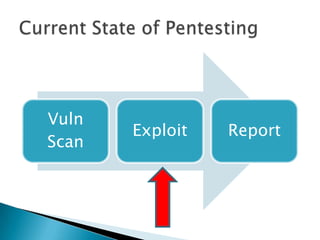
The document discusses using a Teensy microcontroller device to create payloads for penetration testing. It provides an overview of the Teensy, examples of how it has been used in previous penetration tests, and introduces Kautilya, a Ruby-based toolkit that aims to make Teensy more useful for penetration testers by providing pre-built payloads that can be selected and customized. The payloads discussed are mostly for Windows systems and focus on techniques like installing backdoors, modifying system settings, downloading files from pastebins, and collecting information from victims. Limitations and areas for future improvement are also mentioned.