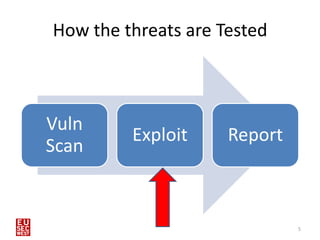
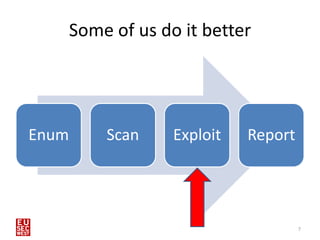
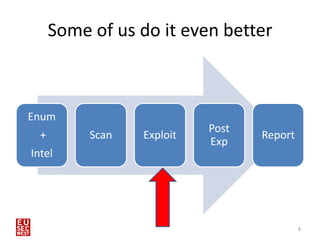
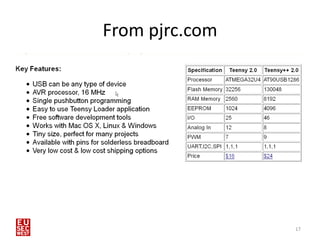
This document discusses using human interface devices like the Teensy microcontroller in penetration tests against Windows 8 systems. It introduces the Kautilya toolkit for programming Teensy payloads and demonstrates attacks against Windows 8 by connecting the Teensy and executing payloads with the privileges of the logged-in user. Limitations of this technique include storage limits on Teensy and an inability to read responses or clear itself after running. Defenses include disabling removable devices or locking USB ports.