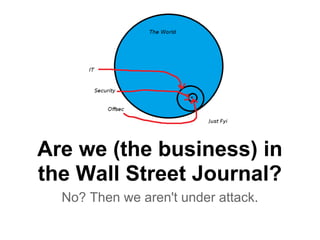
The document discusses practical exploitation techniques used by penetration testers and red teams. It outlines the speaker's background as a senior red teamer who breaks into various systems like mainframes, bank accounts, SCADA systems, and web applications. The speaker defines practical exploitation as applying techniques, tactics, and procedures to accomplish objectives within a targeted engagement. The speaker then demonstrates three exploits: 1) Using a Linux pivot to exploit MS08_067 on Windows, 2) Exploiting a Rails vulnerability to steal credentials using Mimikatz on Windows, and 3) Using a Windows pivot to exploit DistCC on Linux via WinRM on IIS. The speaker emphasizes patching vulnerabilities and not enabling services like WinRM on DMZ