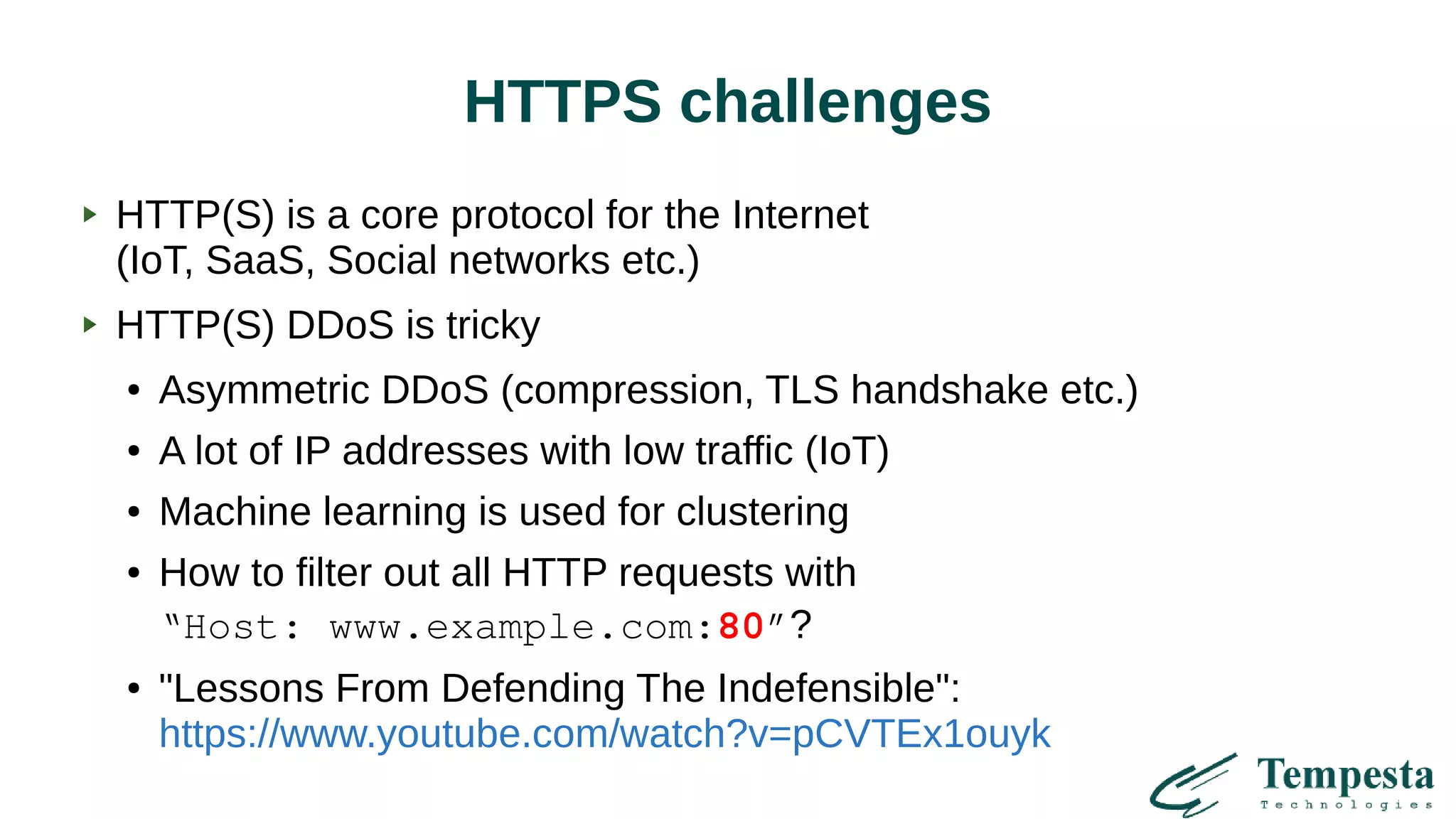
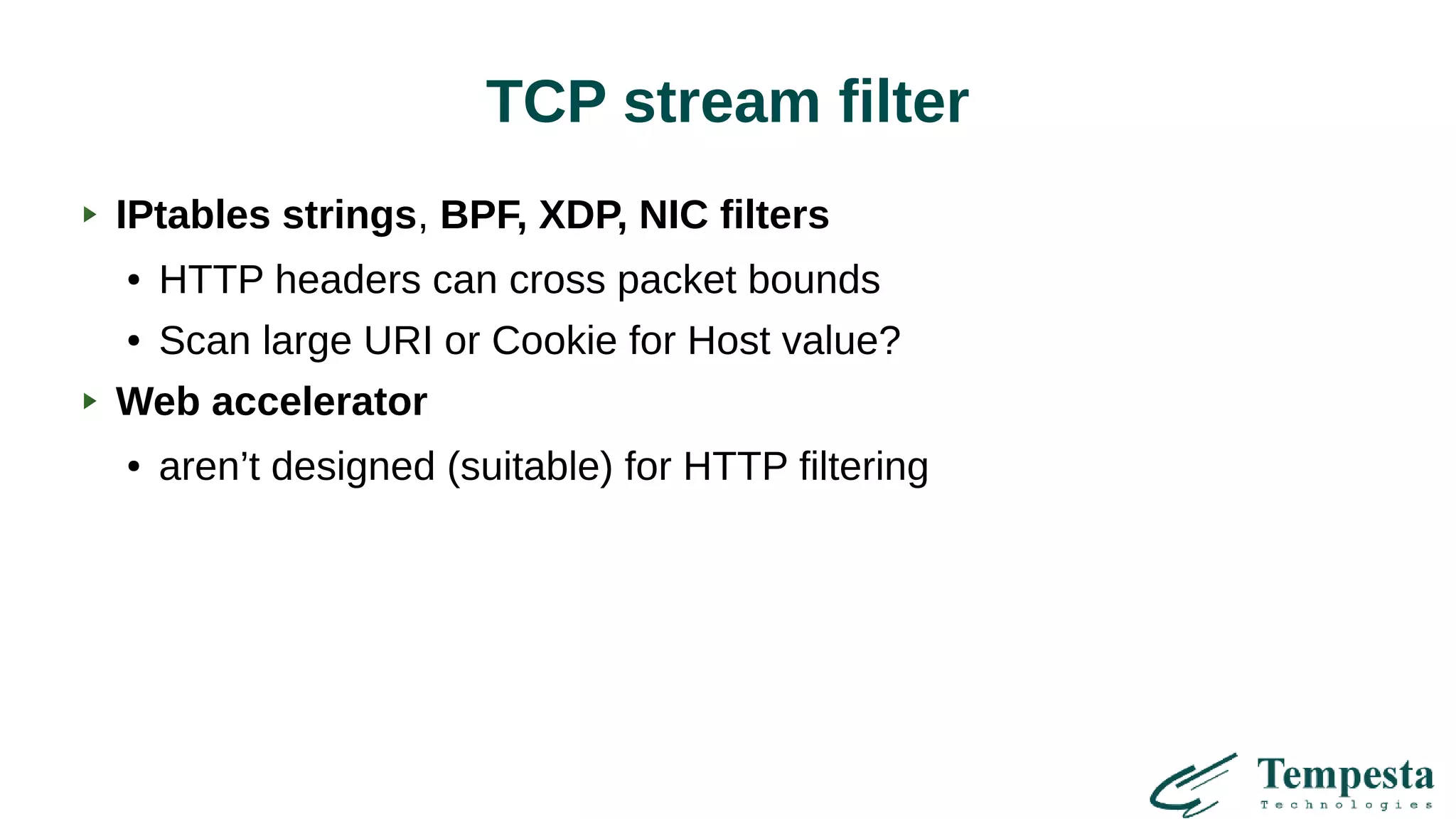
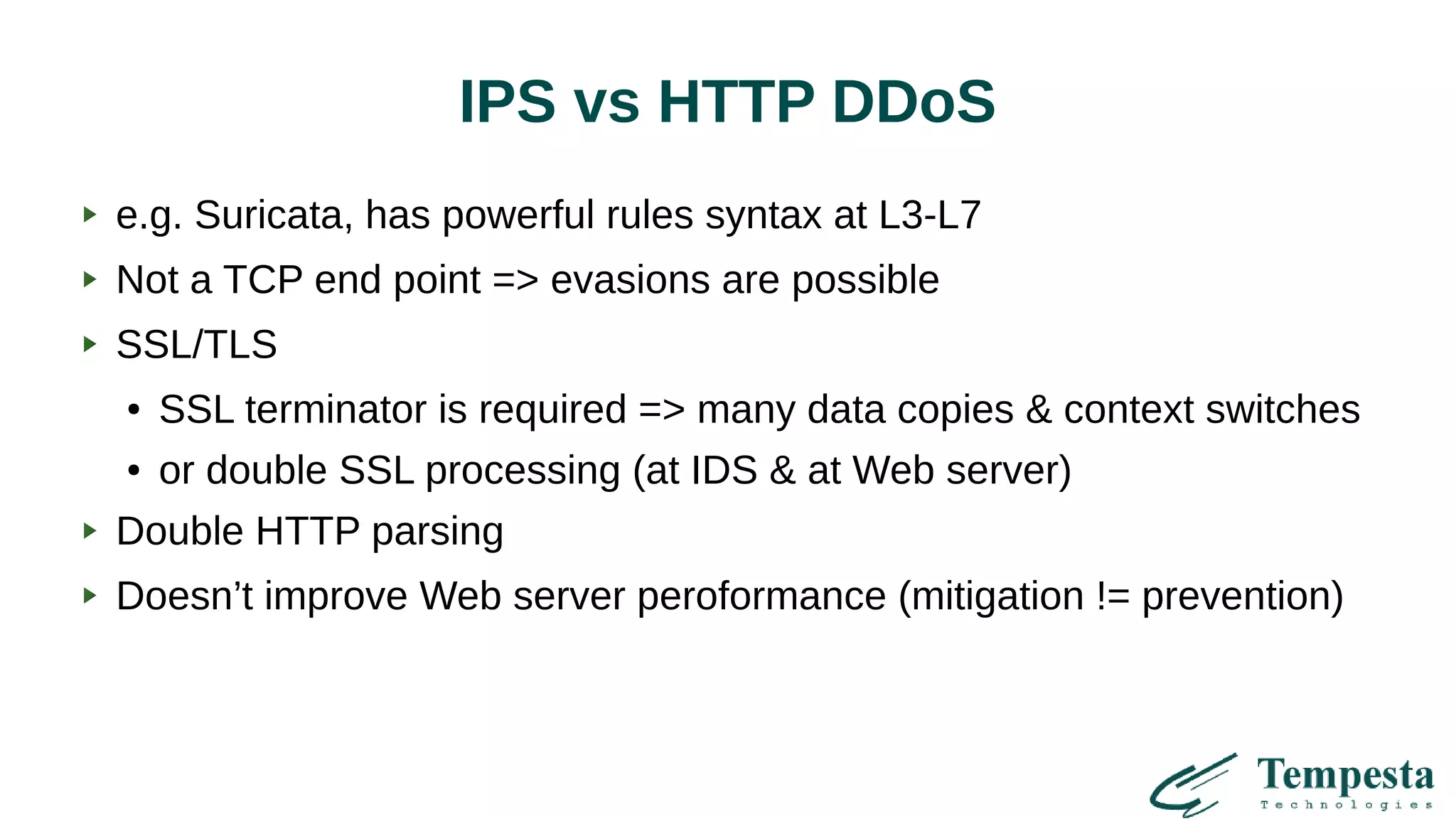
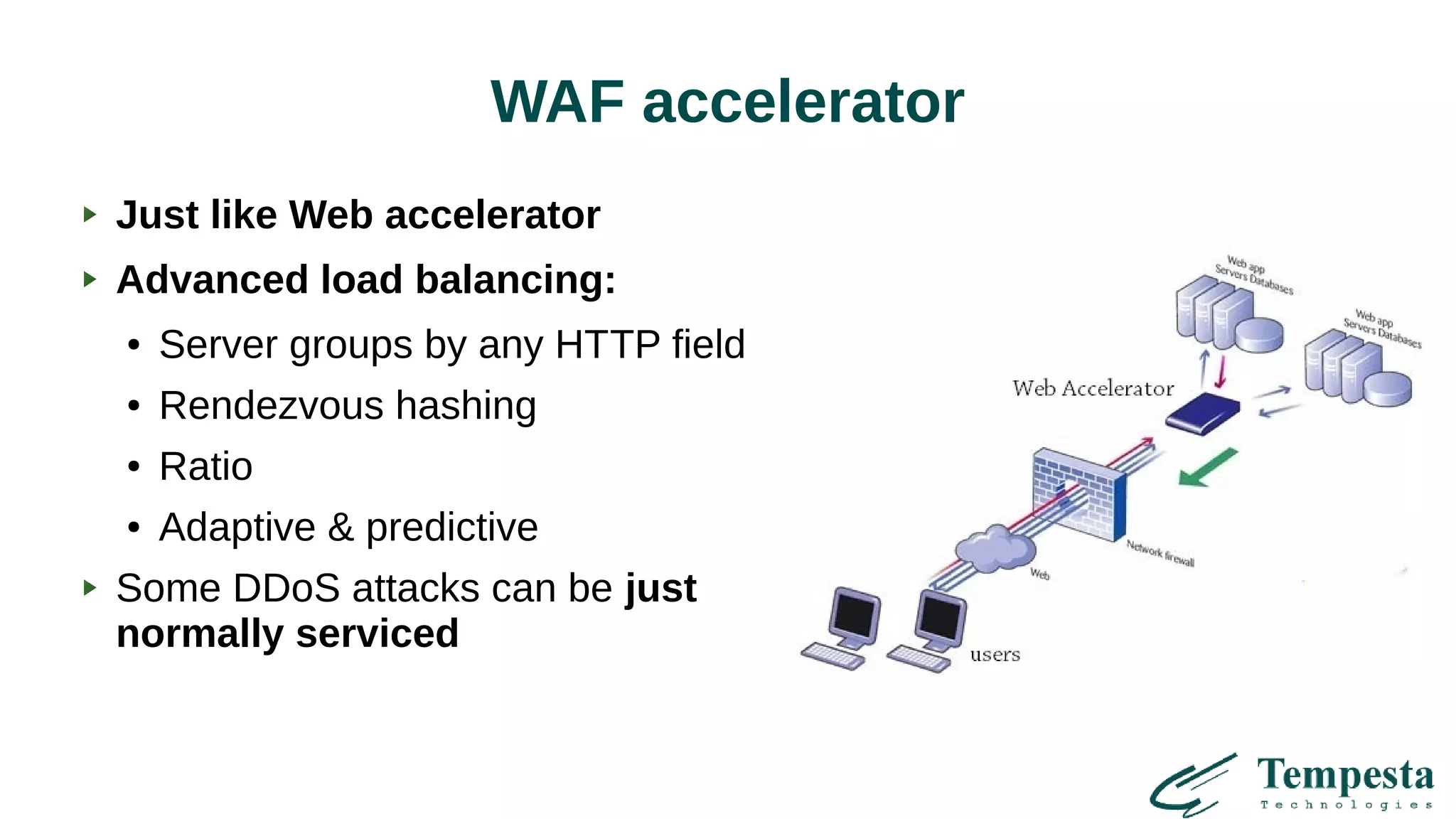
The document discusses challenges and solutions