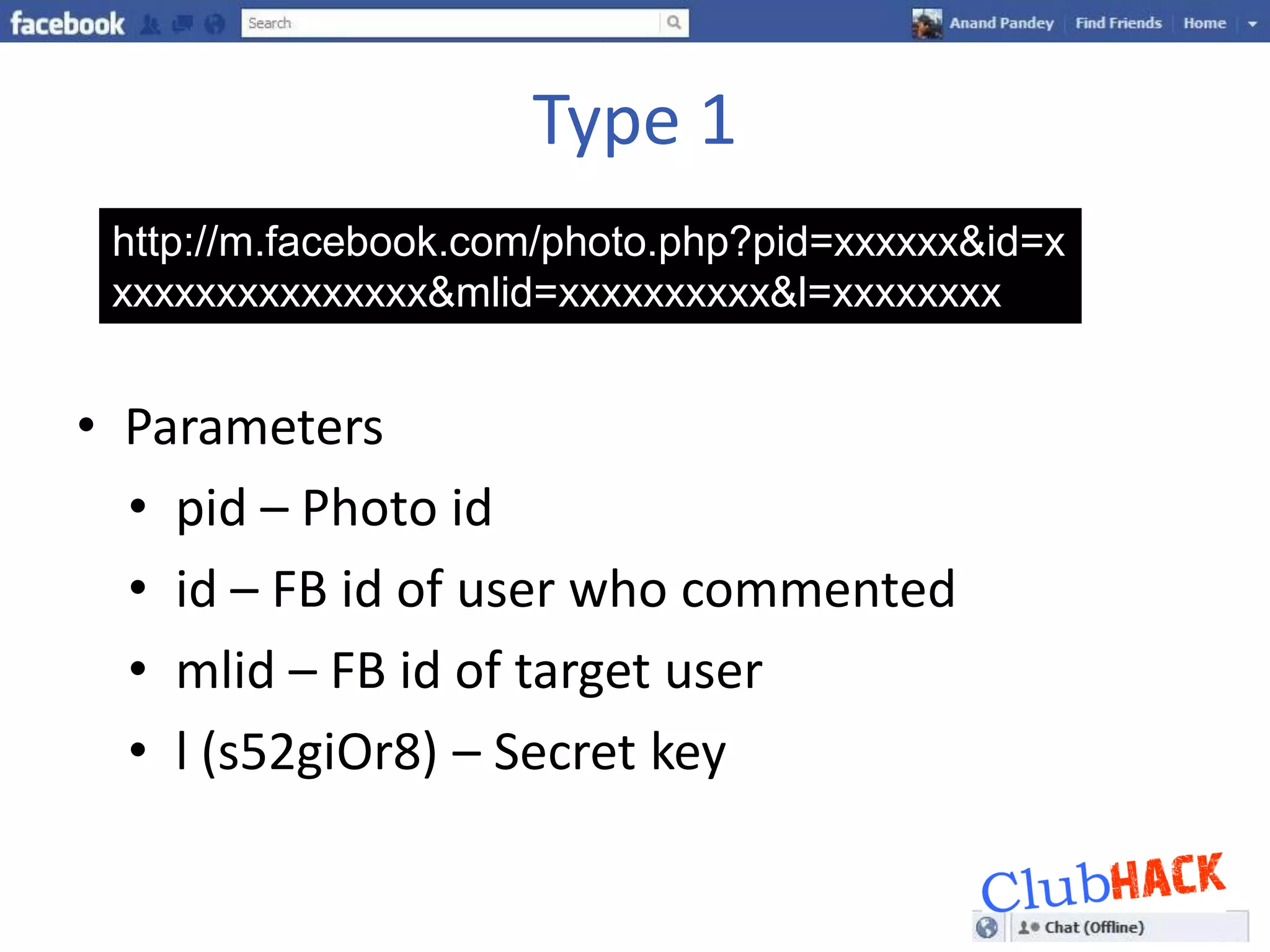
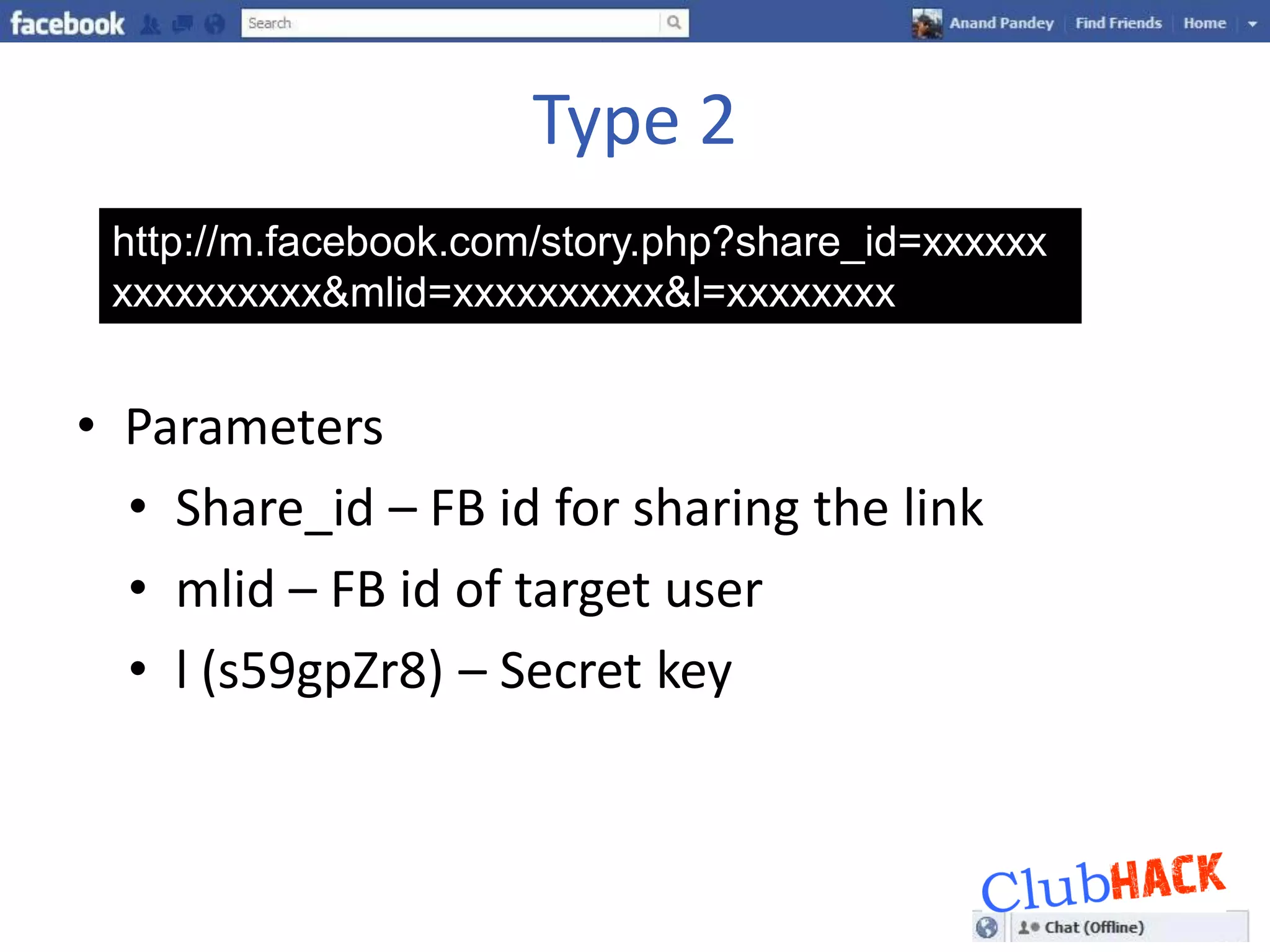
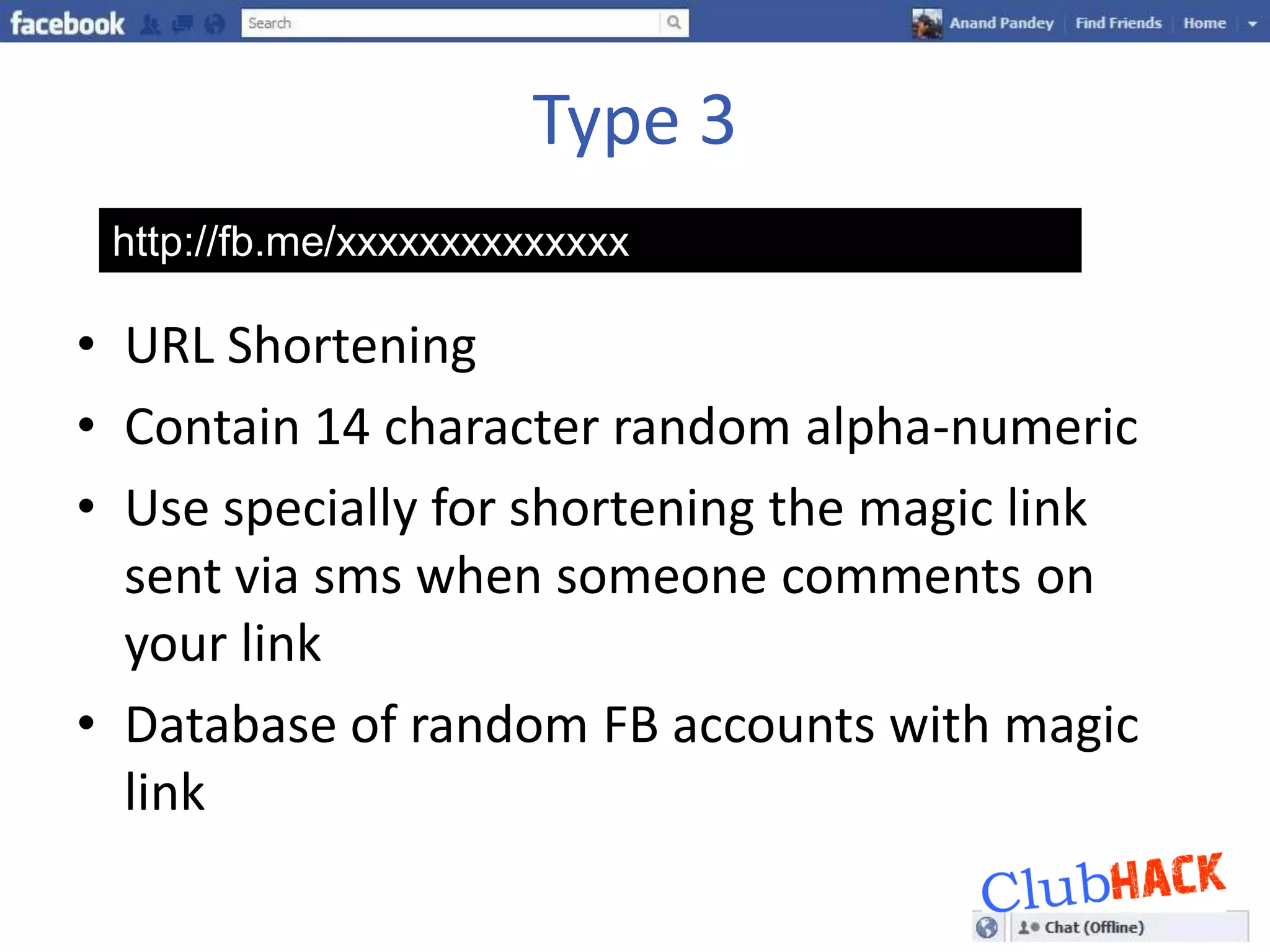
