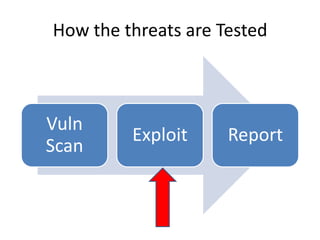
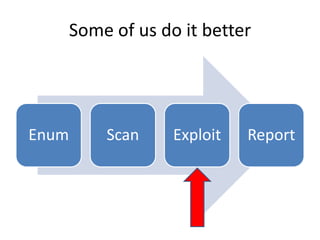
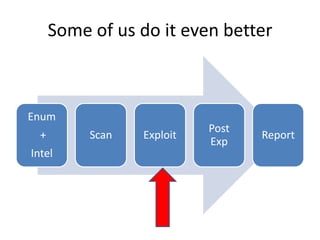
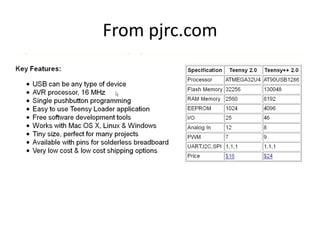
This document provides an overview of a presentation about using human interface devices like keyboards for penetration testing. The presentation covers using the Teensy microcontroller to create payloads that are executed when the device is plugged into a target system. It demonstrates writing payloads using the Kautilya toolkit to perform attacks like installing backdoors, changing system settings, gathering information, and executing code on Windows and Linux machines. The document also discusses limitations and ways to prevent attacks using malicious human interface devices.