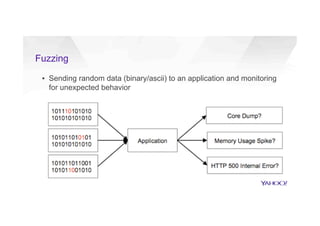
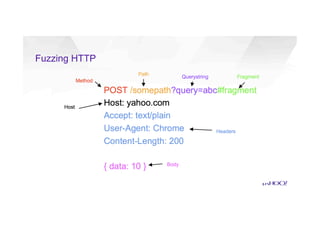
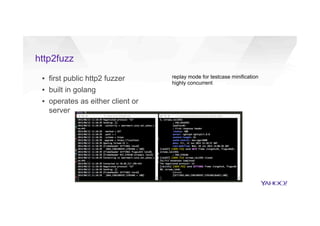
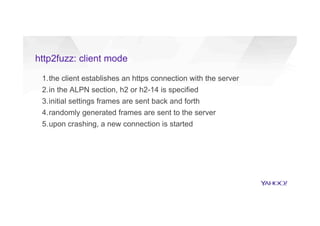
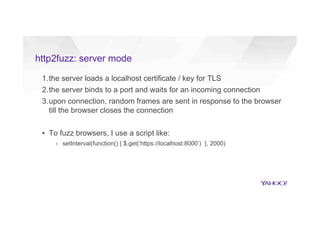
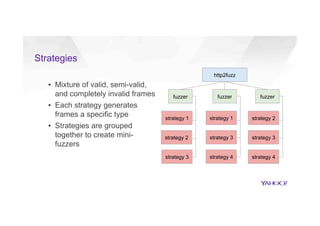
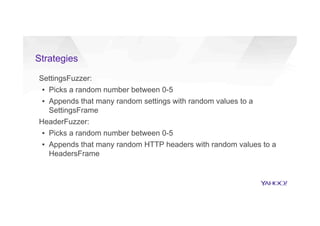
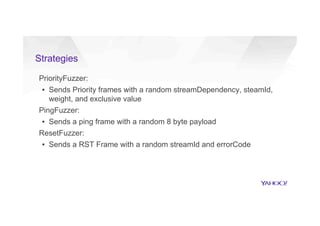
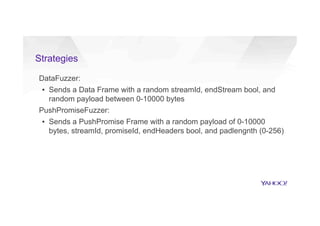
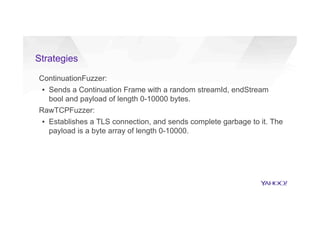
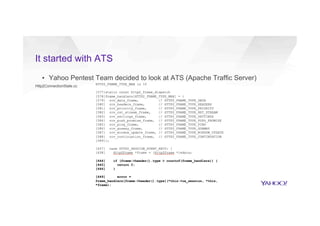
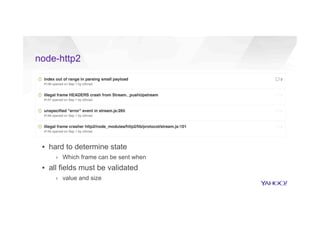
This document discusses attacking HTTP/2 implementations by fuzzing them with malformed requests. It introduces http2fuzz, an open source fuzzer for HTTP/2 written in Go. Using http2fuzz, the authors discovered crashes in the Apache Traffic Server and Firefox HTTP/2 implementations by sending unexpected or invalid frame types and payloads. Fuzzing uncovered vulnerabilities like out-of-bounds memory accesses, integer overflows, and denial of service issues. The document emphasizes that HTTP/2 implementations must carefully validate all frame fields and control states to avoid security issues.