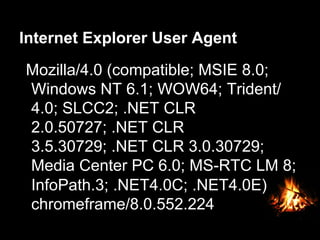
This document discusses various free or low-cost security measures organizations can implement, including: using EMET to help prevent exploits; blocking Java user agents at the proxy to prevent Java-based exploits; implementing internal bug bounty programs; deploying port-forwarding honeypots; disabling WPAD; restricting internal DNS lookups; and using "evil canary" decoys to detect intruders. It also emphasizes the importance of monitoring for unusual traffic patterns and authentication events.