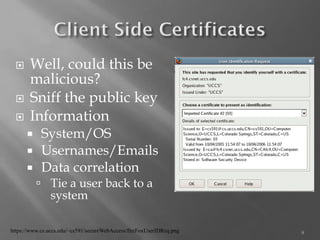
The document discusses the challenges of achieving true anonymity online, emphasizing the importance of privacy and the potential risks faced by users. It explores various anonymization methods, such as proxies and freemail services, while also highlighting the dangers posed to law enforcement and societal order by these technologies. Additionally, the document presents a range of detection techniques used to track users despite their efforts to anonymize themselves.