related to HTTP(S) DDoS attacks, highlighting the need for advanced filtering techniques and optimizations at various network layers. It outlines the limitations of traditional web accelerators and proposes kernel-level TLS processing and fast HTTP parsing as potential mitigations. Additionally, it emphasizes the importance of using machine learning for clustering and creating efficient traffic management strategies to combat asymmetric DDoS attacks.












![Fast network I/O: kernel bypass
Netmap, DPDK, PF_RING etc.
No [zero-copy] tcpdump, tc, ipvs, iptables etc.
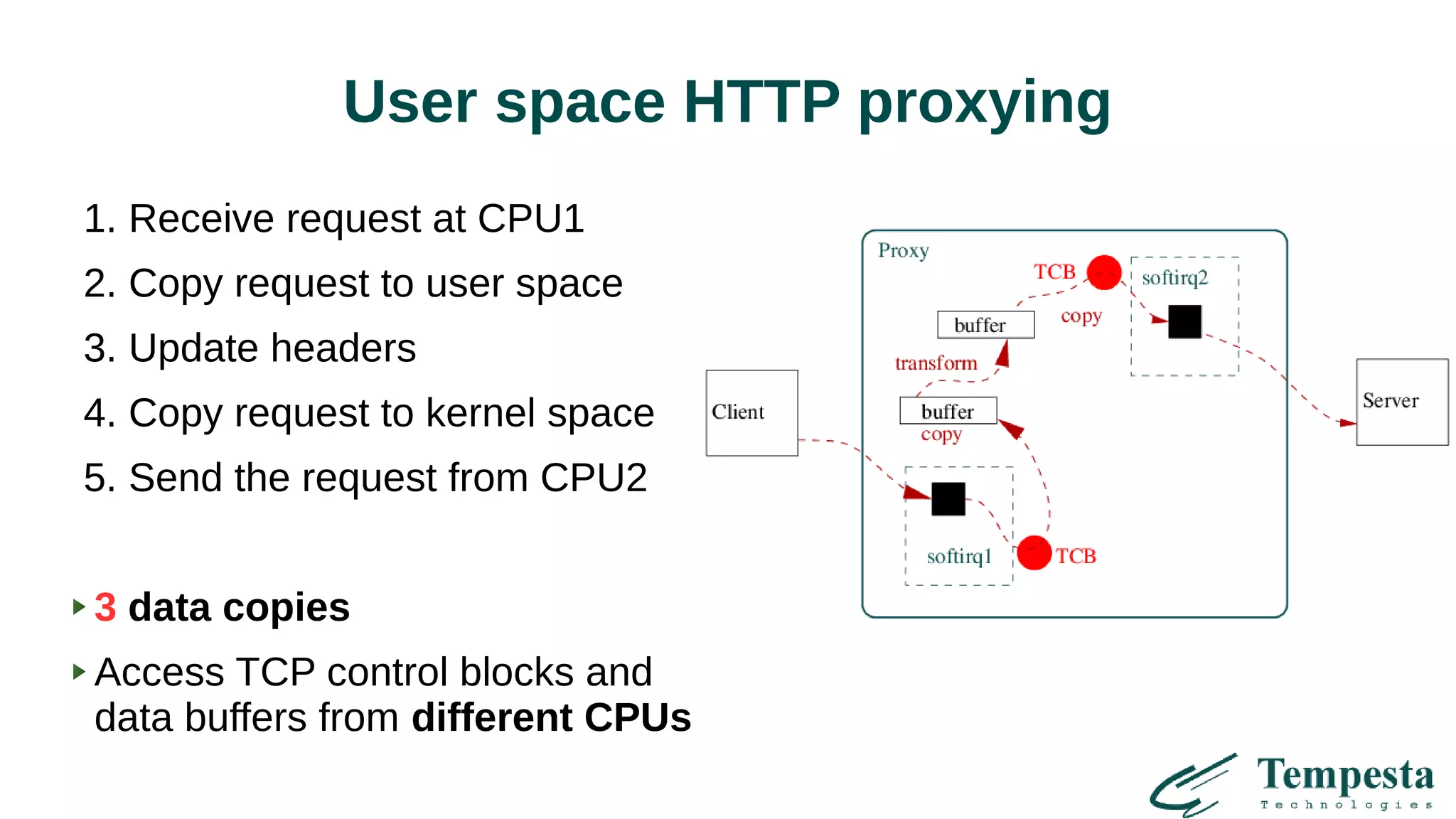
User-space TCP/IP stack issues
