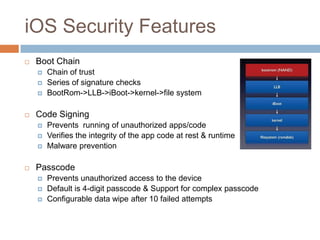
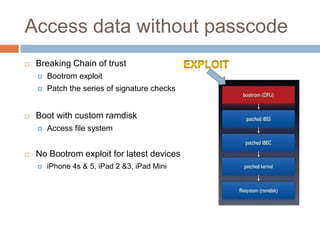
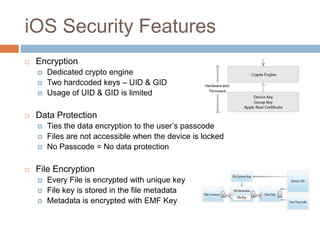
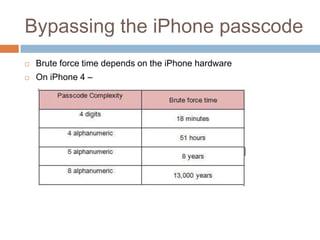
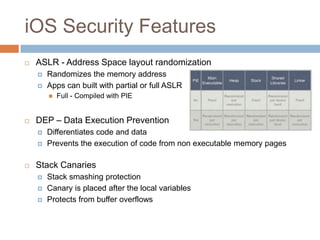
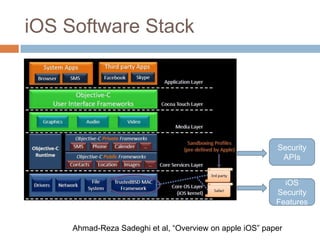
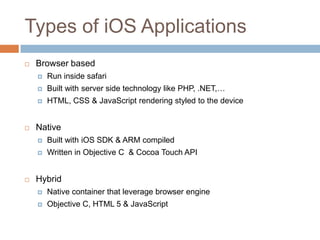
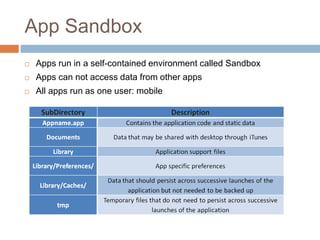
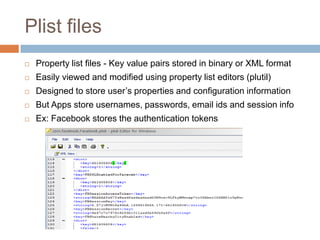
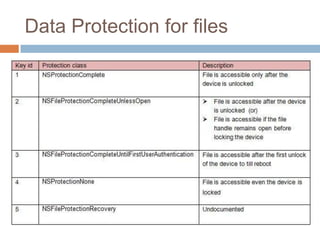
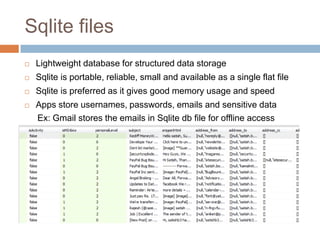
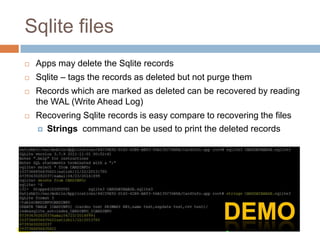
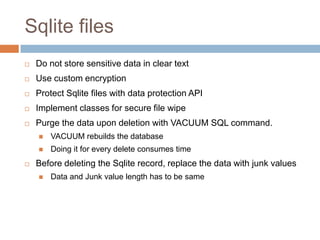
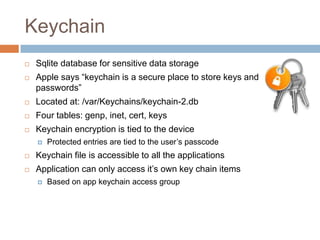
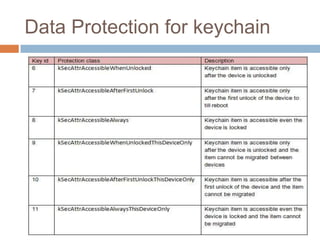
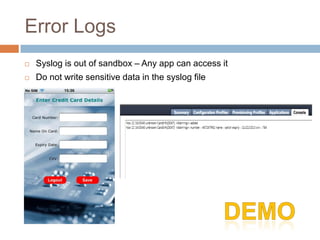
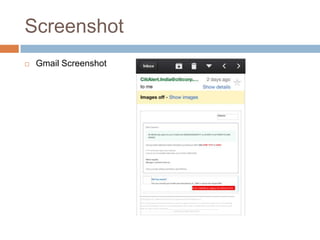
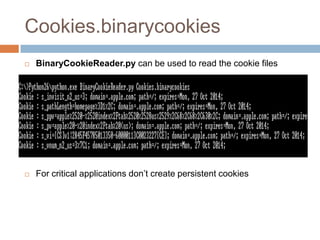
The document discusses iOS application security and hacking techniques, outlining iOS security features such as code signing, encryption, and sandboxing. It details various vulnerabilities, including issues with local storage systems like plist and SQLite files, and suggests best practices for securing sensitive data. Additionally, it examines runtime analysis methods for application exploitation and emphasizes the importance of secure transport protocols in preventing MITM attacks.