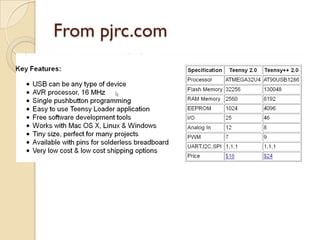
The document presents a talk by Nikhil Mittal about innovative penetration testing techniques using devices like Teensy and the Kautilya toolkit. It explores the limitations and future improvements of these tools, emphasizing the need for new methods in the current penetration testing landscape. The talk also recounts practical examples of using USB devices for exploitation, while addressing challenges faced during assessments.