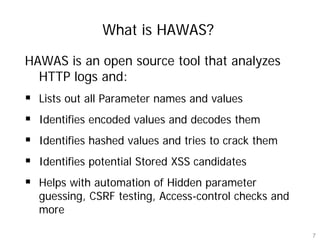
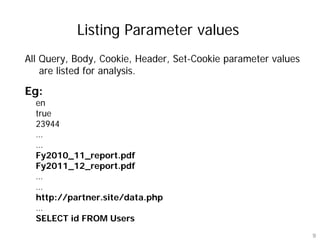
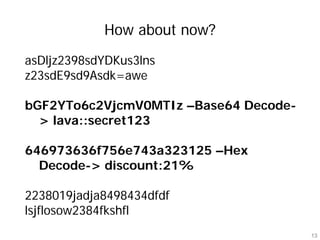
Hawas is an open-source tool designed to automate the analysis of HTTP logs for web application security, focusing on identifying vulnerabilities such as encoded values, hashed values, and stored XSS candidates. It facilitates the testing of hidden parameters, CSRF, and access-control checks by comparing modified requests against baseline responses. The tool helps penetration testers uncover complex vulnerabilities often missed by automated scanners.