● No preemption control => no [good] RCU
● pthread_spinlock are naive (vs. MCS locks.)
● No access to buddy allocator (need memory reservation)
Win for simple applications only
(IP & UDP, but not for TCP & HTTP)](https://image.slidesharecdn.com/1-171110224025/75/Linux-kernel-TLS-HTTPS-Tempesta-Technologies-18-2048.jpg)



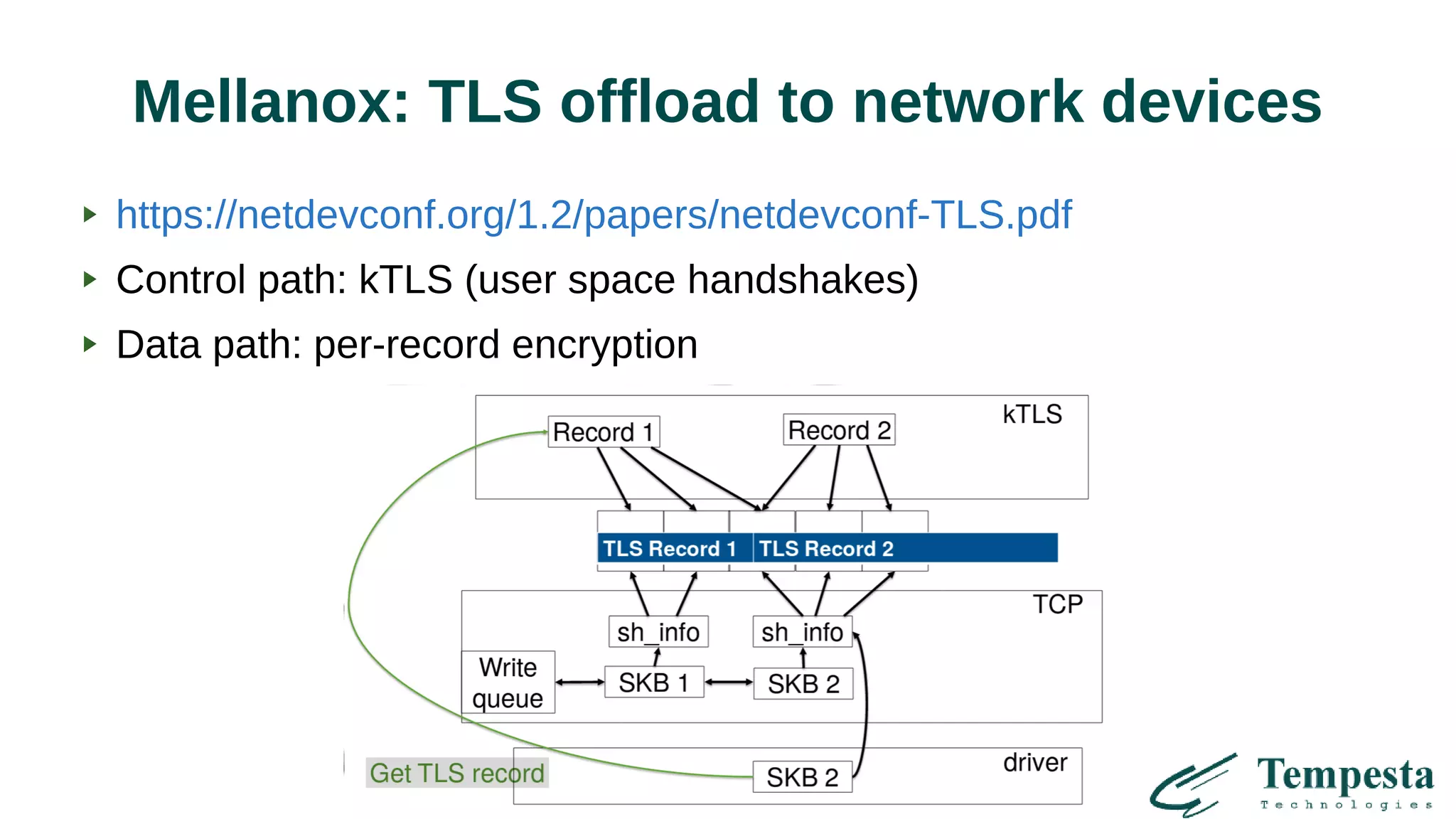

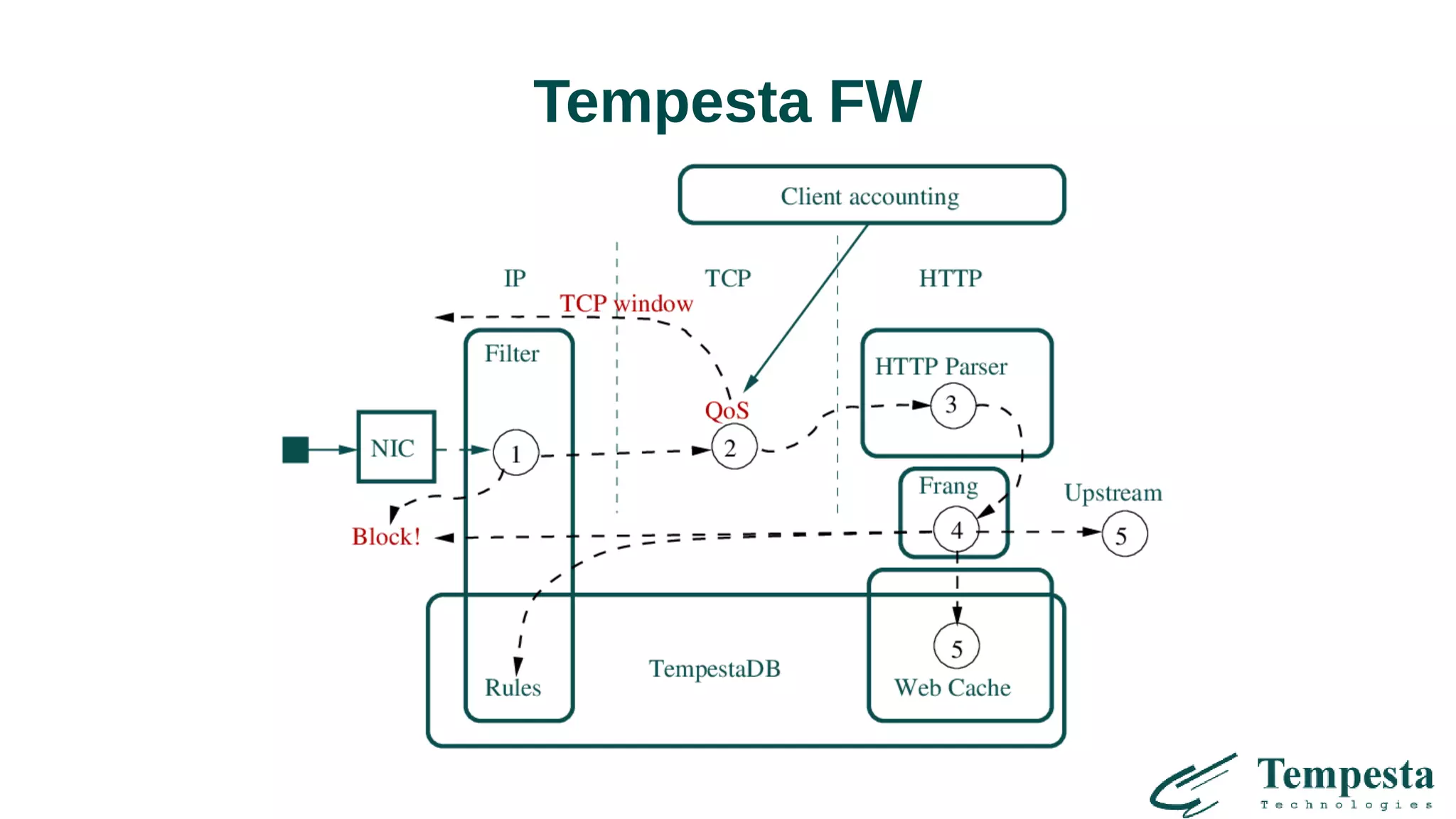
![HTTPS/TCP/IP stack