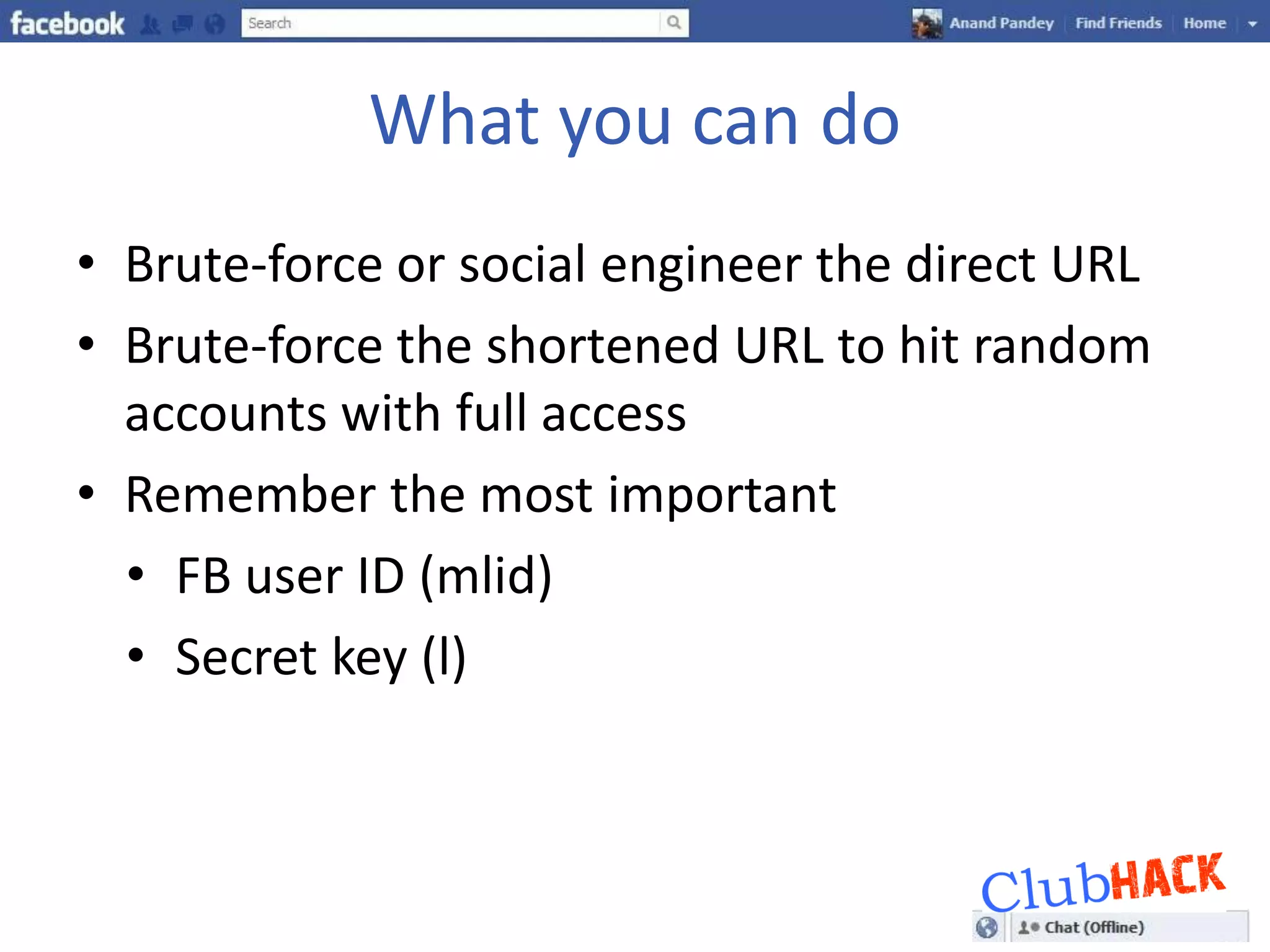
One Link provides direct access to a Facebook account without needing a username or password by bypassing all security points through a single link. The link contains parameters like a photo or user ID and a secret key that can be brute forced or socially engineered to gain full access to random Facebook accounts. Users should be aware of these direct links and the security risks they pose.