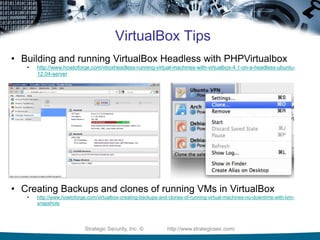
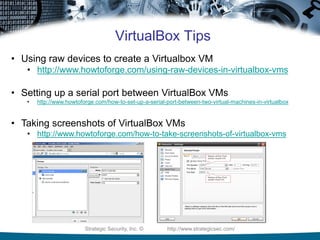
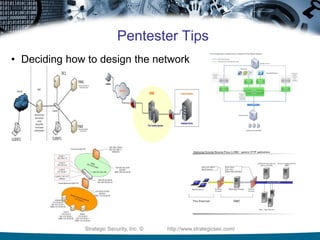
The document provides guidelines for establishing a low-cost hacklab covering hardware, software, VMware, VirtualBox, and pentesting tips. It includes recommendations on hardware options, acquiring operating systems and vulnerable applications, as well as specific technical tips for using VMware and VirtualBox effectively. Additionally, it emphasizes staying updated on vulnerabilities and suggests best practices for network design and defense measures.