(in progress)
Alternative to user space TCP/IP stacks
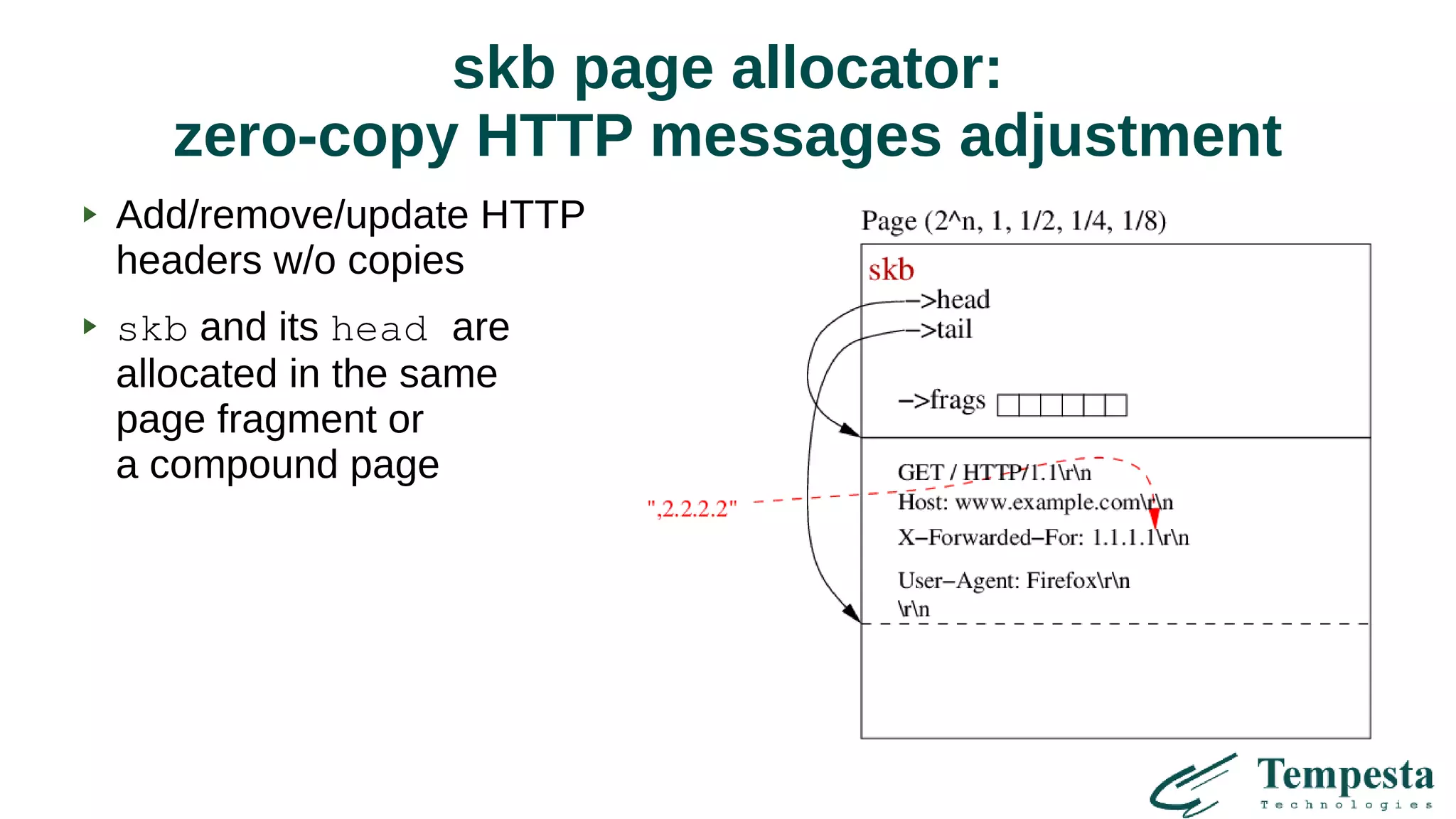
HTTPS is built into TCP/IP stack
Kernel TLS (fork from mbedTLS) – [almost] no copying
(1 human month to port TLS to kernel!)
