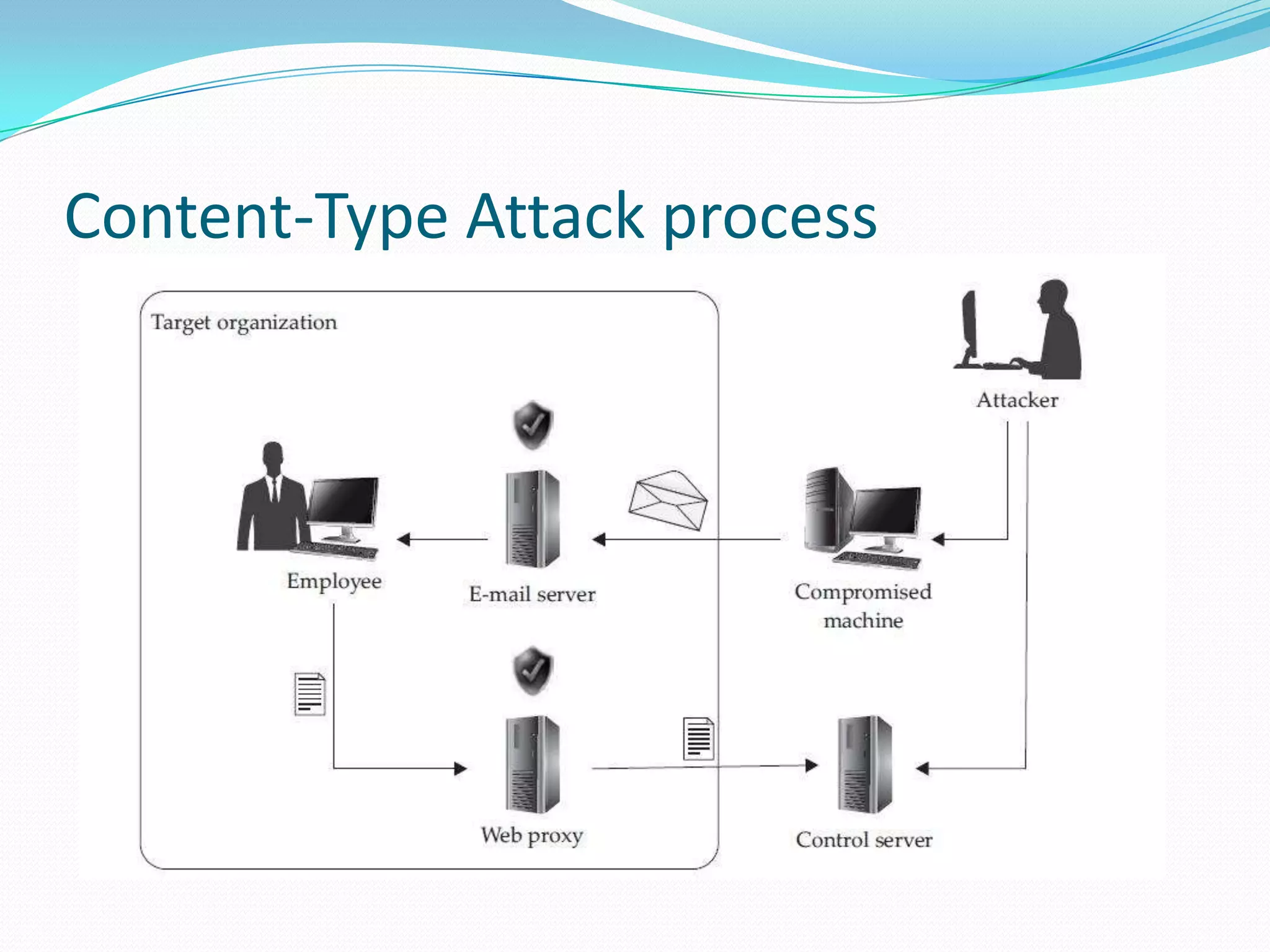
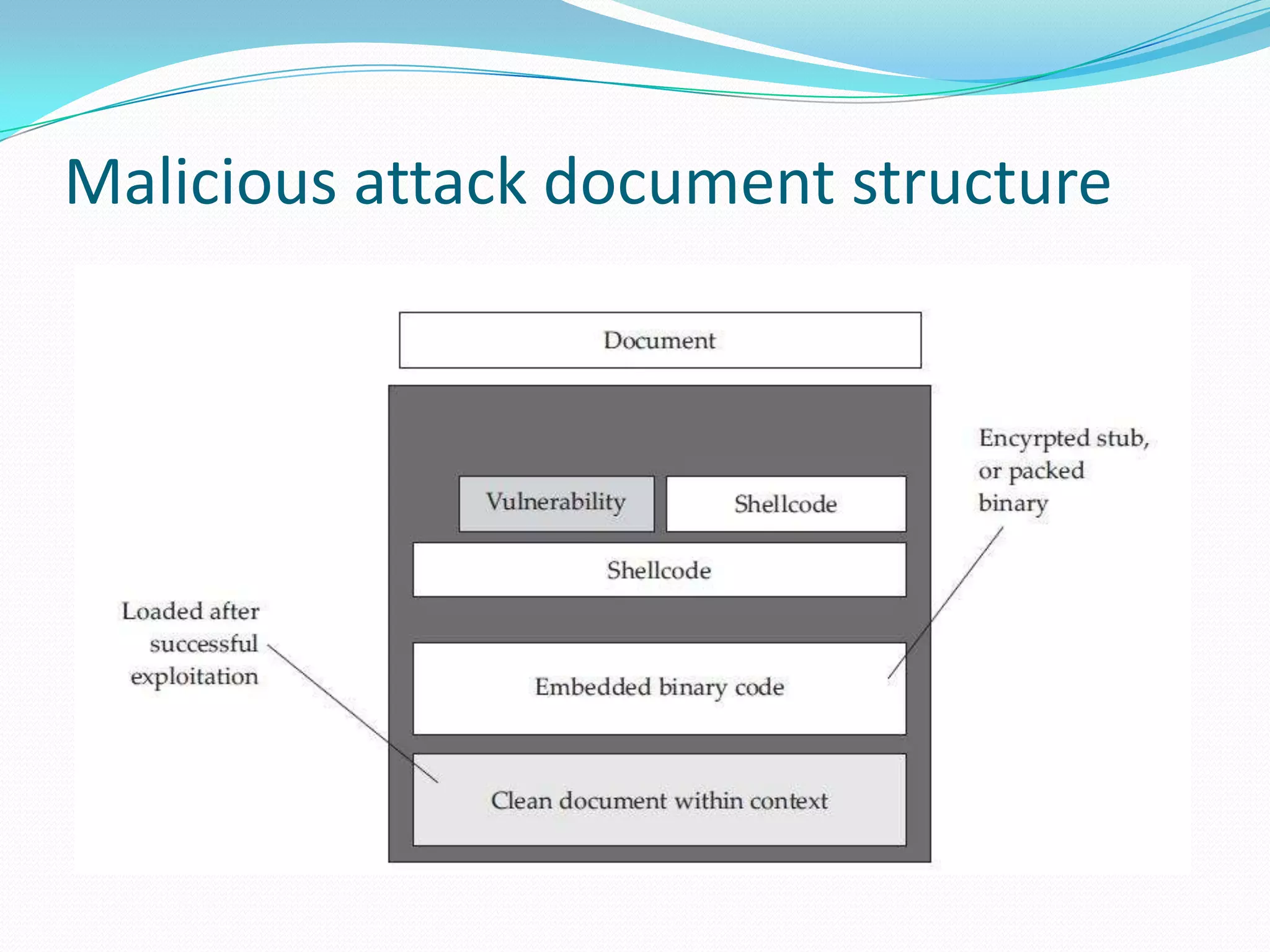
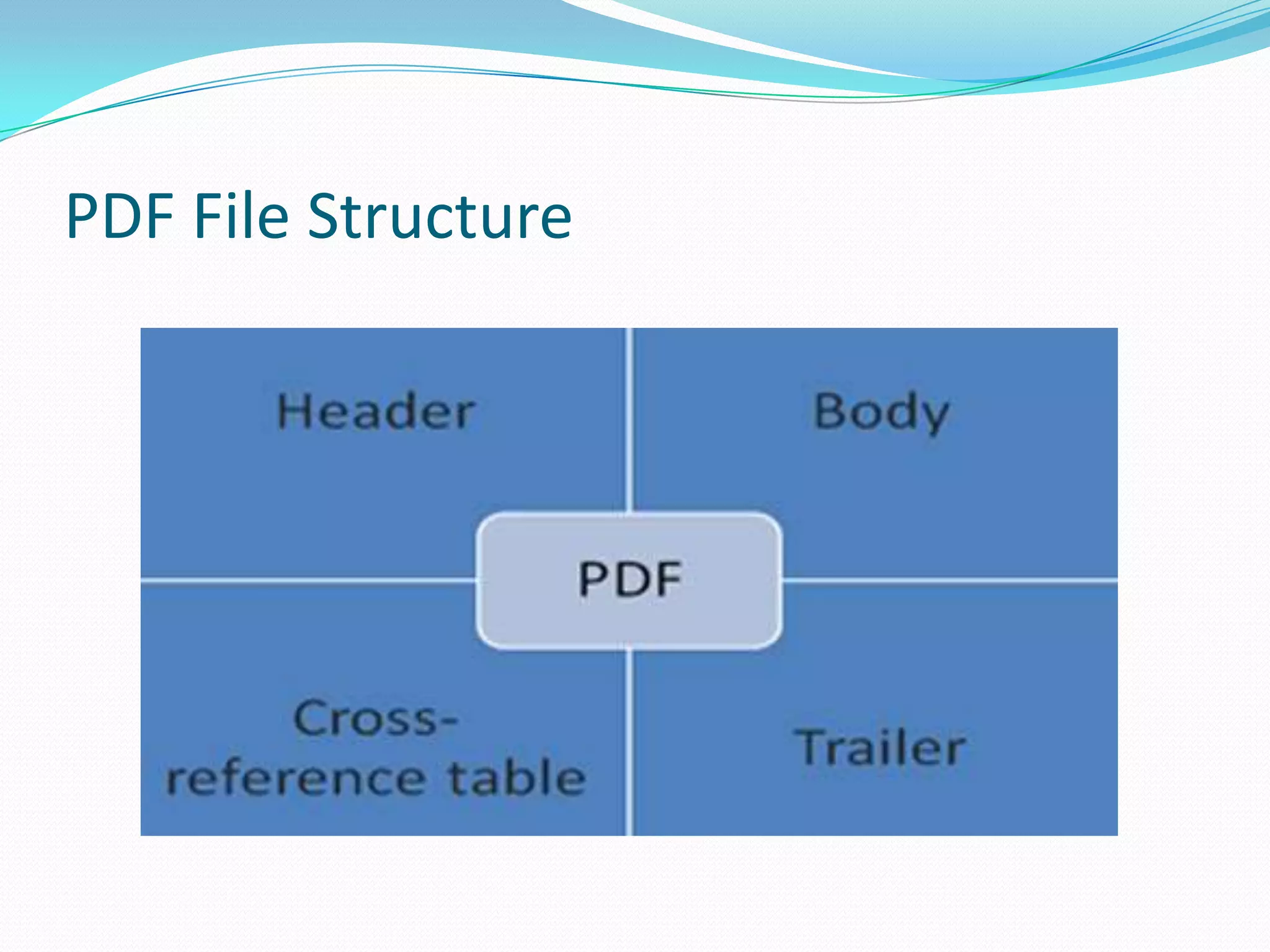
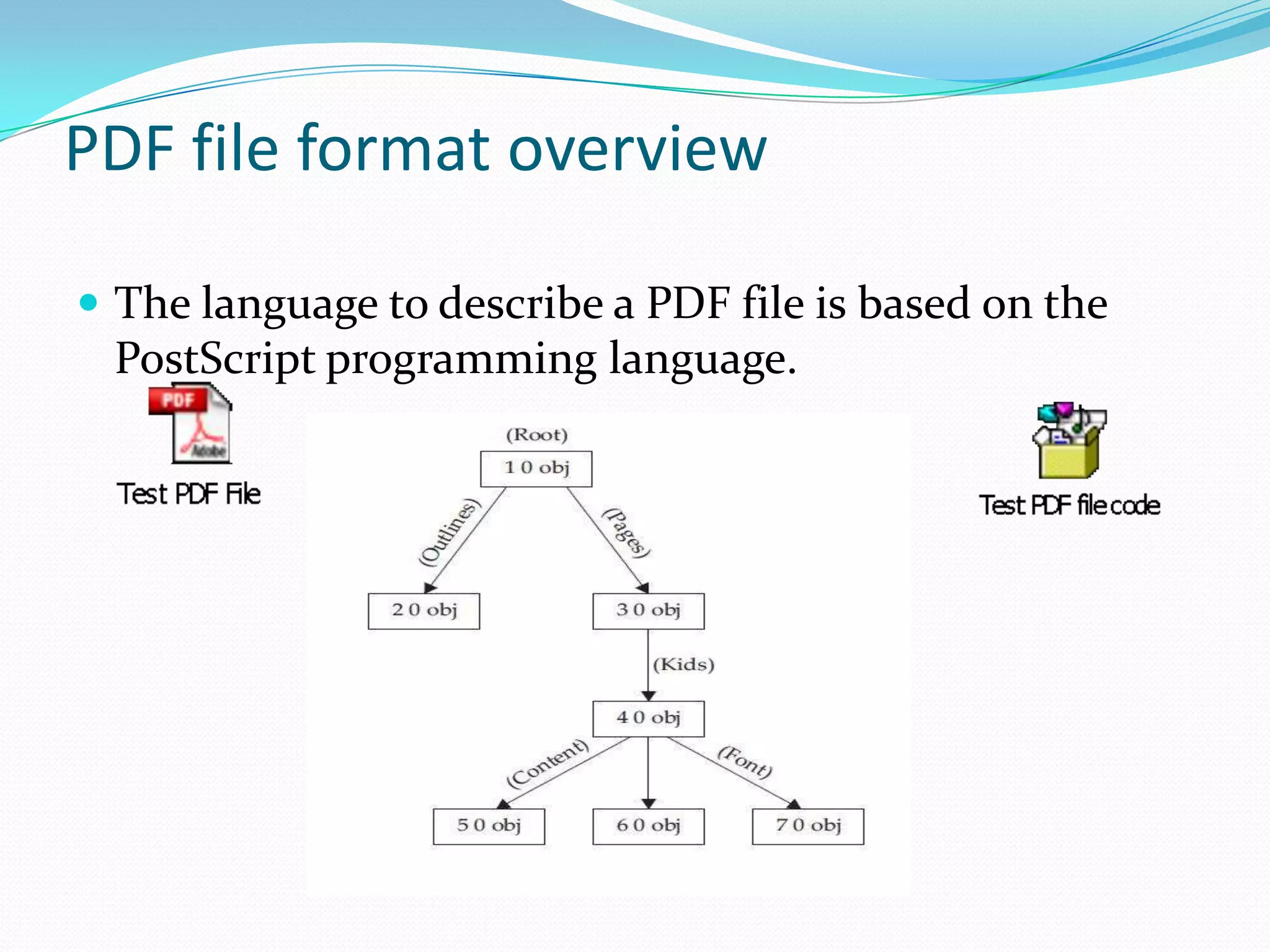
The document discusses Content-Type attacks and how to protect against them. The author works as an information security consultant focusing on vulnerability assessment, penetration testing, and secure environment setup. Content-Type attacks involve exploiting vulnerabilities in client-side software like Adobe Reader or Microsoft Office to execute malicious code. Attackers embed malformed content that corrupts memory, allowing their shellcode to run. The document then covers the attack process, malicious document structure, a demo, PDF file format overview, analyzing PDFs with scripts, and protection techniques like keeping software updated, disabling scripts, enabling data execution prevention, and avoiding opening unknown file attachments.