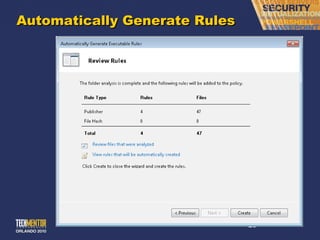
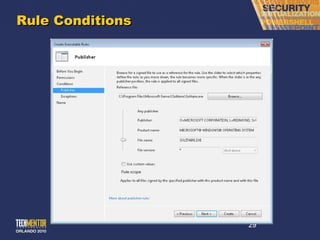
This document discusses implementing AppLocker whitelisting to prevent malware execution. It begins by explaining the limitations of traditional antivirus and introduces AppLocker as a "whitelisting" approach that allows only approved applications to run. It then provides guidance on planning and deploying AppLocker, including determining scope, generating application rules, selecting rule types, and configuring Group Policy for enforcement. The presentation aims to demonstrate how AppLocker can eliminate many IT problems by preventing the execution of unauthorized or unknown software.