HTTP firewall plus to IPtables and Socket filter
Very fast HTTP parser and strings processing using AVX2
Cache-conscious in-memory Web-cache for DDoS mitigation
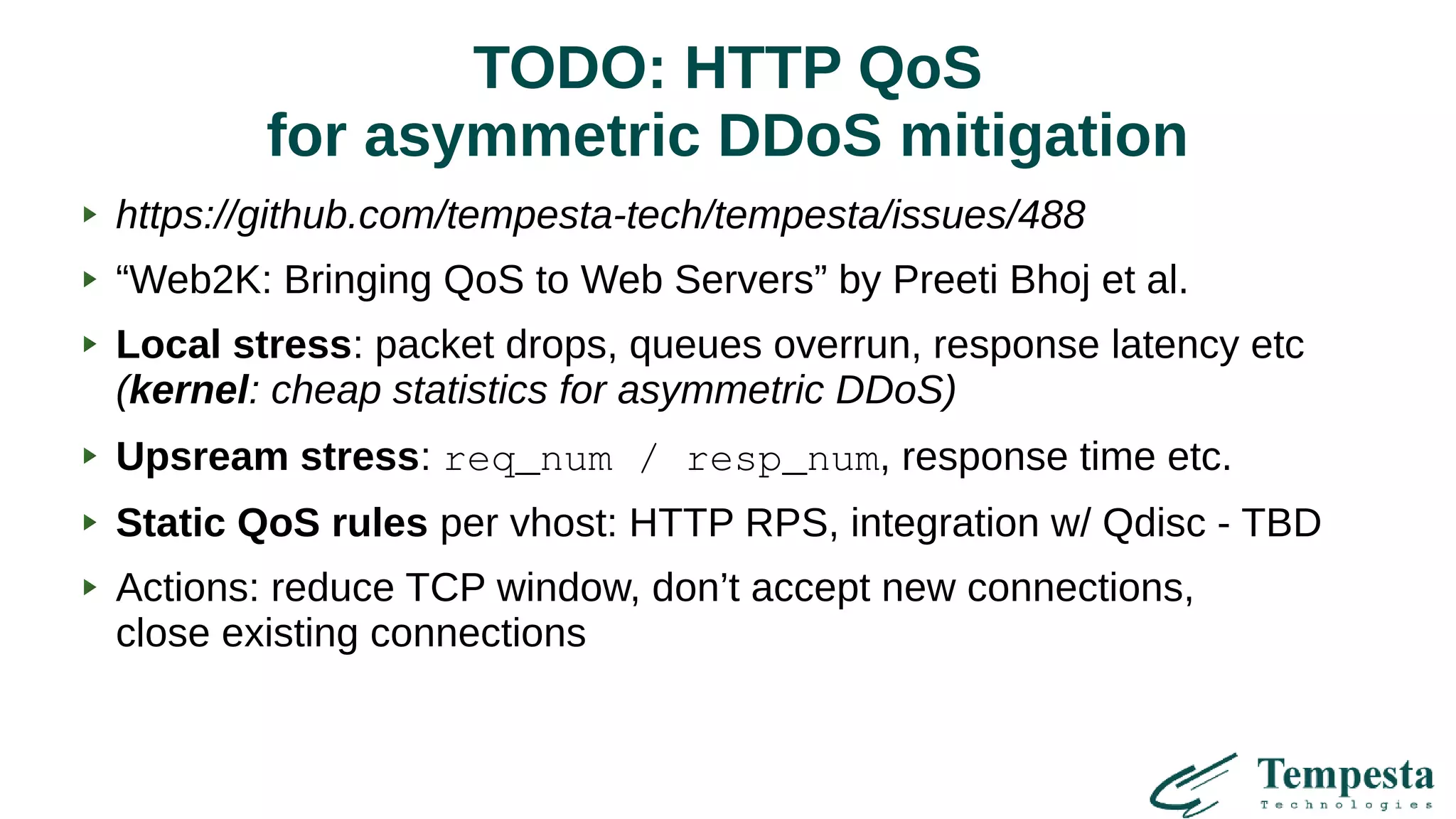
TODO
● HTTP QoS for asymmetric DDoS mitigation
● DSL for multi-layer filter rules](https://image.slidesharecdn.com/1-171110224025/75/Linux-kernel-TLS-HTTPS-Tempesta-Technologies-24-2048.jpg)